Want to disguise your URLs so that they appear suspicious? In the style of websites such as Tiny URL that take your original URL and give you a shortened one to post on your blog or twitter feed, Shady URL takes your original URL and gives you one that might convince people not to click it. Go to Shady URL and paste the URL you wish to disguise. Click submit, and on the next page it will give you a URL that looks, well, shady. It might include something about a mail order bride or an investme...

This beauty video demonstrates how to create a dark fairy Halloween makeup look.

This video tutorial is in the Arts & Crafts category which will show you how to create a floral antique photo stand. The photo stand can be used to place photos or picture cards and it also doubles up as a candle stand. A picture holder measures 4 1/2 inches from top of the ring to the top of the stand. But, you can have different length. Take a lid of a tin and drill a small hole in the center. Place a wire through the hole. Apply generous amount of glue on the outer side of the lid. Sprinkl...

In some places, it's illegal to ride your bike at night without lights or reflectors, so if you plan on going for a joyride on your street bike, then you need to be prepared to share the road with vehicles and be seen. Appropriate gear and lighting are essential for safety when riding a bike at night.

How many stitches does your crochet art have? How can you tell? Why would you even want to know how many stitches are in your crocheted sweater or crocheted hat? Knowing how to count your stitches is a fundamental step in learning to crochet – assuming you want your finished product to be the right size and shape.

This video tutorial from Mark Dusting shows how to create and edit wiki page in Wikispaces. To start, open internet browser and go to www.wikispaces.com.

First of all you have to understand that in this type of crochet you have to do similar to what you did for the front post double crochet. However the basic difference is that in front one you inserted the crochet from the front, however in this type you have to insert the crochet from the back side. So to do this you have to yarn over the crotchet and then go through the back to the right side of your stitch and just open up the front and then go back through on the right side of the stitch ...

Maintaining a strong, healthy physique can be time consuming. If you're looking to stay in shape without committing a large chunk of time, this workout might the one for you. It only takes 15 minutes to build strong muscle and stay in shape!

In this video, which is another installment of Masc Minute, we learn about razor burns, and how to prevent and treat razor burns. One thing is that you don't want to be using a dull razor. As soon as your razor is done, throw it out, because that will definitely irritate your skin. You also want to use a good shaving cream that will protect your skin. But something you can do to help treat razor burns specifically is using a post-shave repair product. The product recommended in this video is ...

Do you win the prize for messiest room in America? That's a difficult contest, but how about messiest room in your house? It’s time to clean your room, so do a good job in the shortest amount of time and get your parents off your back.

You've drafted a promising team, and the season's under way. Now increase your chances of making the playoffs.

Here’s the thing—dogs will do things just to please you. But cats want to know what’s in it for them. Learn how to train a cat.

Photoshop Mama is here to make all your software tutorials you want to post on YouTube so much better! She shares info on the products and where to get them and also covers how shes produce vids and specifically her post production procedure for saving vids for upload to YouTube.

If you have not used your eRecovery system in a long time and have forgotten the password, have no fear. This video is here to help you retrieve your details and use your program again. In this clip, learn how to recover any lost passwords with Acer's eRecovery Manager for Linux.

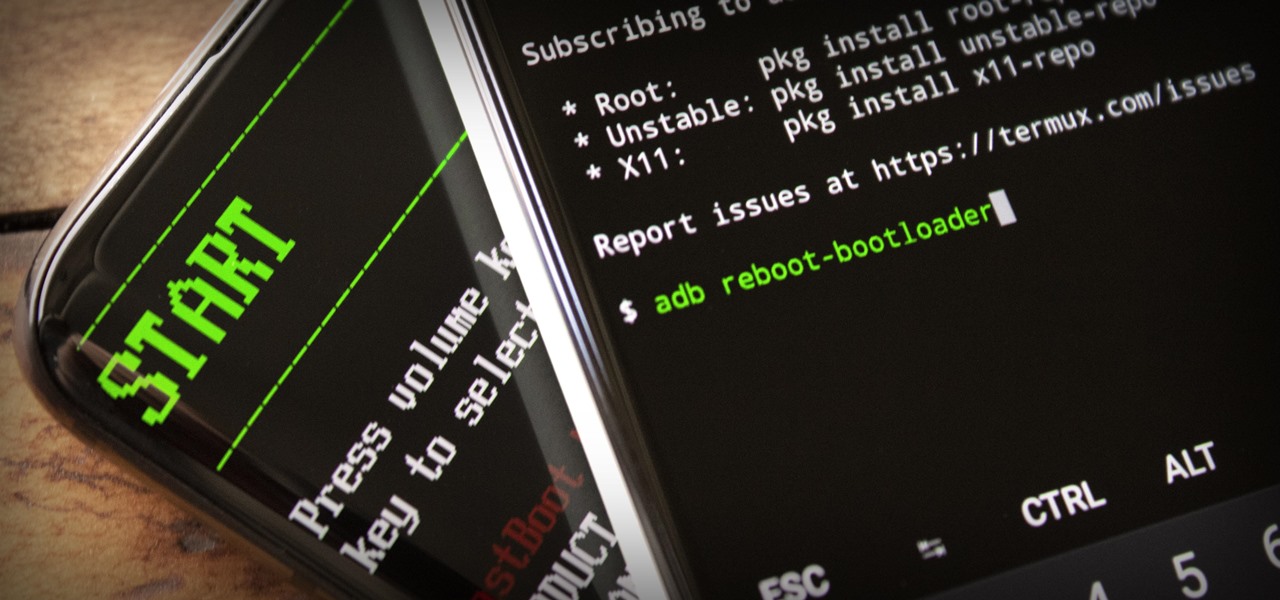
ADB and Fastboot are powerful tools that have always required a computer. But with the right setup, you can now send commands to a phone using another phone.

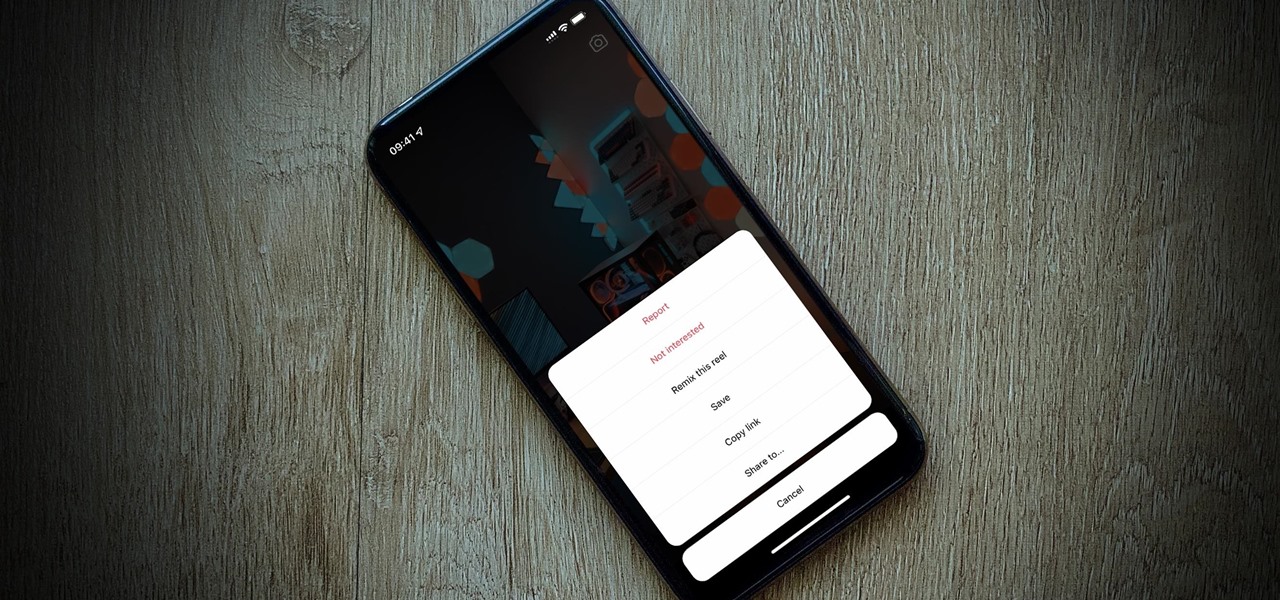
So, you're trying to show a friend or two a hilarious Reel you liked or saved on Instagram, but where is it? Unlike TikTok, Instagram doesn't make it clear where you're supposed to find your liked and saved Reels. Luckily, we can help.

It's nice having a dark theme on Android 10 and One UI 2, but setting it on a schedule takes it a step further. Imagine the light theme turning on every morning, and the dark theme taking over after sunset — all automatically. It sounds pretty simple, but it's one of those things you wouldn't know you need until you try it.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

This week's Magic Leap Lumin OS update contained a number of goodies, including iris authentication, and a way to stream to Twitch from the device.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

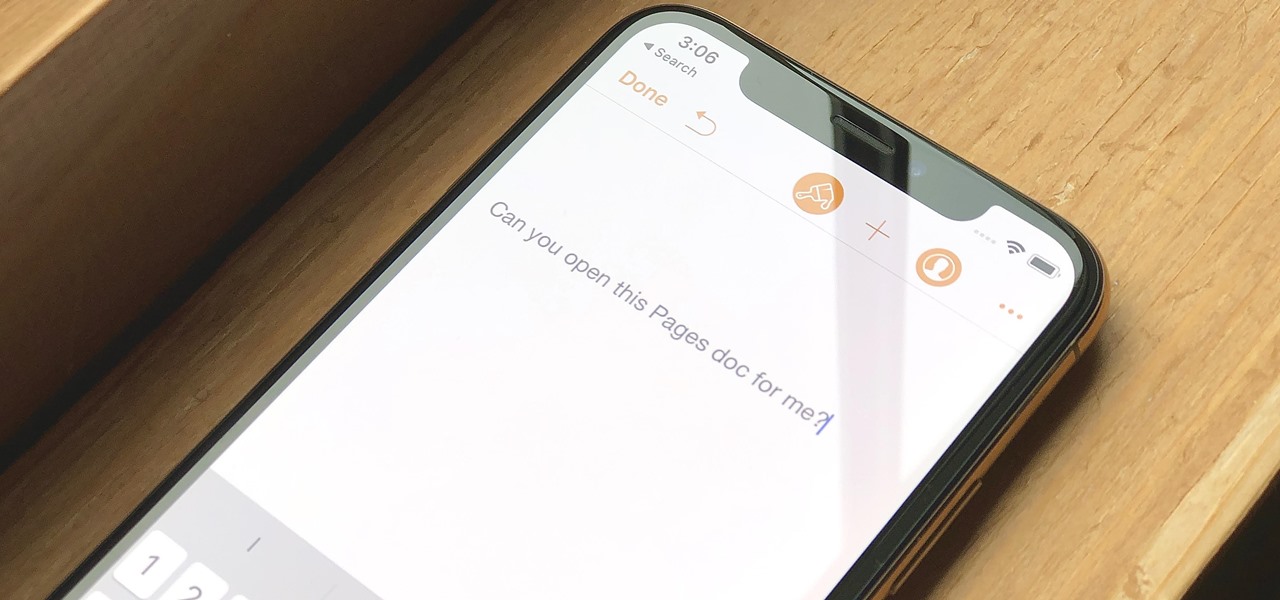
Let's say you have an important report to submit, but you want to check it over for any last-minute edits or changes. Times running out, and you simply can't find this Pages document anywhere. Wouldn't it be great if you could just ask your iPhone to open the report for you, so you could stop wasting time searching and finish the paper? Well, thankfully, Siri can help you out with that.

In Tidal, you could always share a link to your favorite playlist, song, artist, album, or video via a text message, email, or social media post. But if you wanted to share to Instagram Stories or Facebook Stories, you were out of luck. That all changes with Tidal's new sharing features on Android and iOS.

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

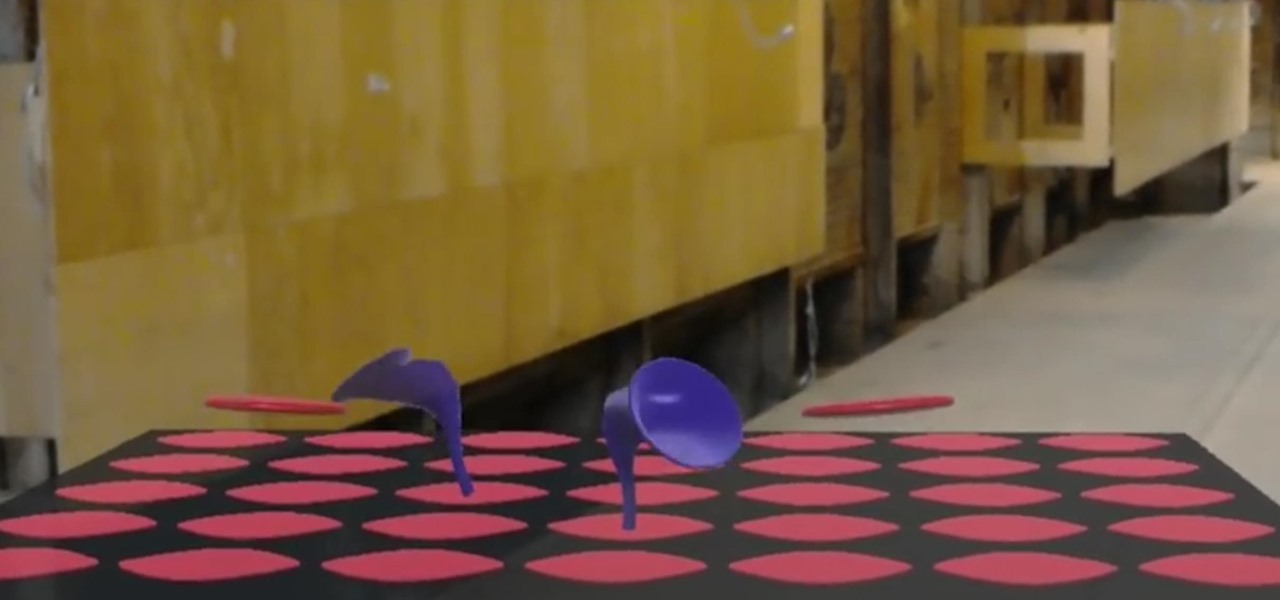
A sizzle reel just released by augmented reality cloud company 6D.ai shows off what kind of hyper-realistic AR experiences developers can build with its SDK.

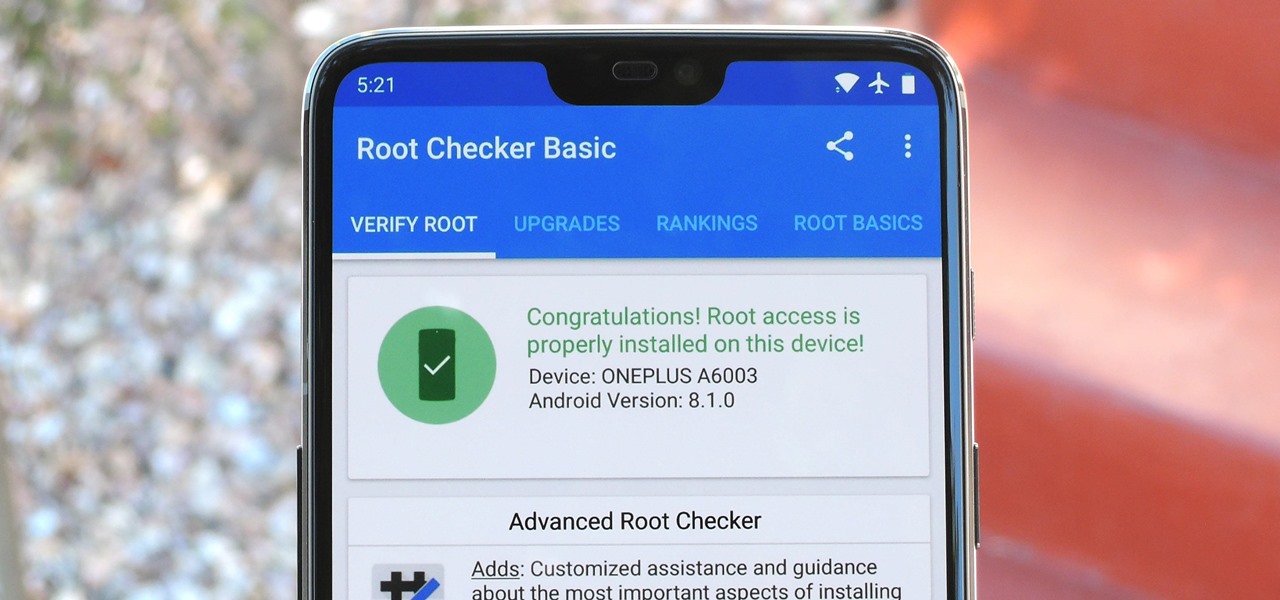
Year in and year out, OnePlus flagships top our list of the best phones for rooting. Why? Primarily because rooting does not void your warranty, and OnePlus goes out of their way to make the whole process as easy as possible.

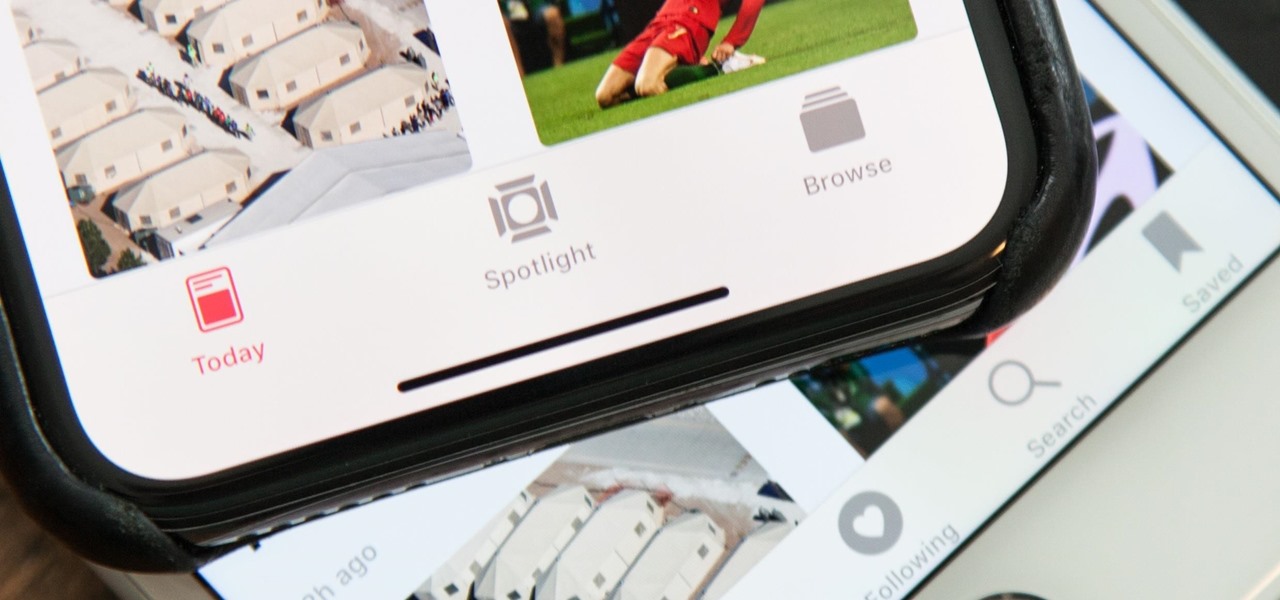
One of the best features in the Apple News app is the ability to save stories for later. If you see an interesting or important article but don't have time to read it right away, there's a good chance you'll never find it again unless you save it. Ever since News' birth in iOS 9, accessing these bookmarked stories was as easy as going to the "Saved" tab, but that's no longer the case in iOS 12.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

After more than a year and a half of silence, the rumors have morphed into reality: Microsoft has finally released an update for the HoloLens. And with that update comes a collection of new features that hint at big plans for the HoloLens this year.

Old school media stalwart Sports Illustrated is billing this year's Swimsuit Issue as the "Most Immersive Experience Ever," and it certainly lives up to that statement, as the magazine has added augmented reality and virtual reality experiences to this year's version via Snapchat and the Life VR app.

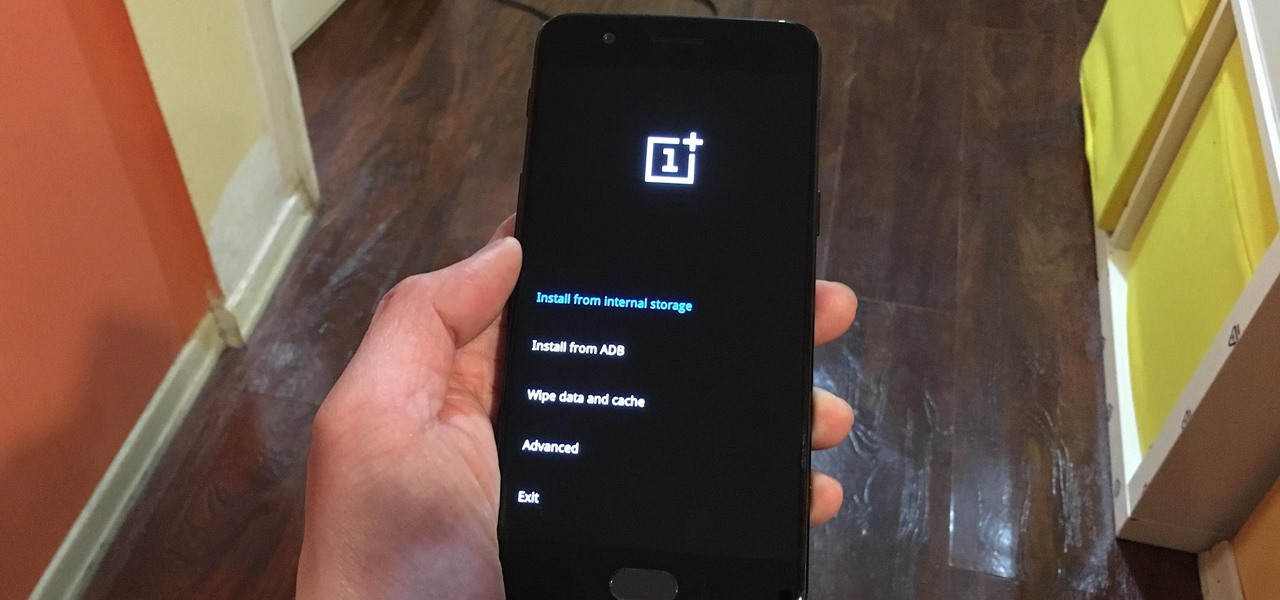
Both the OnePlus 5 and 5T have two pre-boot menus that every owner should know about: Recovery mode and bootloader mode. The recovery screen lets you wipe cache, perform a factory reset, or install firmware, which can help save the phone from a soft-brick. Bootloader mode, on the other hand, lets you send Fastboot commands via PC or Mac to lock or unlock your bootloader or flash images.

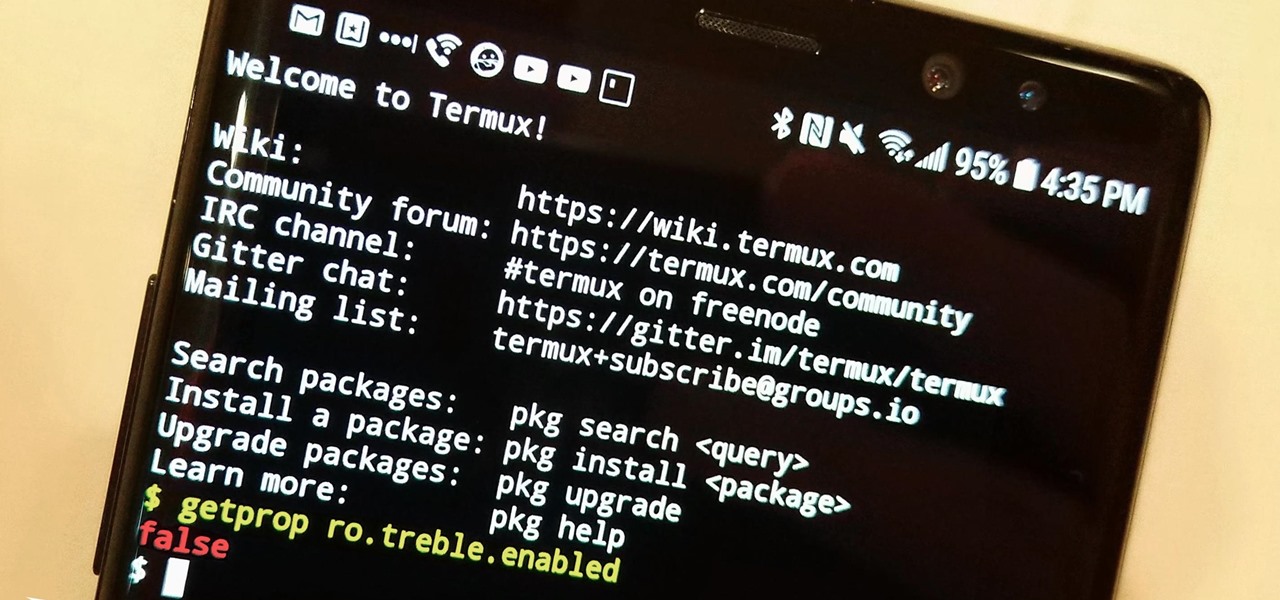
The Oreo beta updates for the S8 and Note 8 have been avilable for some time now. If you're interested in running Oreo on your Galaxy Note 8, you can check out our guide on how to do so. As we dig deeper into the updates, one question on the minds of Galaxy fans is whether or not the Oreo update will support Project Treble. Today, it appears we have an answer.

When playing word association with Star Trek, the first thing to come to mind with regards to augmented reality is likely Holodeck, not The Game, an obscure episode from season five of Star Trek: The Next Generation.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

Advertisers must love when their commercials go viral. Take for instance the Esurance commercial where an elderly woman completely misunderstands Facebook jargon.

Modern warfare takes on a more literal translation with the advent of new augmented reality displays revealed recently by the US Army to improve soldiers' situational awareness on the battlefield.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.