Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Take an animation created in one project and import it into a different project! There are several ways to accomplish this - you can make a new layer or just use the copy command. However, an easier method is to set up your libraries in Adobe Flash CS5 to be shared.

The Image Size command lets you scale an image on screen or in print. Whether you're new to Adobe's popular raster graphics editing software or a seasoned professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this free video guide.

Watch this video to learn a simple cheat that will make your paper longer. Good trick to know when you are in a crunch and need to stretch your class paper. You will need to use your existing term paper and either Microsoft Word or Open Office to use the Find&Replace command. Here's some forums you can post anonymously with other like-minded, less scrupulous people: http://academicdishonesty.net

This Photoshop CS3 for beginners tutorial introduces new Photoshop users to the rectangular marquee tool, the fill command and working with text. You will learn how to create a "senior pic" type graphic using some simple text and basic shapes created with the rectangular marquee tool in Photoshop CS3.

Google TV gives the new Chromecast a home screen full of curated content from your various streaming subscriptions, but it's just that — a home screen app. Underneath, Google's new dongle is running Android TV, meaning its home screen is just a launcher that can be installed on countless other TVs and set-top boxes.

The gesture navigation introduced with Android 10 worked wonders by giving you more of your screen and less tapping. Android 11 offers the option to fine-tune the back gesture sensitivity for your screen's left and right sides. However, the issue still stands for people who like to use the left swipe menu within apps to open hamburger style menus.

Downloading third-party screen recording apps can be dangerous. The primary function of these apps is being able to record everything on one's display, so it's easy to see how a malicious developer could exploit this for their own gain. That's why the addition of Android 10's built-in screen recording is so impactful.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Depending on how you use your phone, you may have noticed your status bar is a bit crowded due to various icons being enabled. While some icons make sense to have, such as Wi-Fi and Bluetooth, the VPN key icon can be redundant, especially if the app uses a notification. Good thing, there is a way to get rid of the icon.

Deep down inside, Android is really just a fork of Linux, the popular open source desktop OS. You can see traces of its roots everywhere, and this lineage still holds a certain appeal with many Android fans. If you're in that boat, you'll love the newest notes app we just found.

The Samsung Galaxy S8's almost bezel-less display is truly a sight to behold, especially when set to Immersive Mode. While transparent when on the home screen, the navigation and status bars on the S8 will often turn opaque depending on what app you're using at the moment. This, in turn, can detract from the overall experience when viewing anything from the S8's display, as the bars along the top and bottom of the screen bump the phone's aspect ratio down to lower levels.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

There are hundreds of keyboard shortcuts out there, but these 7 are the ones you'll definitely want to remember. I use them every day, and you should too. Step 1: Tab Domination

Nearly ten years since the first Galaxy Note and yet the Galaxy Note 20 still hasn't solved one of its biggest problems: bloatware. There are still over 20 redundant or unnecessary apps that are on this $1,000+ phone. But while it does require some advanced tools, it's still possible to remove them.

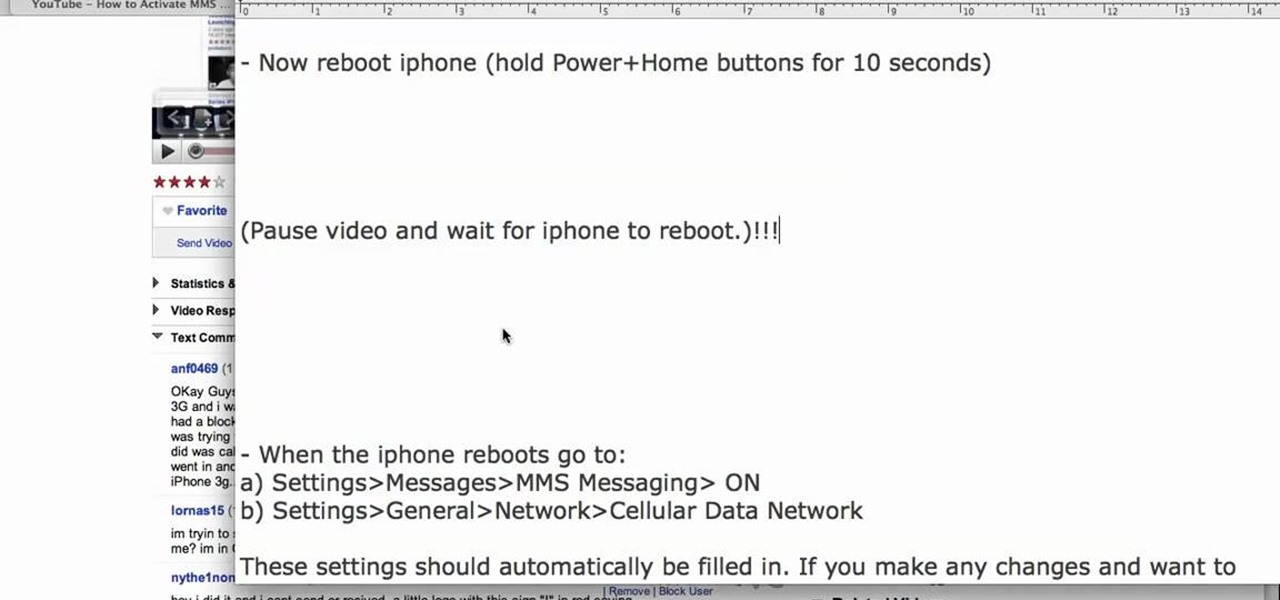
In this tutorial, we learn how to use MMS on T-mobile or ATT iPhone using 3.1 or lower. First, you need to make sure you have iTunes down and it's not running on your computer at all. After this, go to the start menu, then click on the run. Next, type in "command" and hit enter. Then, type or copy and paste "C:/Program Files/iTunes/iTunes.exe/setPreflnt carrier-testin 1" into the command console that comes up. Then, hit enter and reboot your iPhone. When this reboots, go to the settings menu,...

Shawn Powers teaches us how to install Truetype fonts on your Linux systems. First, log onto your web browser and go to Halloween Fonts. Once on this site, browse through the different types of fonts until you find one that you like. After this, save the file for the font onto your desktop. Now, install this font on your command line by first unzipping it. Go to the user share Truetype folder, then make a new custom folder. Move the file into the folder, then make sure the font and the folder...

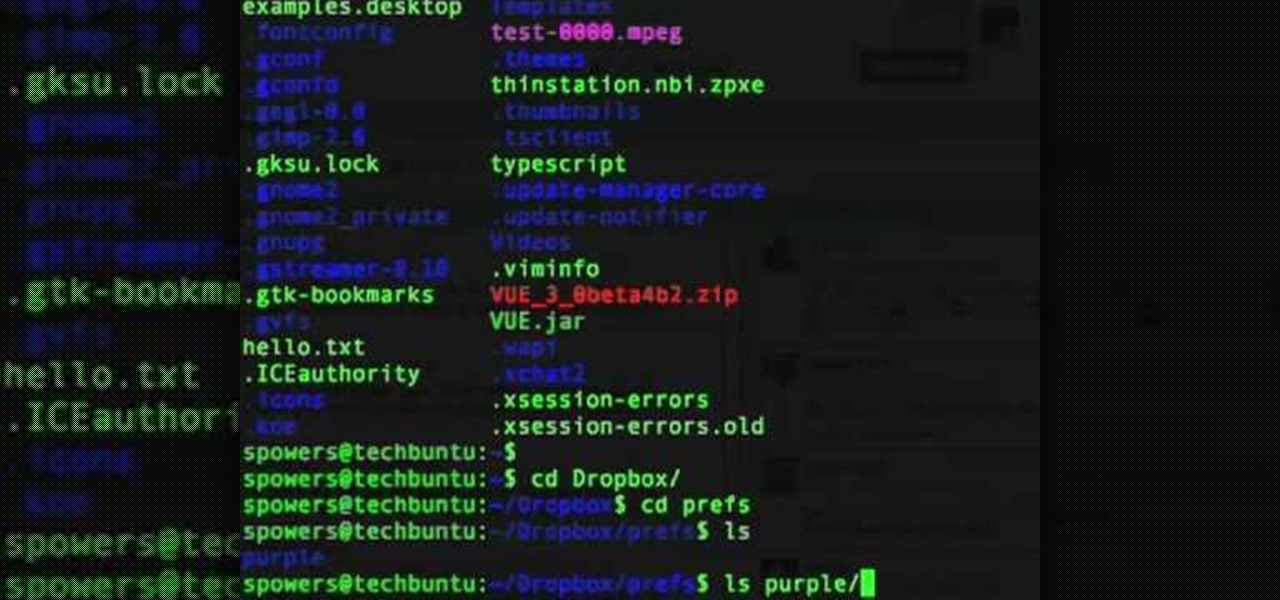
In this tutorial, we learn how to sync preferences with DropBox or Ubuntu one. This doesn't work for everything, but it will sync pigeon preference. It's a folder ".purple" and all the preferences are inside here. If you are familiar with using command prompts, then this will be very easy for you to do. Make a symbolic link from the command prompt to the drop box folder. On every folder, you will get the same result! This is very easy to do and just takes a few seconds to find, then you can c...

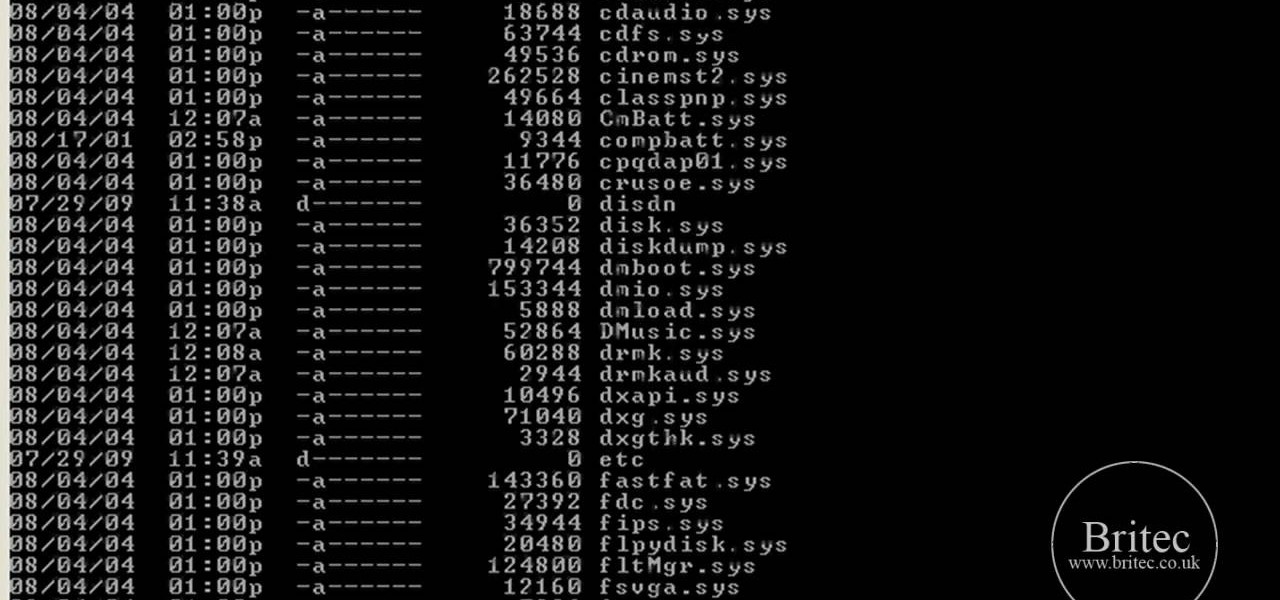
In this tutorial, learn how to fix a missing or corrupt error message "System32\Drivers\Ntfs.sys" Step 1:

In order to install Windows 7 from a USB drive, while you are running XP, you will need a pen drive. You will also need a Windows 7 DVD and a pen driver.

In this video tutorial, viewers learn how to use the Tile Visuals tool with the Voice Over application on a Mac OS X computer. This feature will dim the screen so that the user will be able to go over the Voice Over commands. To enable Voice Over, press the Command and F5 key. To tile the visuals, press the Command, Option and F10 key. Now when users navigate through the screen, only the contents over the Voice Over cursor can be visible. To return to the normal view, press the Control, Optio...

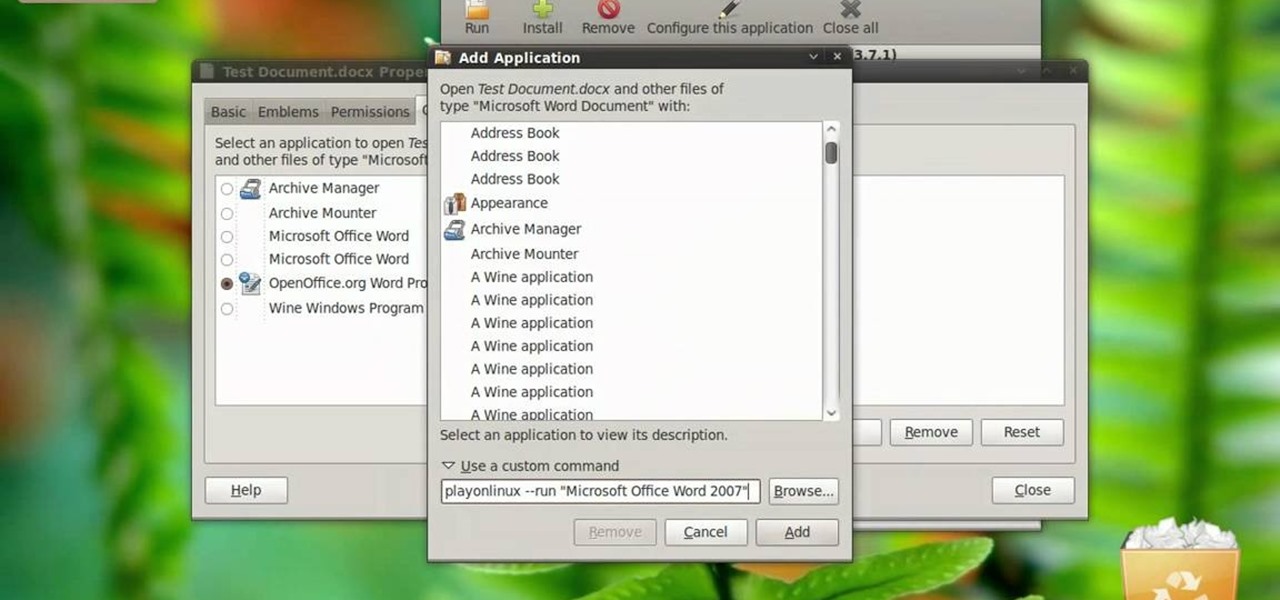
In this video tutorial, viewers learn how to open a Microsoft Word 2007 file by double-clicking it on Ubuntu 9.10. Begin by right-clicking on the file and go to Properties. Click on the Open With tab and select Use a custom command. Now type in [playonlinux --run "Microsoft Office Word 2007" and click Add. Select the custom command from the list and close the window. This video will benefit those viewers who use a Linux computer, and would like to learn how to open Microsoft Word 2007 files b...

Reformatting a flash drive will update its drivers and rid it of all data. This can help in a lot of occurances. This tutorial will show you exactly how to format flash drive properly.

In this video Guides4tech teaches the secrets of finding your local IP and MAC address in simple steps. First click 'Start' and select 'Run' on your computer. Now type 'cmd' to open the command prompt. In the command prompt type 'ipconfig/all' and press 'Enter'. Your IP address will displayed under the 'Ethernet adapter local area connection' menu. Your MAC address will be displayed as 'Physical address' under the same menu.

The instructor, Diesel, teaches how to bypass blocked websites at school like MySpace and YouTube. He shows how to make a batch file which opens the command prompt. Next, he shows how to ping a website like MySpace and how to extract the ip address of the website from the command prompt by using the mark option. Now, you can copy that address, paste it into the browser and go to the blocked site directly. By watching this video, you can easily learn to access blocked websites by bypassing them.

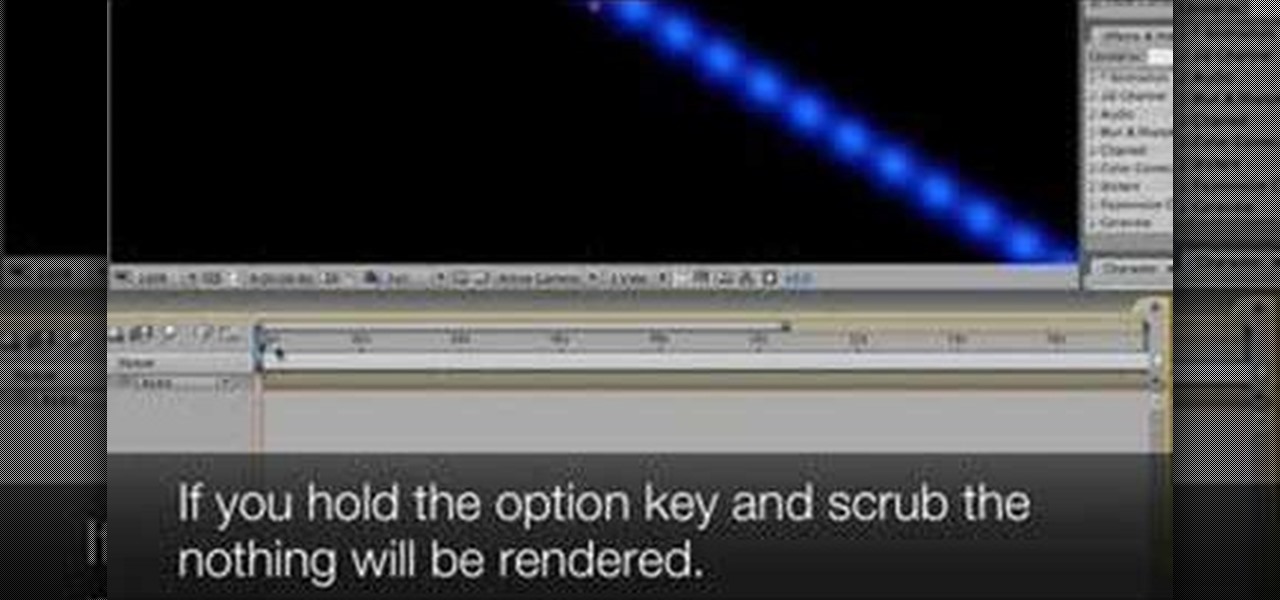
Take a look at this instructional video and learn how to scrub the audio with the program After Effects. You can go about performing this by simply holding the command key and scrubbing the timeline, then that will scrub the audio and render the video. If you hold the option key and scrub nothing will be rendered. But if you hold both the command and the option keys, no video will be rendered but you can scrub through the audio without waiting for the video to render.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

TWRP won't be ready for the Pixel 4 and 4 XL until months after release. But since you can already root with Magisk and tinker with the OS, you might find yourself in a situation where your phone won't boot, yet you don't have a custom recovery installed to fix it. Luckily, there's still a way around this.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

The main draw for Google's Pixel series is the software. It rocks a clean version of stock Android instead of a heavy OEM skin like TouchWiz, it gets frequent prompt OS updates, the camera software is downright amazing, and it has perhaps the most fluid UI of any phone. But an understated advantage of the software is how dead-simple it is to modify with root-level tweaks.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.