Animation controls run on the bottom of the screen. The time slider is the most important control for designing frames in Maya. Playback is exactly intuitive. This is a basic overview of Maya animation protocol and a lesson in using Maya tools.
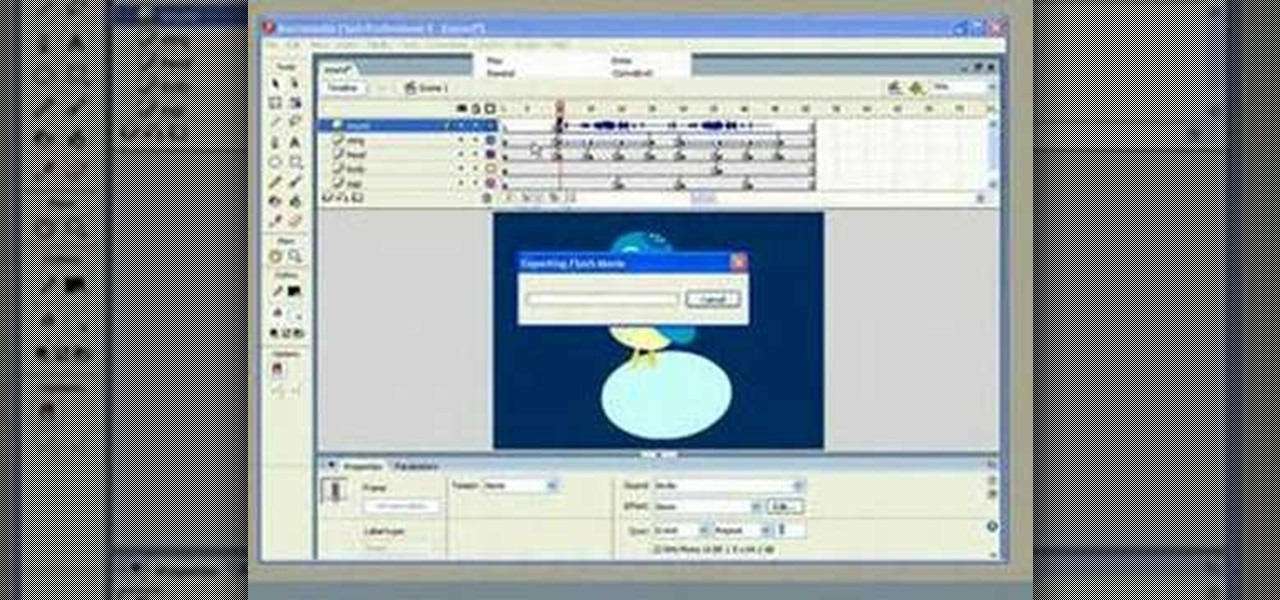
Adding sound in Flash is a simple process. Add sound files without even compressing them in the original import. You can import a .WAV file into a Flash.
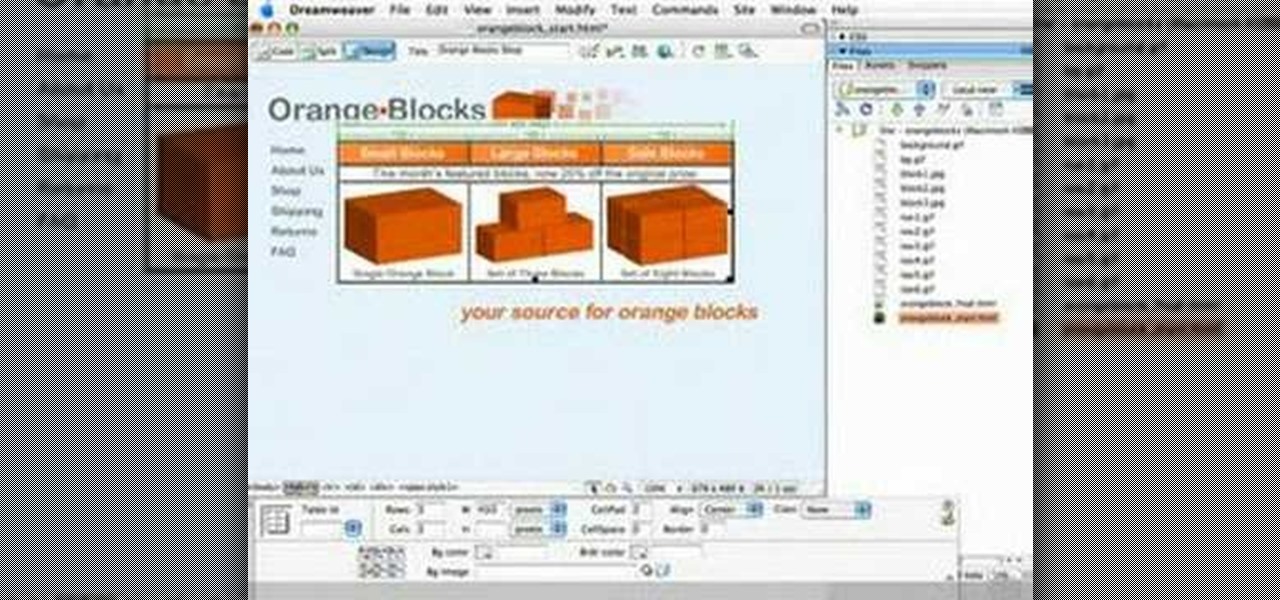
Check out this tutorial video from Sessions Online Schools of Art & Design's "Dreamweaver I" course. This is part of Sessions' Web Design certificate programs.
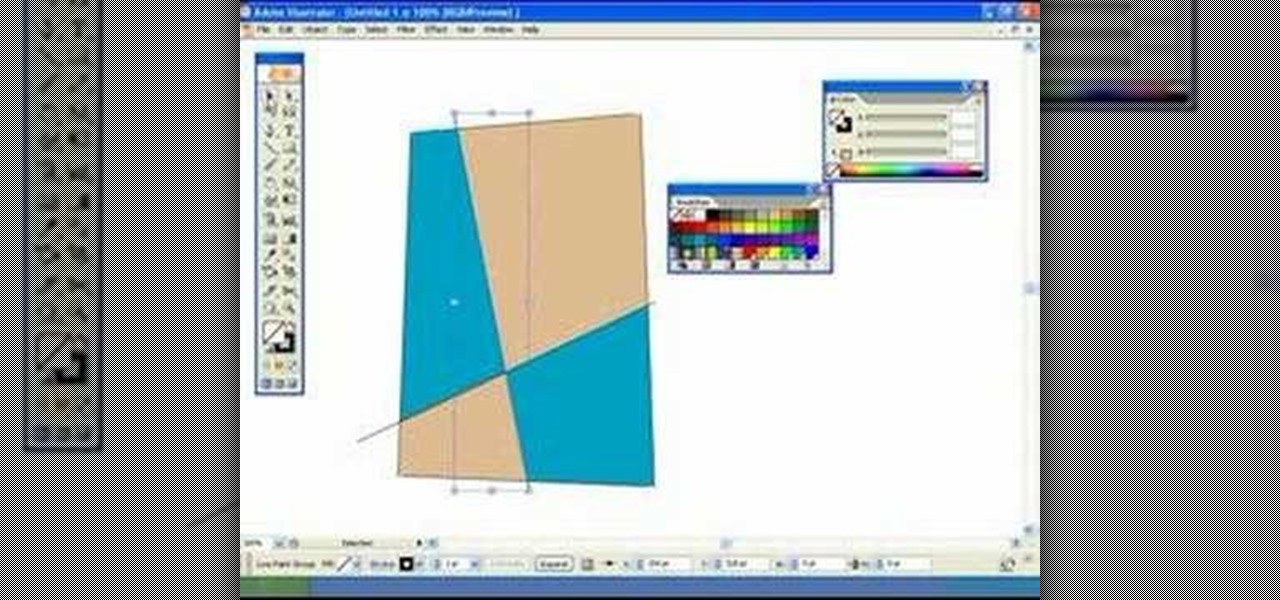
This tutorial will show you how to use live paint in Illustrator. Using live paint in CS2 recognizes empty spaces even those with gaps.

Want to close Firefox without losing all your tabs? Now you don't have to wait for it to crash. Watch this software tutorial video to learn how to turn on session restore. Turning on session restore will allow you to keep your tabs between Firefox sessions.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

While maggots living in human eyeballs isn't necessarily a problem in the states, it could happen to you one day if a fly decides your warm eyeball is a suitable place for its larvae. If this rare event should happen, before you start gouging your eyeball out, remember this trick from National Geographic explorer and engineer Albert Lin and everything will be okay.

Accidentally leave your Gmail open on a public computer terminal? Don't fret. You can have Gmail sign out any unwanted sessions with a click of the mouse. This free video tutorial from the folks at CNET TV will show exactly what to do. Protect your Gmail email account and log out any unwanted sessions with this how-to.

Creating curves with the pen tool in Adobe Illustrator is a good challenge. Check out this video on both drawing and editing with the pen tool. Click once in a place and then drag. This pulls out the direction handles.

Before you can get started recording or mixing in Pro Tools 9, you'll need to create a new session for your project. This free video software tutorial from Lynda presents a complete and thorough overview of the process. Whether you're new to Pro Tools or just new to Pro Tools 9, Avid's first native, software-only version of their popular Pro Tools DAW, you're sure to find much of value in this brief video.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

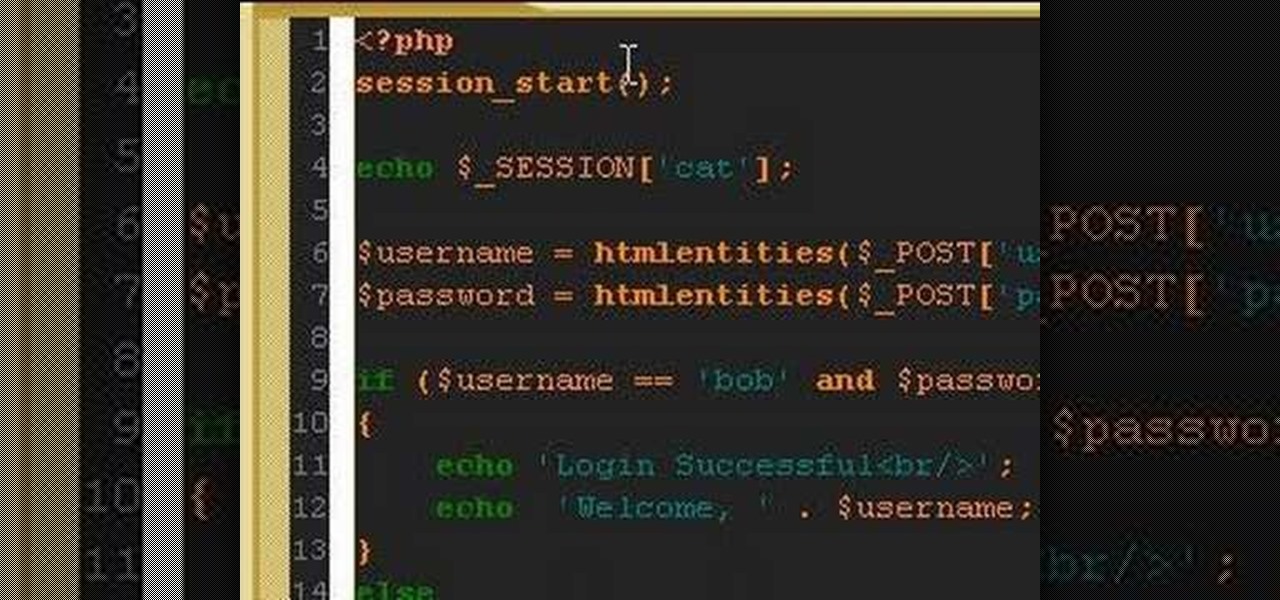
In this clip, you'll learn how to create a session class with PHP to track users on your website. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look.

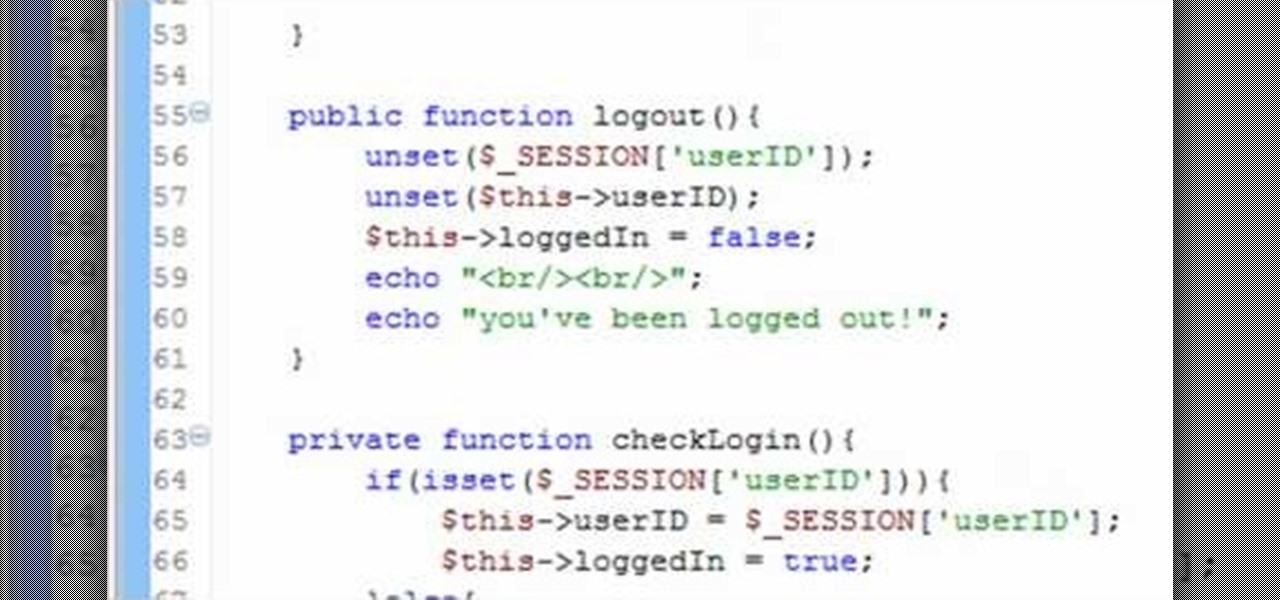
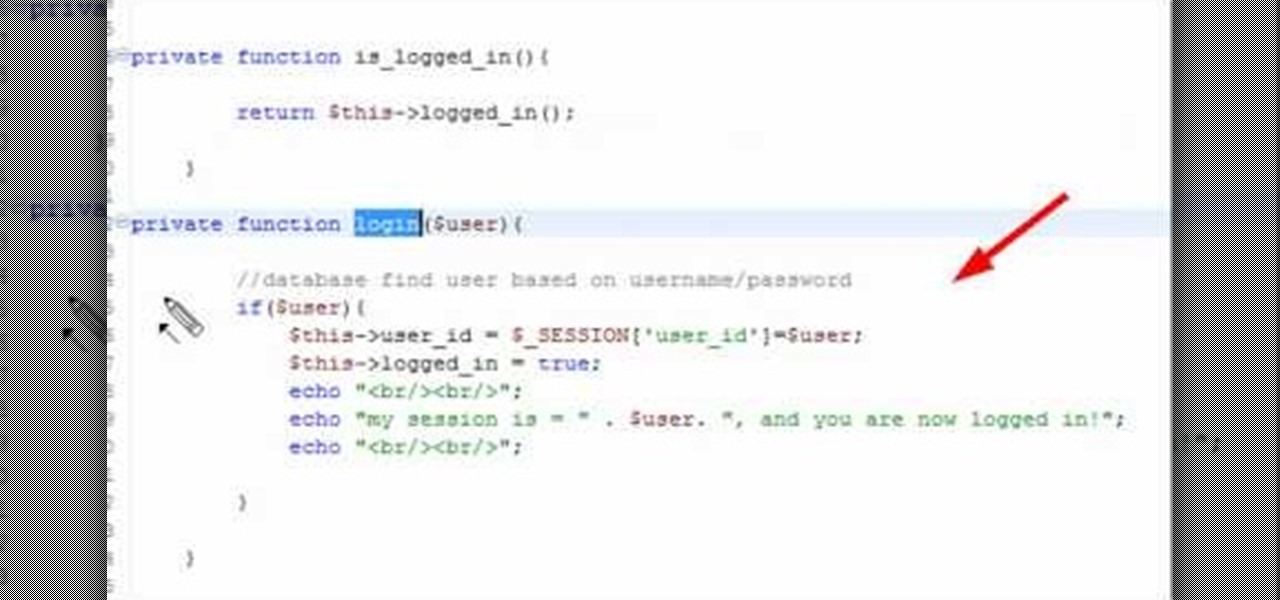
In this clip, you'll learn how to create a ogin (or log-in) session class with PHP. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look.

You can kill the x in Ubuntu with dontzap. Its really convenient if you like it. First thing you need to do is to download this package called dontzap. Now you can run the command sudo dontzap -d, it will disable that feature that Ubuntu uses and it will let you kill x by just pressing the ctrl + alt + backspace. It is really simple as that and there is no chance that you accidently pres the ctrl + alt + backspace and kill your x session. So after that you need to reboot your computer and you...

This session is about page view sharing. Click collaborate, send collaborate live. It works with Acrobat. It opens a live chat session. Log in with Adobe ID. You can invite others to collaborate. Click to select name, attach a file and send an email. File can be saved on Acrobat. Access can be restricted to those who are invited. Collaborate live panel opens. You can open the invitees computer. Invitee needs to sign in. You have the ability to chat. Start page sharing. Pages are synchronized....

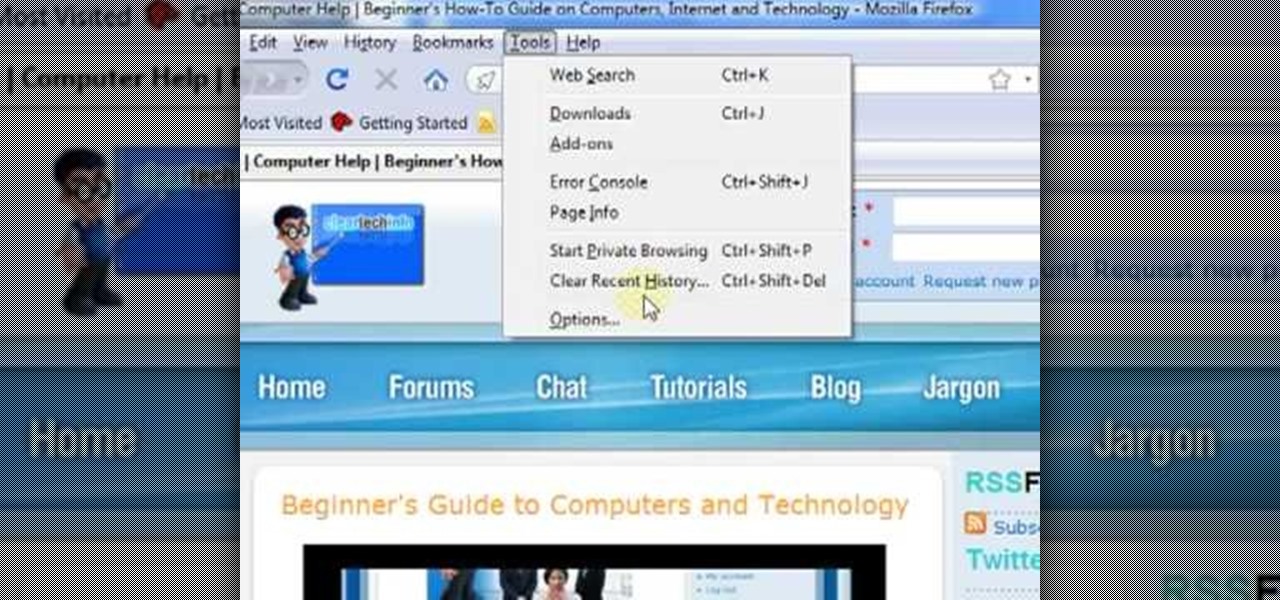
In this ClearTechInfo video the instructor shows how to use the Firefox 3.5+ private browsing feature. To use this feature you need a Firefox version 3.5 or more. Now to start a private browsing session go to tools and click on Private Browsing button. This will trigger a new private browsing session that will now store any browser history, search history or any temporary internet files for that session. But this will still allow you to download and keep files and also add bookmarks. This vid...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to session hijack with a pineapple.

Check out this video on creating type areas and paths in Illustrator. This uses more than just text boxes. You can adjust the font, color and area using the area type tool.

Sometimes you want to burn to a CD-R multiple times to make the best use of the available space on the disc. In Mac OS X Leopard, you can create what's known as a multi-session disc and burn to a CD-R multiple times. For more, and to learn how to create your own multi-session discs, watch this video tutorial from Apple.

DOZ explains the setup for a tattoo session and steps you through it while he tattoo's his own upper right thigh.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

A PHP programming tutorial on creating login sessions to keep users logged in.

After publishing two batches of videos from its L.E.A.P. developer conference, Magic Leap has made the session on Seedling from Insomniac Games available to the public.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Interested in making Firefox save your browser state more frequently to protect against crashes and outages? This clip will show you how it's done. It's easy! So easy, in fact, that this handy home-computing how-to from the folks at Tekzilla can present a complete overview of the process in about two minutes' time. For more information, including detailed, step-by-step instructions, take a look.

In order to get add-ons and plug-ins for Google Chrome, you to go to Chrome Plugins. Type the address into your browser. Then, press Enter. Scroll down the list. Choose and add-on that you want: for example, Click & Clean. Click on the one that you would like to choose. Find "Download Latest Version" and click on it. Wait for it to download and click on it. There are lots of options. Click & Clean allows you to clean your browser with only one click. Session Save allows you to save the sessio...

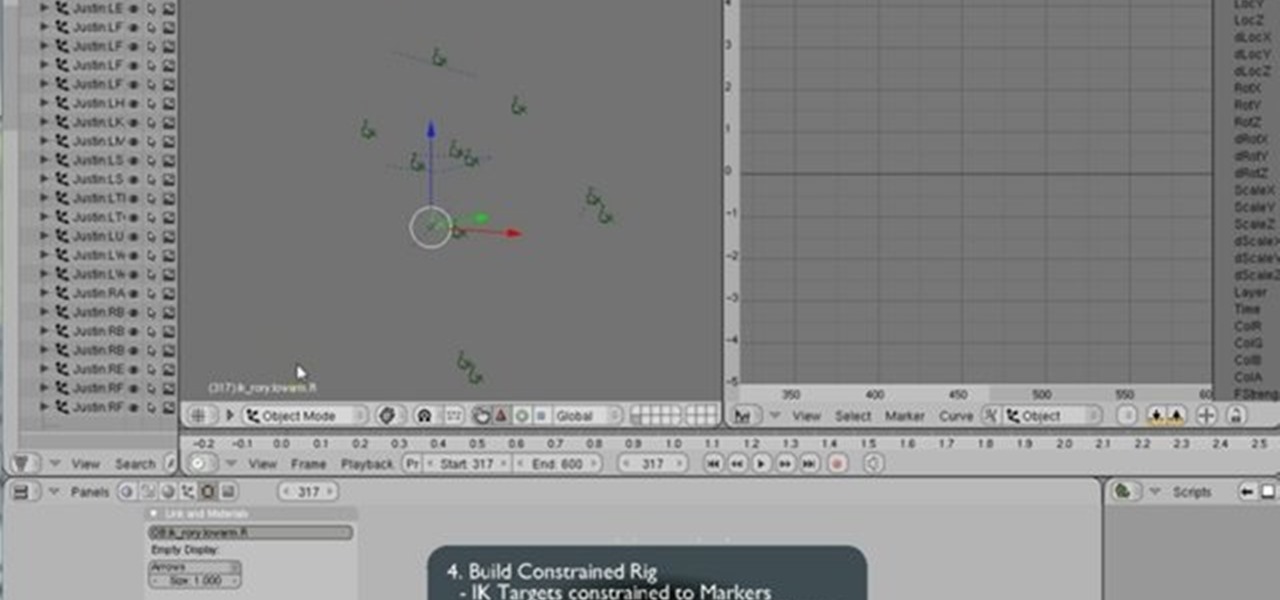
In Blender, you can build up a library of Actions, Poses, and IK Target motion based on real-world motion capture sessions. These session files are freely available and cover hundreds of everyday motion. Use these libraries to study and augment your hand-animation skills, or use directly to animate your character. Whether you're new to the Blender Foundation's popular 3D modeling program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're s...

Take advantage of this unique opportunity to prepare for the Advanced Certification exam in an interactive day long, live session with an Advanced Certified Pro advisor! Get a jump start on becoming a QuickBooks Advanced Certified Pro Advisor. Learn how advanced certification can help you grow your business and continue to improve your skills. You will understand what advanced certification is, why it is important to your practice and how it can benefit you and your clients. Learn how to effi...

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

You always wanted to make an undetected payload and make it look legit, Well this is what this tutorial is about, You're going to learn how to backdoor any (Unfortunately only 32-Bit) software, Let's get into it

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

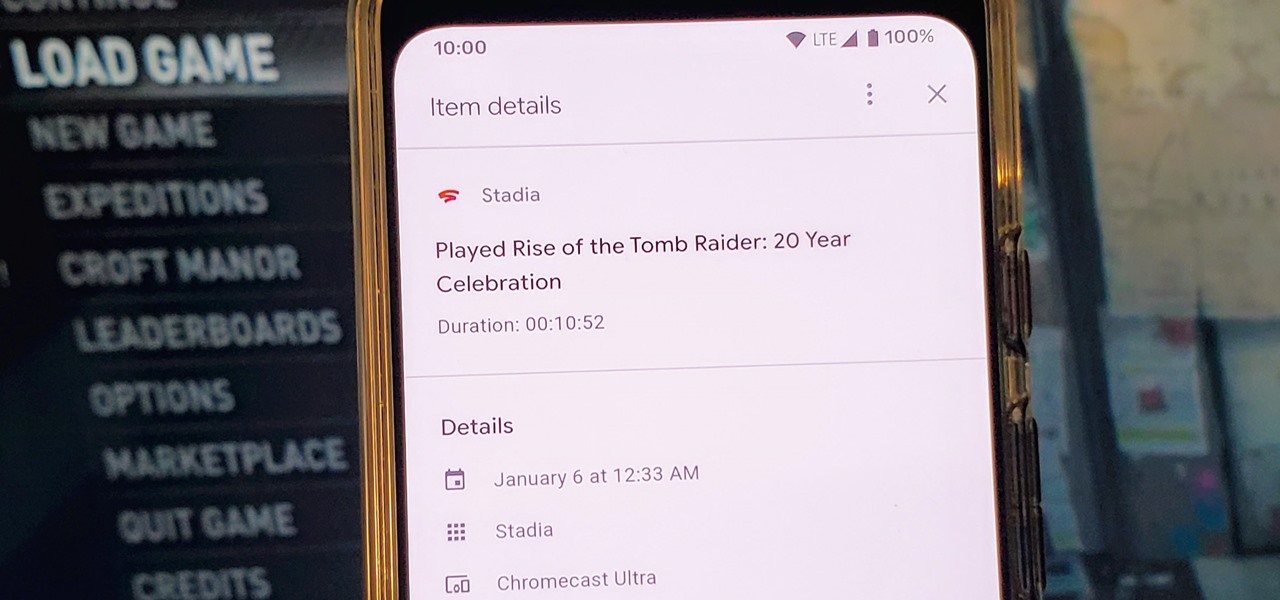
Since Stadia is an early access game streaming platform, Google is still working on bringing big things to the table. You can expect wireless Stadia controller support for many more devices, high-quality 4K gaming on all Chrome web browsers, and more Google Assistant features. They also managed to silently sneak in a way to keep track of your Stadia gaming sessions too, which is pretty handy.

There's nothing wrong with indulging in guilty pleasures on Spotify every once in a while — we all need a little Coldplay and Creed in our lives. The only problem is, all of your friends and family might be watching. Anyone that is following your Spotify account can potentially see what you're listening to, but there are several ways to hide this shameful and embarrassing activity from the world.

On Wednesday, in addition to uploading another batch of videos from its L.E.A.P. conference to its YouTube channel, Magic Leap also launched a new video series for developers called Spacebar.

Magic Leap's recent L.E.A.P. conference was free to all who registered in time, but if you weren't able to make the trip to Hollywood, the company just released video of some of the sessions that took place over the course of two days.