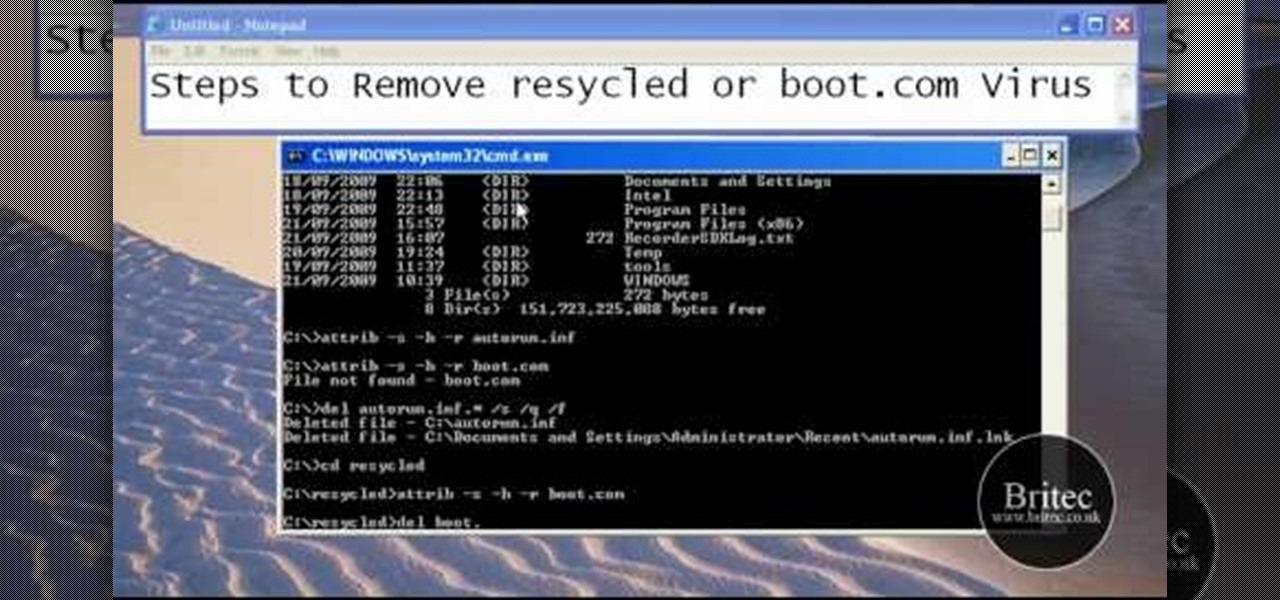
This tutorial describes the procedure to remove autorun.inf and boot.com virus. This virus is commonly called as resycled/boot.com virus, which could damage the system files and may steal important information from the system.This can be removed by any malware / spyware remover like Malewarebytes.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.
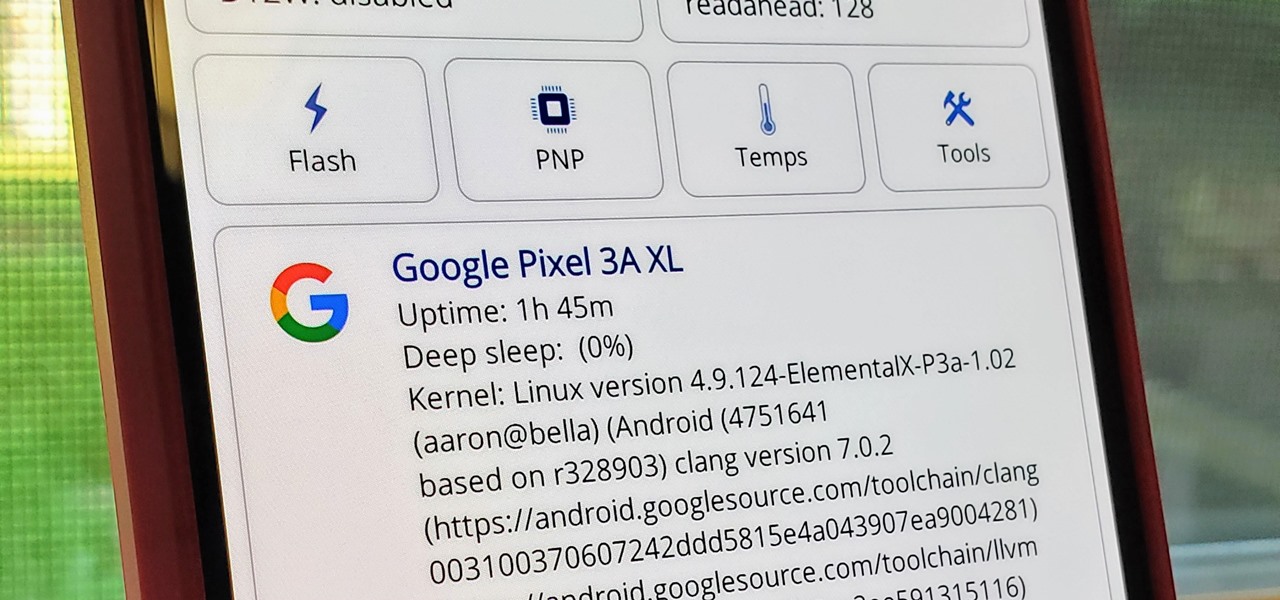
The Pixel 3a runs smoothly out of the box already, but installing a custom kernel can supercharge your experience even more. From fine-tuned CPU tweaks for boosting performance or battery life to adjusting the display colors for your screen how you want, ElementalX kernel can provide you with a ton of new features you didn't know you were missing.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

Whether you love Motion Sense or think it's a gimmick, one thing we can agree on is that its functionality is limited. It's currently limited to switching tracks on a playlist, snoozing alarms, silencing calls, lowering the volume of alerts, and checking notifications. But a new mod will help you do so much more with it.

Lover it or hate it, Android 10 is a big improvement over Android 9 Pie. Based on previous versions, most flagships released in the last two years will get Android 10, but the question is when. So while you wait for those cool new gestures, how about I show you an app that gives you a nearly identical experience?

The OnePlus 7 Pro is truly the best phone that the company has ever created to date — it's even one of the hottest phones around regardless of OEM. It offers an awesome display with minimal bezels, a smooth 90-hertz refresh rate, a pop-up selfie camera, and the best triple camera system in a OnePlus phone so far. It can truly compete with other flagship phones while keeping the cost down.

The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.

Flashing ROMs can be a tricky process, and sometimes you can end up leaving yourself without a ROM at all, often referred to as a soft brick. If you accidentally wiped your internal memory before a flash or forgot to download the ROM before wiping your system partition, don't worry, there is always a way to get your phone back up and running.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

If you live in the US, it's pretty simple: The Google Pixel 4a is the best phone for rooting and modding in 2020. Its price keeps the risk-reward ratio nice and low, and its unlockable bootloader makes it easy to modify virtually any aspect of Android.

This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer's IP address. Click on Download Here link, fill in the registration information, and click submit. 3. Install a VNC listener on your iPod so it can connect to your desktop. Jailbreak your iPod, and open the installer. Click All Programs; scroll down until ...

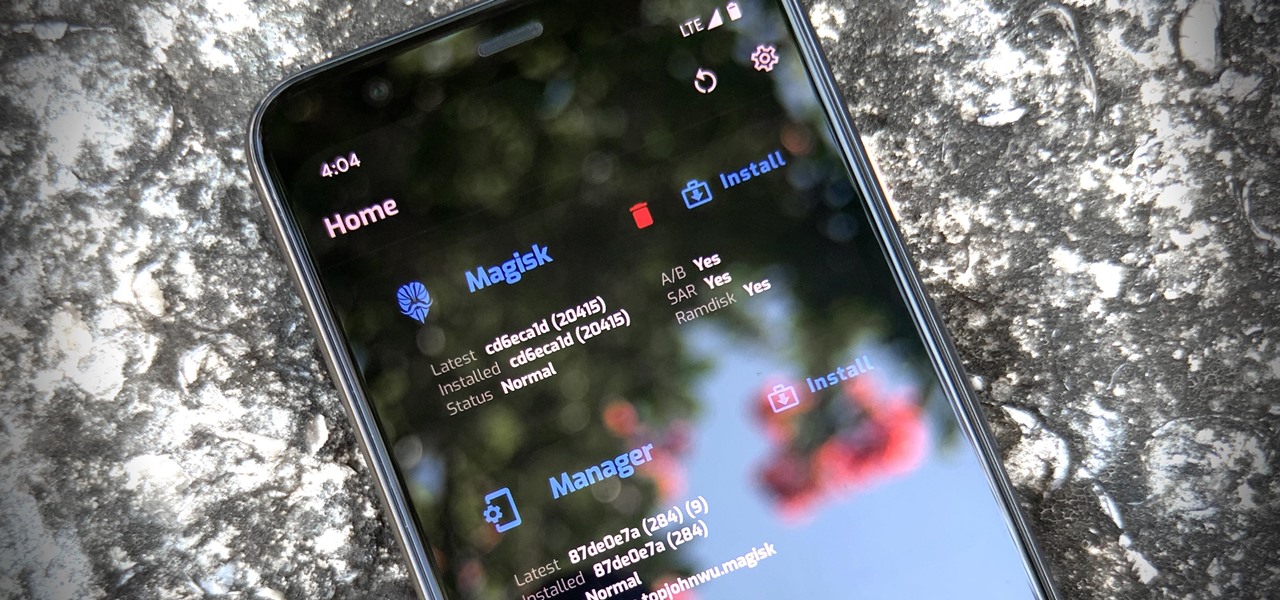
Thanks to Magisk, you don't have to lose root when updating to Android 11. The popular systemless rooting tool already achieved superuser access on Google's latest OS, even before the official release. It's currently in its experimental stages so the process is trickier than usual, but it does work.

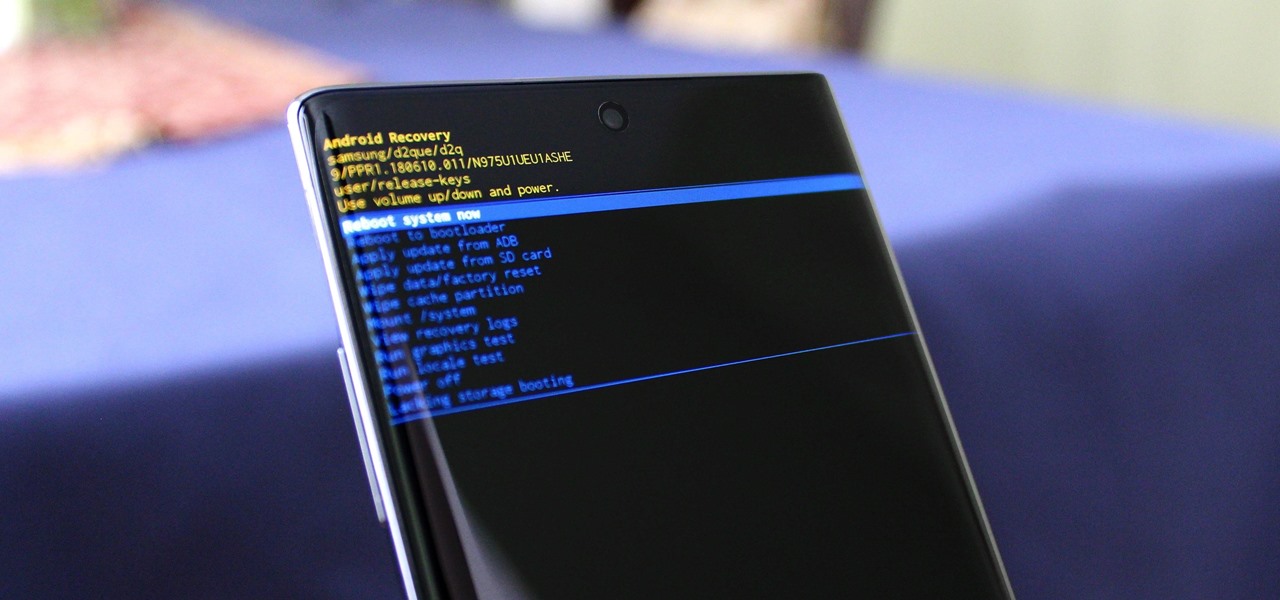
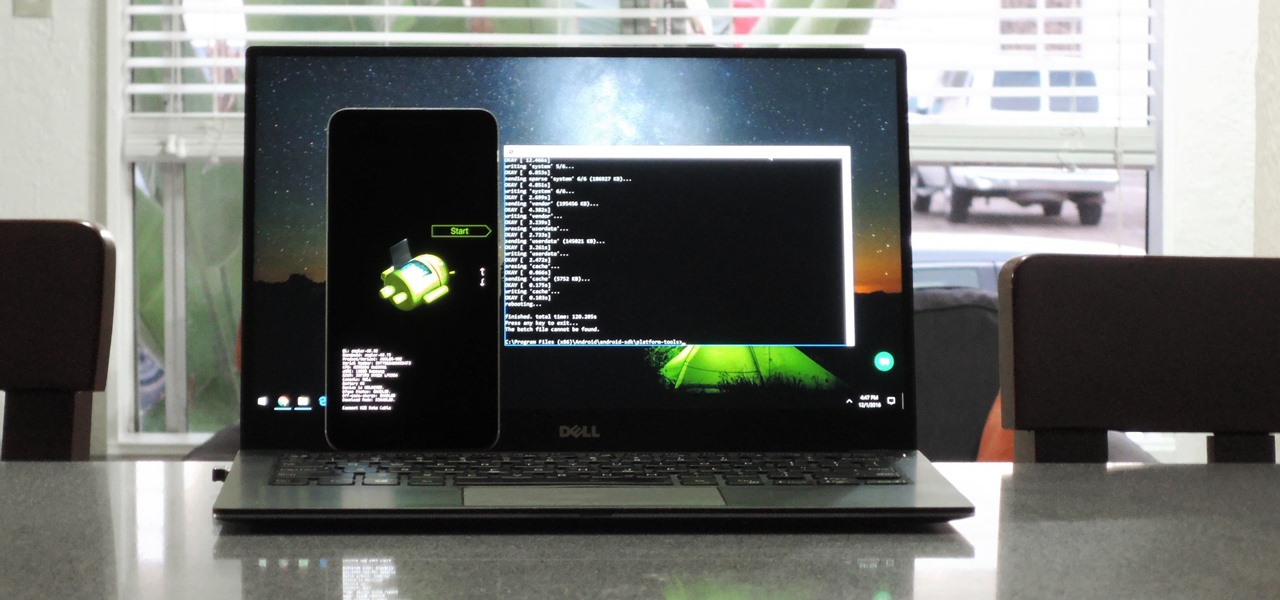
You can't call yourself an Android pro without knowing about Recovery or Download Mode. These menus are critical to do more advanced tasks on your phone, include sideloading software updates and un-bricking a device. But this year, Samsung changed the button combinations that will get you there.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

We've gotten pretty close to a Google Experience before, and even played around with the actual Google Play Edition build. However, the devs over at XDA have a much better solution: actually converting your HTC One into a complete factory-fresh Google Play Edition.

In order to access your wireless router settings in a Windows PC you need to use a command called ipconfig. The purpose of this command is to find out what your IP is. Go into the command console and use ipconfig to find out what it is but instead of noting down the IP address, we actually have to note down the default gateway values for the task at hand. Now all you need to do is open your web browser and insert the default gateway values from before into the address bar. By doing so you wil...

In this video the instructor shows how to hide any kind of file in a .Jpeg image file. To do this take the image in a new folder. Go to start button and then to run. Type cmd in the run and hit enter to open the command prompt. Now browse to the directory that contains the picture and also the file that you want to store using the CD command. Type the command to create our required file as shown in the video. Now a new file will be created that contains your image as well as the file that you...

This walk-through video tutorial shows you how to find out your IP address for XBox live. First press the start button and search for run as shown, click the result, bring up the dialog and type in the given command to open the command prompt window. Type the command in the given window and hit enter. The number that appears is your IP address, use it as the key for XBox Live. In the case of XBox 360, it automatically detects it.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

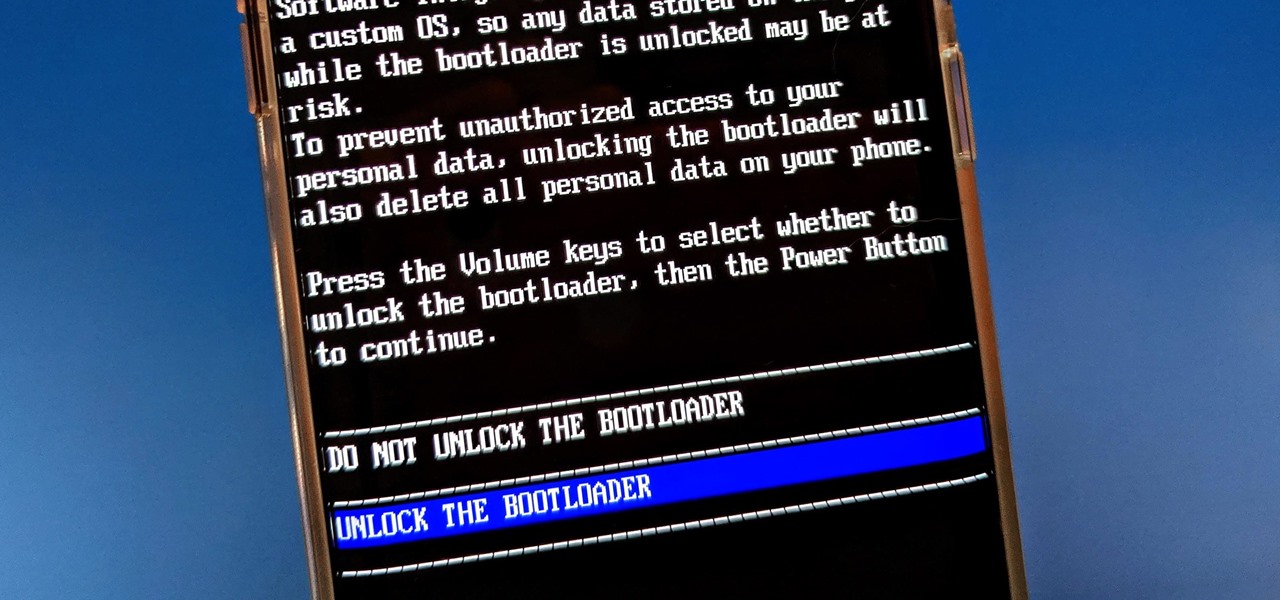
If your phone has an unlocked bootloader, you can use Fastboot commands to flash factory images. That may sound like a bunch of technical jargon, but when it comes down to it, this is the best method for updating a rooted device, fixing a bricked phone, reverting to stock, or even getting new Android updates before everyone else.

When new Android versions come out, the modding community has to find new ways to root the OS. It's a fun cat and mouse game to follow, but it also means the process of rooting isn't exactly the same as it was the last time you did it. Android 10 changes how root works on a system level for some devices, but luckily, the developers are already on top of things.

The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

When it comes to modifying Android, the single, most powerful tool available is TWRP custom recovery. It's even more capable than simple root access when it comes to changing the look and feel of your software, and you can even use TWRP to root your device in a few simple steps.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.