This video tutorial is about Android, and no it's not a robotic creature, it's a software platform and operating system form mobile phones and PDAs. The Android system is based on Linux and was developed by Google and the Open Handset Alliance. Code is managed in the Java language, but can be written in C also, although C is not officially supported. A lot of the new cell phone and other mobile devices will be running off of Android, so know how to use it.

Want to get rid of neck pain? Then try using massage as a pain reliever. Follow along with this diet and health how-to video to learn how to massage pain in the neck. When massaging the neck it is important to focus on all sections of the neck like the lateral and anterior sides. With a few thirty minutes massage sessions you notice the pain in your neck start to go away.

Professional BMX rider Ben Snowden teaches you how to do a 540 on a box jump landing, quarter pipe, and vert ramp. He also throws down some extra moves at the end of the video tutorial in a bonus solo riding session. So, if you want to be an awesome BMX bicycle king, just learn how to do a 540 trick on a BMX bicycle. Ben Snowden will tell you all about it, but he recommends you already know how to do a 180 or 360 spin on your bike.

Congratulations, you've made it deep into the middle of flu season! If you're reading this, you're either a very smart preemptive sick day prepper, or already in the throes of fighting off a cold or flu situation.
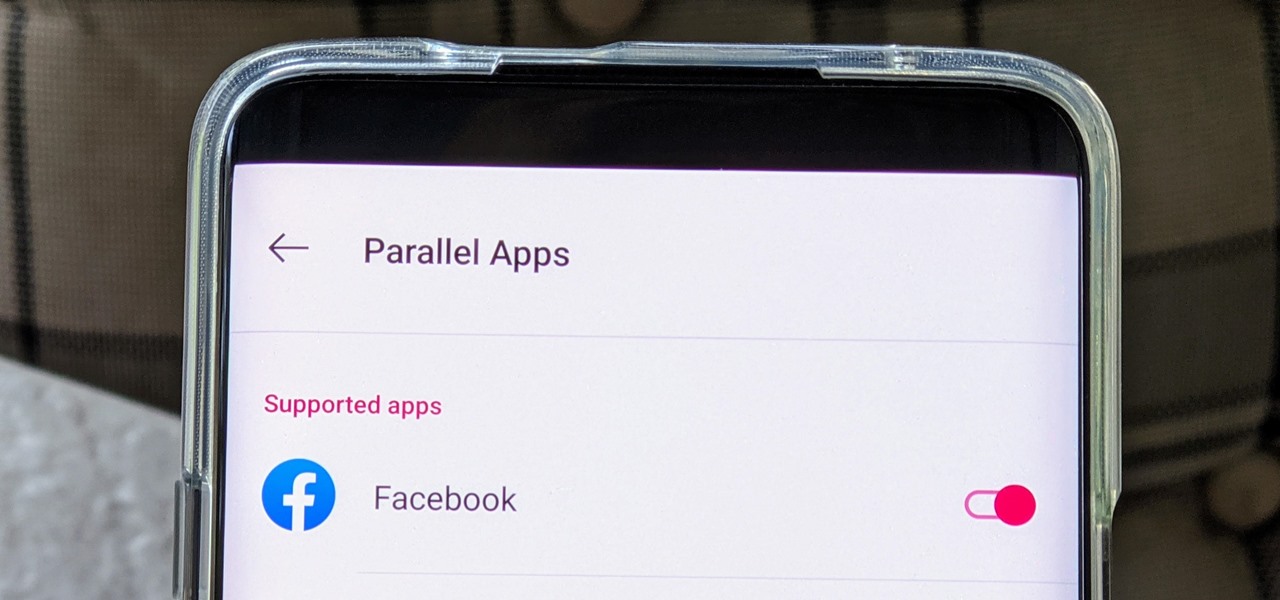
The Facebook app only supports one account being logged in at a time — but what if you need one for work and one for your personal life? That would normally involve logging out and logging in every time you need to switch accounts, but your OnePlus device offers a much better solution.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

After Apple unveiled ARKit 3 at WWDC on Monday, Unity Technologies wasted little time on ensuring its developers can take advantage of it.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

If you've been debating on whether or not HTC's new virtual reality headset, the Vive, is worth the $800 price tag, then you'll be able to find out for yourself soon enough.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

At the beginning of regular gameplay in Grand Theft Auto 5, you play the role of Michael robbing a bank in North Yankton with his accomplices—shooting police and evading a high-speed train in the process. While you do revisit North Yankton during regular gameplay in Los Santos, it's strangely unavailable for online play.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

You aren't just born with broad Stallone shoulders and arms, gentlemen. Of course we know you wish you never had to work to get those tight, chiseled arms and shoulders, but even the best of the best - that's right, including Stallone - have to work what their mama gave them to keep in shape.

In this tutorial, we learn how to remove stretch marks with lasers. The laser treatment is the most effective for removing stretch marks. This will turn the purple marks lighter, and once they are silver/white, they will make those less apparent. The Affirm laser treatment is proven to be extremely effective to remove the stretch marks, and make them only noticeable under a microscope. It will take several sessions to drastically remove the stretch marks, but it will be worth it in the end. D...

This video provides a demonstration of how to beat the bosses of maps one through four of Epic Quest. The video game is an arcade style fighter where you lead teams of three creatures into battle. The first boss is a solitary enemy, easily taken down. The boss pair on map two is only slightly more challenging. The three squid creatures on map three are easily taken down, if you are level 31. On map four, you should be more careful. This boss team requires the use of several potions and healin...

In this photography tutorial video, the self-appointed "Prince of Cheap" shows you how to use natural light and enhance it with continuous fluorescent light for some really killer headshots that stand strong! This photographs are really strong. In this 5 minute clip, David explains his thought process while you watch one of his garage shoots that lead to great quality and many "How'd he do that?" exclamations. This time you'll be able to see him on his session! How much can you learn in 5 min...

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Heavy Water & Light Ice Experiment. What happens? Ice floating over vegetable oil but it decreases in baby oil.

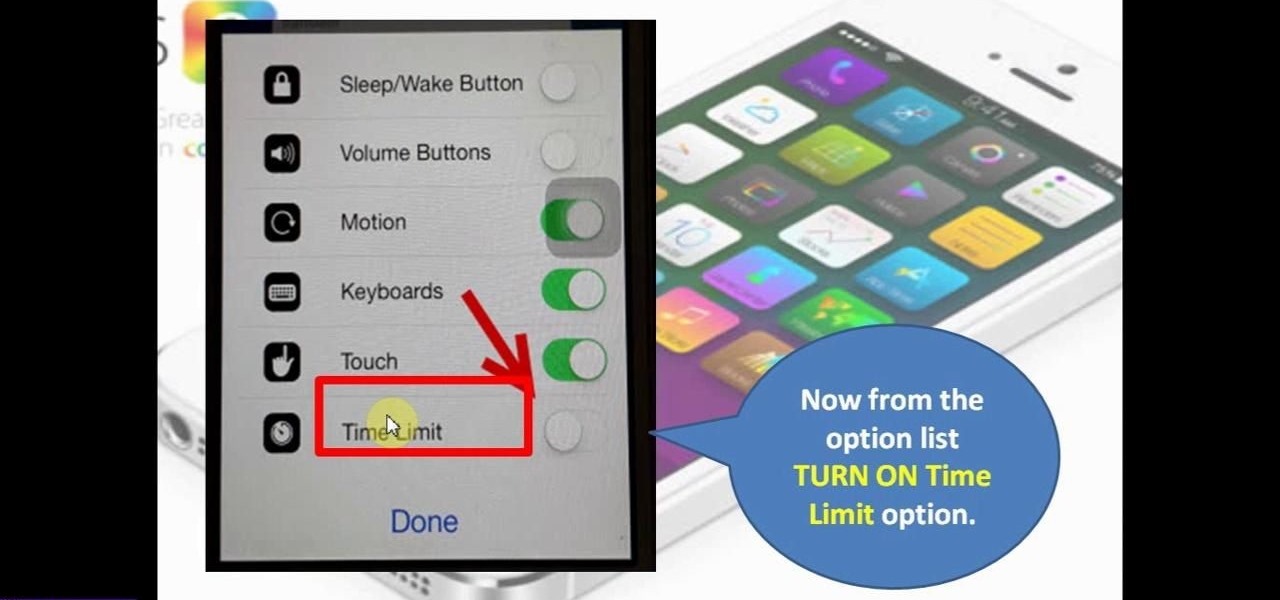
This video will show you how to set time limit for your children games in your iPhone or iPad. This will restrict children from excessive use of your iPhone or iPad. When this time limit is over, the game your child is playing will be stopped automatically. They will not be able to continue playing games until you start a new session for them. So please watch the video and employ it in your phone.

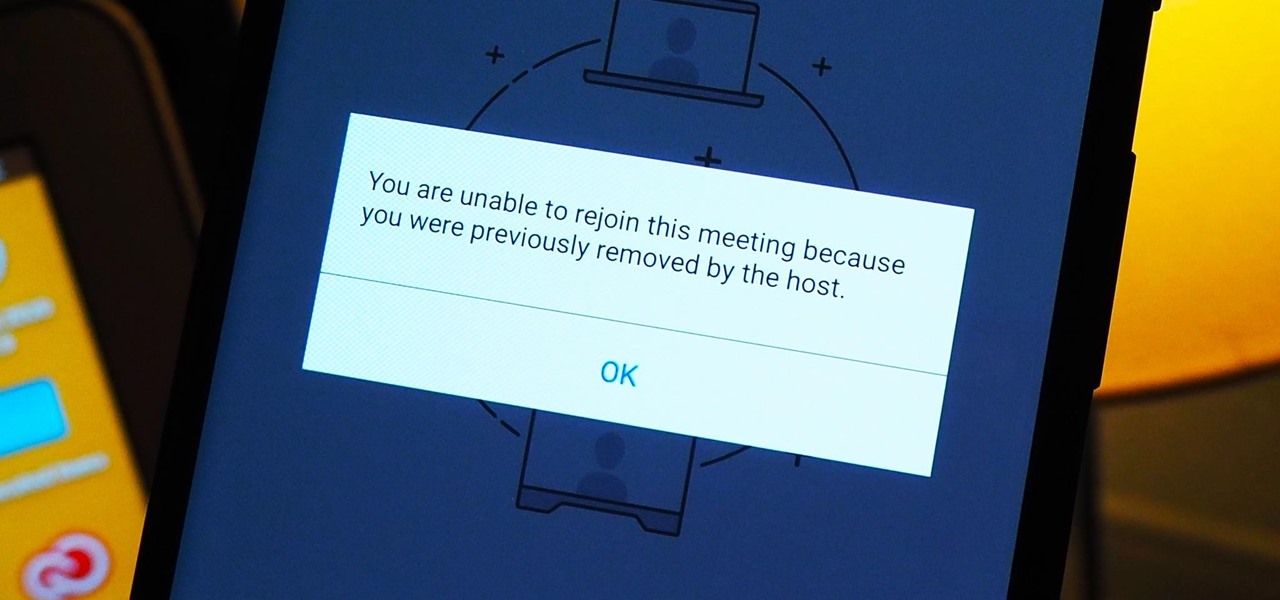
As more and more people use the video conferencing service Zoom, the chances of trolling behavior and attacks only increase. But it's not just "Zoombombers" you need to worry about. A heated discussion between family, friends, or colleagues could turn sideways real quick, and sometimes the best course of action is to remove the participant from the group video meeting altogether.

The business world is currently figuring out how to deal with the coronavirus crisis, with many offices opting to work remotely for at least the next few weeks as a safety precaution. Predictably, this has thrown remote meeting software back into the spotlight, especially augmented reality solutions.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

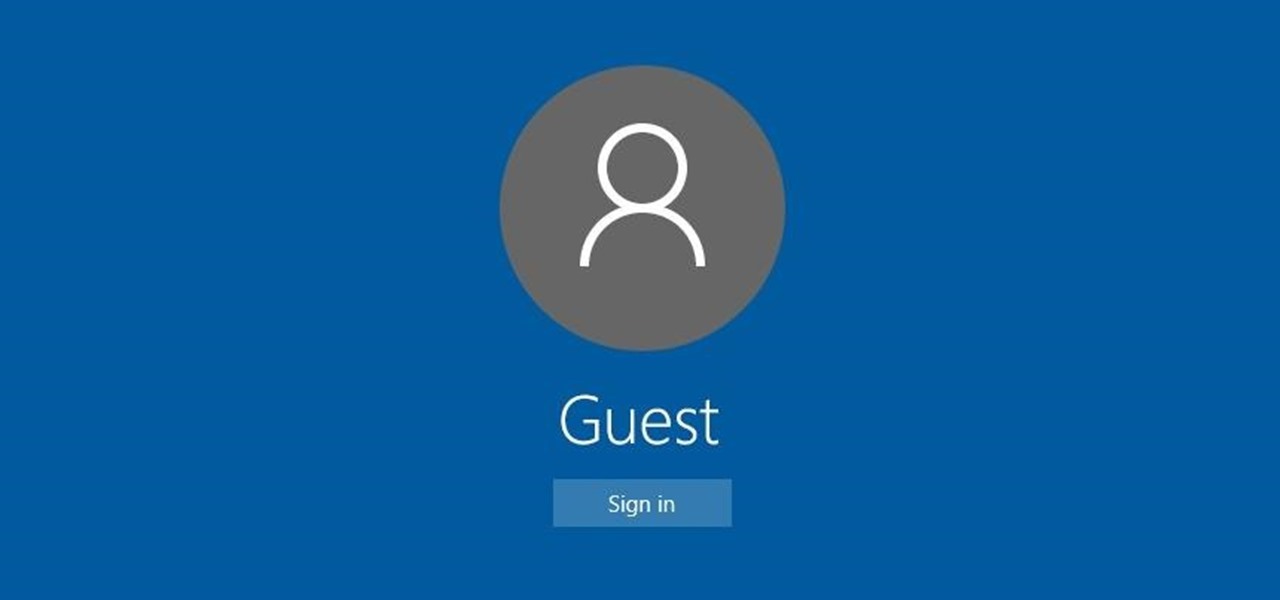
For reasons unknown, Microsoft decided to change the way the Guest account feature in the new Windows 10 operating system works. In previous versions, the Guest account feature allowed you to set up a limited account for other users so they don't have access to your important documents and settings. Now, the process requires assigning an email to a new account and configuring share settings.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

How many times have you heard someone utter the phrase, "Now, let's break into groups"? From classroom discussions to workplace think tanks, gathering into groups to generate ideas is common practice. These forced get-togethers are intended to encourage creativity and unique thought, but they can actually do the opposite. More often than not, group brainstorming is annoying rather than encouraging, and these group sessions can actually be detrimental to your productivity. Getting together har...

For the last three years, Apple has hosted its Worldwide Developers Conference at the San Jose Convention Center, but thanks to the COVID-19 pandemic, WWDC 2020 is now an online-only event. So what can you expect from the new virtual format and when and how can you watch the keynote and developer sessions?

It's not hard to let the new SARS-CoV-2 strain of coronavirus put pressure on our minds. Fear of catching COVID-19 is never far from the topic of conversation. But it doesn't have to be that way. If you're struggling with anxiety, stress, depression, or any negative emotions due to the virus's effect on our lives right now, you might find some solace in meditation.

While Unity is already the leading 3D engine for augmented reality content in terms of volume, the announcement of Project MARS, a new augmented reality authoring tool, at Unite Berlin in June promised to expand AR development to a whole new audience of designers and other non-coders this fall.

With barely a whisper of augmented reality during the first day of its developer's conference, Samsung came out swinging on day two with the introduction of its version of the AR cloud and a partnership with Wacom that turns Samsung's S-Pen into an augmented reality magic wand.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Magic Leap just did something it didn't do during its recent Twitch hardware demo: show us some new demo footage of what augmented reality really looks like through the Magic Leap One.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

During Google Developer Days, taking place now at the ICE Congress Center in Krakow, Poland, an introductory session on ARCore provides some insights on how the platform operates.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

I'm lucky enough to have internet access on my laptop practically everywhere I go because of my mobile hotspot plan. All I have to do is enable the personal hotspot feature from my iPhone and I can surf the web on any Wi-Fi enabled device. But of course, there's a catch.