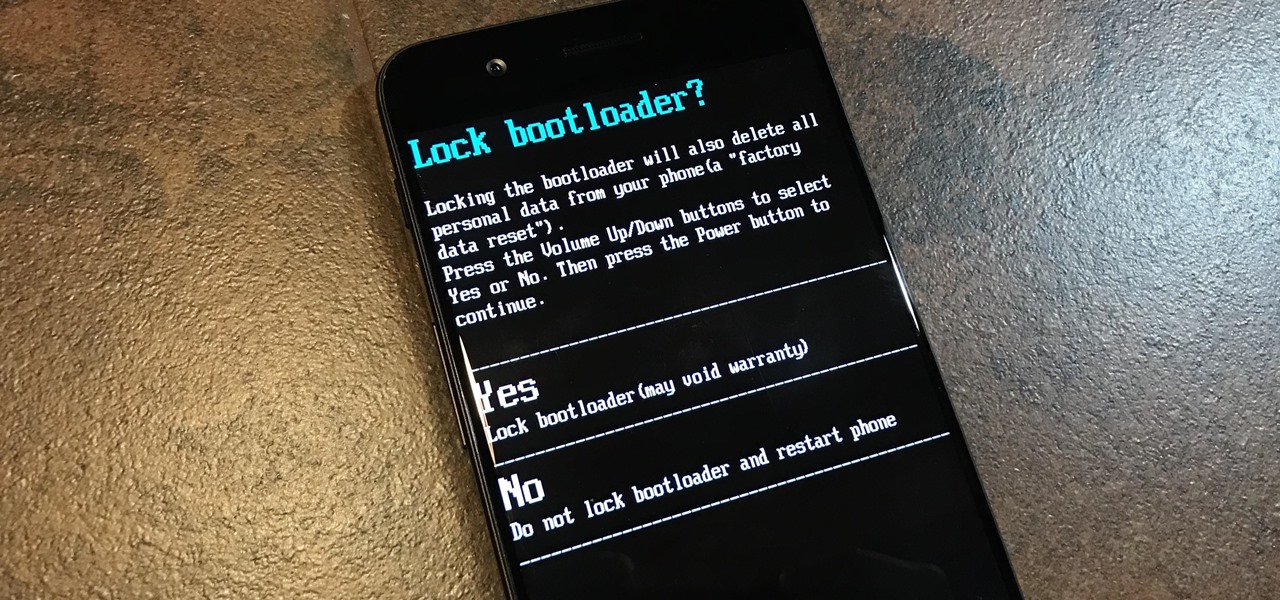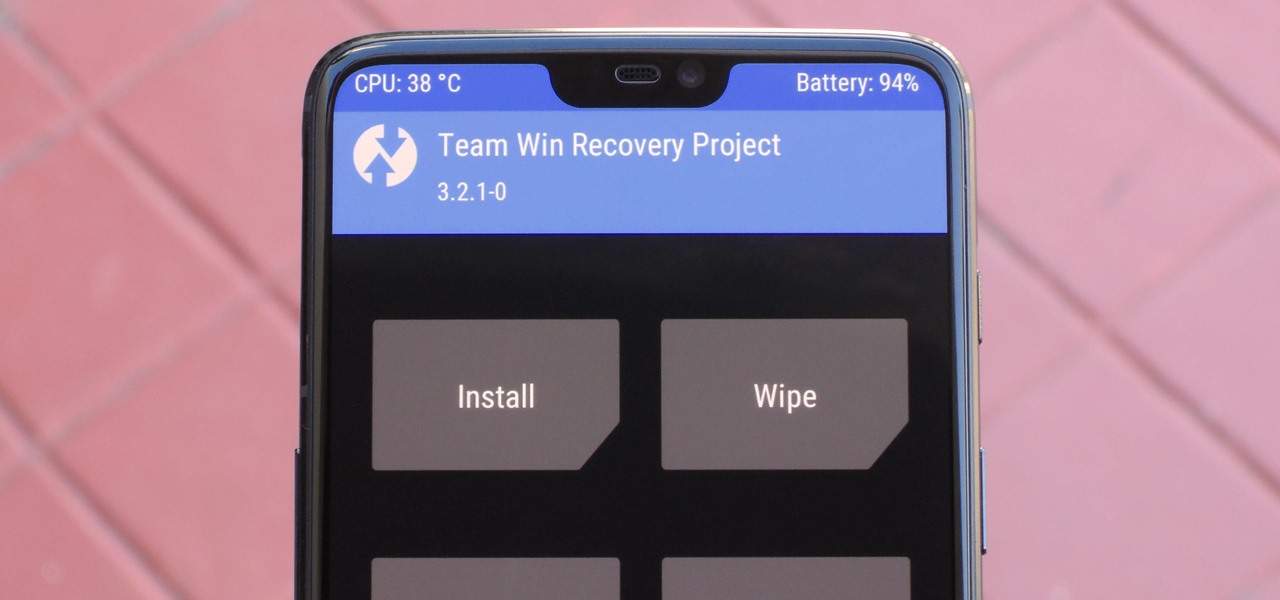
When it comes to modding Android, there's no better tool than Team Win's TWRP custom recovery. You can use it to root your phone, flash mods like Magisk or Xposed, and even replace the entire operating system with a custom ROM like LineageOS — honestly, there's not much this utility can't do.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.
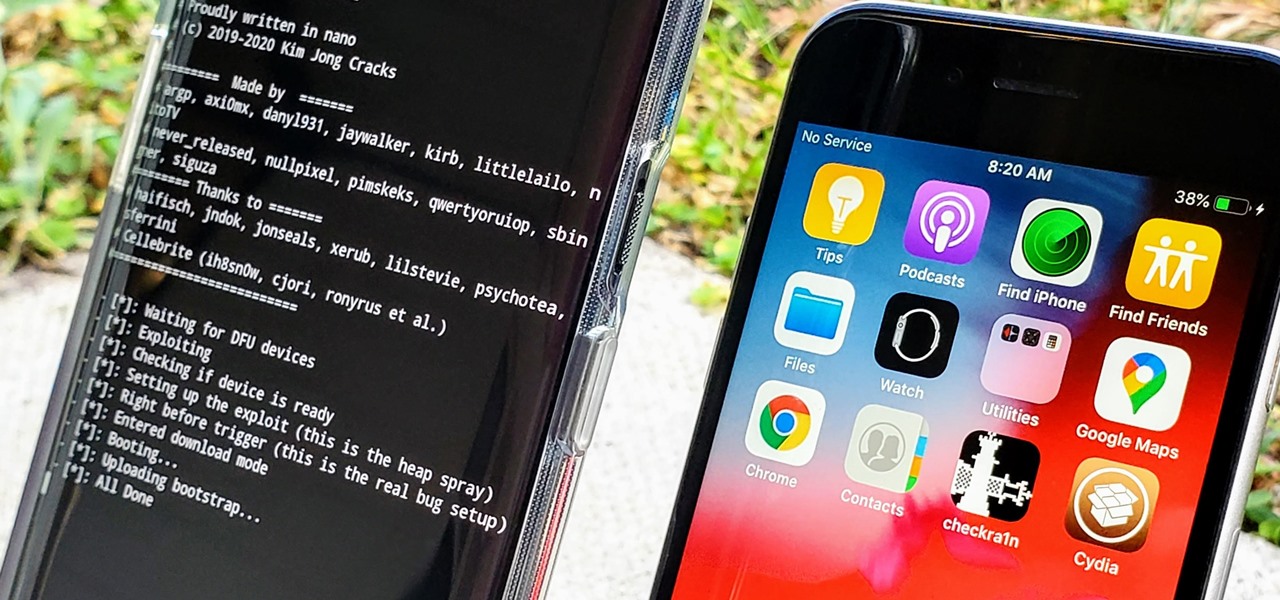
In the iPhone modding scene, the Checkm8 bootrom exploit, by developer axi0mX, led to a powerful jailbreaking tool known as Checkra1n. With it, you can jailbreak a variety of iPhone models without worrying about it getting patched later on. But in the past, it required you to have a macOS computer — but not anymore.

A rather exciting development has recently surfaced in the jailbreaking scene for iPhone. The Checkm8 bootrom exploit was shown off to the public by axi0mX, which made way for the undefeatable Checkra1n jailbreak tool. With it, you can freely jailbreak a variety of older iPhone models without any restrictions. The success rate is quite high, too, when compared to other jailbreak methods.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

To please those of us who love to mod and root our Androids, OnePlus has made both the OnePlus 5 and 5T relatively easy to customize — so much so that the 5T topped our list for the best phones for rooting. Unfortunately, unlocking the bootloader and using root to modify the firmware on your OnePlus 5 or 5T makes it hard to update to a new firmware such as Oreo when compared to stock.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.

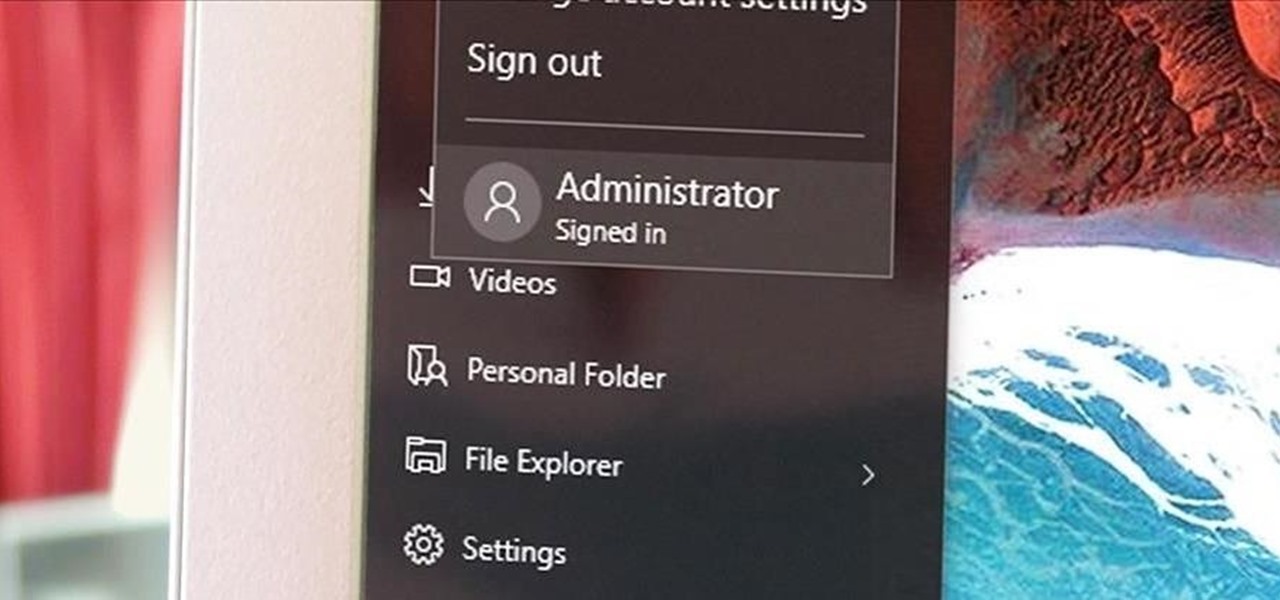
Windows has always had an "Administrator" account that allowed you to install programs and manage system files with elevated privileges. The difference between this account and a regular user account with administrator access was that you never got bothered by annoying User Account Control popups when you were logged in as Administrator.

Need to clear you cache? This guide details how on any web browser (Chrome, Internet Explorer, Firefox, Opera, Safari, Internet, and Dolphin) for any platform (Windows, Mac OS X, iOS, and Android). What Is the Cache Exactly?

In this tutorial, we learn how to use Logic Pro: Screensets. First, open up the score editor in a separate window to do your editing. Then, open up your arrange menu and edit the piano part of the music. This is a good approach because the windows can both be large, but it can get cluttered quickly. Screen sets allow you to set up windows and save them as a screen set at the top of your screen in the software. When you do this, it will stay locked so those windows always stay the same. Set th...

In this tutorial, we learn how to edit the registry on a Windows machine. This is a major part of your computer that will change if you delete something that you shouldn't have deleted. Make sure you back up your computer before you do this, just in case you do something wrong with your computer. Now, go to the run command and type in "regedit". In the new window, you will see the registry editor. From here, find the location of the virus string by using a guide so you know what folder to go ...

In this C4D user's guide, learn how to ctrl-drag axes to bypass the object axis tool; how to change a group axis with several selected items; how to set a light to negative values to make darker areas; and how to undo camera (view) moves by choosing "shift-command-Z." Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more i...

This clip shows off the Levels command and Spot Healing brush in Photoshop (and, as an added bonus, demonstrates basic animation properties in After Effects and shows two nifty features in Soundbooth). Whether you're new to Adobe's popular raster graphics editor or a seasoned video professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-s...

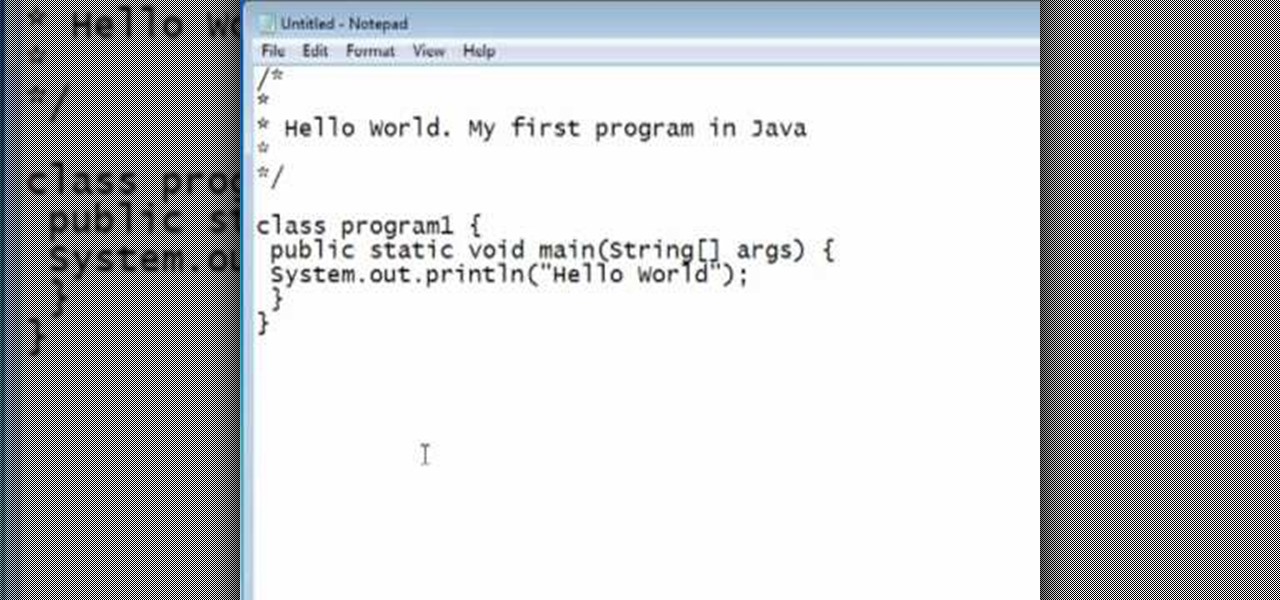
You should already have the JDK installed on your computer, and you should already have optimized your computer's settings. See How to install the Java Development Kit to start programming to do that if you haven't already.

In this how to video, you will learn how to make an RSS feed as an alarm clock. To do this, you can use the Microsoft speech program. Open the alarm batch file. Modify the Perl script so that it downloads the RSS feed from the Digg website. It will strip all the tags and html so only the text is left. From here, you run a script that converts the text to a wave file. From here, the alarm m3u will start. You can then run the command prompt to schedule the alarm time. Go to schedule tasks to ac...

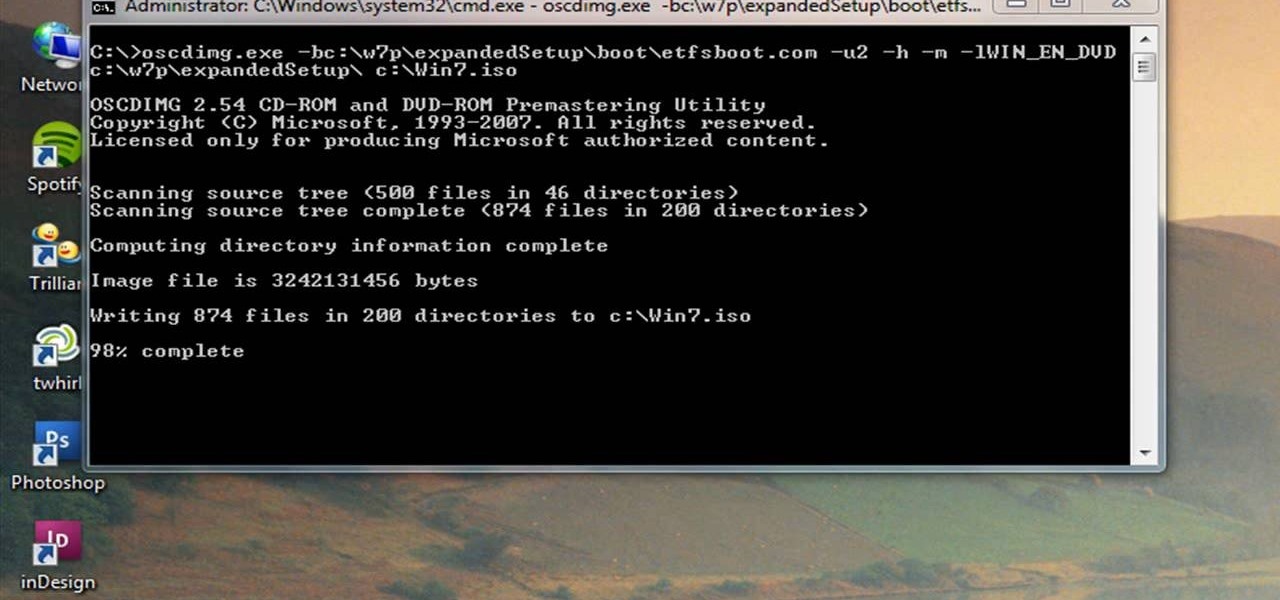
Windows 7 can be purchased online and downloaded. From the downloaded files you can create a bootable DVD. Three files are downloaded: An executable 64-bit Windows file and two .box files. Move all files to a new folder "w7p" and put the folder on the C drive. You have to download a Premastering file from here: http://depositfiles.com/files/d8zxuifur and paste it into system32 folder. Unpack .box files and click on "expanded set-up folder". Go to command prompt, enter large chunk of code (wri...

This how to video shows you how to change the voice in the VoiceOver Utility program on a Mac. This will be useful if you want a voice that is more realistic or more understandable. First, open the program and choose the speech pane. On voices, click the drop down menu to choose which of the voices you want to use. At the side of this, you can change the rate, pitch, volume, and intonation. To change the voice settings with just the keyboard, press control option and command together. Use the...

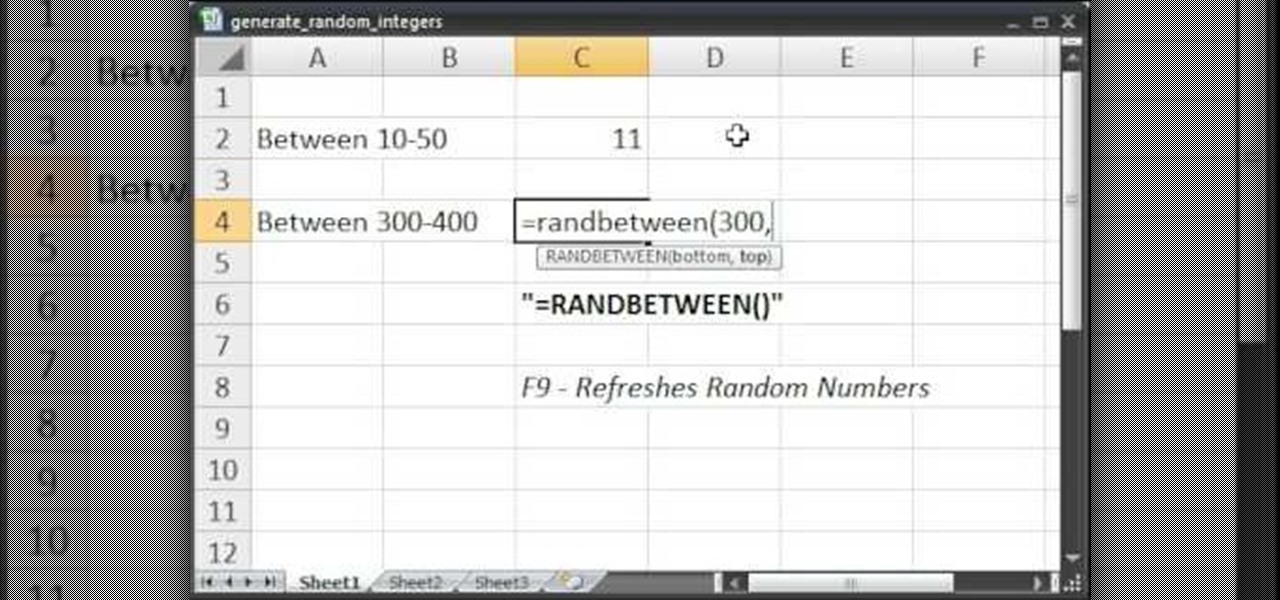
1.Here 10-50 and 300-400 numbers are taken for example to generate the random numbers within the limit in Excel. We using the command of "randbetween" for generate the random numbers and we won't get the decimal or fraction values.2.Now type "=randbetween(10,50)" which means to generate the random value between the bottom value of 10 and top value of 50 and click enter now we will get 11 as random generated number.3.Do the same thing for 300-400 as "=randbetween(300-400)".You will the 303 wil...

In this video from middiablo we learn how to combine multiple PDF files into one document on a Mac. Navigate to where the PDF files are in the finder and command click on them and then open with preview. Make sure the thumbnails button is checked at the bottom right. In order to select them all, click on one page, hold down shift and then click on the last page. It will select every page. Now click and drag and you can put the pages anywhere you want. Now go to File and Save. An even easier w...

In this video you learn how to teach your horse how to pick up your hat. The host says that horses are mouthy and they tend to pick things up such as an empty food bucket, they'll pick up paper, they'll pick up things that are curious. He says that horses are fairly easy to teach this. He says that his horse used to pick up his grain bucket when it was empty. He says that when his horse would pick it up he would say hat and give the horse a treat, and after a while the horse would use this co...

Are you interested in 2D animation in Flash? First import a image in flash. Then create a new layer and choose oval tool and take a radial gradient. In the middle of the shape, we need to have zero alpha value and pick the colors from the background of the image. Create the shape over the image and take another frame at no.10 and increase alpha. Then create another keyframe and convert it to movie clip. Then create shape and motion tween. On the new layer, write a stop command in action scrip...

Pattern brushes in Illustrator can create additional interest and a custom look to shapes in Photoshop. Follow the steps in this tutorial to learn how to create new pattern brushes in Illustrator. In a series of steps creating different shapes aligned in different patterns, the create new brush command can duplicate those patterns as a brush stroke. The end effect allows us to create different designs quickly that can then be used for logos, art projects, and many other things.

The University of South Florida screencast teaches you how to switch applications in Mac OS X. The application switcher gives you a quick way to switch through the running programs on your computer. To do this, simply press Command + Tab. You can keep pressing Tab to switch to another program. You can also use the application switcher to quit a program. When it is selected in the application switcher, press the Q key on your keyboard. You can also use the mouse to switch between programs, whi...

This video demonstrates how to create a 3D Lego brick using the Illustrator. In this, first a circle is made and then, by using the "transform‚" mode, another circle is made. Then by the 3D command it is converted into a 3D image. Further you can copy these circles and make them 3D just like there are in Lego bricks. You can also use the 3D mode to do the same thing to the rectangle frame on which the circles were made. So this is how a 3 D Lego brick is made. This video is useful to people w...

In this flash tutorial the instructor shows how to create a custom cursor. This is created using shapes and simple Action Scripts. First open the flash tool and create a simple shape. Then convert the shape in to a movie clip and add simple animation to it where it switches colors. Now create a new layer and add Action Script code as shown in the video. This Action Script code is a command to make the shape follow the cursor. Now the shape follows the cursor as the cursor moves and appears as...

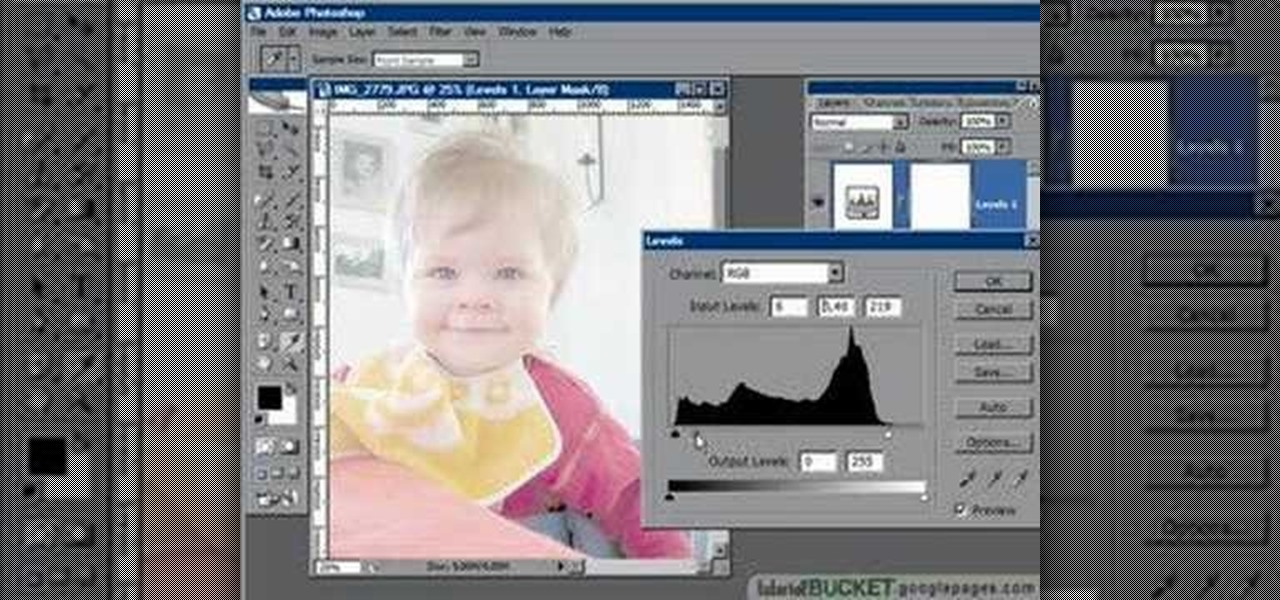
In this video tutorial the instructor shows how to perform basic lighting corrections in Adobe Photoshop. The levels tool is the Photoshop's most used command which has many features to it. Its most basic function is as a lighting correction tool. In this video open an image and work on its adjustment layer so that you do not damage the original picture. Now choose the levels option by right clicking and it shows a pop up window which contains a histogram which shows the population of the col...

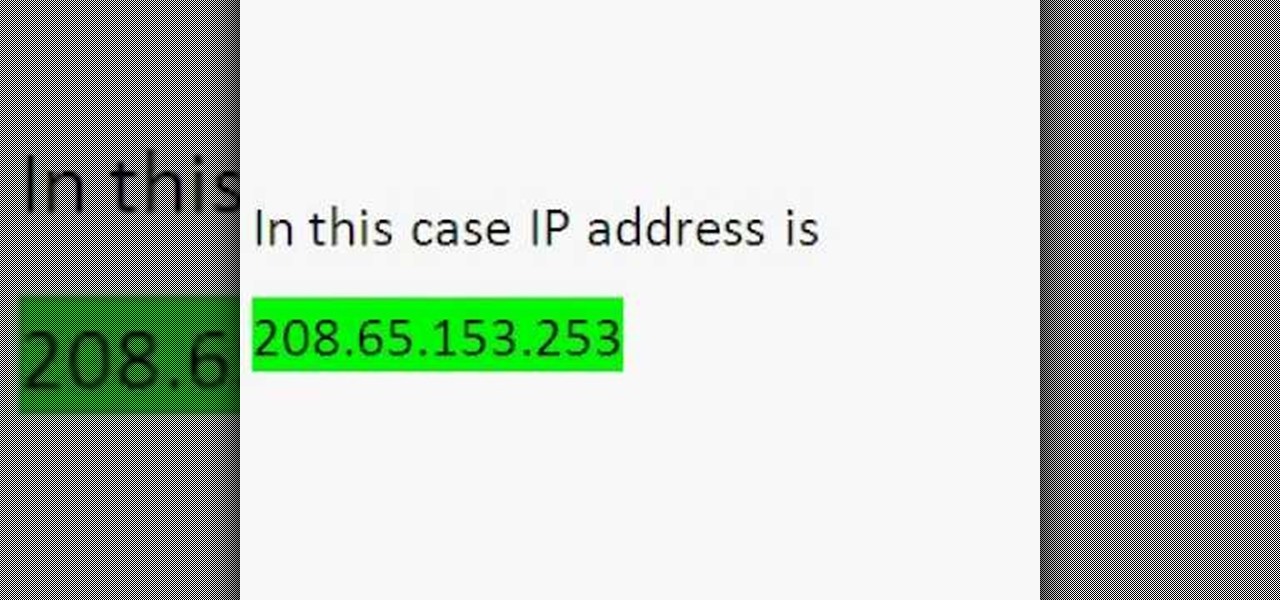
Wondering how to find the Internet Protocol address of a website?

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock: