In this how-to video, you will learn how to access Gmail automatically every time you click a mail to link in Google Chrome. In order to do this, you must have a computer that has the Google Chrome browser, as well as a Gmail account. First, prepare Chrome to use extensions. Right click the shortcut and add the following command in the target path area. After this is done, add the new extension. A crx file from the blog must be downloaded. Install the extension and now you will be able to ope...
This video shows you how to install software in Ubuntu Linux. The presenters in the video are Chris Del Checcolo and Ricky Hussmann.
You want to use the websites you want to use, regardless of any school blocks or other hindrances, so how? This video tells us by using the IP addresses of your favorite sites. To find this IP address, at your home, or an other unblocked location, in your start menu, you must access Programs, then Accessories, then Command Prompt. When the window pops up, then type in "Ping http://www.myspace.com" without the quotations, for instance. Write down, then, the string of numbers that appears, whic...

Learn how you would bypass a school’s web filters so that you can go to content sites that are always blocked in examples of YouTube. Click the ‘Start’ button and then click on ‘Run’ and type in cmd and hit enter on your keyboard. This will bring up a command prompt where you type in ‘ping’ and then when that populates the next prompt you enter in the website to bring up the IP address. By entering the populated number you can get into a website from the search field of a web browser. It incl...

This is a Cheat Engine guide on how to hack this flash game - P.O.D. Kongregate Acheatment shows you how to hack P.O.D. with Cheat Engine (09/23/09). This P.O.D. cheat will give you a level hack.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to defend your hacker space with a USB missile launcher.

In this video Chris Pels shows how to create an MSBuild project that orchestrates the execution of the aspnet_compiler and aspnet_merge utilities for an ASP.NET web site. First, learn the fundamentals of the compilation process for an ASP.NET web site and the role of the two command line utilities. Next, see how to create an MSBuild project file and the primary elements such as PropertyGroup and Target. Then learn the details of how to execute the aspnet_compiler and aspnet_merge utilities fr...

Check out this instructional language video to learn how to speak Cherokee! In this lesson, learn how to conjugate the verb "To Sing" in the imperative (the command form), the future tense, and the present continuous verb tense. This is in the Eastern (Giduwa) Cherokee dialect. This video is great for beginners who want to improve their Cherokee language skills. Practice your Cherokee by learning to conjugate the verb "To Sing." Here is the list of forms:

The Apple Spotlight application in Mac OS X can do more than just searches for documents. Throughout your day, you may need to perform a calculation or look up a definition for a word. You can now do that directly from Spotlight. To acccess Spotlight, you can either click on the magnifying glass icon at the top right of your screen or hit command spacebar to bring up the search field. To learn more about using advanced features in OS X Spotlight, watch this video tutorial.

This is hardcore, serious hacking at its best. So it goes without saying that you probably shouldn't be attempting this computer hack unless you've successfully shut down your friend's computer at school using Command Prompt and sent out a fake virus to loved ones.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

The Pixel 5 is a great value proposition in this era of $1,500 phones. With its reasonable price tag, fully open-sourced software, and unlockable bootloader, it's also an ideal phone for rooting.

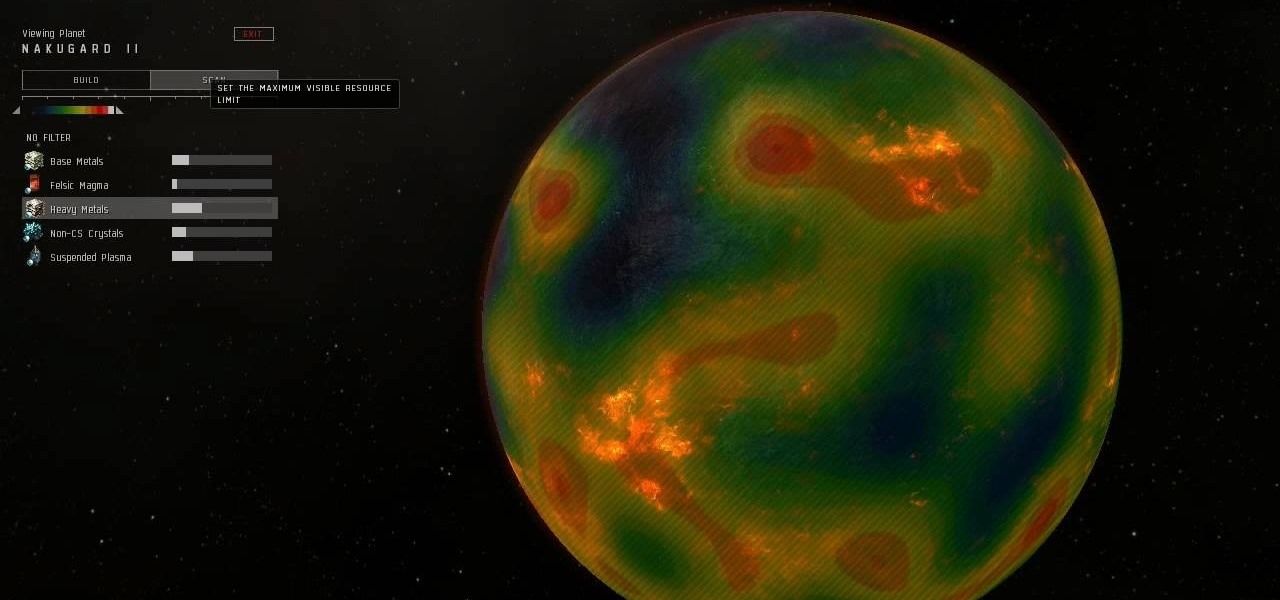
Planetary Interaction is a feature of the EVE Online expansion, Tyrannis. This video guide shows you how to use this new function. Choose your own planet, buy the command center and start exploiting its resources for your own gain!

This video tutorial from izbyfl shows how install Google Chrome and enable its plugins in Ubuntu. First download application from here: http://www.google.com/chrome/intl/en/eula_dev.html?dl=unstable_i386_deb.

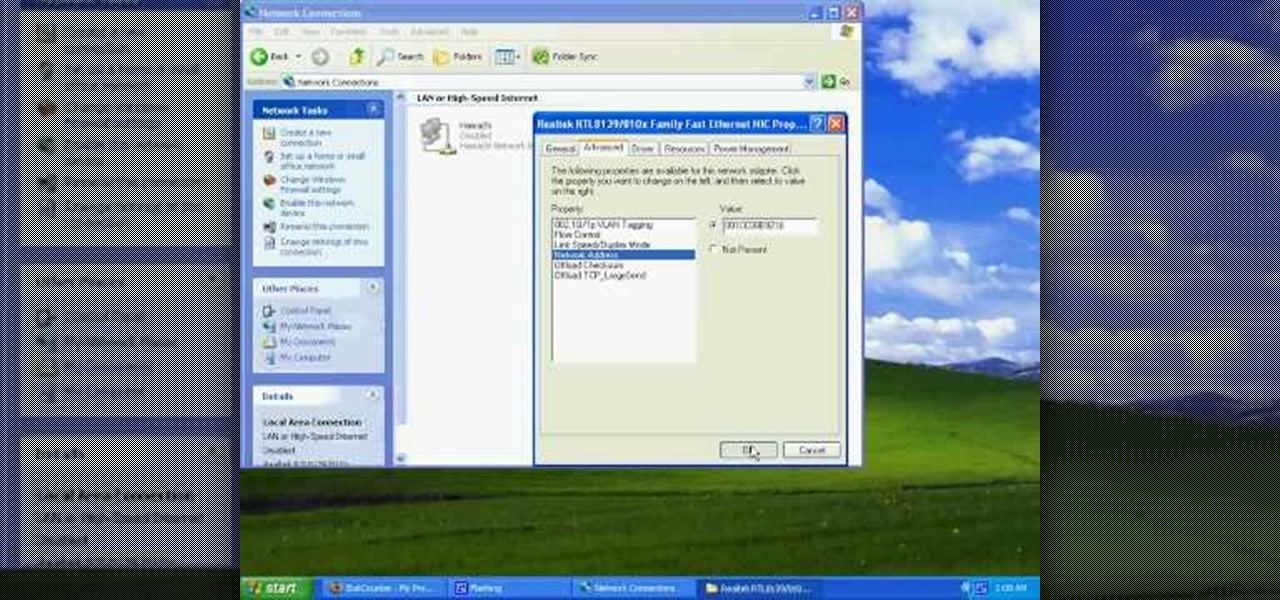
This video tutorial from tarunkumarsinghal shows how to change Mac address on Windows XP. Click Start menu and then Control Panel. Make sure control panel window is in classic view mode. If not, change it to classic from the left pane.

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.

In this how-to video, you will learn how to remove the Windows genuine advantage notification from your operating system. First, open my computer and go to the windows folder. Look for the system32 folder and open it. Search for WGAtray.exe. Select both wgatray.exe and wgalogin and delete. Next, go to the run command and type in regedit. Click okay to open the program. Now, back up the registry. Once this is done, it will be safe to edit the registry. Now, navigate to hkeylocalmachine, softwa...

First of all you have to go to 'logic pro' and select any instrument you want to play. Here you can choose a synthesizer. Now click on the record button at the bottom and it shall start playing and produce a loop. Now from the side bar you can select the ‘low pass filter’ and change the ‘frequency’. From the new pop out, you can change the volume or the note. You can click in ‘command 'L' to open the keyboard ‘assignments settings’ and click where you want to add it. In this case you have to ...

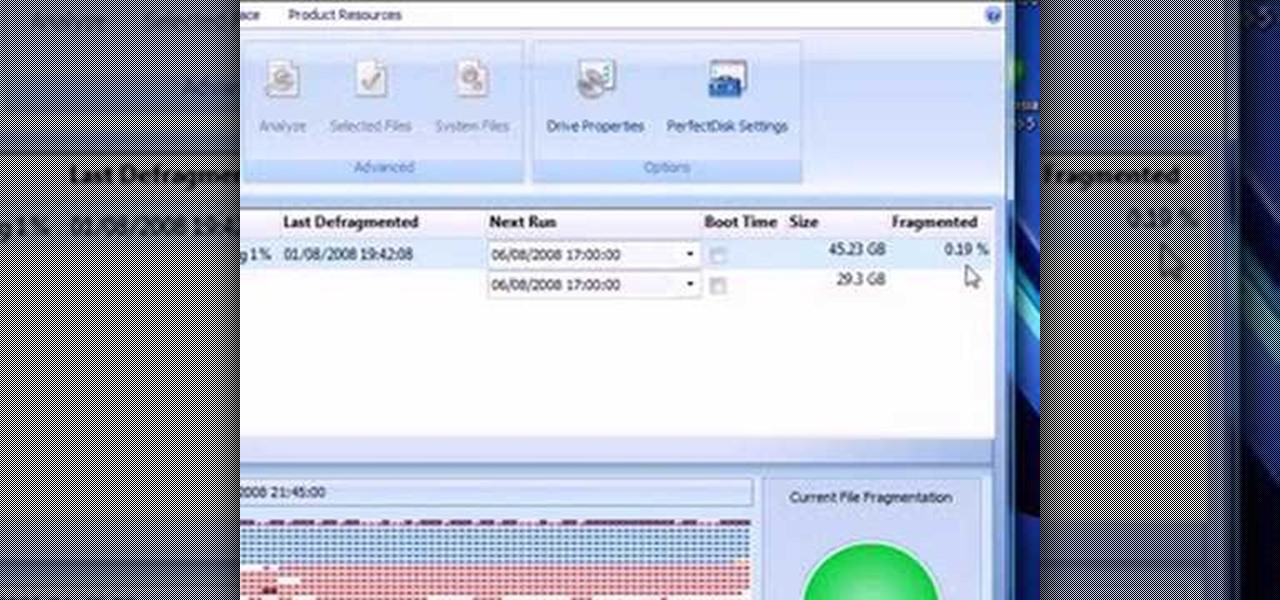
This video presents how to defragment and shrink a Windows Vista partition using Perfect Disk 2008 Professional program.First you need to download and install software application named Perfect Disk 2008.Type Perfect Disk 2008 into Google search engine, choose first link from the list.On the Raxco software home page choose Free Evaluation option from the list to the right.Download and install Perfect Disk 2008 Professional.Once it is installed, run the application. From Menu choose Analyze op...

In this video, Britec09 shows, "How to Fix and Troubleshoot Internet Explorer Browser Problems". First ensure that your computer is connected to the internet and your system is not infected by a computer virus, or any other type of infection, that will cause your computer to function incorrectly. First you should download Firefox to validate if the problem is with the internet explorer or the website itself. Second, you must check the version of your internet explorer. If it is old, update th...

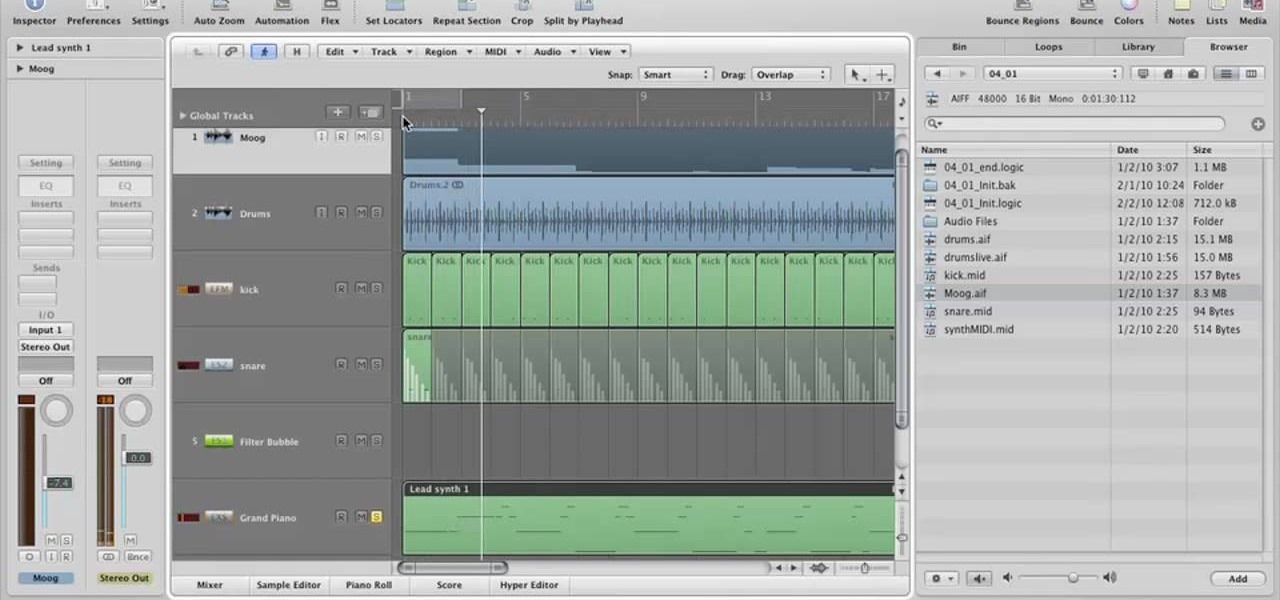
This Lynda tutorial teaches how to use the Logic pro, a songwriting application. Midi sequencing and quantizing is the main focus of this video. Midi is a short name for Musical instrumental digital interface. Midi is not sound. It is a low resolution computer protocol, developed in early 80’s to enable computer to communicate each other. Midi is fast, simple and reliable. It has a intensity stream. In this project, Scot Hirsch explained how a midi file is manipulated in Logic pro. Midi file ...

If you've ever wanted to know how to write checks in Intuit QuickBooks program, this instructional is for you. To write a check in the QuickBooks program: Select banking from the menu bar, and then the write checks command. Select the checking account for which the checks will be drawn from the checking accounts drop down menu. Assign the check a number if you will be printing the check. If you are printing the check, make sure that the "to be printed" box is checked. Enter the correct date f...

First in the training for a German Shepherd is that your dog should start the very first day you bring your German Shepherd puppy or adult home. In general, Dog obedience training benefits are to give proper mental and physical activities. Secondly, there should be existence of friendly relation (bond) between you and your dog. The third is to ensure that your dog's safety and happiness. Lastly correct many types of dog nuisance behaviors like digging, barking and chewing etc. Two levels of D...

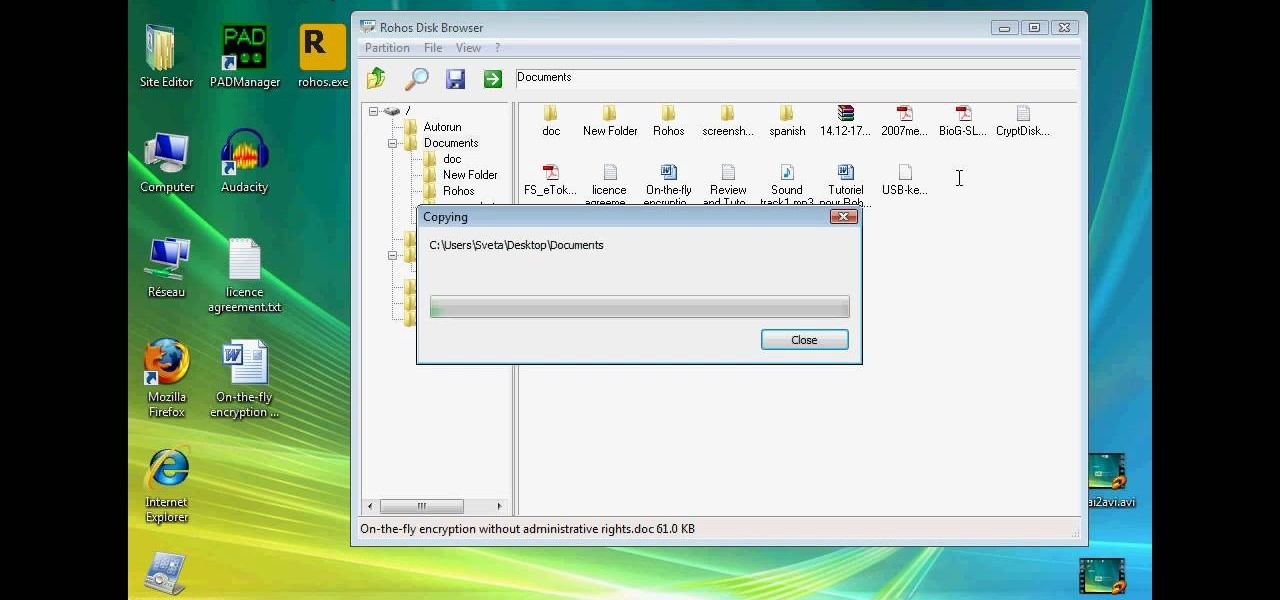
This technical video will show you all about the Rohos Mini Drive. See how you may work with an encrypted partition on a PC without admin rights using this free portable encryption solution. It securely protects your portable data on any USB device. Portable utility Rohos Disk Browser gives you opportunity to work with your sensitive data on a USB drive in the usual way on any PC (even at an internet cafe, where you don’t have admin rights).

So, you've downloaded Boxee... Experience TV in a brand new way! This video will help you get started.

Do you constantly let people walk all over you? Go from doormat to dominator with this advice. You Will Need

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

So, you rooted your Pixel 2 or 2 XL and everything seems to be working quite well. However, a month passes, and you get a notification to install the monthly security update. Like clockwork, Google has been pushing out OTA security patches every single month for a while, but there is a new problem for you at this point — as a rooted user, you are unable to apply the update correctly.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

During the Google I/O 2019 keynote, the latest Android Q Beta was released to the public for Pixel smartphones along with 15 other non-Pixel devices. It's the third Developer Preview for Android 10, but it's the first official public beta outside of Google's Pixel smartphones. A new public beta means good things are on the way as the future of Android continues to evolve.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

It's been little over a month since the official release of LG's latest flagship phone, the LG V20. Despite a few minor hiccups, the V20 has been attracting attention from all over for being an amazing phone. But like with most Android phones, there's no better feeling than rooting and taking complete ownership of it.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

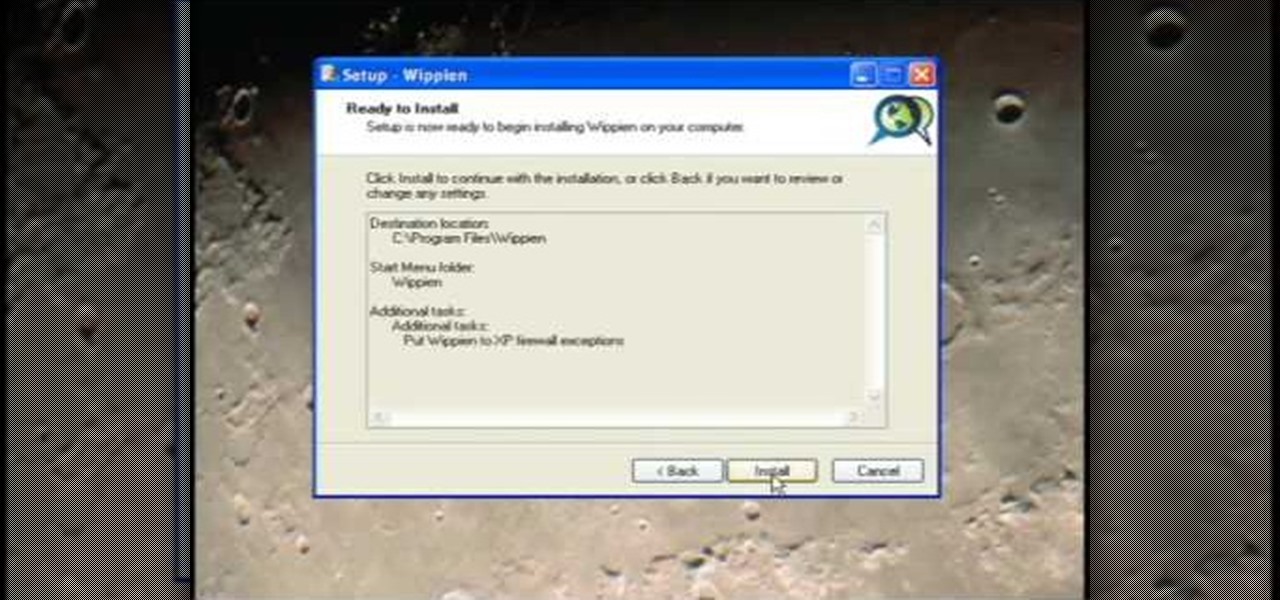
This video tutorial from ruralgeek shows how to set up and use Wippien VPN on Windows XP. First, download Wippien client from here: www.wippien.com.