Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Hello friends. This is actually my first how to.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

If you installed Android 9.0 Pie, you might have enjoyed trying out some of the new features in the latest version of Google's OS. However, change isn't always a good thing, so you might be wishing you could downgrade back to Oreo right about now. Good news — you can.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

An attacker can create three, five, or even ten new Netcat connections to a compromised MacBook with one command. Performing complex post-exploitation attacks might otherwise be difficult from a single shell without this essential trick.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

There's safety in numbers. Protect yourself as you explore the unpredictable world of Minecraft with a pack of wolves. You can use bones to tame wolves and keep them as your pets. Minecraft is a lot safer when you have a pack of wolves who do whatever you command.

Hiding icons from the system tray is easy, but what if you want to get rid of the program entirely? This tutorial shows you how to use the command prompt in Windows to create a service that will allow to delete all extraneous programs.

This only works for the PC version of the game, since you will need to enable the dev console to be able to get it. Once you do, you can use a console command to get access to a room that gives you all the items in the game.

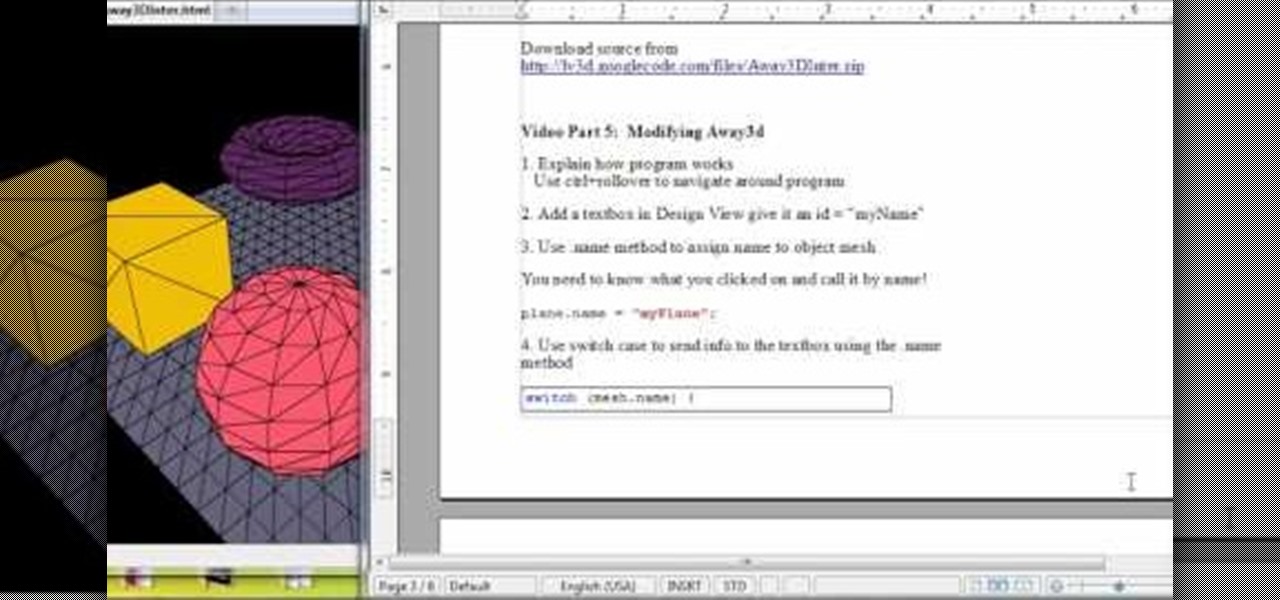
Set up your Flash-based meshes in Away 3D to be responsive to user clicks. This particular tutorial will display the name of the image when the user clicks on it, and you're also taught how to use the ctrl+rollover command to navigate the program.

This tutorial will show you how to enable the Windows Vista Administrator account using either the Command Prompt or Computer management. It's easy! So easy, in fact, that this home-computing how-to can present a complete overview of the process in about three minutes' time. For details, and to get started using the Admin account on your own Microsoft Windows Vista PC, take a look.

This episode of TUTCAST shows you how to get rid of blemishes in your photos using Photoshop. For this demonstration the patch tool in Photoshop is used to clean the blemish. Use the elliptical marquee tool to select the area including the blemish as shown and then feather the selection using the selection modify feather command. Use the patch tool to patch the area with the blemish and use the clone stamp tool to clean up the unevenness as demonstrated.

It was bound to happen with all those numbers floating around in your brain – you've forgotten your Windows password. Here's how to recover it.

This video game tutorial demonstrates how to build and script a flag with a simple load URL command in Second Life. Scripting a flag isn't that hardest thing to do, once you get the hang of it.

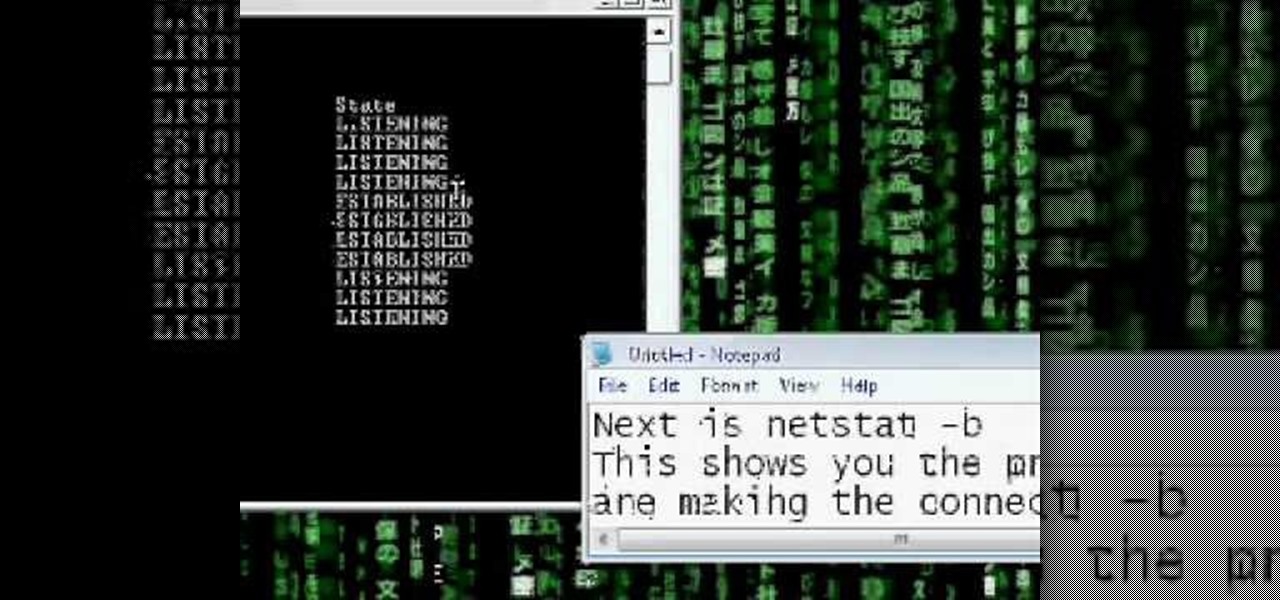
Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

With a Mac, you always have a dictionary and thesaurus close by in any Apple application. Simply highlight the word and hold down command control D. For a step-by-step walkthrough of the the look up process within Mac OS X, watch this video tutorial.

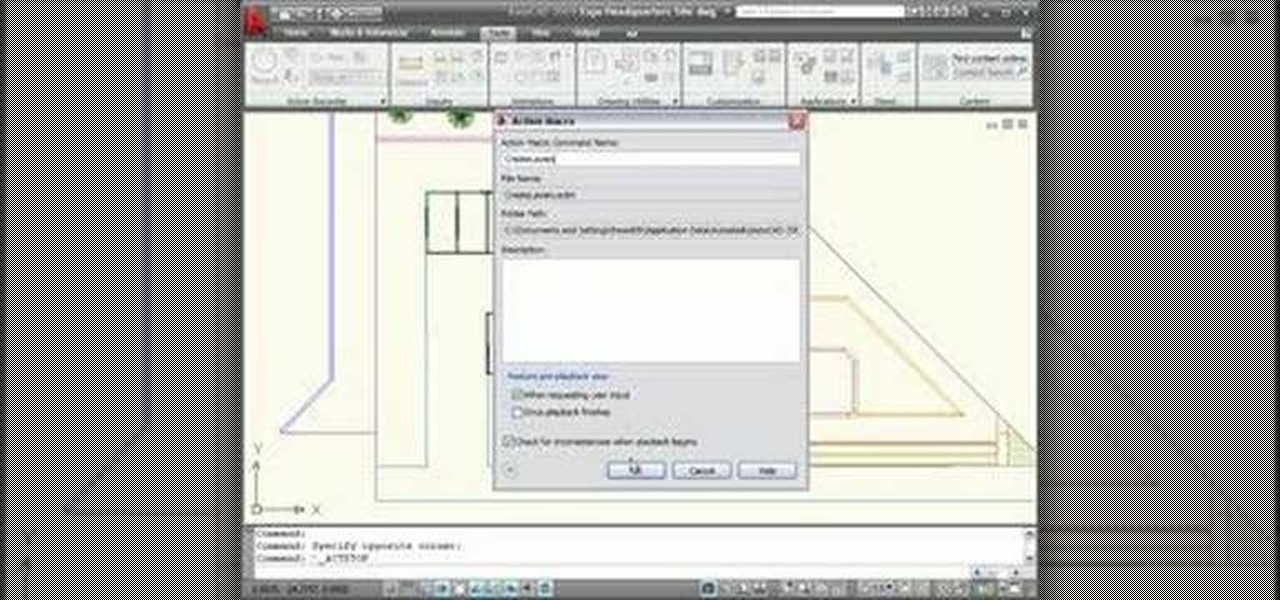
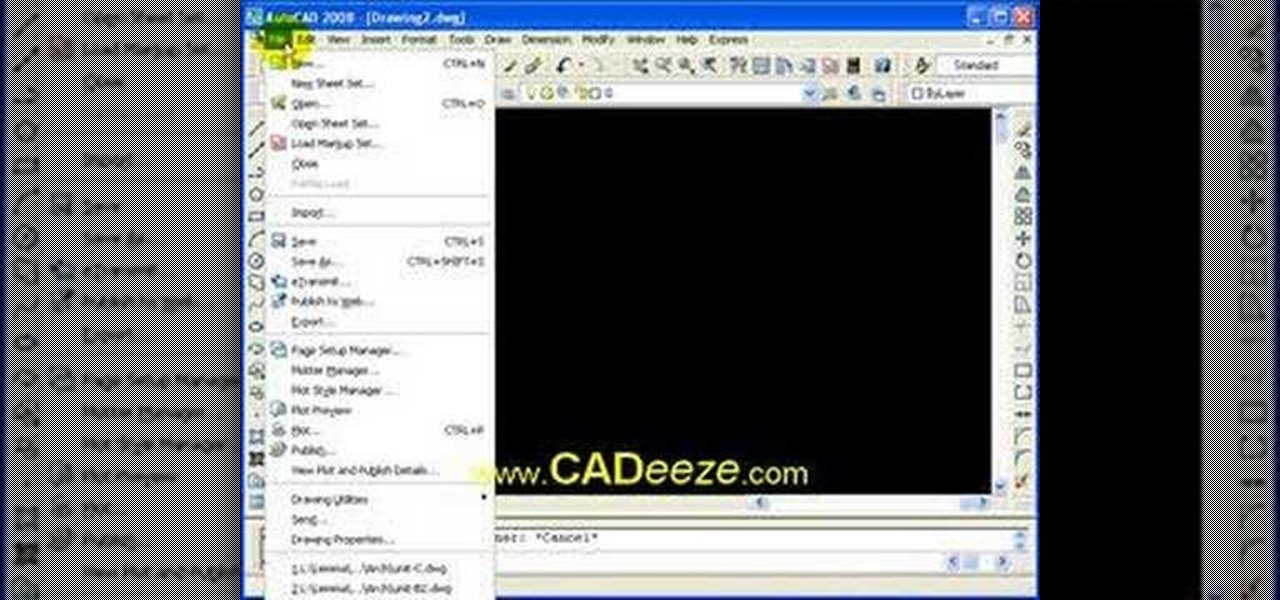
Heidi Hewett demos the Action Recorder feature in AutoCAD 2009. Recording actions with the Action Recorder can increase your productivity by automating repetitive tasks you have to perform on every AutoCAD 2009 drawing. You can record actions from the command line, toolbars, ribbon panels, and more. See how in this AutoCAD 2009 lesson.

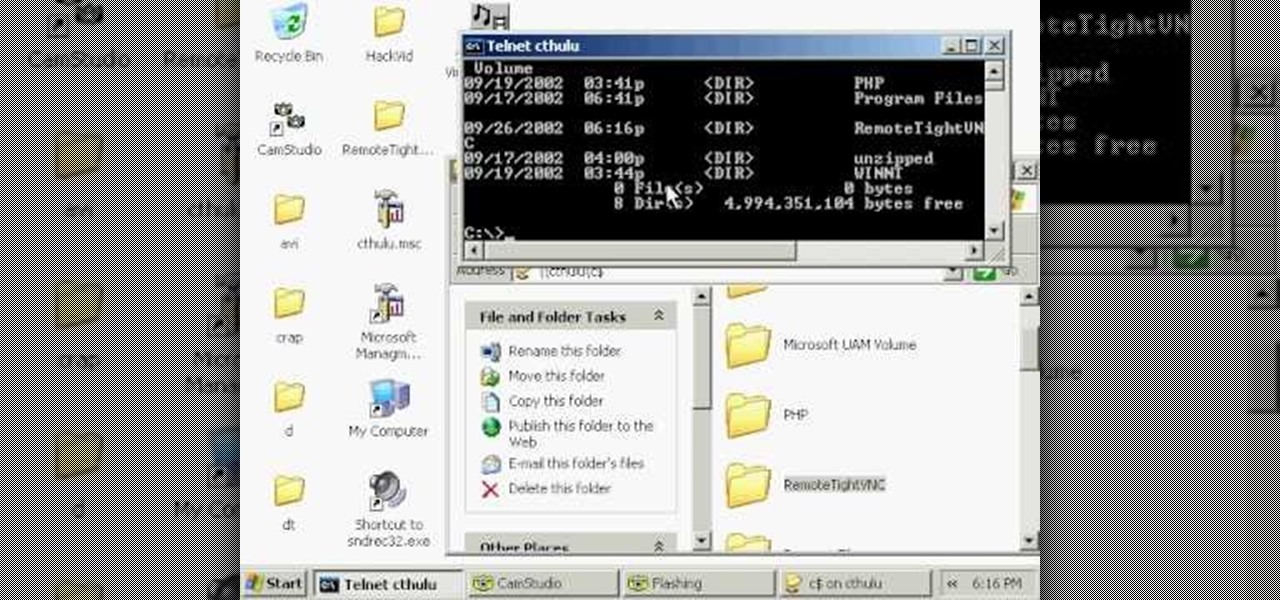
In this video tutorial, you'll learn how to install VNC, or Virtual Network Computing, remotely onto a Windows machine for GUI access. This tutorial assumes you know how to start a session and get into active command line access in a remote Windows PC. For step-by-step instructions, press play.

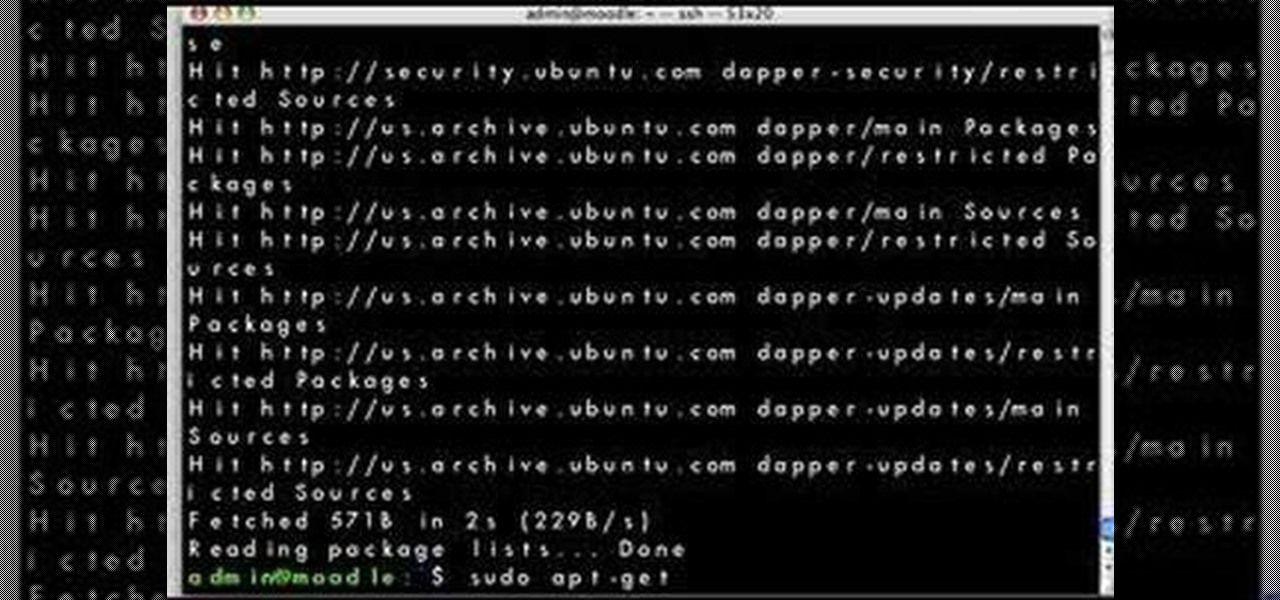
Looking for a simple way to update your Linux distribution? This video tutorial demonstrates how to upgrade your Linux distribution via the apt-get command in the terminal. To get started using the apt-get update tool, press play!

With the Freeze Panes command in Microsoft Office Excel 2007, you can make sure specific rows and columns stay visible while you scroll. Take a look at this instructional video and learn how to freeze and unfreeze rows and columns, and make viewing your worksheet a snap.

This video tutorial shows how to train a dog to lay down. "Lie down" is a simple, basic, and useful word command to teach a dog.

AutoCAD 2008 Tutorial covers the Autocad interface, toolbars, pull-down menus, command line, and accessing commands.

Has your dog ever gotten off its leash, or made a quick escape from an open door? Training or teaching your pup to come to you on command is an essential part of obedience training. With a little practice, your dog will learn how in no time!

Photoshop Mama shows you how to use the Match Color command in Photoshop to match the color temperature from one image to another.

This Photoshop tutorial will show you one method for changing clothing color utilizing the Select Color Range command and fine tuning techniques to use on the mask of the Hue and Saturation adjustment layer. Also shows how to clone.

In this tutorial learn how to eject a stuck CD using a terminal command on your Mac OS X computer.

The free download manager wget lets you download all the files on a page or directory with a single command. It also allows you to resume downloads after getting disconnected letting you start where you left off instead of starting the download at 0% again. Check out this tutorial and see how to install and use wget.

This Premiere Pro CS3 tutorial walks you through a few of the quickest and easiest methods for copying motion properties and video effects from one clip in a sequence to other clips.

Learn how to install PHP and some of the basics of PHP programming including some basic commands including conditionals and booleans for creating scripts and command line interfaces.

The introduction of transparency has been quite controversial in print production over the past few years, though the fact is that for most transparency in Adobe files works just fine. However, those of us out there with older RIPs may have issues printing transparency. In this video you'll see how to flatten transparency in your PDF files before you ever hit the Print command.