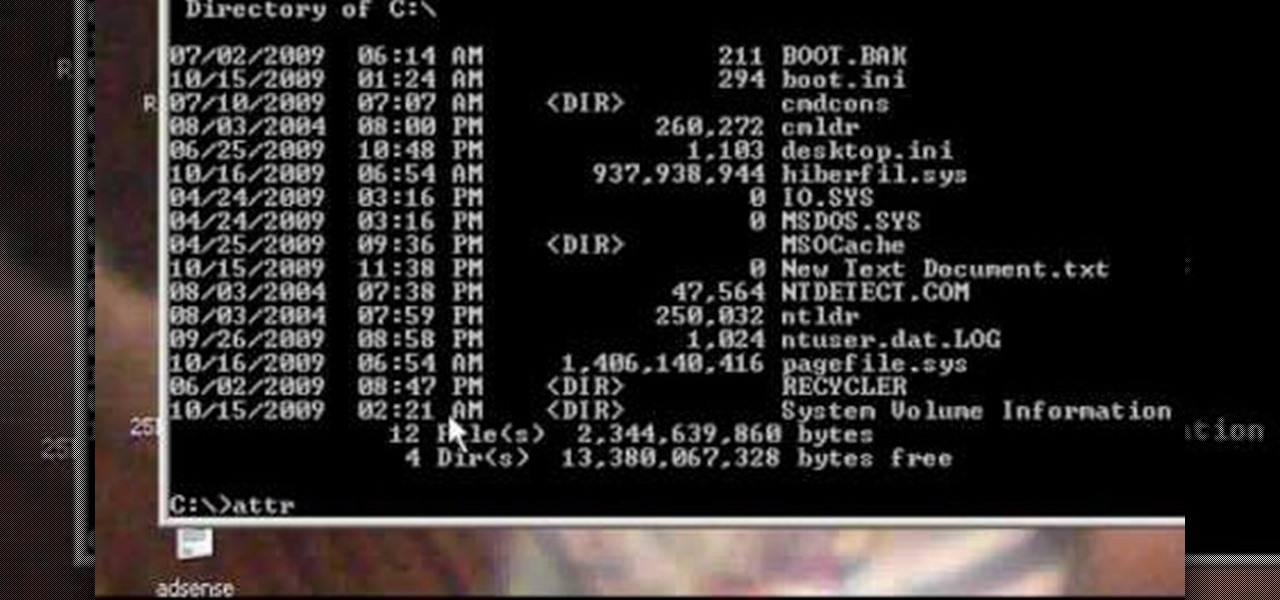
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

After years of user complaints, Samsung is finally letting us remap the Bixby button without the need of a third-party app. The new feature requires One UI a simple app update to Bixby, but there's one major downside: Samsung won't let you remap the button to open other digital assistants like Amazon Echo, Microsoft Cortana, and Google Assistant. Luckily, there's an easy workaround.

Putting your Galaxy S9 in Immersive Mode lets you truly enjoy the gorgeous display that Samsung is so famous for. You can't have it set on at all times, however, so you'll still have to deal with the status and navigation bars that cut the phone's aspect ratio down to that of a standard phone. But if you're willing to dig a little deeper, there are ways to go full Immersive Mode on your S9 for good.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

ADB and Fastboot are probably the most essential tools for any Android aficionado. They can do everything from backing up your device to unlocking your bootloader with a few simple steps. This paves the way for many new tweaks and customizations that weren't possible before. The required platform works with the three most popular computer operating systems, too, which is good news for everyone.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

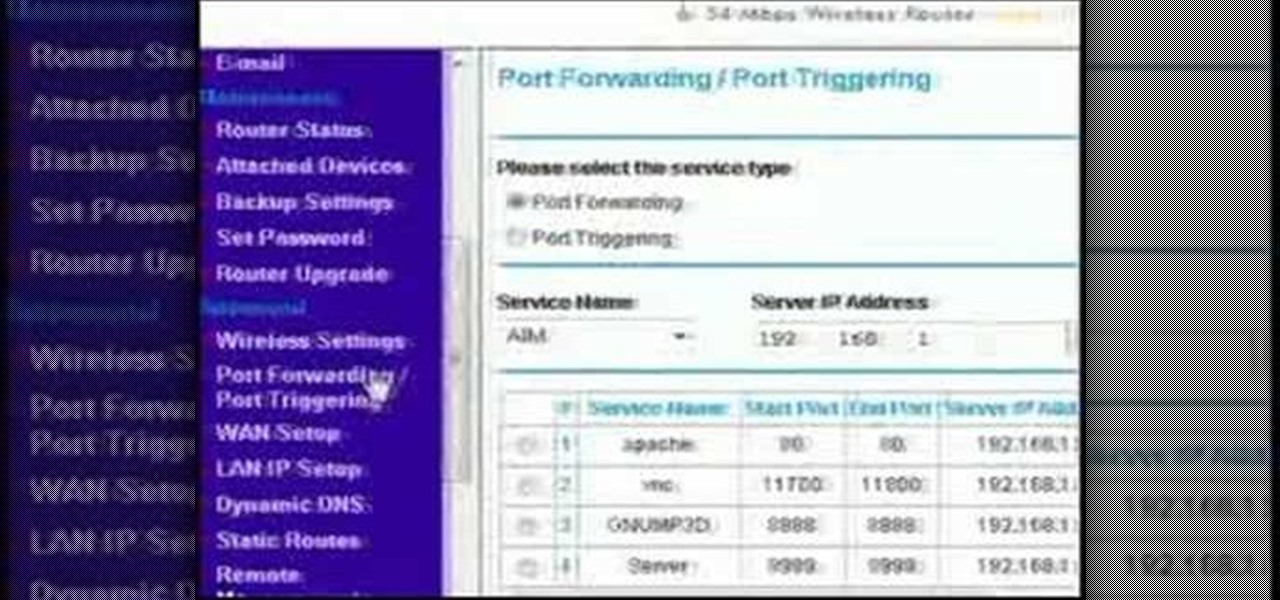
This video discusses how to bypass your router to access your server. In the search window type in CMD to open up a command prompt. Then type in ipconfig to bring up the ip configuration. You want to look for the ip address for the default gateway and the one for your computer. They should both start with 192.168. Once you find them open up internet explorer and type in the ip address for your default gateway and it should then prompt you for a user name and password. Log in and look for a po...

Forget keyboard commands, try out some simple mouse gestures to control your Windows computer. You can customize mouse gestures that let you take command of your PC in ways you never thought existed. If you prefer the mouse over the board, this is for you!

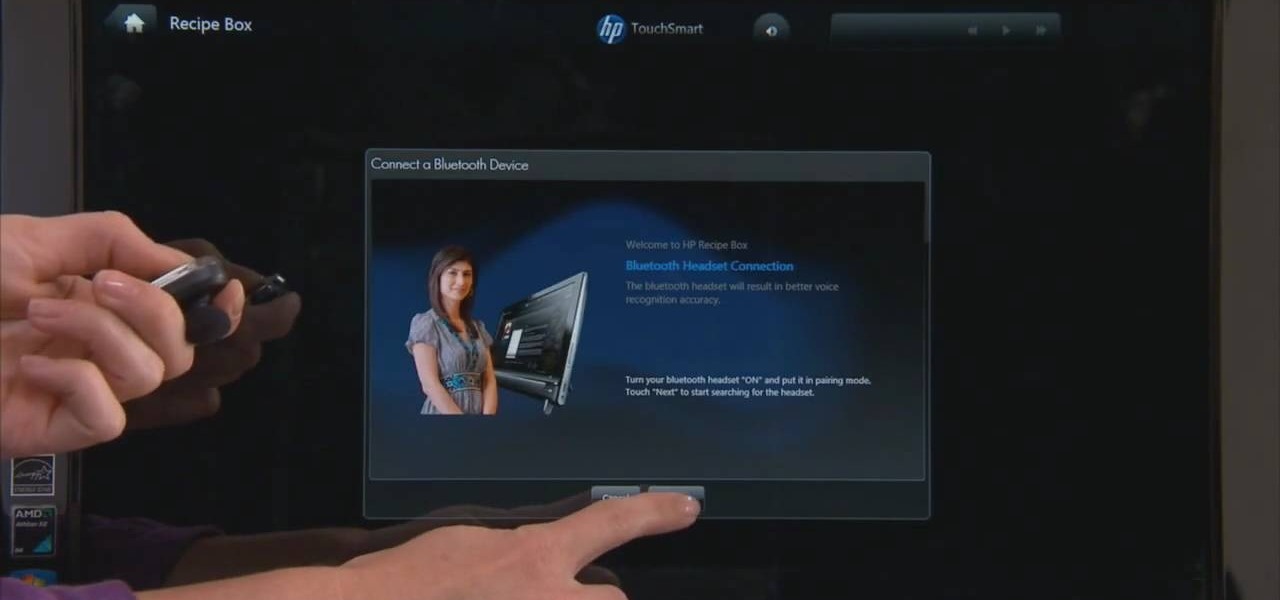
HP TouchSmart is a powerful PC with innovative features. Using the HP TouchSmart Recipe box you can set up the blue tooth headset. The recipe box provides an easy way to work with you recipes using voice commands. You can set up your blue tooth head set to use the voice command feature of the recipe box. This gives the freedom to walk around your kitchen while cooking. The microphones embedded in the TouchSmart can also be used for this purpose but the blue tooth head set gives a better voice...

First of all open an image which shows many different lights in a night background. Now make a new layer now set the color of background to black by first and the foreground color set to white. Click the background for the bottom of the left bar and then pressing 'd'’. Next select the 'gradient' tool. Make sure to select the style from the foreground to background. Select the 'mode' to 'normal' and ‘opacity’ to '100%'. Now drag the top right hand corner to the bottom of the left hand corner. ...

1)Open image, go to channel. Look for the channel that gives the most contrast by going through them one by one.

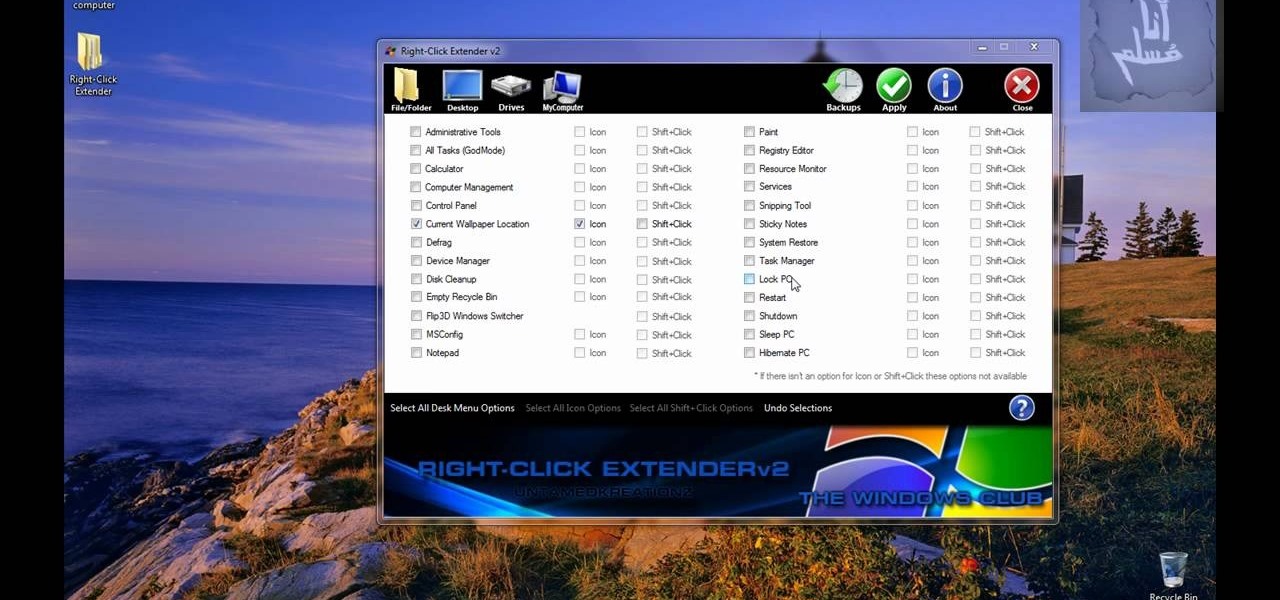
Tired of being limited with your right-click options in Microsoft Windows? There's a program that could help you out, and it's called Right-Click Extender. Insert many different additional items to the right-click context menu.

Tutvid shows you how to add flare and dramatic color to your raw camera images (usually the format of a DSLR). In a step-by-step guide with narration, Tutvid takes you through the process of using CameraRaw (used as an extension of Photoshop but never really brings it in photoshop) to add desired colors to your picture. Pull up your raw file in CameraRaw, and press "Command" or "Ctrl + R" to open up the editing panel. With an example, he shows you how to bring out lights in underexposed (dark...

There's plenty of reasons why one would want to convert a webpage to a PDF document. And there's numerous ways on how one can convert that web page (HTML) into a PDF file. Check out this video tutorial on how to convert webpage HTML to PDF on Ubuntu Linux.

Pull off this easy prank, and – without causing any permanent damage – watch your coworker squirm with frustration.

Systm presents this detailed tutorial on how to make a custom Star Wars style light saber. Luke, Darth and Obi-Wan's Lightsabers were pieced out of junk piles. David shows you how to build exact replicas and an original design from The Custom Saber Shop. Then he picks a fight with Patrick.

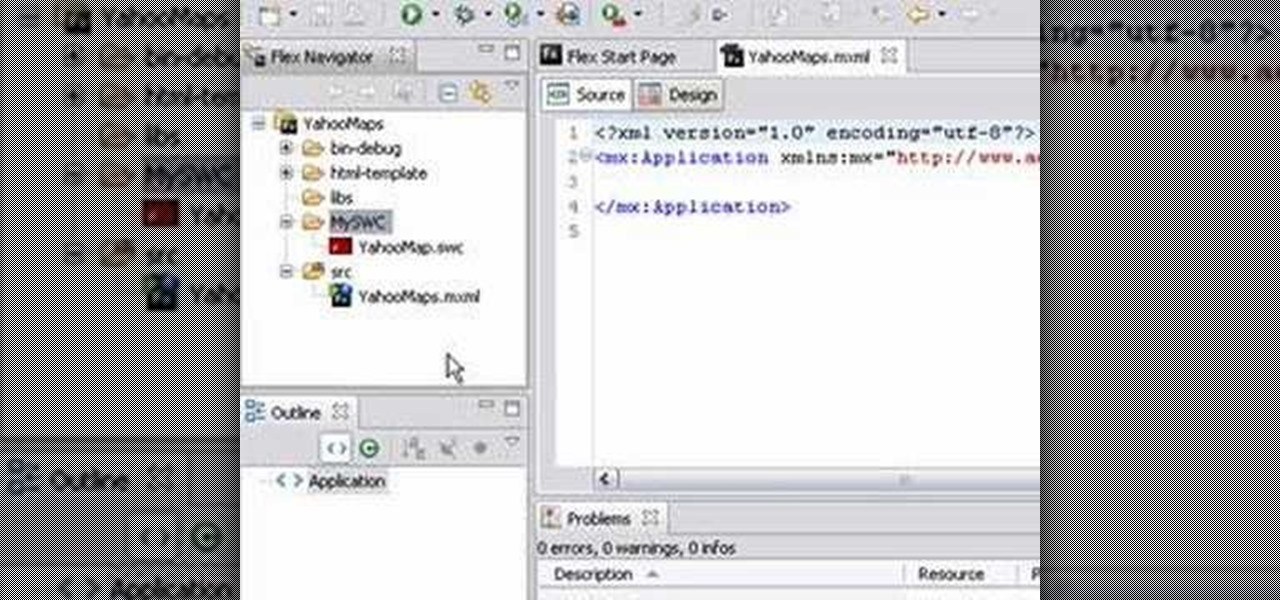
This video tutorial series shows you how to use the Yahoo Maps AS3 API in Adobe Flex 3. This new API gives you the ability to place Yahoo maps directly into Adobe Flex 3. Mike Lively Director of Instructional Design at Northern Kentucky University will be taking you through this tutorial.

In this video tutorial, Chris Pels shows how to use the ASP.NET IIS Registration Tool to configure ASP.NET. First, see how file extensions are mapped to ASP.NET in the IIS Manager on a global and web-site-by-web site basis. These script maps provide the basis for configuring individual ASP.NET applications to run under a specific version of the .NET Framework. Next, see how aspnet_regiis.exe, the IIS Registration Tool command line utility, is specific to each version of the .NET Framework and...

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update today with a few simple steps.

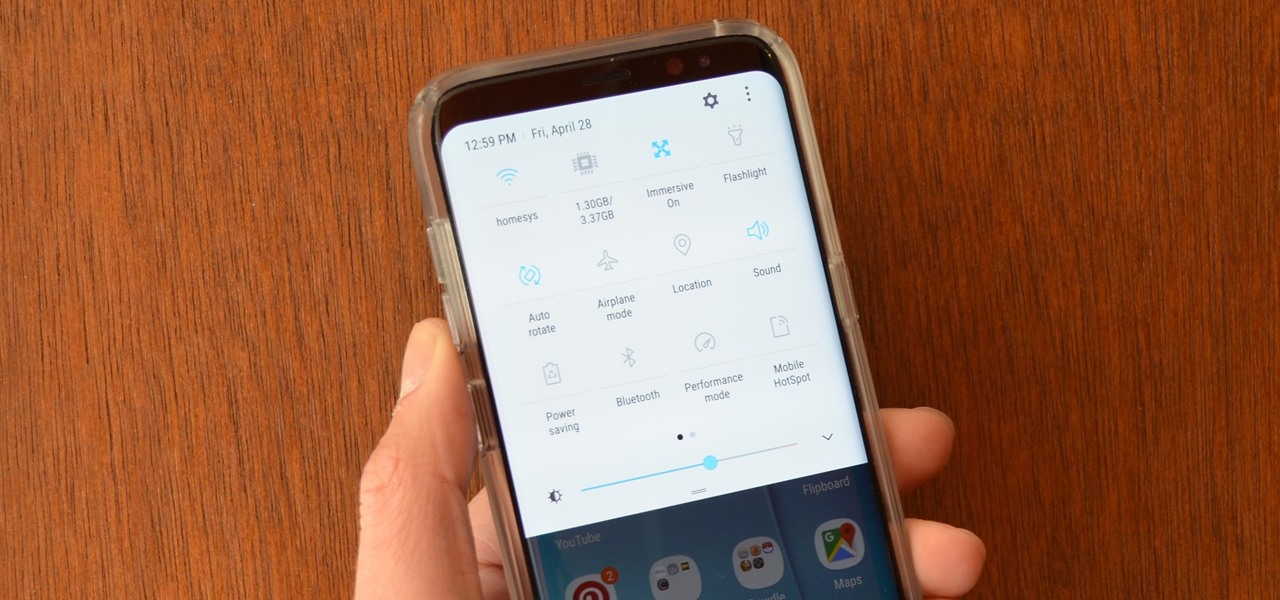
Up until now, enabling full-time Immersive Mode on an Android device has been a tedious task which required you to run individual ADB commands each time you wanted to toggle it on or off. This was a shame, too, since Immersive Mode helps reclaim lots of screen real estate by auto-hiding your navigation and status bars.

If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Have you ever gotten the error message, "BOOTMGR is missing" on your PC? Well, if you have check out this video. In this tutorial, learn how to remedy and fix this problem in no time.

This video explains how to use the Speech Recognition tool on the Mac, which allows you to speak most of the commands that you use on the computer. To enable speech recognition, go the Apple menu, select System Preferences and click on Speech. Then click on “On” next to Speakable Items, and click OK.

Clintprexis teaches viewers how tot delete a virus manually without using anti-virus. First, you have to kill the process that keeps the virus running. You can do this by opening up test manager by clicking CTRL+ALT+DEL. When you open task manager go to the process tab and kill the process that keeps it running. Now, you have to figure out which process is running the virus. You have to do research to find this and it is usually a 'wscript.exe'. Now you'll want to go to Start then go to run a...

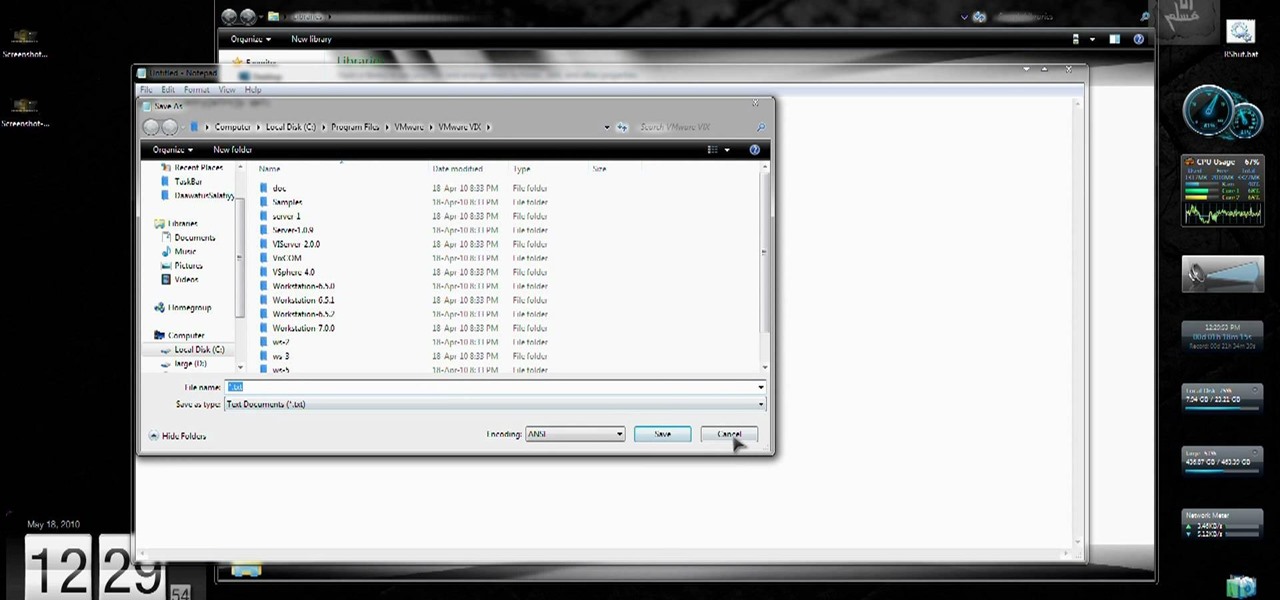
In this video you will learn how to get past website blocks on your school network. Some school computers have command prompts blocked. If this is the case then you will want to open a notepad. In the notepad type command, then save as something school related, making sure the file name ends with .bat. Do not save it on the desktop, but rather in a folder deeper on the unit. Once you've saved it, make sure no one is looking, then open the file. It will bring up a blank black window. In the bl...

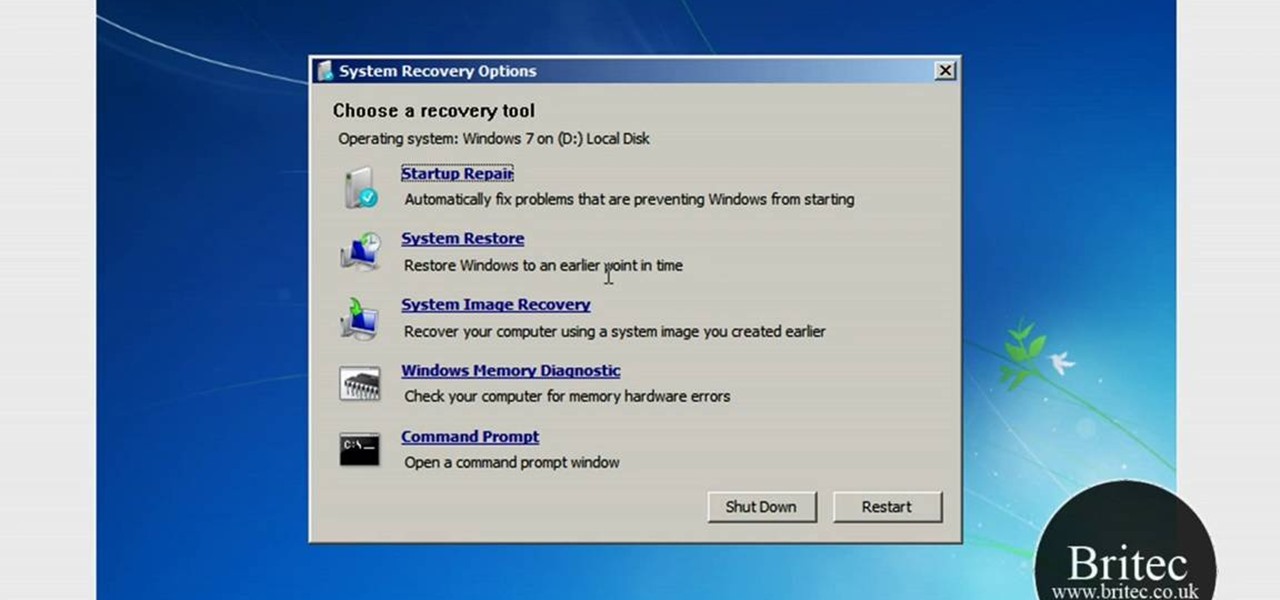
This video tutorial from Britec09 presents how to backup and restore Window 7 registry.First, press Start button and enter regedit command into Start Search area.Registry editor window will open, click File-Export.This option works on all Windows operating systems.Type file name - registrybackup and click Save. You can save it wherever you want, but in this video it was saved to Desktop.Next step is to reboot to Windows DVD. Insert you Windows DVD and reboot computer.Press any key to boot fro...

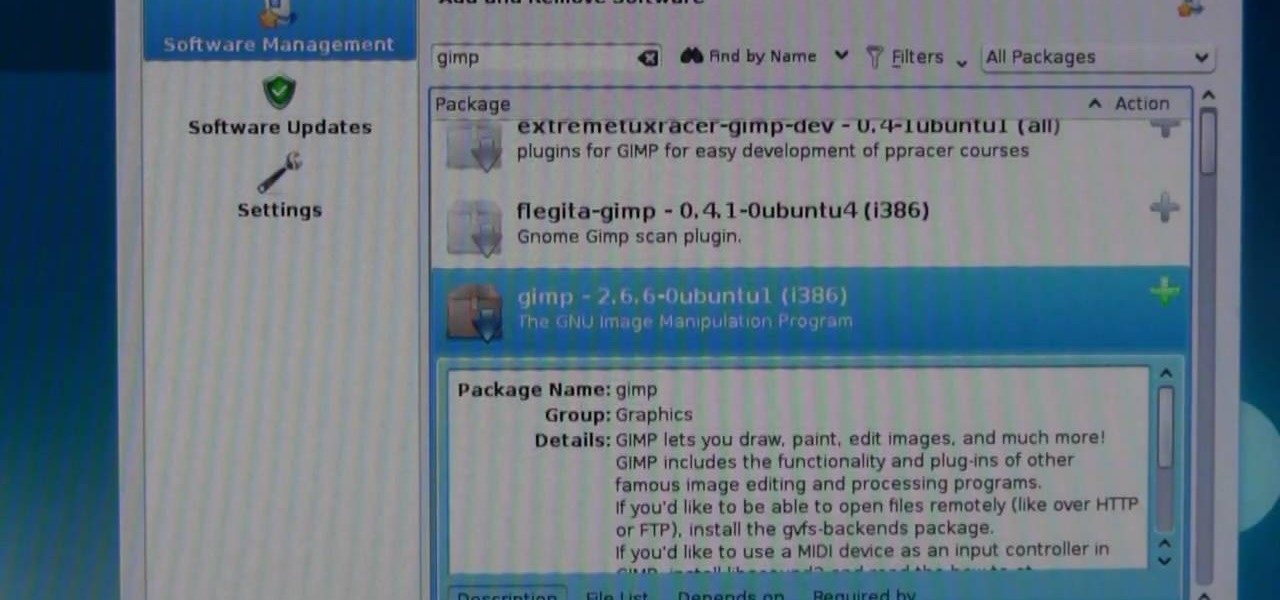
Finding Linux hard to handle after using Windows? Well this should help, here is how to install software on Linux. Start off by clicking on application launcher. Here go into applications, then into 'system' where you should find software management. In this program go straight into the settings and then edit software sources. Under 'downloadable from internet' make sure every option has a check against it. Now press the software management tab on the side. Now this is where you can get which...

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.