From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Because of the way Android is laid out, you automatically lose a portion of the top and bottom of your screen thanks to the status and navigation bars. The thing is, you don't always need the navigation buttons. By hiding them, you can enjoy more of your Galaxy S10's big, beautiful display.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update today with a few simple steps.

So yeah. Its AugustFackYou and I felt like posting today and being an active member of the community. After reading this please tell me if you have any comments on what I can do better or if this method is bad. Anyway today I will be showing you how to get root on a mac. I managed to become an administrator at my school with this and one other method.

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

For those times when you can't get something done by clicking a few buttons with your mouse, the Windows command prompt has always been an indispensable tool. But as much as advanced users have relied on this useful utility, it hasn't seen a significant update since the Windows 95 days.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Bad news first: It's not out yet, but it's coming really soon. The premise for the game is this:

Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

The Air Command window on Samsung Galaxy Note devices makes it easy to access all of the features that the S Pen has to offer, such as Action Memo, which turns your handwritten notes into actionable links, and Pen Window, where you can draw a square on the screen to open a certain application.

Still working on mega project builds. This one is going into my own PVP server which (will) contain 4 theme'd biomes inside of a 155m sphere - inside of a 255 meter containment sphere inside a 1000m+ void. The outer sphere acts as both artificial sunlight and a drop-death height of 50m. 4 more outer panels to go (water and lava) and it's ready for interior work and redstone - including command-block powered proximity traps that don't have any triggers marking them as well as hidden walls that...

Anyone who is familiar with Linux knows that to use your OS to the max, you will need to use the terminal every now and then. Whether it is to install a package or update the system or even delete a file.

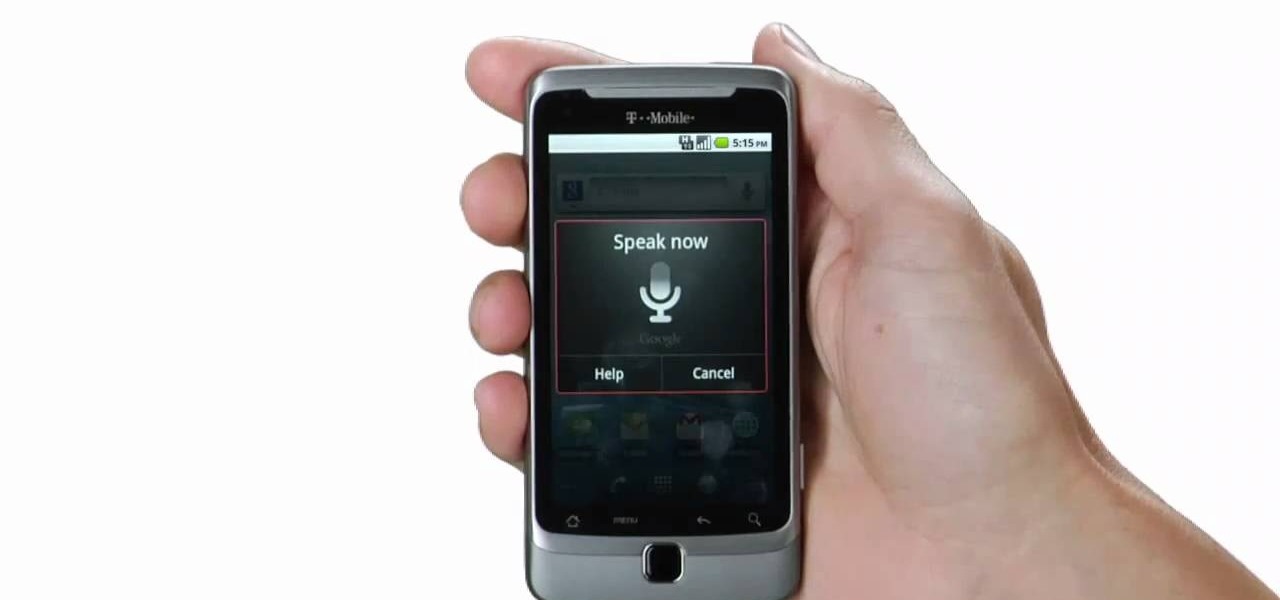
Make calls and send text messages and emails with voice commands on your T-Mobile G2! This clip will teach you how. Whether you're the proud owner of a a T-Mobile G2 Google Android smartphone or are merely toying with the idea of picking one up in the near future, you're sure to be well served by this official video guide from the folks at T-Mobile.

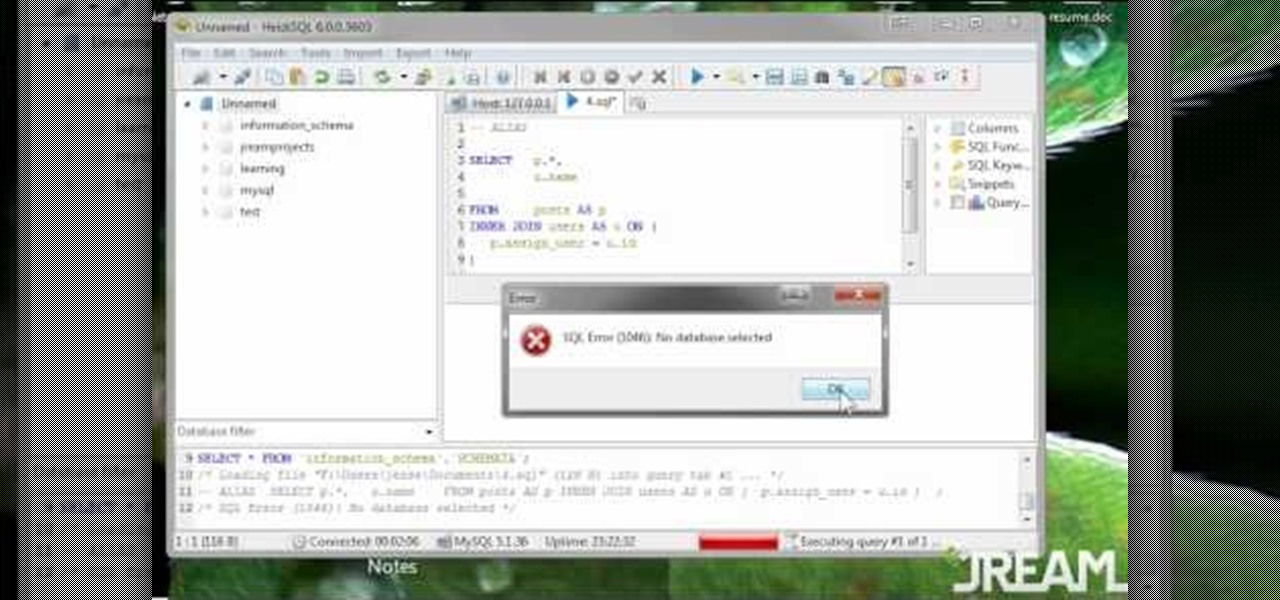
The greatest function of the ALIAS command is as a shortcut. Being able to use this properly will make your MySQL database much easier to use, more functional and streamline all your programming. This tutorial shows you everything you'll need to know about using ALIAS in your database programs.

Of course, you'll want other people to be able to interact with your program. Linux sets up a command shell automatically, but if you're programming with Python on a Windws machine, you'll need to do it manually - and this video shows you how.

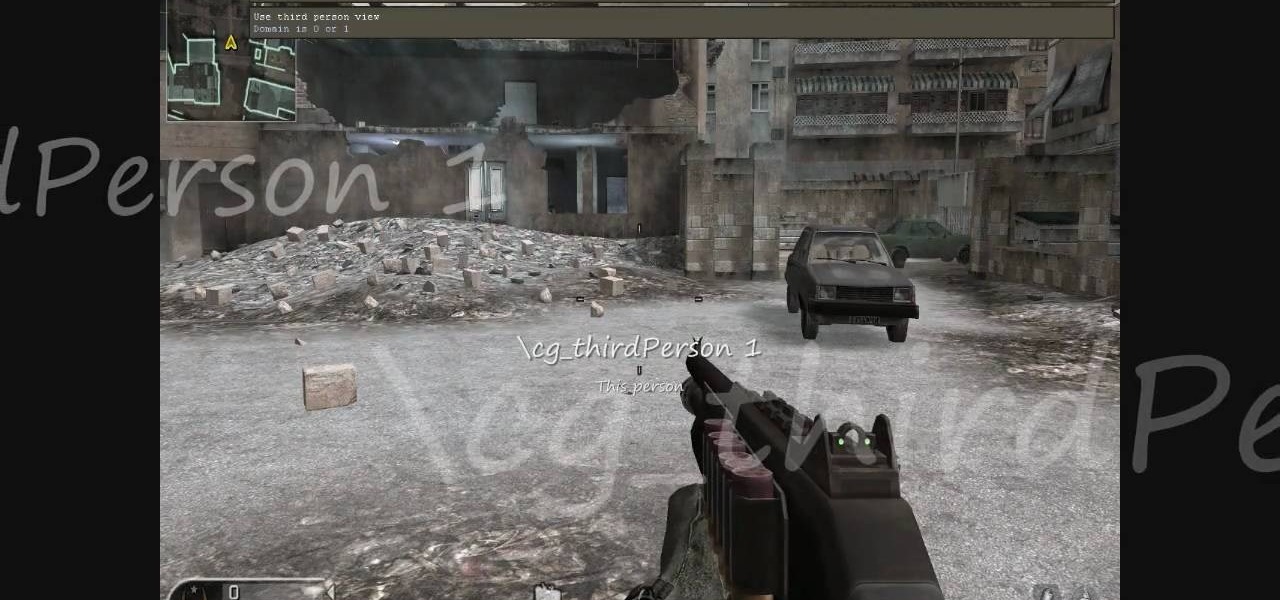
When you enable the dev console for CoD 4, you can get into the developer's menu and give yourself all sorts of cool tricks, extra equipment and more! This video shows you a few commands you can enter when the console has been enabled.

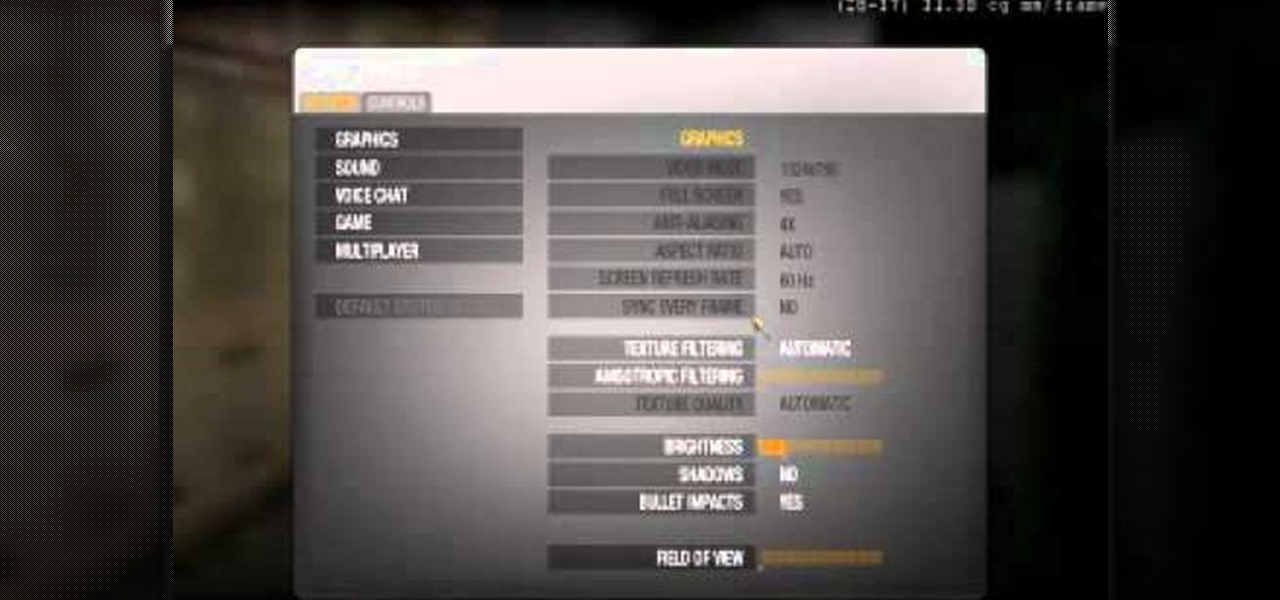
If you're having some problems playing Call of Duty: Black Ops because your computer can't quite handle everything, you can use the console commands to scale everything back a bit. This is a great stopgap to use until the patch comes out.

In need of a little help? In this clip, you'll learn how to defeat the San Francisco - Tactical Command & Moon Pool Room levels of Resistance 2 for the Sony PS3, the sequel to the popular sci-fi first-person shoot-em-'up Resistance: Fall of Man. For all of the details, and to get started dominating this level yourself, watch this video walkthrough.

You can keep water in a liquid state, even if it's below freezing temperature. This tutorial shows you how to take some distilled or purified water, and apply some basic science to make the water freeze on command - or a couple other neat tricks!

In this clip, we learn how to use voice commands to make calls, search the web and open apps on a Windows Phone 7. Whether you're the proud owner of a Microsoft Windows Phone 7 smartphone or are merely considering picking one up, you're sure to be well served by this video tutorial. For more information, including detailed instructions, take a look!

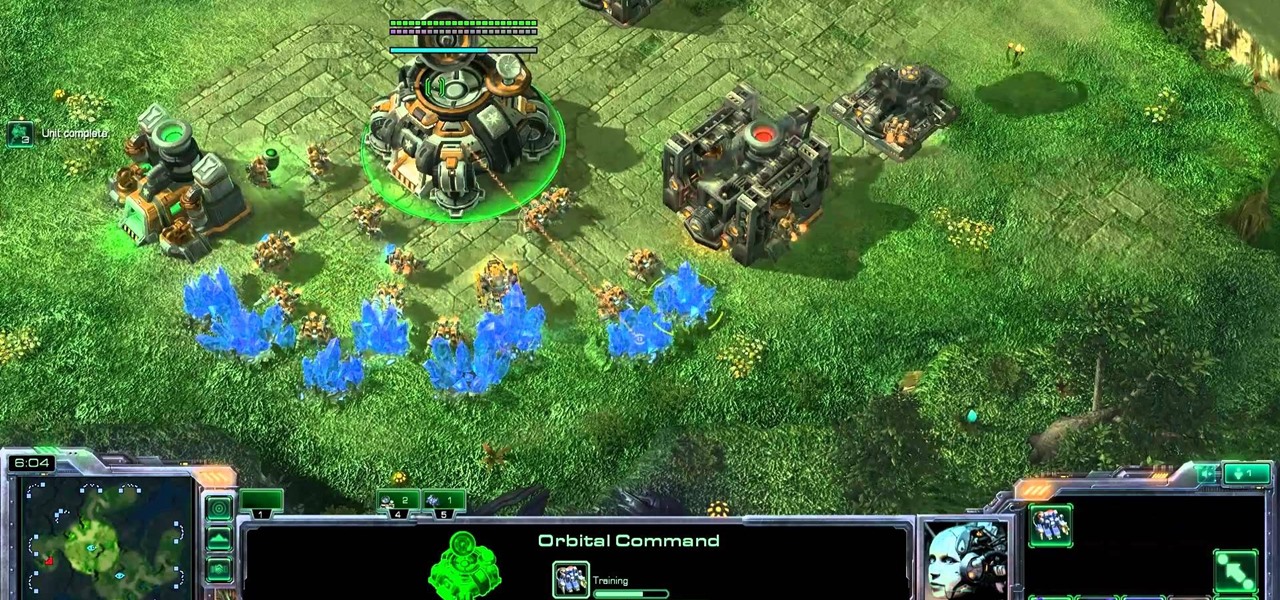
Here's another effective build order for Terran players of the popular StarCraft II strategy game. This build order centers around setting up a double command center for your armies, and is especially effective when you're waging a battle on a large map.

Birds are tricky to train due to their tiny brains, but nearly any hook-billed bird species can be trained to step onto your finger on command. They're at least that smart. This video will teach you a quick and easy way to do it.

Were you aware that you can launch the Windows System Restore tool from the command prompt? Well, you can! And, what's more, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just under three minutes. For more information, including step-by-step instructions, take a look.

For all you that are not computer geeks or nerds, this tutorial is going to show you some tips on using the command prompt in Windows 7. Although it's not vital information, this can still be used to fix certain computer problems and is fun to use when opening certain programs or doing other things as well. So sit back, pay attention, and being a geek or nerd is cool so relax!

The lady shows how to make the steadicam arm to work with glidecam stabilizer. The steadicam arm is made such as only a steadicam can be fitted on that. The video describes how to make the usable for glidecam with three simple tools ,a 10 ounce hammer ,a long nose player and a flathead screwdriver. First take out the circular clip with which the post is secured with the screwdriver unscrew and pull the post out .Using the hammer straighten the post .The post will have a scratch but the straig...

This tutorial teaches you how to create a mosaic photo made up of many smaller photos in Photoshop. It explains the use of the crop tool, image resizing, use of sharpen filters and of fading command. It also handles creation of custom patterns with the use of the define pattern command as well as later use of the said pattern for a custom pattern fill. Finally, it describes the use of the overlay blend mode for achieving the desired effect.

Say you have imported a mesh into modo and some of the polygon normals are inverted. Align will do it's darndest to find and rectify those errors and make your mesh complete again. Watch this 3D software tutorial and learn how to use the align command to flip the inverted polygons in modo 101 and higher.

Need to change your IP address? In this how-to, you'll find instructions for changing your IP address from the Windows command prompt with the ipconfig console application. For step-by-step instructions, take a look. NB: Changing your IP will not protect your identity; it's merely a simple expedient for getting around certain problems ones might encounter while using the Internet.

Interested in creating an OpenScenGraph project without using the XCode GUI (or, more generally, curious about how to use XCode from the terminal)? If so, then this tutorial, which demonstrates how to build an OpenSceneGraph program using the command line (Terminal.app) in Mac OS X, is for you. Take a look!

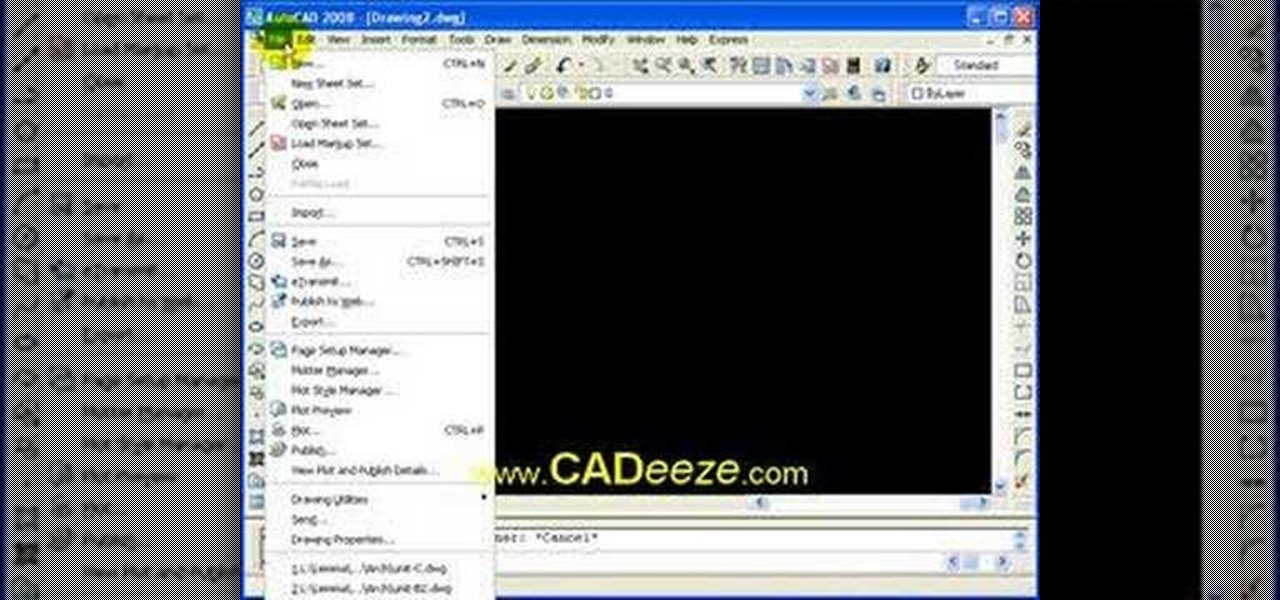
This AutoCAD 2008 tutorial covers working with Command Line Options.

AutoCAD 2008 Tutorial covers the Autocad interface, toolbars, pull-down menus, command line, and accessing commands.

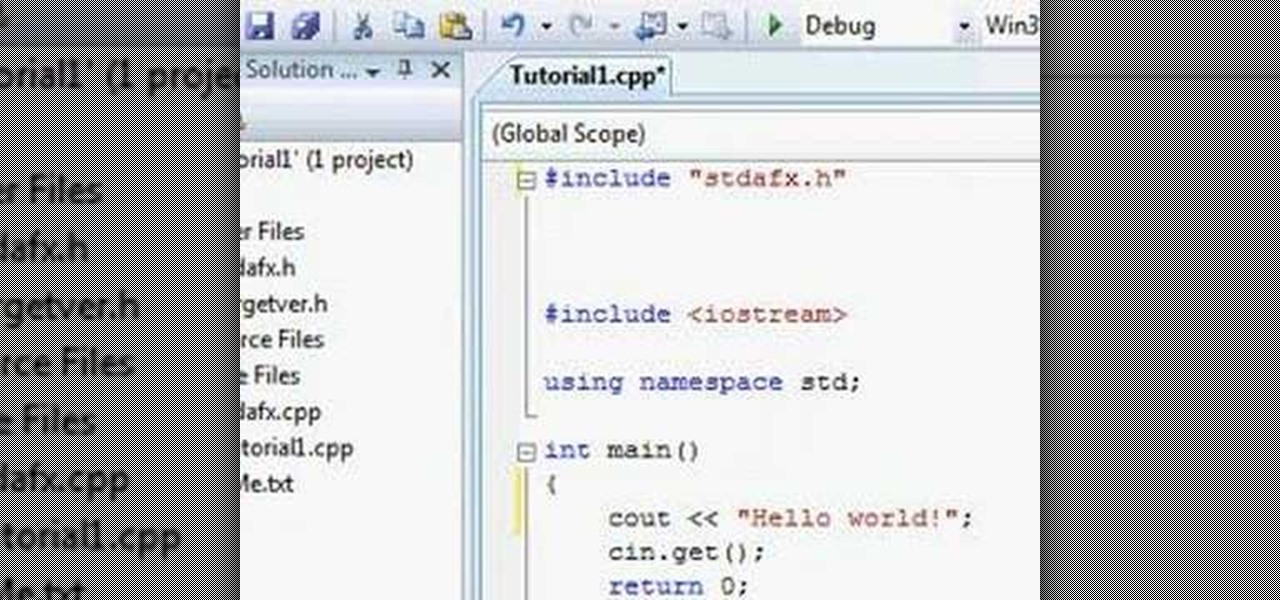
Watch this video to learn about the fundamental commands of C++. Also covered are the topics of custom commands, different file types, headers, and the main function.

John demonstrates the Command+Tab features built-into OS X Leopard and Tiger. Learn how to easily switch between different applications on your Mac, hide applications, and even quit applications with this useful functionality.

This tutorial shows you how to use voice commands with BMW Bluetooth and navigation. This video pertains in particular to the BMW 3 series/M3 (E46).