
News: Magic Leap & Weta Workshop Release Dr. Grordbort's Invaders for Magic Leap One
As promised last week, Magic Leap has finally released the long-awaited augmented reality game Dr. Grordbort's Invaders.


As promised last week, Magic Leap has finally released the long-awaited augmented reality game Dr. Grordbort's Invaders.

Magic Leap One owners with itchy trigger fingers may have their itch scratched next week, as Magic Leap has shared a brief teaser on Twitter for the long-awaited Dr. Grordbort's Invaders game from Weta Workshop.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

With developers chomping at the bit to play with ARKit 2.0, Unity has updated its ARKit plugin to enable access to the new augmented reality superpowers of the toolkit.

On Tuesday, at Google's I/O developer conference, the company announced a huge update to its ARCore augmented reality toolkit that matches the latest features of ARKit, and surpasses Apple's AR platform via support for shared experiences.

During Snap Inc.'s quarterly earnings report, released on Tuesday, the company disclosed that it snagged a revenue total of $230.8 million for the first quarter of 2018, an increase of 54% compared to last year, largely fueled by its augmented reality offerings and other advertising products.
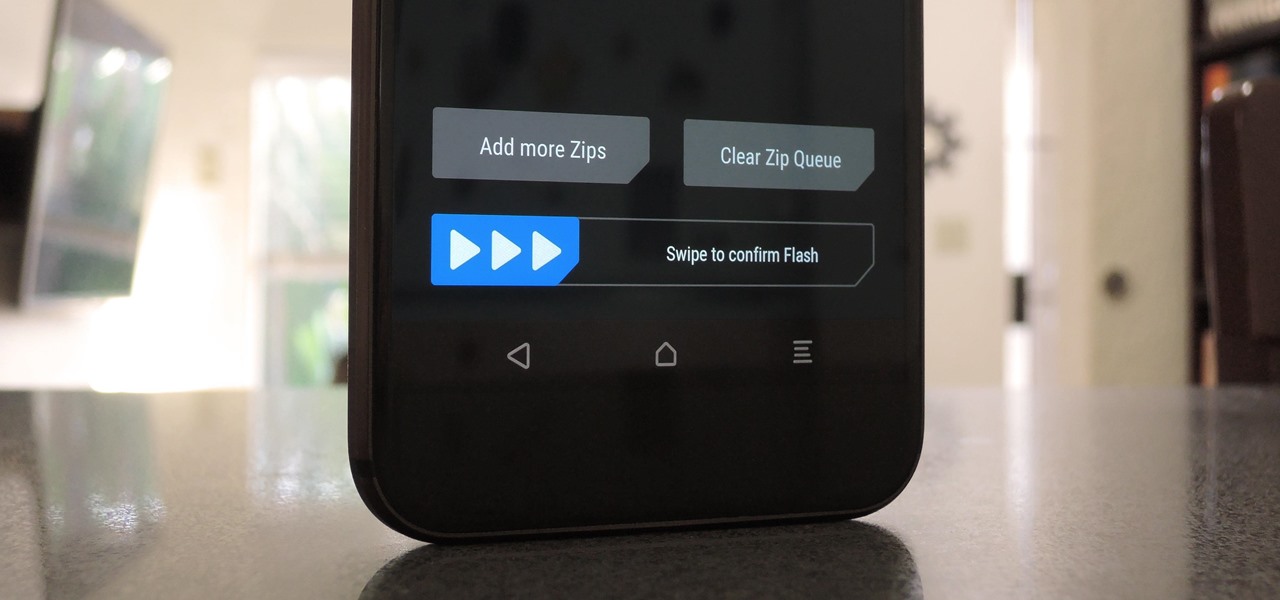
When you're flashing a custom ROM with TWRP recovery, it's almost never just one ZIP. Instead, you have to flash the ROM file, the Gapps, a custom kernel, and maybe even Xposed or Magisk, which results in a lot of back-and-forth. Thankfully, it doesn't have to be this way.

Smartglass maker ThirdEye Gen, Inc. has introduced an augmented reality solution for enterprises that includes their X1 Smartglass and a suite of software applications that enable completely hands-free computing.

Some Montana inhabitants have been making impassioned pleas to legalize raw milk this week. The debate took place during a hearing on House Bill 325, which was held by the Senate Agriculture, Livestock, and Irrigation Committee on Tuesday, March 21.

We've been hearing some interesting rumors in the last few days that are stirring up all kinds of speculation about the potential upcoming consumer release of the HoloLens. However, MSPoweruser has speculated a bit further past the consumer HoloLens release to a possible HoloLens 2 as soon as Q3 2017.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

Five Phases of Hacking:- The five phases of Hacking are as follow:

Hello My Fellow Hackerzz.. This is my first How-to and i'll be updating the “Hacking Android Using Kali” to msfvenom and some FAQ about known problems from comments. So Here we GO!!

If you want to watch a movie on Netflix with a friend, family member, or significant other, but can't meet up in the same living room, the next best thing is doing it remotely from the comfort of your own homes.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.
Collaborating with other people can be a pain, especially if you have to share one device between the entire group. Usually when you're creating a new design or trying to edit a mockup, you end up hunched around a single screen or end up emailing revisions back and forth, which can be difficult when you're short on time.

Back in the '80s, recording live radio was as simple as popping a cassette tape into your boombox and pressing the record button. While we've come along way with regard to accessing radio stations thanks to websites and apps that stream live broadcasts over the internet, it's no longer quite as easy to record.
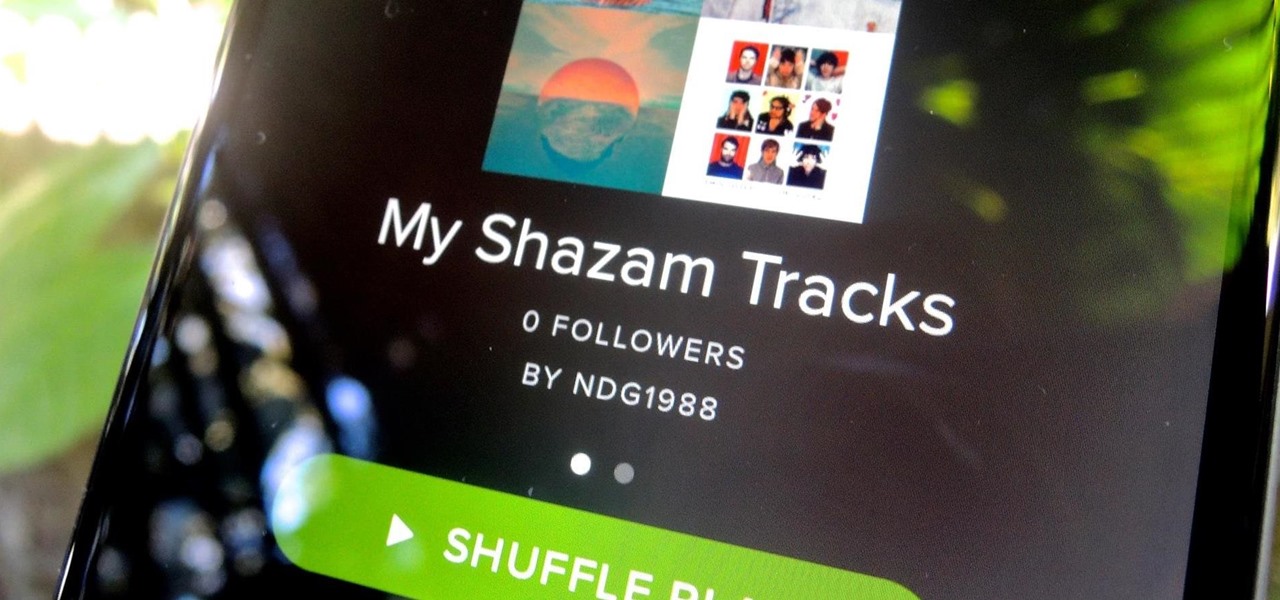
We recently showed you how to recover your Shazam history from Siri, which is a lot less intuitive than finding the songs you've tagged directly in the Shazam app. But with a subscription to Rdio or Spotify, there's no need to even locate your history. You can Shazam songs and have them automatically added to a newly created playlist titled "My Shazam Tracks."
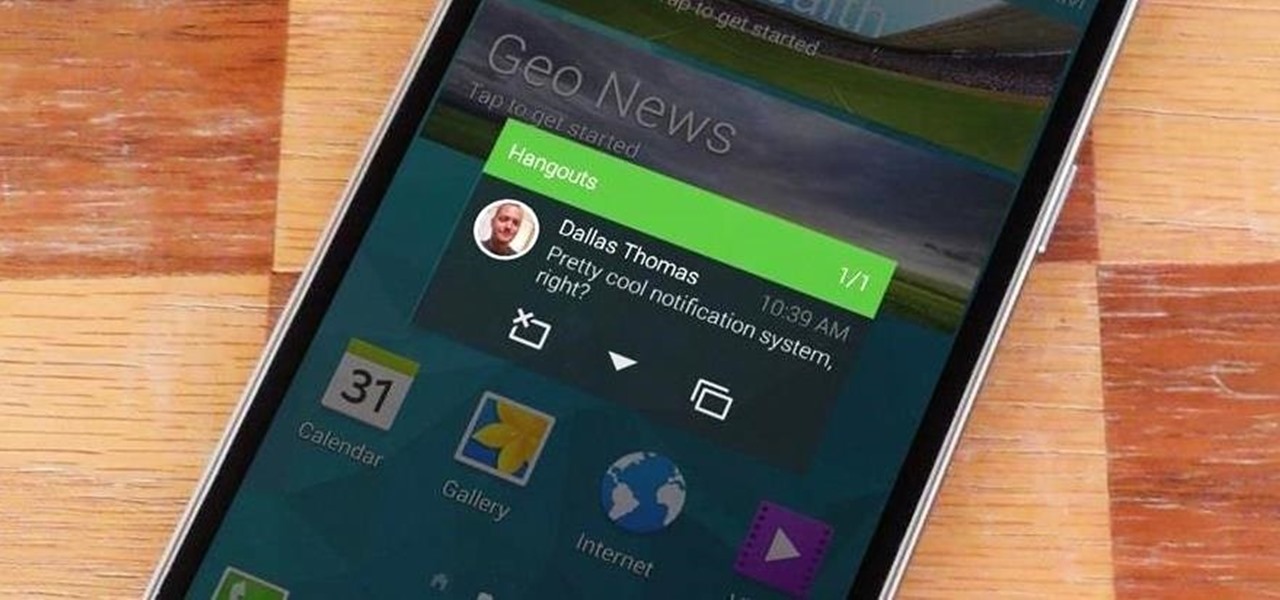
Notifications are an integral part of our day-to-day smartphone usage. They allow us to easily see and act upon all of the latest information that comes our way. Well, most of the time, that is.

If you're like most people, you've stretched before a workout or playing sports. Doing so should help you get your muscles ready to work. While stretching is good for your muscles, you're wasting your time if it's the first thing you do. I talked to Dr. Brian Parr, professor at the Dept. of Exercise and Sports Science at the University of South Carolina Aiken, who explained this misconception and what you can do about it:

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

I'm still amazed by all the things some people just don't know. Script-kiddies often refer to Metasploit if someone asks them how to hack a computer because they think there's simply no other way. Well here I am today trying to increase your set of tools and -of course- skills.

This video tutorial shows how to use a Roarockit Thin Air Press for teaching deckmaking. The glueup is done in one session. See how to build a skateboard with the Roarockit Thin Air Press!

Before starting a boxing training session it is important to wrap hands properly. A boxer's hands are useless if not properly cared for. Learn how to wrap hands in this boxing video tutorial.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Safari's private browsing mode on your iPhone won't sync to other Apple devices or remember your search history, AutoFill data, or visited webpages. Still, it doesn't stop anyone who accesses your iPhone from opening your private tabs. If you don't want anyone snooping through your private tabs, use Chrome instead so you can lock the tabs behind biometric authentication.

It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional and physiological well-being with your smartphone.

Let's be honest, nobody enjoys doing cardio — they tolerate it. That dreadful, loathsome feeling you experience when you're doing cardio workouts isn't unique to you, it's almost universal. Sure, it gets easier the more you do it, but there are some ways to make it better now.

This week's Magic Leap Lumin OS update contained a number of goodies, including iris authentication, and a way to stream to Twitch from the device.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.
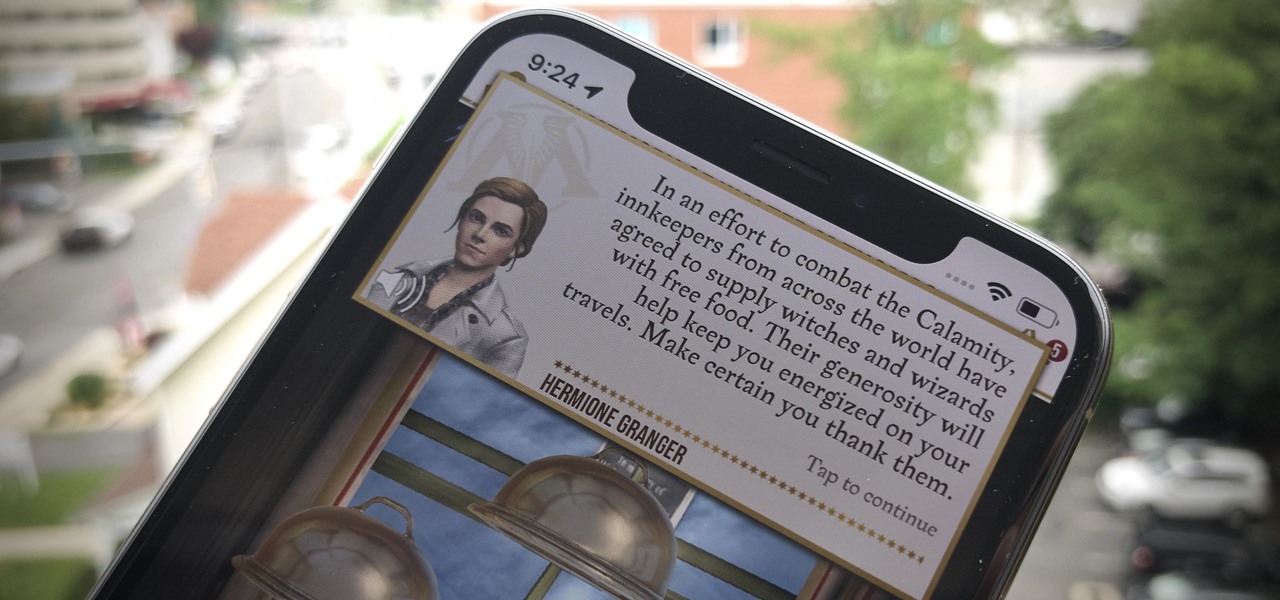
We Harry Potter fans all remember Hogwarts students pulling Mandrake Roots in the greenhouses in Chamber of Secrets. Well, in Harry Potter: Wizards Unite, we now have an opportunity to work in our own Greenhouses, as well as dine inside Inns scattered throughout the map. Let's take a look at how these two establishments help you along your magical AR journey.

Comparing the present-day states of the consumer and enterprise sectors of augmented reality is like evaluating the merits of sports car versus work trucks. Like consumer AR, sports cars are sexy and exciting, but perhaps a bit impractical at times. On the other hand, enterprise AR is utilitarian, but it gets the job done and, in the long run, pays for itself.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.