Every time you place an image in InDesign, chances are you have to execute a fitting command to make it fit in the frame or area that you specified. In this video of the Creative Suite Podcast Terry White will show you ways to do it most efficiently. You’ll also see how to better integrate the Bridge into your workflow.

Google released the first build of Android 12 almost exactly one year after dropping Android 11, which is remarkable in the midst of a global pandemic. But you can tell the Android engineers have been hard at work while quarantining, because the latest OS version is absolutely packed with new features.

It took a while, but the premiere custom recovery for Android is now available for Google's Pixel 4 and Pixel 4 XL, so it's finally open season on root mods.

Up until Android 5.0 Lollipop, the actual text of incoming notifications would scroll by in your status bar. These ticker style alerts didn't pop on screen or interfere with what you were currently working on, but you could still read the message. They were replaced by the new "heads up" alerts, but you can still bring them back.
You may have noticed your Note 10 came with quite a bit of bloatware. Even the unlocked version of the phone comes with Facebook preinstalled, and if you bought it from a carrier, it's much worse. Luckily, there's a way to remove any apps you don't want, and you don't need root or a paid app to do it.

The first thing you'll always have to do before getting your customization game on with most phones is to unlock the bootloader. Doing so opens the true potential of the device, allowing you to root, install TWRP, Magisk, custom ROMs, and other mods. No matter your wants or needs, there's no way around it — the bootloader must be unlocked to modify the system.

Android 9.0 Pie moved the status bar clock from the right corner to the left to accommodate phones with notches, but there's one major downside for Samsung users: since no Galaxy phones have a notch, all this did was take away space for the notification icons that would otherwise start from the left corner.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Samsung isn't known for its timely rollout of major Android updates, and Android 9.0 Pie won't be an exception. If we go by their Oreo update timeline, we can expect Android Pie to officially touch down for the Galaxy S9 and S9+ sometime around November, with the final version rolling out the around the first quarter of 2019. But a leaked version of the beta has already hit the internet.

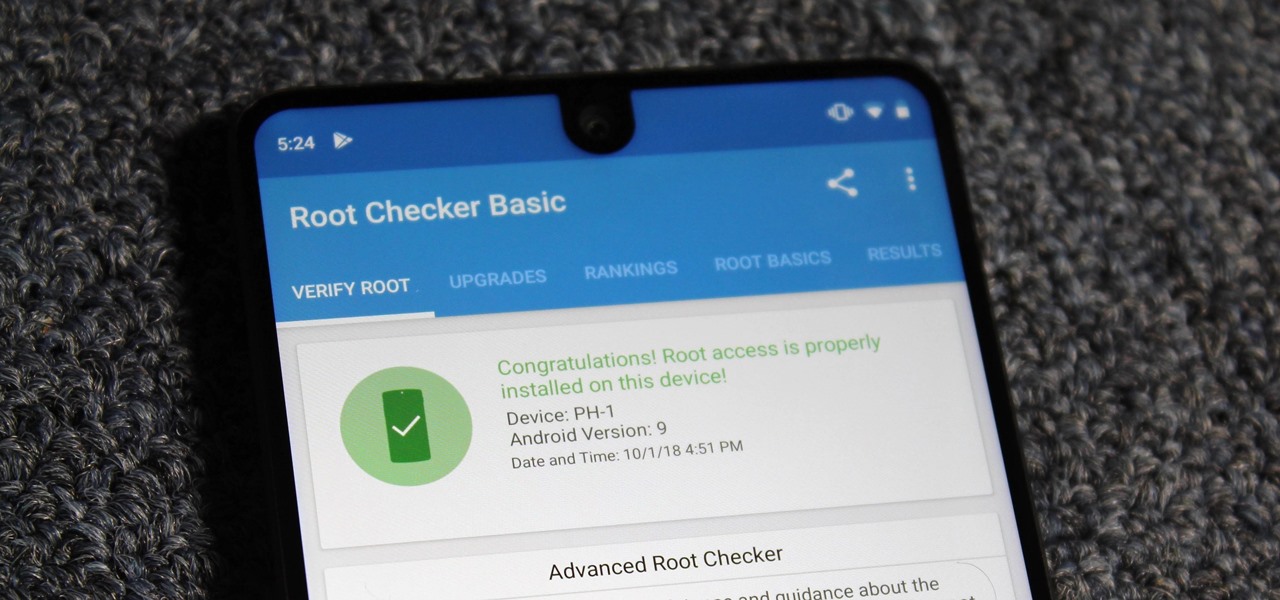
Despite its rocky start, the Essential PH-1 has a lot going for it. Not only does it get consistent security patches and system updates hours after the Pixels, but like the Google-developed lineup, it's also great for rooting. Not only is your warranty not void with rooting, but the process is pretty straightforward.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

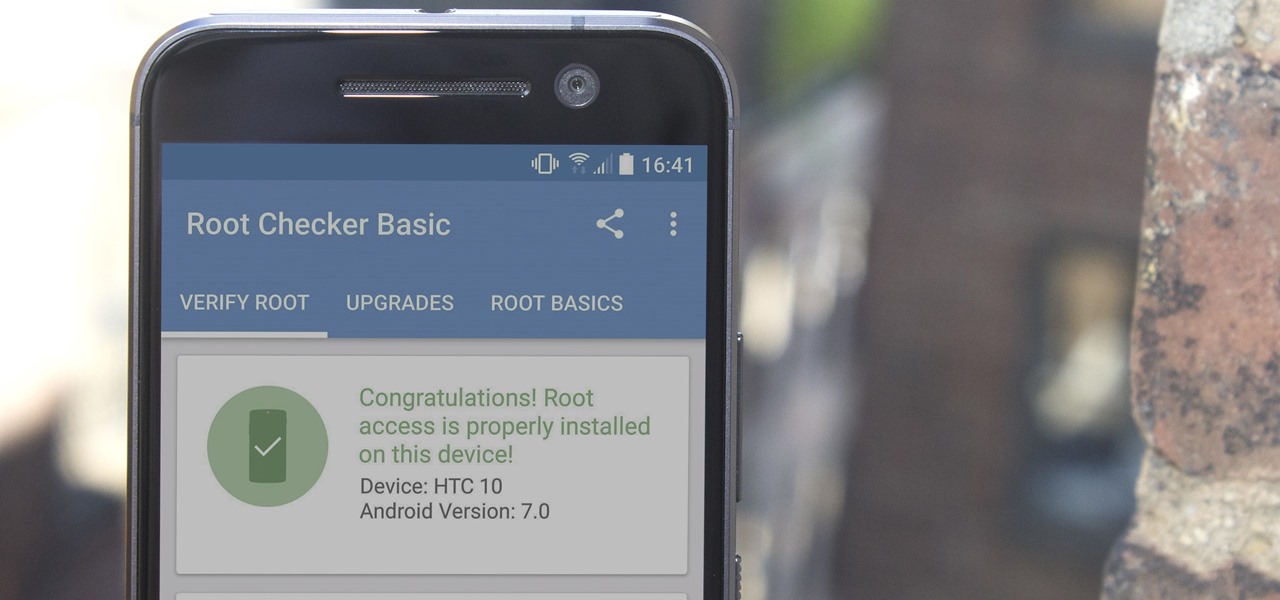
There are many great reasons to root your phone, but if you're not experienced with tools like ADB and Fastboot, it can seem like a daunting task. Fret not, because if you want to root your HTC 10, we're here to walk you through the process.

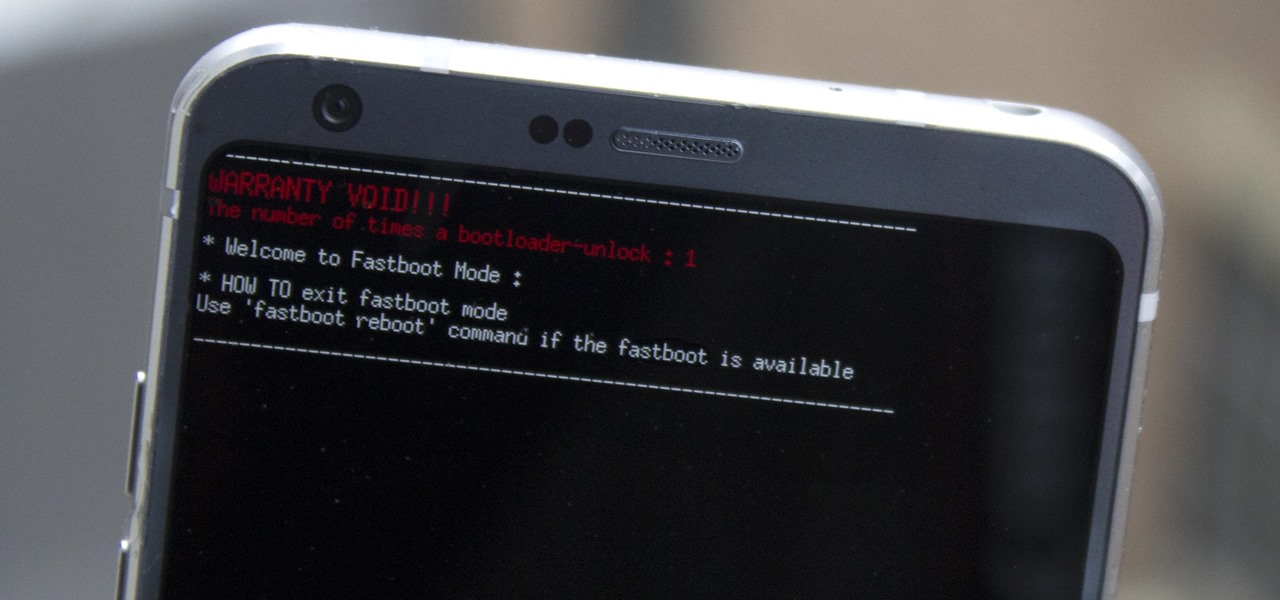
Preorders for the LG G6 have all been fulfilled, and the phone has been up for grabs at local cell phone providers for three weeks now. However, not every LG G6 was created and released equally. The T-Mobile variant of the LG G6 features an unlockable bootloader, while most other North American variants come with a tightly locked down bootloader, which effectively limits the full potential of your brand new fairly expensive phone.

The Pixel and Pixel XL both use AMOLED screens, which are noted for their deeper blacks and sharper contrast ratios when compared to traditional LCD panels. However, AMOLED displays still have one fairly major downside, and that's the fact that they're vulnerable to screen burn-in.

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

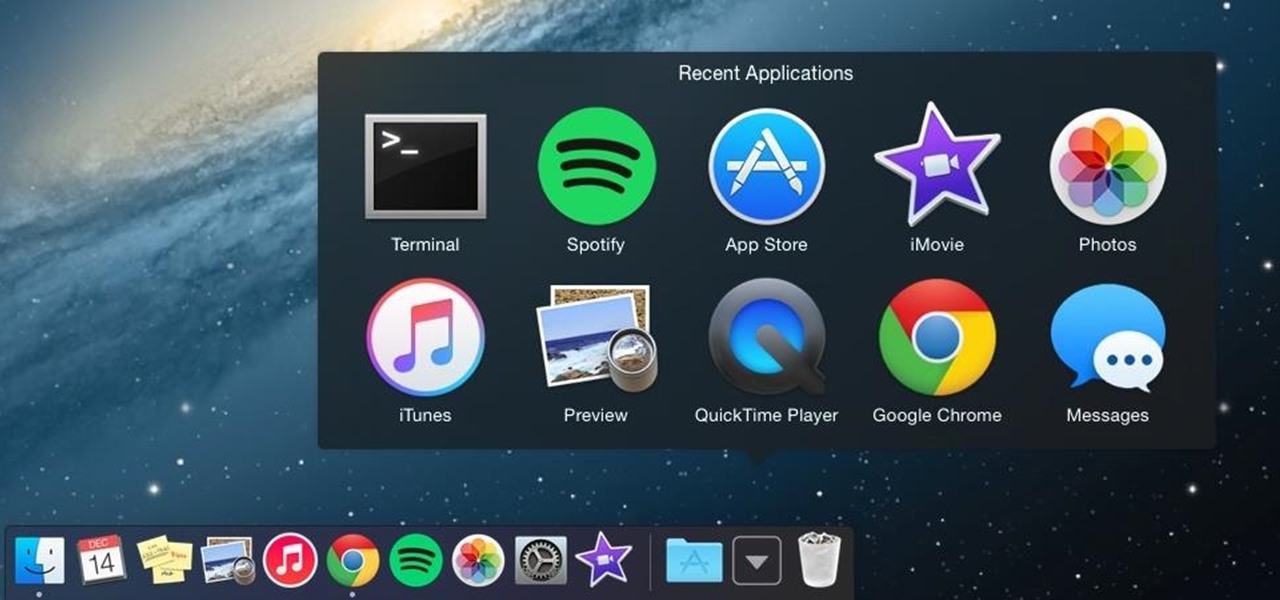
Apple makes it easy to access your favorite and most recently used applications and documents in Mac OS X. You can simply add your favorite apps and folders to the dock, and you can always visit the Apple menu from the menu bar to see a list of your most recently used apps and docs.

And we meet again Crackers! Welcome to my 7th post (Part-2), this tutorial will explain about some more basics of Batch Scripting, with C00L Scripts, which in turn will help you learn and understand better

Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

If you can't get access to a wifi hotspot or an Internet connection with your PSP, you can use this method to get online. You will need access to a computer that is online, and a USB cord that can connect the computer to your PSP. Then, open up the command prompt on your computer, configure your IP and then add your PSP as a device on the network. This method uses the DNS method of getting to the Internet rather than having to hack a wifi connection.