Don't even think about posting a fake camping picture to Instagram because this account is committed to calling you out. The account entitled @youdidnotsleepthere is exposing fake pictures posted by travel bloggers to its over 36,000 followers.

Now that Fyre Festival co-founder Billy McFarland is charged with fraud, this is the perfect time to list off those top 15 influencers who promoted tickets to the disastrous event to their loyal followers, right?

There are a few ways to do this, but I'm going to share with you the easiest way that I know how to share an image on Instagram Stories that isn't currently in your Stories queue.
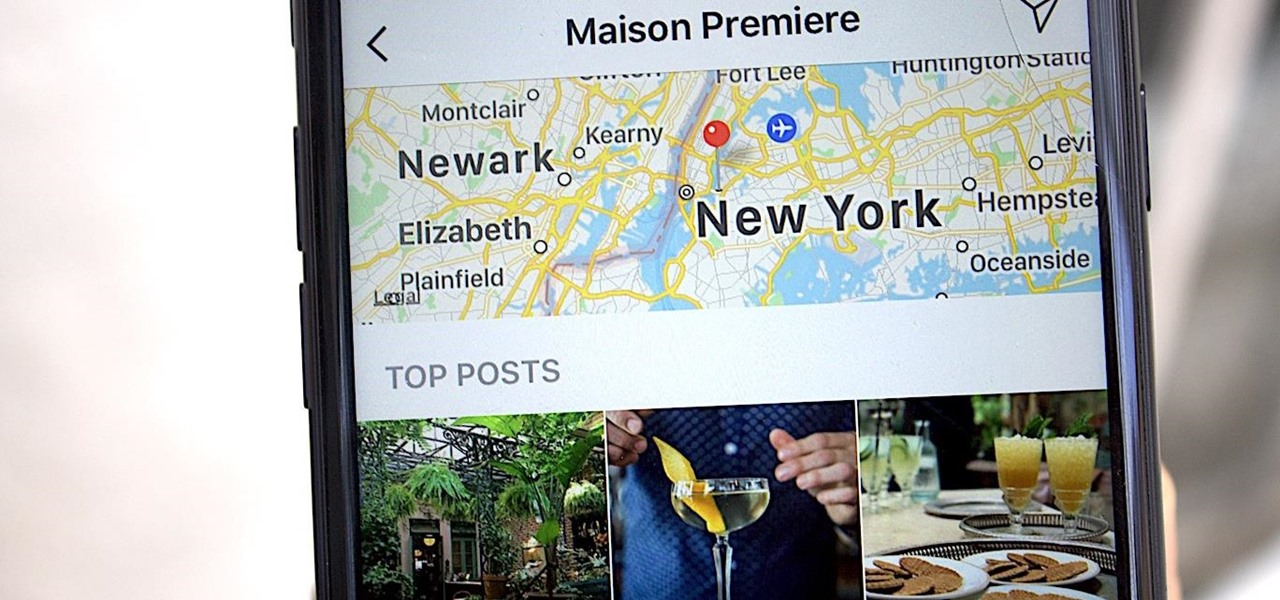
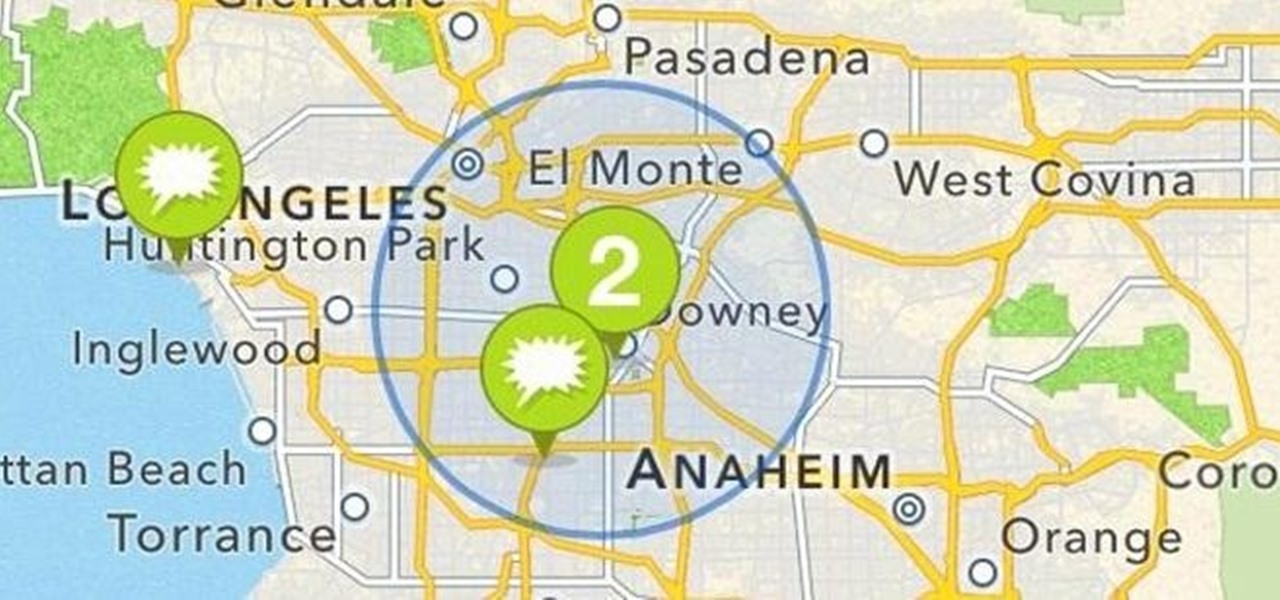
Geotagging your location on Instagram is one of the most undervalued ways to generate traffic to your profile. The beauty about adding your location to your IG posts is that it allows you to be seen by other users than the ones that already follow you.

It looks like all the unregulated fun and games we were having promoting products on Instagram is about to get, well ... regulated. According to a new report by Mediakix, 93% of celebrities on Instagram are not in compliance with the Federal Trade Commission when it comes to posting paid content.
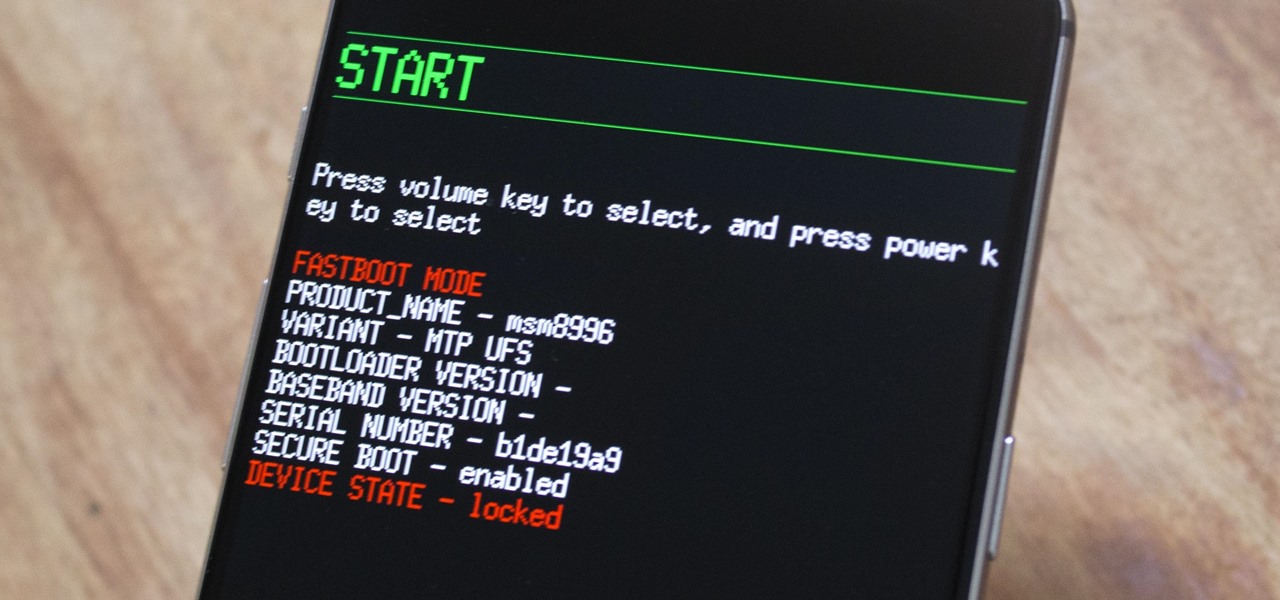
The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that they have an unlockable bootloader, receive timely kernel source releases, and are actually quite easy to root.

The Washington Post believes augmented reality adds an extra layer to stories, and they're doubling down on that belief by adding in new AR features into their already popular "rainbow" news (iOS and Android) and Classic (iOS and Android) news apps.

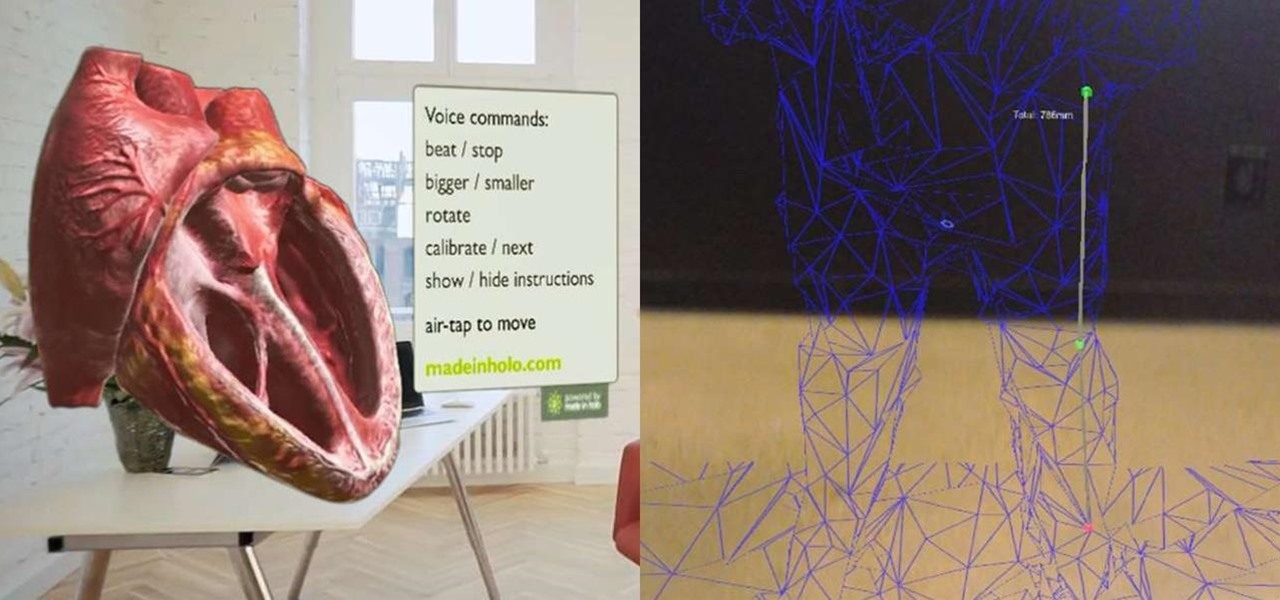
While all of my previous Have You Seen This? posts have all focused on individual HoloLens apps in the Windows Store, this time I'll be sharing a couple at once. These holographic applications are really simple in scope, so there is not a lot to say about them, yet they are interesting enough for me to want to share them with you.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

Google Maps, in conjunction with the Android operating system, is a powerful tool for navigation that is often underutilized. While it's no secret that it can get you to wherever you're going and back, some of you might not know that you can use Google Maps without even having to touch the screen. Not having to touch your display means you can concentrate on other things, you know, like driving or eating that jelly-filled donut.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

Google's Chrome browser is evolving into a very powerful platform. Not only can it be used to view your favorite website or mirror tabs to your Chromecast, but now that it has an App Engine, more powerful tools can be run within Chrome.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

The dock has been a staple of Mac OS X since its creation and not much has been needed to improve its functionality, but when you add theming to the mix, you can run into some issues.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Since the days of Friendster and MySpace, social media platforms have taken leaps forward, revolutionizing how we live our lives by changing the way we communicate with others. Not only has social media become a catalyst for major uprisings around the world, but on a personal level, it connects people together in ways that were unimaginable even 10 year ago—no one was taking pictures of their brunch to share with the world in 2004.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

This video will show you how to target your audience for Facebook post. You could set country, language, age group, qualification, etc. for watching your post. Watch the video and follow all the steps. Employ the technique in your Facebook account.

This video will show how to target your facebook post for a specific audience. With this tutorial video you could target a set of audience who has interest about the post.

When Google introduced their new launcher alongside the Nexus 5, one of the most innovative features was the "always listening" voice search, meaning that at any time you were on your home screen, triggering a Google search was as simple as saying "Okay, Google."

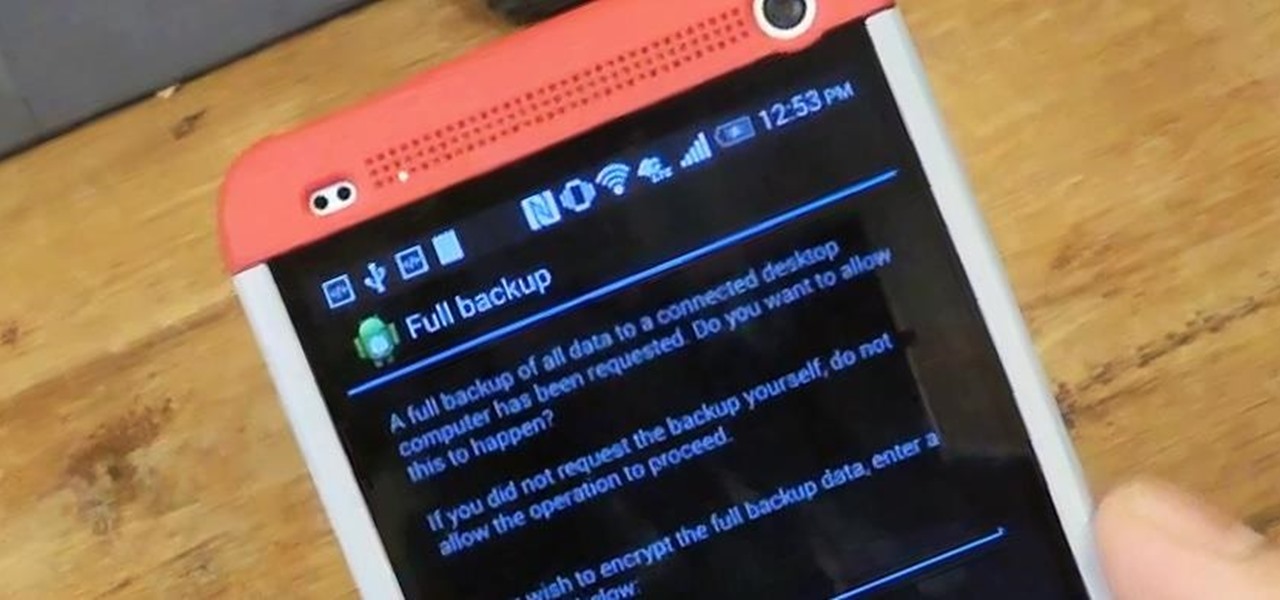
Today, I'm going show you how to back up all of your apps and their data using Android Debug Bridge (ADB)—an essential function for all softModders. These commands will be especially useful when you are updating your version of Android, since they don't require a third-party program to run on your device.

The long standing popularity of 4chan has been due to the entirely anonymous setup. The site's anonymous community and culture has provoked media attention, in turn inciting larger audiences. On the other side of the spectrum is Facebook—popular for its connectivity and easily identifiable names. With the brush of keyboard stroke, you can be connected with your entire high school class in a matter of seconds.

Depending on what mobile device you own, you'll see something that says "via device name" next to the date of your post on Facebook. If you're device is not recognized, you'll simply see a "via Mobile" note, which is what happens when I post from my phone. If you allowed your iPhone to be called iPhone when you logged into the app, it'll show up as a recognized device on Facebook, and will post "via iPhone." Same thing goes if you have a Samsung Galaxy S3 or Nexus 7 or iPad. It could also jus...

How to remove a timber fence post the Uncle Knackers way...even if it is encased in concrete. After watching it you'll all want to go out to your back yards and start pulling down your fence, just for the hell of it! BE WARNED, there are near NUDE scenes in this video.

In this clip, you'll learn how to use the Voice Control feature on an iPad. Whether you're the proud owner of an Apple iPad or perhaps just considering picking one up, you're sure to benefit from this free video tutorial, which presents a complete overview of how to enable the Voice Control tool. For details, and to see what it takes to use iPhone-style voice commands on an iPad, take a look.

Want to switch between various open applications via keyboard shortcut? With Mac OS X and the app switcher tool, it's a breeze. It's so easy, in fact, that this home-computing how-to can presenta complete overview of the process in just over two minutes. For more information, and to get started using this essential window- and life-changing key command yourself, take a look.

For anyone who lives in a space that may frown upon making holes in the walls, or for anyone who may not want to take on such a task, there's a simple alternative to hanging curtains or drapes. And the answer is brilliantly simple.

This is a Tinkernut video cast. This video shows you how to control your computer (mainly games and miscellaneous programs such as Google Earth) using your webcam.

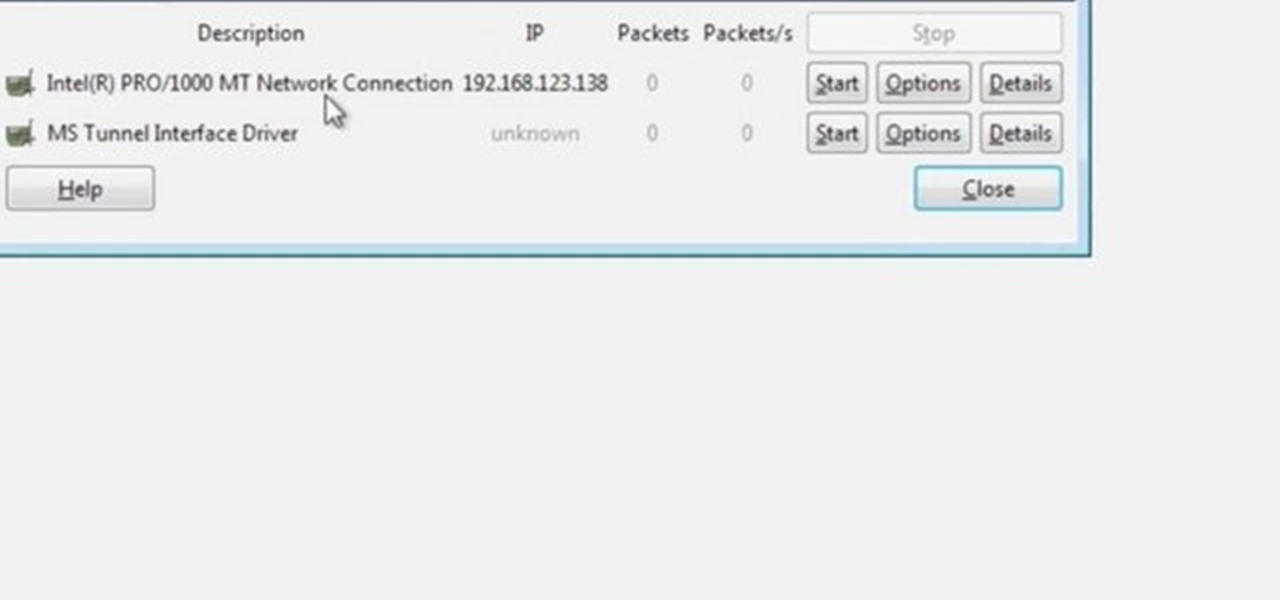
Wireshark is the world's foremost network protocol analyzer, and is the de facto (and often de jure) standard across many industries and educational institutions. This video tutorial demonstrates how to get the Wireshark packet sniffer up and running to do a capture as well as how to run a traceroute command. To get started hacking with Wireshark, watch this how-to.

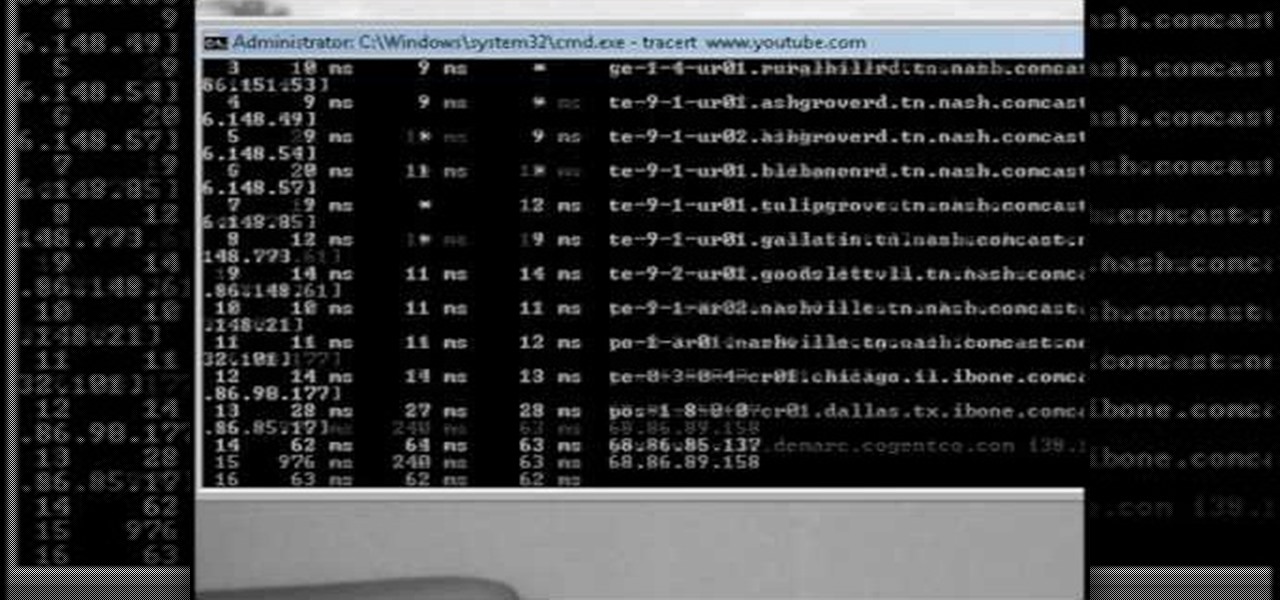
This video will show you how you can trace IP address or websites to a specific location using Windows command functions.

The tether command allows you to tether your camera to your Mac and capture images directly into Aperture. It's fast, easy to set up, and gives studio photographers immediate full-screen feedback while they shoot.

Blogger Jimmy R. demonstrates how you can embed hidden files into an innocent-looking JPEG image using the free 7-Zip and the Windows command line.

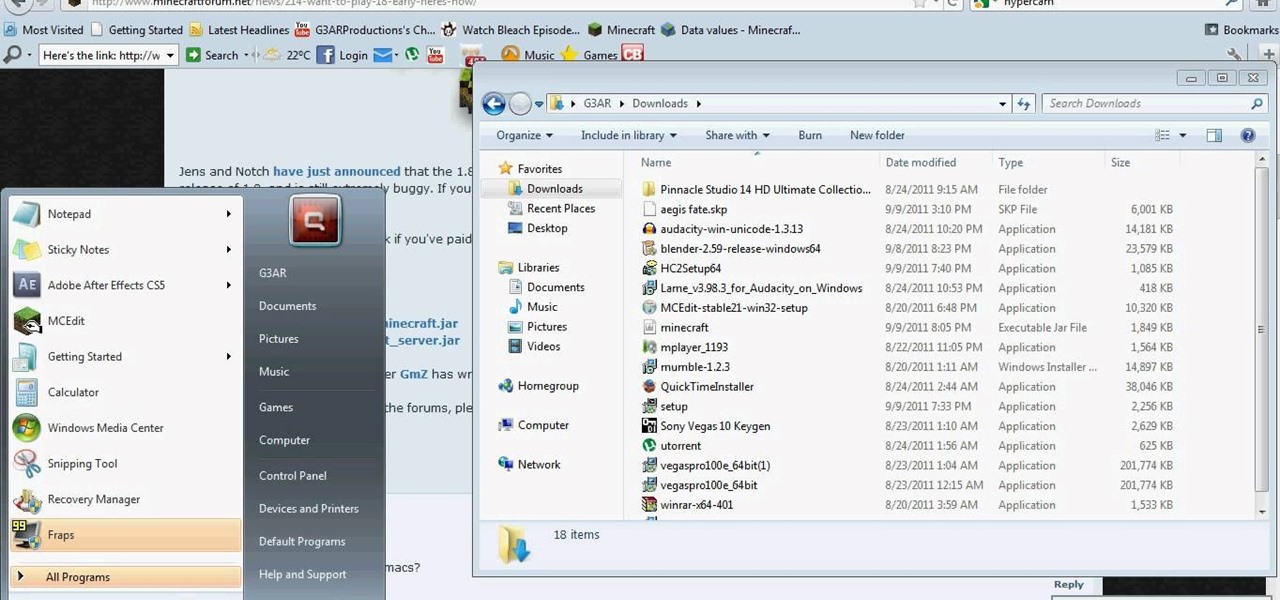
Notch posted the pre-release of Minecraft 1.8 before it got an official release. If you want to install Minecraft 1.8, take a look at this tutorial for instructions on adding the update to your Minecraft folder in Windows on your PC. You can download the pre-release on the Minecraft forums in this post.

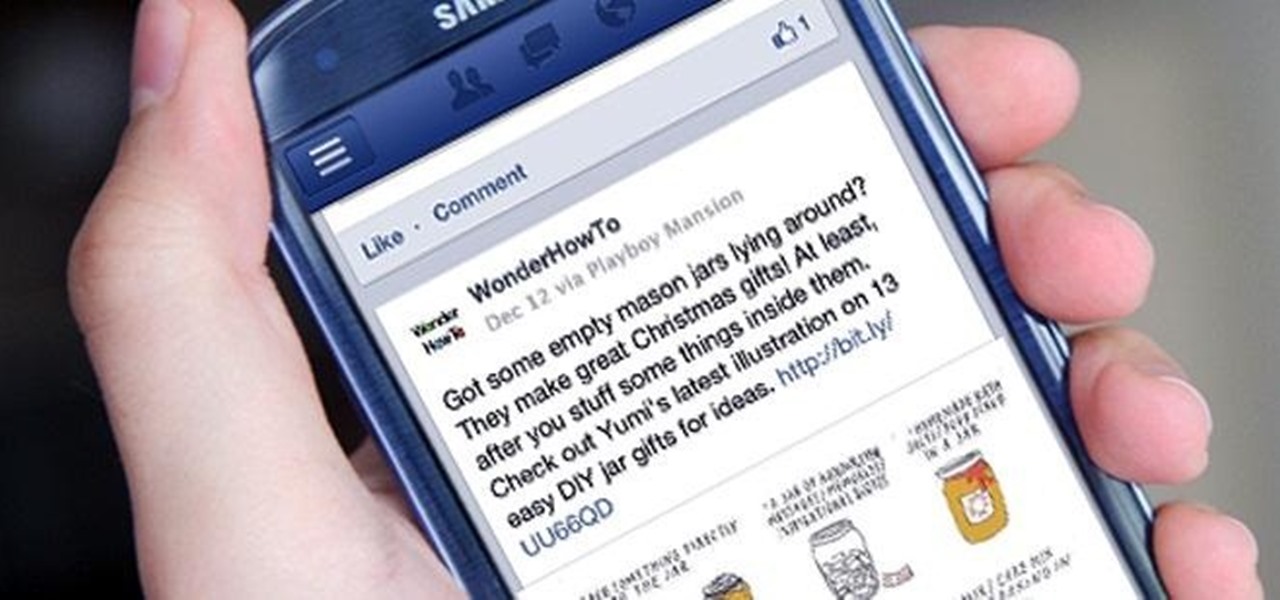
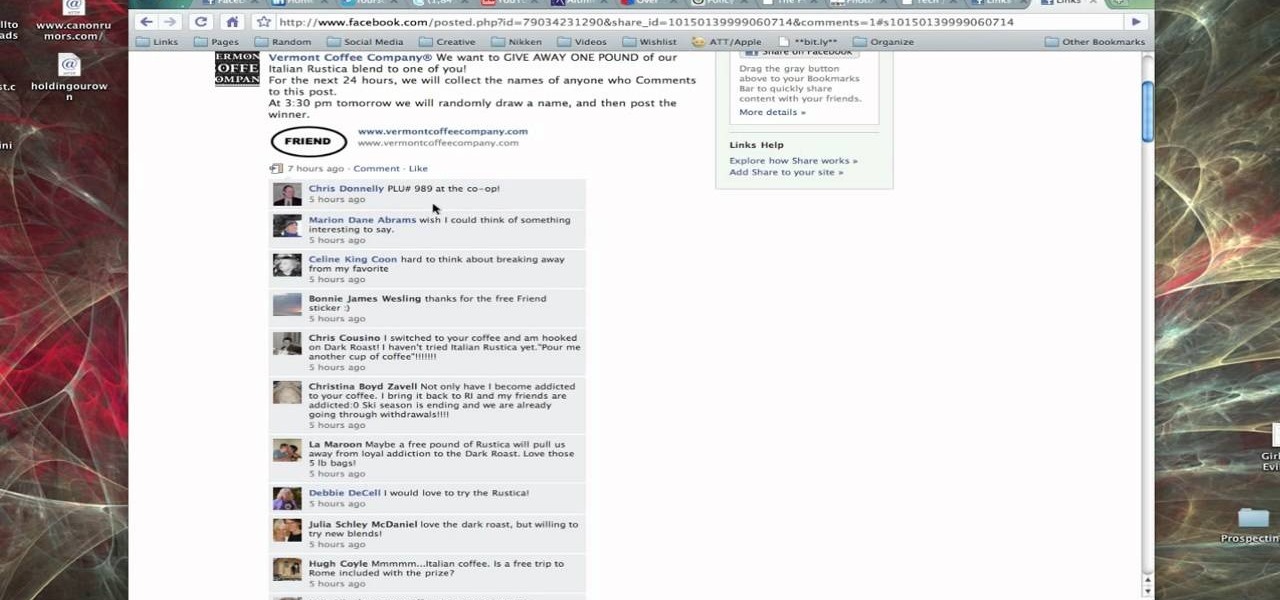
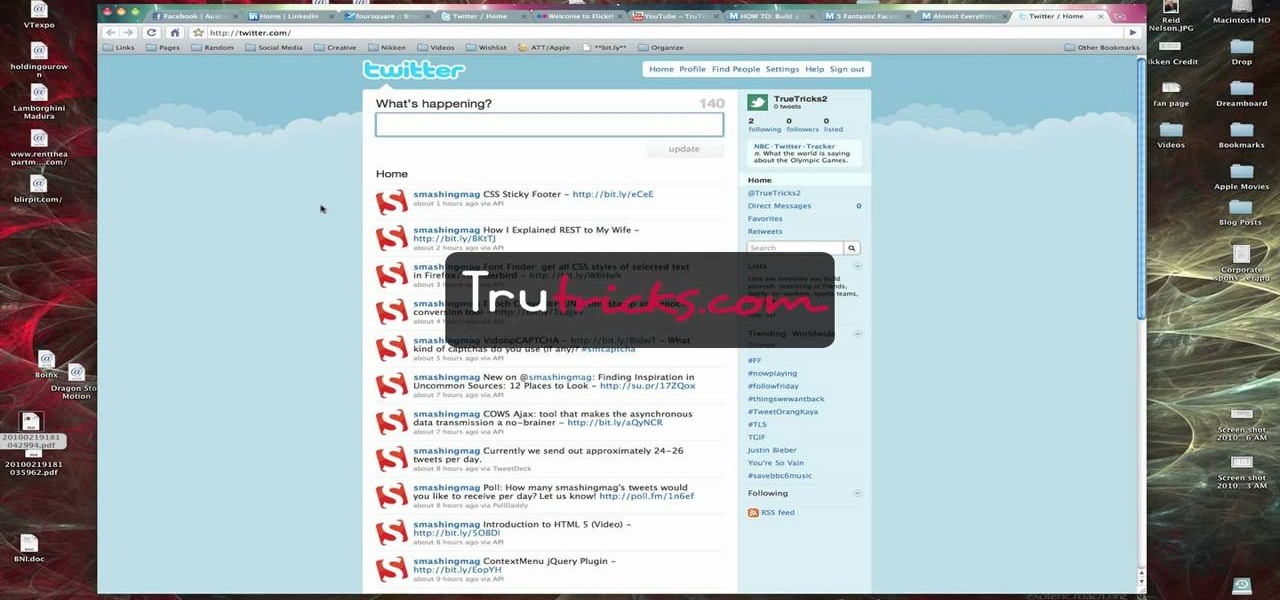
In this tutorial, Brian from TruTricks shows us an example of what Facebook can do to promote your business! One of the best ways to do this is to do micro giveaways on your Facebook. You don't have to give away something big, just something small that gives people incentive to post on your page and become a fan of your business! You will be able to see what people are posting on the page as well as everyone that is entered in your contest. This giveaway has given all the fans reason to parti...

Brian explains us how to use Twitter, one of the best social media networks out there. One thing to notice is that Twitter allows you to send text messages up to 140 characters. In the right corner you can see you account name and your avatar which can be changed from the settings menu. Twitter allows you to follow people and be followed by people. Basically when you follow people you will be able to see messages they post and when people follow you, they will see what you post. Twitter is a ...