MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Unscheduled pit stops go hand in hand with road trips, no matter how well-planned they are. In the past, making a stop due to low fuel or an emergency bathroom break may have snowballed into massive delays when you went off course on your own, but thanks to a feature in Apple Maps, you can do this in the most efficient manner possible.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

The Samsung Galaxy S8's almost bezel-less display is truly a sight to behold, especially when set to Immersive Mode. While transparent when on the home screen, the navigation and status bars on the S8 will often turn opaque depending on what app you're using at the moment. This, in turn, can detract from the overall experience when viewing anything from the S8's display, as the bars along the top and bottom of the screen bump the phone's aspect ratio down to lower levels.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

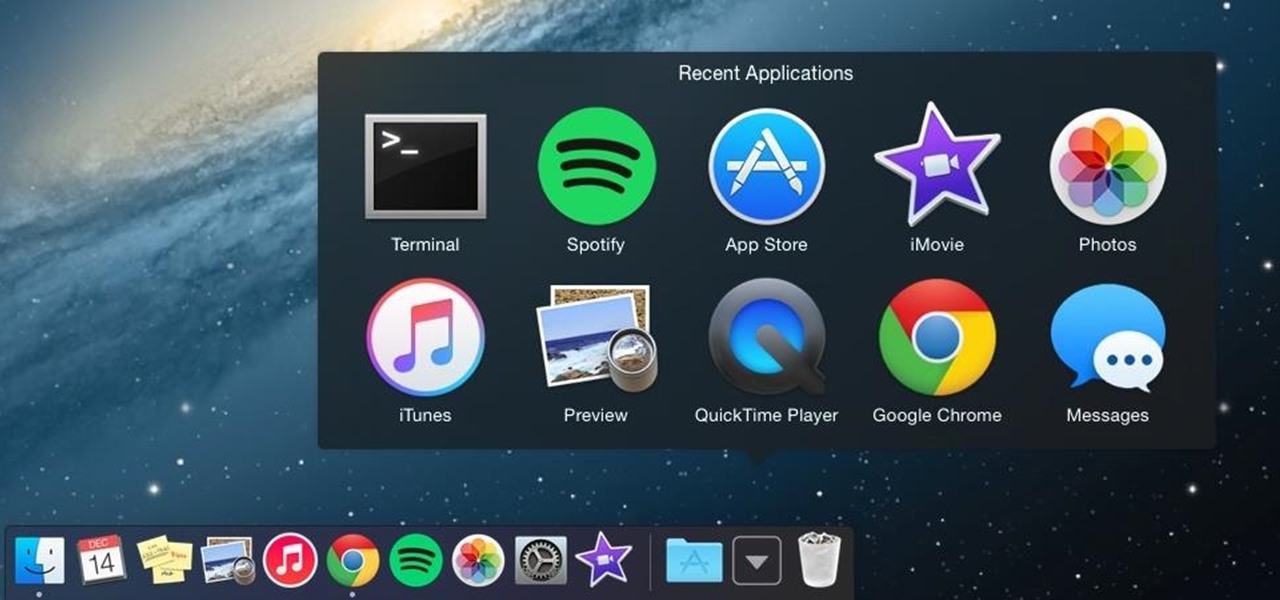
Apple makes it easy to access your favorite and most recently used applications and documents in Mac OS X. You can simply add your favorite apps and folders to the dock, and you can always visit the Apple menu from the menu bar to see a list of your most recently used apps and docs.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

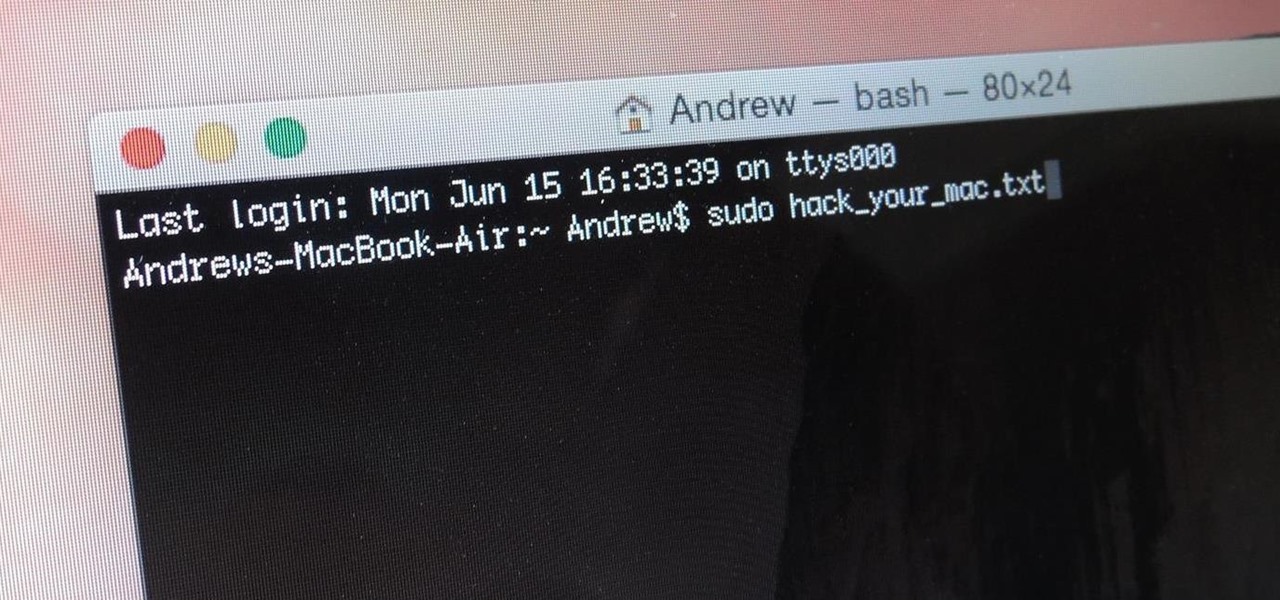
When attempting to run a script, it can be rather inconvenient to have to locate the script, and run it time and time again. What if there were a way to run a script from anywhere. Well that's what we'll be doing today. This can be useful for any scripts you use frequently, it can save you time by removing the need to locate and execute.

When you think of Terminal, you probably imagine some hacker sitting in front of their computer in a dimly lit room trying to break into an FBI database. In reality, it's just a simple tool that can make using your Mac much easier.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.

It seems like custom Google Now commands are a dime a dozen these days. With Commandr for Google Now giving non-rooted users their first taste of custom voice commands just a couple weeks ago, you may wonder why we're covering this subject again.

Whether it's because you want to make a quick tutorial video or want to show off your gameplay skills, recording the screen your Nexus 7 tablet isn't an easy feat. At least, until now. Hidden inside Android 4.4 KitKat is a built-in screen capturing feature, but it takes a little effort to dig it out.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

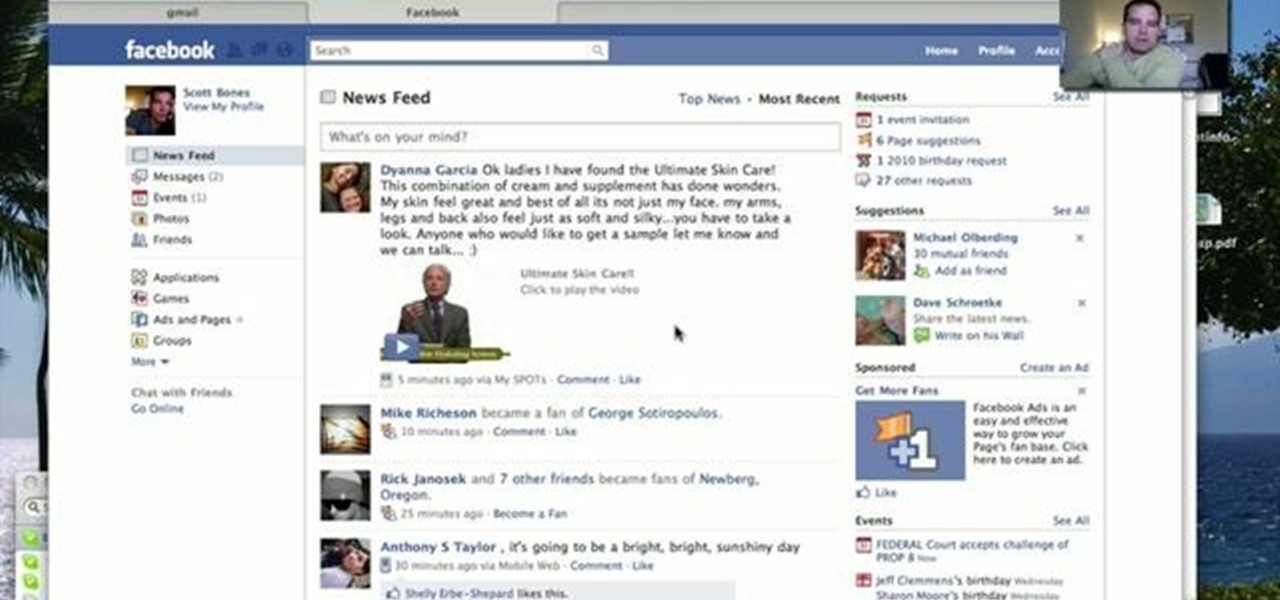
In this video, we learn how to delete wall posts on Facebook. To do this, log into your Facebook account on your preferred browser. Now, click on your profile button so you see your profile. If you see posts you don't like that you want to delete click on the right hand side of the post and you will be able to delete it by clicking "remove". This will remove the entire post from your wall and nobody, including you will be able to see it ever again. This is a good way to remove things you don'...

Donna teaches how to do a front-post, back-post crochet stitch. First of all you'll need yarn and a hook. Start with a single crochet. Donna uses white to create the single crochet and to create a heart, goes over the single line with pink to create a double crochet. To create the double line, go around and through. from front to back, through the single post. Always have the yarn going through the same side. The basic method using the pink, is to make the design in a "V" shape. Using this me...

Follow along with this video and learn how to retweet a post on Twitter. -A Tweet is simply a message posted on Twitter.

Nowadays many schools and colleges have blocked the social community sites from accessing them through school computers. The video shows how one can access to these sites using a command prompt.

There is a great cost effective and durable fence option that is available now. It is fence made from plastic PVC. Start by putting a stake in the ground to mark the location of the first fence post. Use a string tied to the first stake to mark the rest of the fence line. Drive stakes in the ground to mark the location of additional fence posts along the string line every eight feet. Dig your fence post holes with a post hole digger or rent a motorized digger. Once you've dug the hole put gra...

After learning the foundation tricks of "sit!" "stay!" and "come!" have your dog try their paws at a jump.

From housebreaking to traveling, crate training a puppy or dog can have long-term rewards for both owners and pets. Watch this how to video to learn how to teach a dog to shake hands.

It's fun to be out in warm weather cutting big timbers and doing a project that sees quick, upward progress. In this video, you'll find instructions for building a post and plank-style retaining wall. This post-and-plank retaining system is based on the way seawalls (or bulkheads) work. You set posts into the ground, vertically, then plank behind them. This creates a wall with texture and shadow lines with nice hollows between the posts for plantings or grass. And, because there's so much pos...

Make your own earrings out of buttons! Use some vintage buttons, or cover some regular buttons with pretty fabric. All you will need are the buttons, some hot glue and a few basic jewelry making supplies (earring posts and backings).

You have to admit, the armor set on the front of the Fallout New Vegas cover is pretty awesome, but the only way to acquire the armor, besides console commands on the PC, is to kill an NCR Ranger Veteran. There's a way to pull it off without getting any negative fame with the NCR, and the info is in this video!

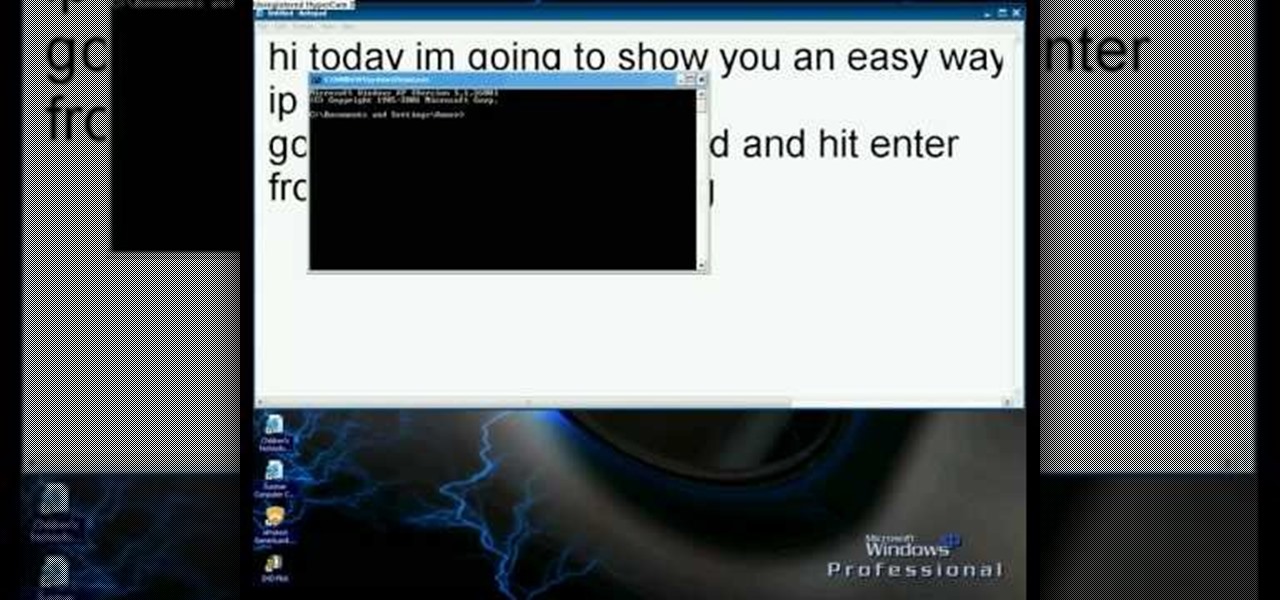
In this video we learn how to find your IP address with the Command prompt. First, go to the start menu on your desktop. Then, find the run box and type in "cmd". After this, hit "enter" and then a black command prompt will show up on your screen. Next, type in "ip config" and then hit the enter button again. Now, a list of information will appear on the black screen. Look down the list to find the IP address listed on the page. Once you have this, you should write down your IP address and th...

What you eat before and after you work up a sweat is actually just as important as the workout itself. The main thing to keep in mind is that you can't eat so much that you still have a bunch of stuff bumping around in your stomach when you're jumping or running.

A dog who constantly follows you around the house wagging his tail is a dog who really likes you (or is hungry), but sometimes you're tired and just want your dog to sit and be still for once. Teaching a dog to sit is one of the most basic obedience training tricks out there, and one of the most important (especially in cases of your dog bounding onto friends who enter the house).

Now that you've mastered the front post double crochet stitching pattern, let's work on the back posts!

Privacy is important on Facebook, a lot of users don't even realize that their posts are being broadcast to the masses.

In this how to video, you will learn how to build a patio enclosure with seating walls. You will need measuring tape, a level, a dead blow hammer, a square, masking tape, safety glasses, and work gloves. You will need the courtyard collection as well. First, draw out a plan for the enclosure. Mark the locations of the posts and panels with tape. Openings should be three to four feet wide. Start building walls at posts. Adjustments must be made at corners. Start by placing four corner blocks. ...

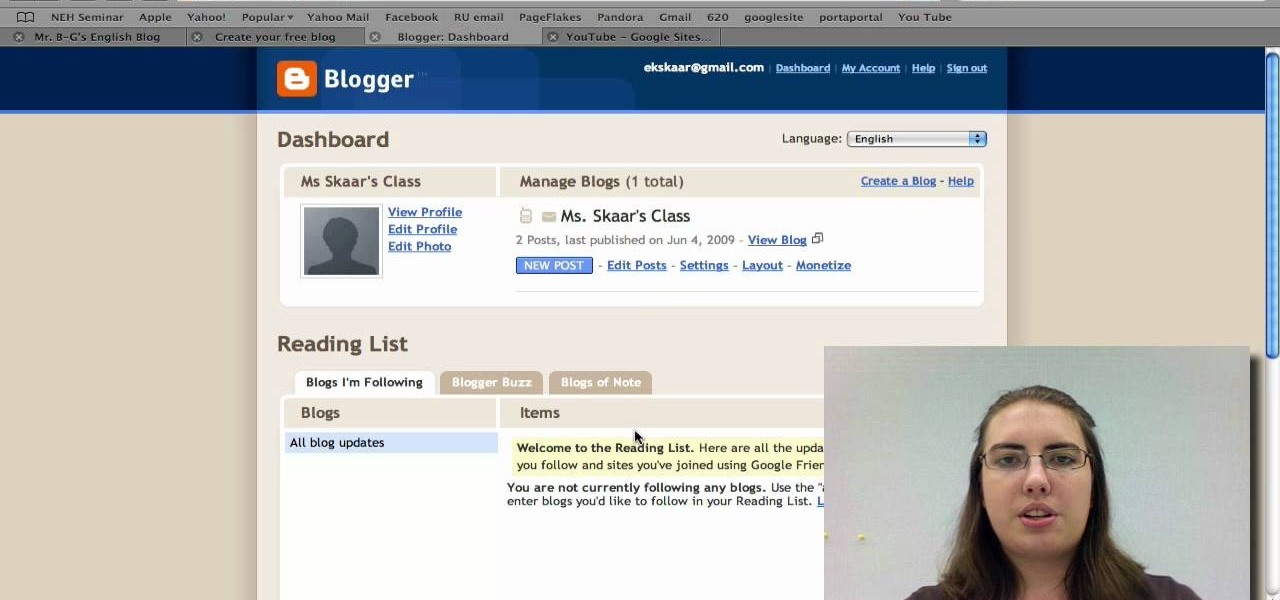
Radford University demonstrates how to upload pictures, embed videos and then publish them in Blogger. Log into blogger and go to your dashboard page. Click edit posts or create a new post. In the blog editor choose edit image from the toolbar. You can now add an image from a URL or upload one from your computer by choosing the choose file option. Next, choose your image position and size. Then, click the upload image button and then click done. Your image will now appear in your post. To emb...

In order to access your wireless router settings in a Windows PC you need to use a command called ipconfig. The purpose of this command is to find out what your IP is. Go into the command console and use ipconfig to find out what it is but instead of noting down the IP address, we actually have to note down the default gateway values for the task at hand. Now all you need to do is open your web browser and insert the default gateway values from before into the address bar. By doing so you wil...

Getting text from one area to another is quite simple. You can do so between any text frames. This video will demonstrate exactly how to cut, copy, and paste on your Macintosh.

In this video the instructor shows how to hide any kind of file in a .Jpeg image file. To do this take the image in a new folder. Go to start button and then to run. Type cmd in the run and hit enter to open the command prompt. Now browse to the directory that contains the picture and also the file that you want to store using the CD command. Type the command to create our required file as shown in the video. Now a new file will be created that contains your image as well as the file that you...