Want to switch between various open applications via keyboard shortcut? With Mac OS X and the app switcher tool, it's a breeze. It's so easy, in fact, that this home-computing how-to can presenta complete overview of the process in just over two minutes. For more information, and to get started using this essential window- and life-changing key command yourself, take a look.
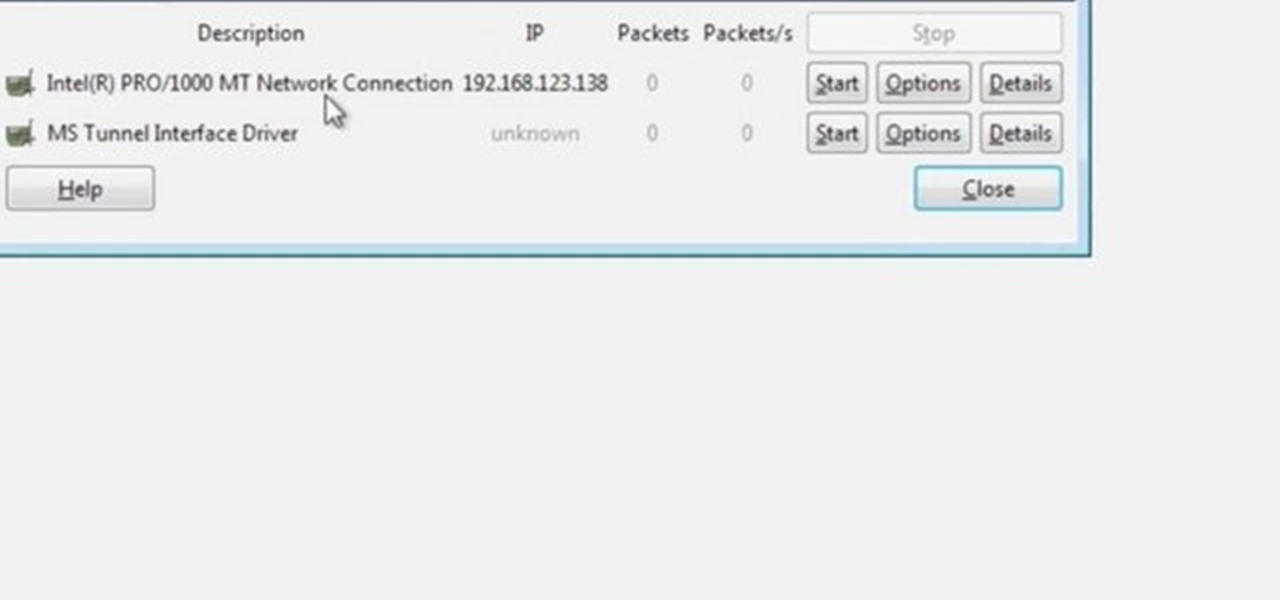
Wireshark is the world's foremost network protocol analyzer, and is the de facto (and often de jure) standard across many industries and educational institutions. This video tutorial demonstrates how to get the Wireshark packet sniffer up and running to do a capture as well as how to run a traceroute command. To get started hacking with Wireshark, watch this how-to.
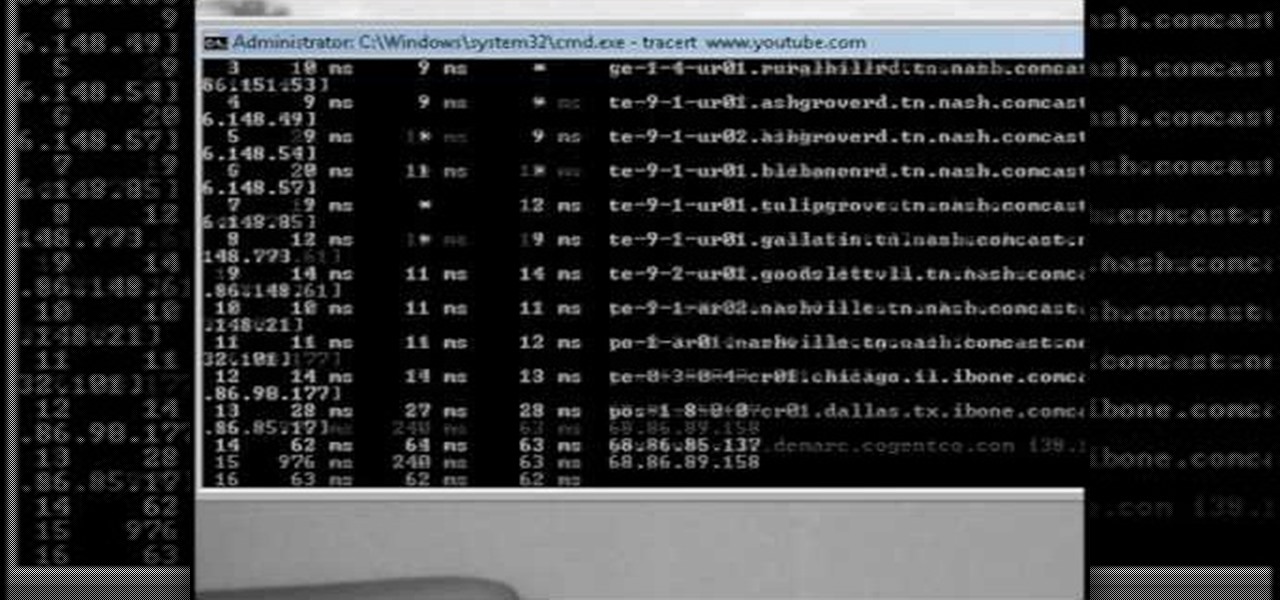
This video will show you how you can trace IP address or websites to a specific location using Windows command functions.

The tether command allows you to tether your camera to your Mac and capture images directly into Aperture. It's fast, easy to set up, and gives studio photographers immediate full-screen feedback while they shoot.

Blogger Jimmy R. demonstrates how you can embed hidden files into an innocent-looking JPEG image using the free 7-Zip and the Windows command line.

In this video, we learn how to find the family tree achievements in Godfather II. All of these involve you manipulating the family tree. For the right hand man, you have to promote one of your soldiers and give them a different ability. The second in command achievements will be done by promoting one of your capos an under boss. Basically, these achievements will be done by you promoting different people and giving them different types of abilities. Once you do this, you will continue to unlo...

We're not exaggerating when we say that every girl remembers her first Audrey Hepburn movie. That's because your life is never the same after witnessing the woman who basically invented the chic modern woman sensibility.

We're addicted to "True Blood." And, if we're going to be honest here, it's not just because the show has labyrinthine plot lines and exciting vampire vs. human vs. werewolf action. With hot chicks and hot guys, the show seems to be a breeding ground of good looks. And we're not complaining.

In this video tutorial, viewers learn how to save and swap icons on a Mac OS X computer. Begin by selecting the application that you want to get the icon from, and copy it. Then open preview, go to the File menu and click on "Create new clipboard". Users are also able to apply the icons on other applications or drives. After you have copied the desired icon, select the application with the icon that you want to replace, press the Command and I buttons, select the icon and paste the copied ico...

Gaussian Blur is a filter that blurs an image. But it's also the math behind the Feather command, drop shadows, and everything that is soft in Photoshop. Watch this video and learn why Gaussian Blur is so important. Whether you're new to Adobe's popular raster graphics editing software or a seasoned professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including d...

As powerful as Photoshop is, there is little about the program that is obvious. Case in point: How do you rotate a layer? Right-click on it and select Rotate? Choose Rotate from the Layer menu? Click on the Rotate tool? The answer is no, no, and no. Fortunately, there's the Free Transform command, which rotates the active layer and much, much more. Whether you're new to Adobe's popular raster graphics editing software or a seasoned professional just looking to better acquaint yourself with th...

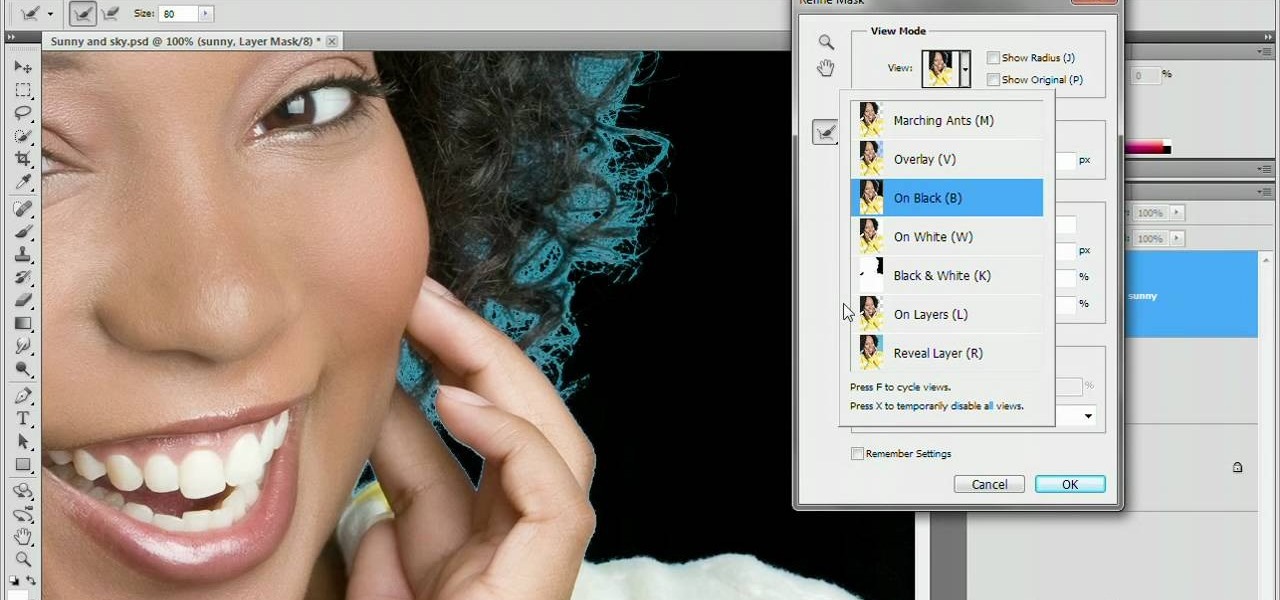
Refining selections and creating masks are unglamorous but utterly essential Photoshop techniques—you've got to master both in order to perform tricky compositing tasks, such as extracting a person from an image and then adding a different background.

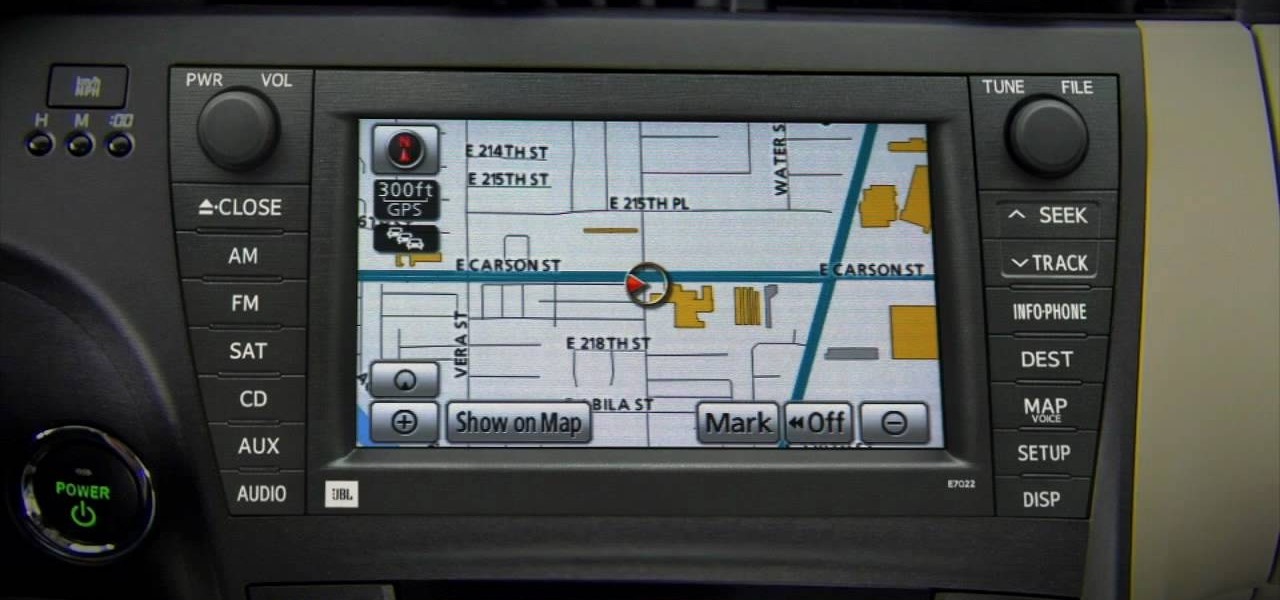
Learn how to use the navigation system in a new 2010 Toyota Prius in simple steps. It has DVD based navigation system with easy to use touch screen display. All the navigation routes of USA, Hawaii and parts of Canada are available in it supporting English, French and Spanish languages. When you start the car it opens the map and you can input the destination using voice command or entering text. You can also input your home address and five other special location address.

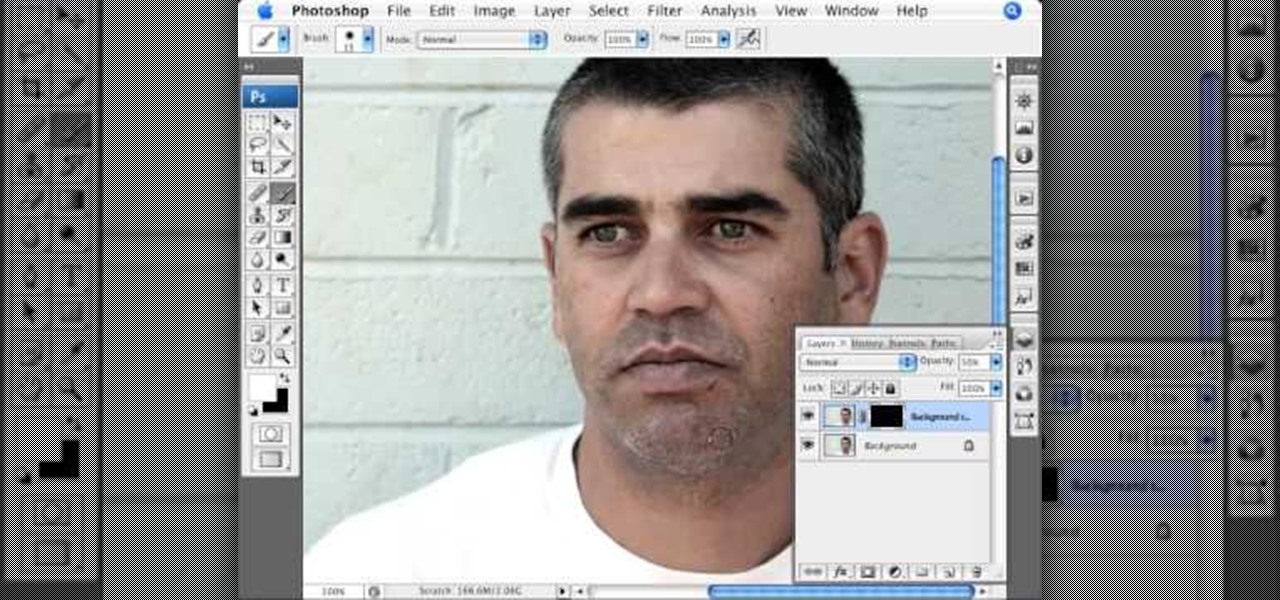
This video, produced by Photoshop Universe, teaches how to reduce beard stubble or 5 o'clock shadows from male pictures. We are shown how to use the dust and scratches filter, layer mask, as well as the advanced layer style command "blend if" on the underlying layer helps us to make this possible. The first step is to duplicate the layer and then select filter, noise, and dust and scratches. The second step is to apply some dust and scratches to the beard selection. Finally we blur the layer ...

This video by photoshopuniverse shows you how to simulate lightning in a night time scenic photo. For this a night time scene is required. Open the image in Photoshop and create a new layer and with the gradient tool create a gradient as shown from the top left to the bottom right. Apply the filter, difference clouds on the layer and inverse the layer as shown. Exaggerate the lightening by using the adjust levels command. Change the layer mode to stream and tweak the hue and saturation so tha...

In this web TV presentation the host is talking about Grub 2. In Grub 2 you can mount an ISO file like a device with the loop back function. In Grub 1 you can use tack tack mem to mount iso files if the files are not fragmented by using the map command. Grub 2 is an application available for download that will be available after download as a chain from Grub 1 to Grub 2 to your operating system. Grub is a program that compresses all of your favorite boot programs into one.

Having trouble with people snatching your stuff? Did someone take your lunch from the company fridge? Here is an inexpensive, sneaky gizmo you can make to keep those sticky fingers away. This is a junk drawer hack from Make Magazine's Kipkay. It's activated when an item is moved from it, triggering a clothes pin to close and activate the voice command. See how to make a talking booby track in this video tutorial with KipKay!

The application the makes Apple's Final Cut Studio is the film editing app Final Cut Pro. With its ability to log and capture video onto your hard drive for editing, you can easily edit and process your indie film, or maybe even a professional movie. Final Cut Pro is a non-linear editing program that even the best editors use.

Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

So we got half a Maya model...now what? We mirror it over and merge the vertices, all with one command, to get us a solid object. We use the dolphin from our organic polygon modeling series, but the technique can be applied to any polygon model. Watch and learn how to mirror geometry the new school way in Maya (with the mirror geometry tool!) NOTE: there are often problems with this method of mirroring, but don't worry, they're covered.

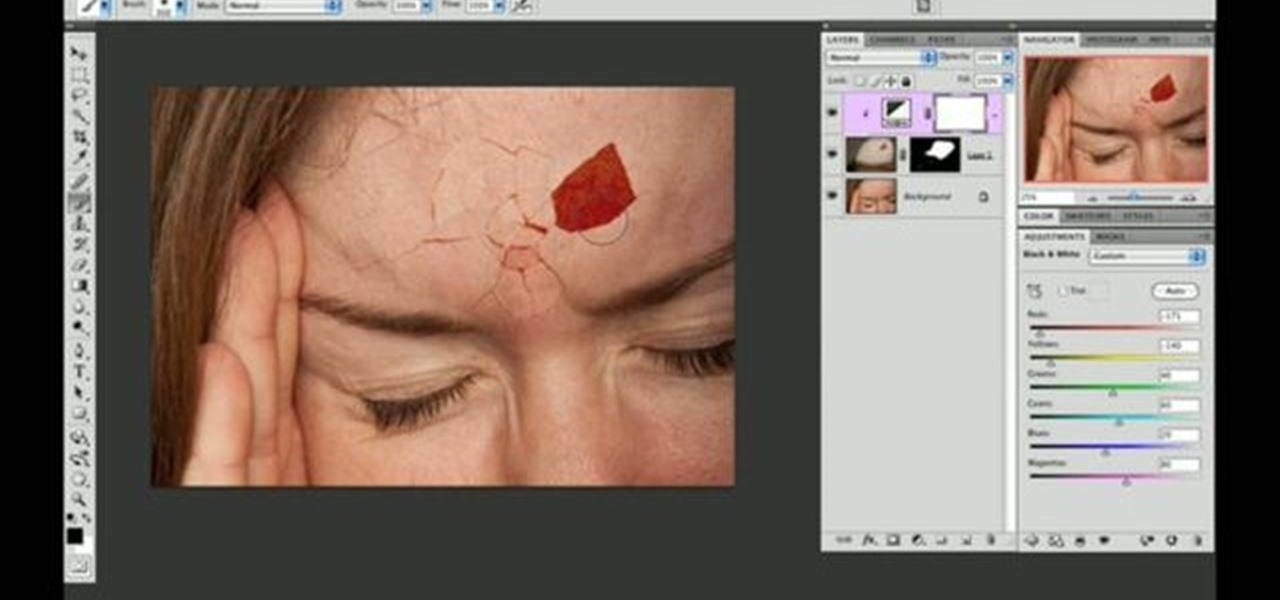
Use two photos, a main image and a photo of a cracked egg which will be your source of the headache. Drag the egg into the main image by holding down the shift key. Resize the egg. Change the opacity down to 50%. Zoom out. Command T flips the image. Hold option and right click. Position the image. Add layer mask icon. Bring back to 100%. Brush. Go to color palate and make sure black paint is on. Paint away all, but the cracked part of the egg. Add the black and white layer, only the egg porti...

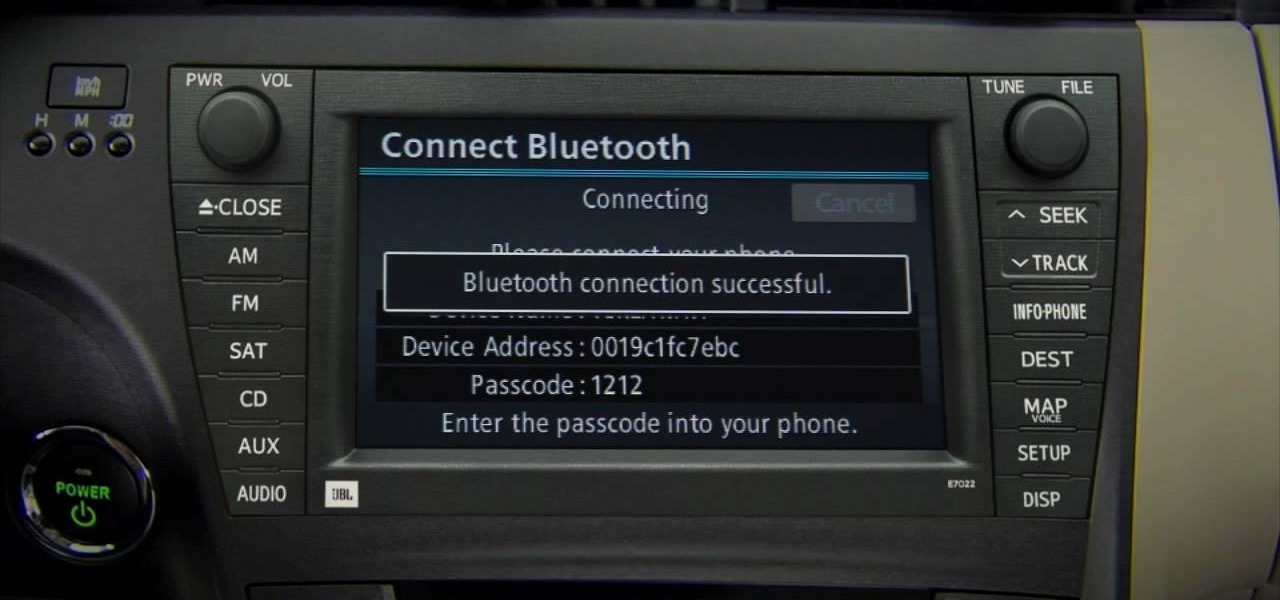
Learn how to pair a phone through Bluetooth with a 2010 Prius in simple steps. 1. You can connect your phone to the vehicle through Bluetooth without using any wires. 2. Press the 'Info Phone' button on the right side of the display screen, press 'Phone' now and press 'Yes' when prompted. 3. Now enter the pass code when prompted on your phone to pair it successfully. 4. You can pair more than a single phone by using the same process but you can use only one at a time. 5. You can also transfer...

Settling a new planet will decrease your pride ratio, because your population will increase when you're settling a new planet. If you're not sure how to even settle planets...

In order to spy and gain intelligence on your Conrohl enemies, you need to make an intelligence agency. Then you recruit your spies to perform simple espionage.

Hack Mafia Wars. Mafia Wars hacks, glitches, cheats. Mafia Wars is a popular facebook app / game. Watch this video tutorial to learn how to mass add Mafia Wars Facebook friends.

Hack Mafia Wars. Mafia Wars hacks, glitches, cheats. Mafia Wars is a popular facebook app / game. Watch this video tutorial to learn how to easily manage your Mafia Wars player updates.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

Root, TWRP, Xposed, Magisk, custom ROMs — before you can have any of these, the first thing you should do is unlock your bootloader. Thankfully, the Pixel 2 and Pixel 2 XL are some of the most modder-friendly phones out there, so you only need to send a single fastboot command to unlock the bootloader.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Hello Guys, Today I have made a script for ddosing sites with VBScript! And I don't know how you guys do it, but I've made a script that refreshes the page in a chosen amout of milliseconds. And if you want it a number of times or if you want it to go on and on. And this is a script to run it on your botnet. But again I don't know if this works on your botnet too.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Hello guys, I recently made a how to about whatsapp but the problem with that script is that it is way to long and you need to copy and paste it so many times so I made a new one that works just fine and is more easy to use lets get into it (Here Is How The Code Supposed To Look)

Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

There are many ways to take a screenshot in macOS (previously Mac OS X), but all of the well-known options give you a drop shadow in the picture when snapping application windows.

With the new navigation gestures in Android 10, you reclaim a lot of screen real estate that used to be occupied by the back, home, and recent apps buttons. But there's still a small bar on the bottom edge of the screen, and in most apps, it still sits atop a black background. Thankfully, an easy hack will give you true full-screen without breaking the new gestures.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...