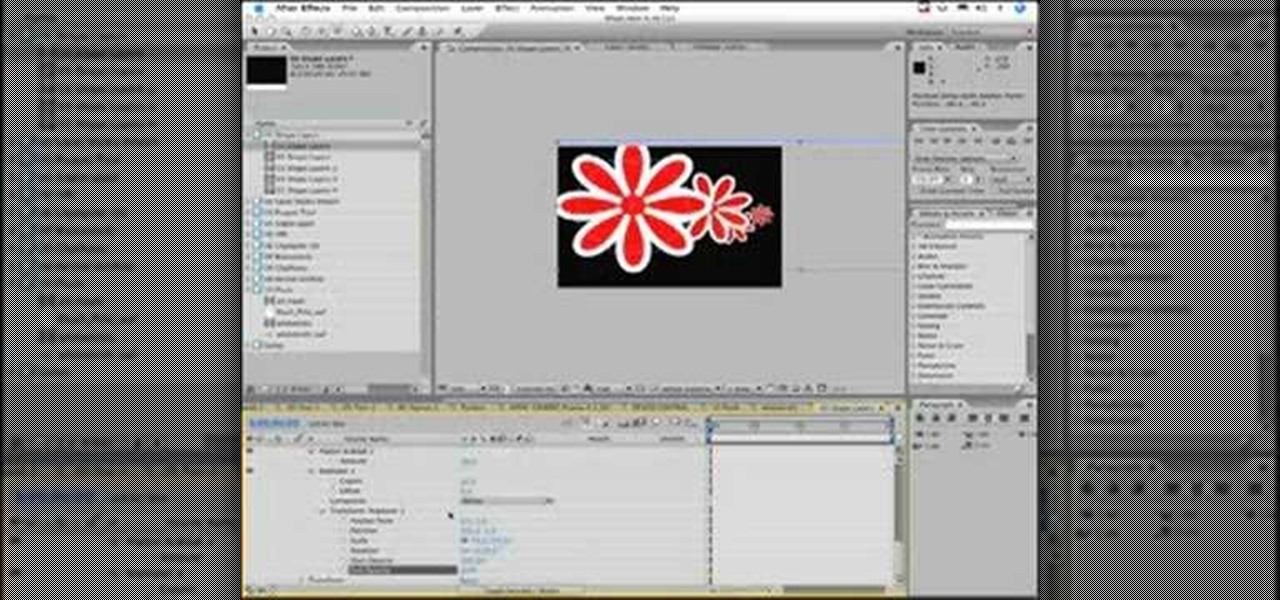
Learn how to use the Shape Tools to create dynamic motion graphics elements in After Effects. This tutorial was recorded as part of a session at the 2007 NY Post Production Conference. Watch and learn how to effectively use the shape tools in After Effects CS3 for your motion graphics and compositing projects.

Take a look at this instructional video and learn how to mount your tennis racket with a 6-Point mounting system. You seldom have to move the mounting system's posts if you restring the same tennis racket. The micro adjusters assist in getting the tennis racket snug.

In this video tutorial, you'll learn to use CKK modules ImageCache and Imagefield to build a system for posting images on your Drupal website. Learn to create a robust and flexible system for handling images and has a bright future with more modules born every day that tap in. (This micro-lesson depends on prior understanding of the CCK module and the Views module.)

When a thick piece of wood is treated the treatment doesn't soak into the center of the wood. If you are using the wood for a fence post you need to treat the bottom of the wood so that the ground moisture doesn't damage it. In this how to video, home improvement expert Danny Lipford gives a great way to treat the bottom of your pre-treated wood.

Model Airplane News Editor Roger Post shows you how to iron out the wrinkles in your RC plane. It's important to clean any possible dust or dirt before ironing. Watch this video tutorial and learn how to take the wrinkles out of a remote control ariplane's cover.

This is a video puzzle tutorial on how to solve the Right Brain Teaser made by Channel Craft, which some people would call the game device of cruel torture.

In this video tutorial, Scott Golightly shows how to create an ASP.NET HttpModule to “rewrite” the URL when a request for a web page comes in. You may want to rewrite URLs to create friendly URLs or to direct an old URL to a new URL. We will look at the code needed to implement URL rewriting and also how to handle page post back events.

Learn how to make an origami bird out of a Post-it note. Use just one square sheet from the pad to make your origami bird.

A brief overview on sharing using iMovie. iMovie makes it easy to share your movies, whether you want to show them on your own TV, carry them with you, or post them on your website.

The slip knot is the easiest way to attach a line to a post or bar. Learn how to tie a slip know in this video tutorial.

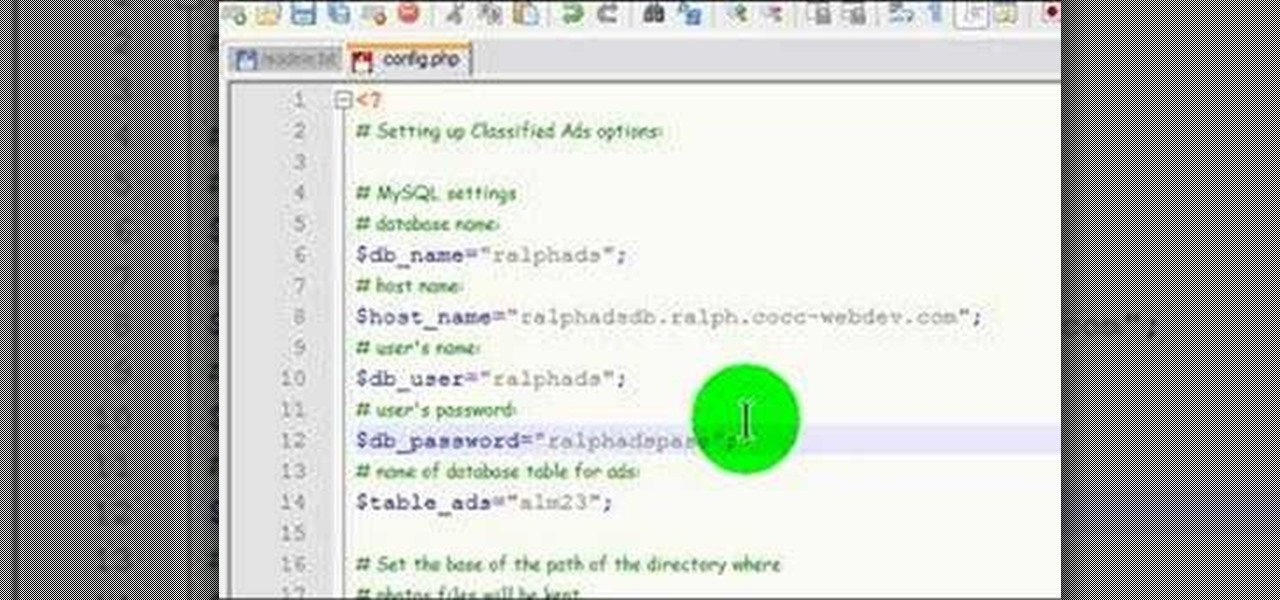
This video documents installing a php script (Almond Classified) that allows for web visitors to post classified ads on your web page.

Why would you want to have an action just for creating a 500px size image? Well, that's the perfect size for posting images on a forum, and if you create an action in Photoshop to do this, you'll never have to manually resize an image for the web again! Learn how to create, and customize this action.

Made from cherry wood, this is a handmade woodcarved coyote call. Thanks to information posted on Preditormasters for the help in making this video.

Pound board and put back is a great drill for developing arm strength and lay-ups for post play. This video explains how to practice this basketball drill.

EFT is a highly effective way of dealing with Post Traumatic Stress Disorder (PTSD). If you have an event in your life that you need to be at peace with, this video will help you. Tapping (EFT or Emotional Freedom Technique) is a way to take away the emotional component of the memory. If you find the event too painful to visit on your own, please consult a qualified EFT Practitioner.

Erik Beck of Indy Mogul shows you how to make a non-working jet pack for under $30. He'll also show you how to create a flying effect for the jet pack in post-production using a green screen.

Every now and then you may need to use HTML tags outside of your HTML editor. Posting things for sale on eBay is a perfect example. In this video tutorial you'll see how you can use GoLive CS2 to generate all the HTML to make your descriptions pop.

Learn this exciting swing dance from the 30s. Sosh and Gina will start at the very beginning, no experience necessary. Learn how to dance from our instructional dance video clips (it's like a virtual dance lesson). Each? week we will post a new video clip here on our video podcast. If you're interested in more check out our site www.iDance.net.

The gesture navigation introduced with Android 10 worked wonders by giving you more of your screen and less tapping. Android 11 offers the option to fine-tune the back gesture sensitivity for your screen's left and right sides. However, the issue still stands for people who like to use the left swipe menu within apps to open hamburger style menus.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

Spam calls are one of the most annoying things to happen in the world of smartphones for more than one reason. Not only are they bothersome, but they can also be dangerous to people who don't know any better. Google has come up with a crafty solution known as "Call Screen" to let the Google Assistant handle the call for you while you listen in on the caller like a stealth ninja.

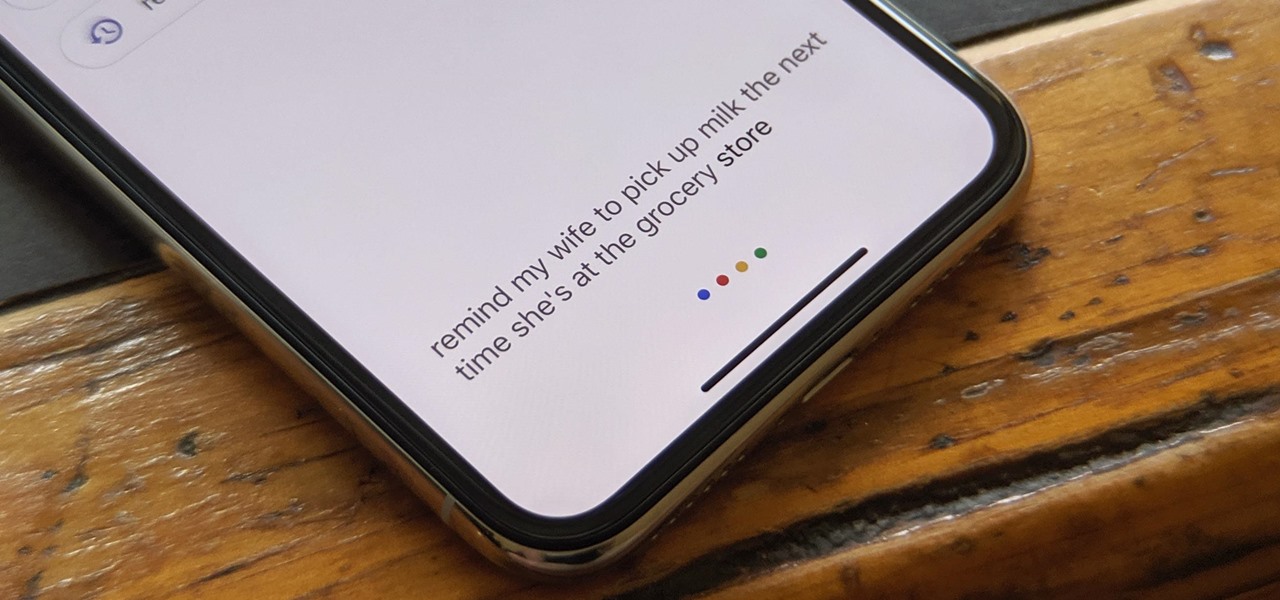
The Google Assistant is available almost everywhere. It powers smart speakers like the Google Home, it's built into Android phones, and it can even be installed on iPhones and iPads. So when Google adds a feature like the ability to send reminders to other people's Assistants, it's far reaching.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

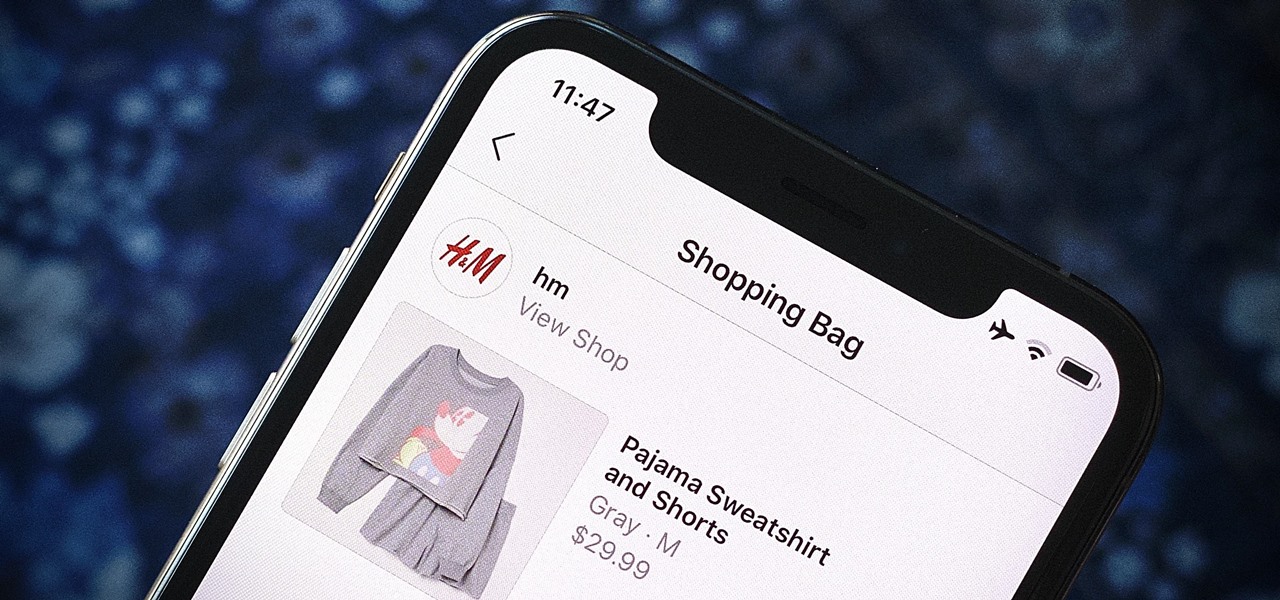
Instagram wants to bridge the gap between advertising and shopping for a more central buying experience. The app has long been a platform for advertisements, with both companies and creators using it as an outlet to link to products, so it's only natural for Instagram to allow users to buy content featured in posts without ever leaving the app.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

In late-2017, Instagram rolled out a feature that automatically saves your ephemeral Stories to a private archive. Before that, Stories disappeared into the ether after 24 hours, but not everyone was comfortable losing these precious photos and videos. If you post to Instagram Stories quite often, you can now easily access your history from your account — and you might not even know it.

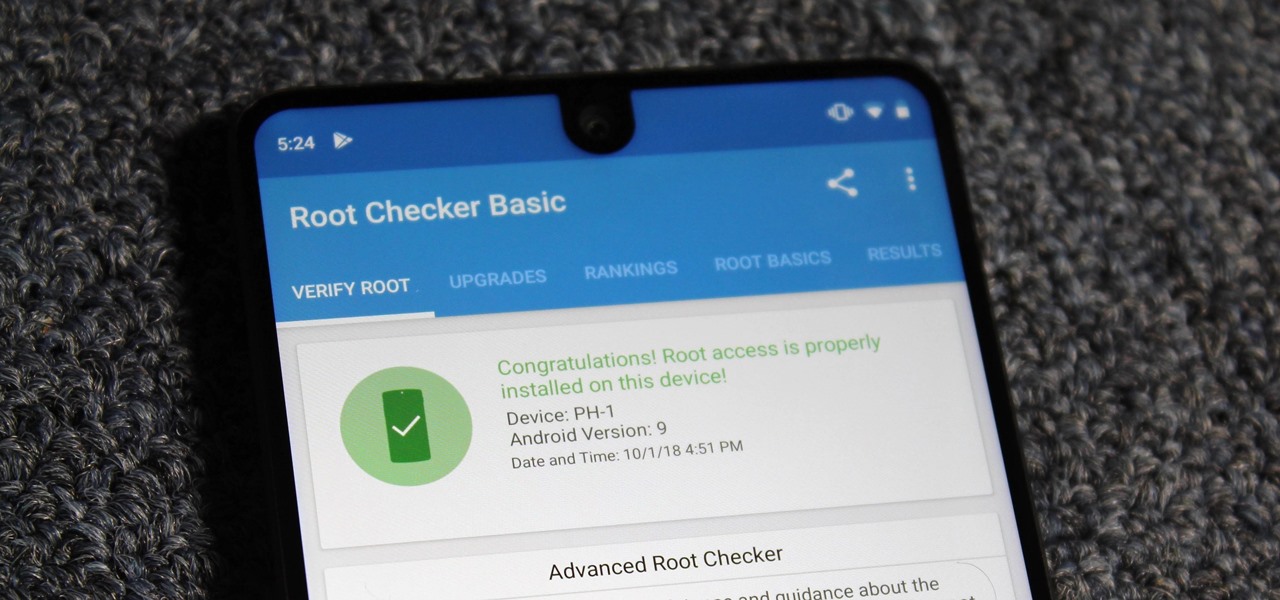
Despite its rocky start, the Essential PH-1 has a lot going for it. Not only does it get consistent security patches and system updates hours after the Pixels, but like the Google-developed lineup, it's also great for rooting. Not only is your warranty not void with rooting, but the process is pretty straightforward.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.