With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.
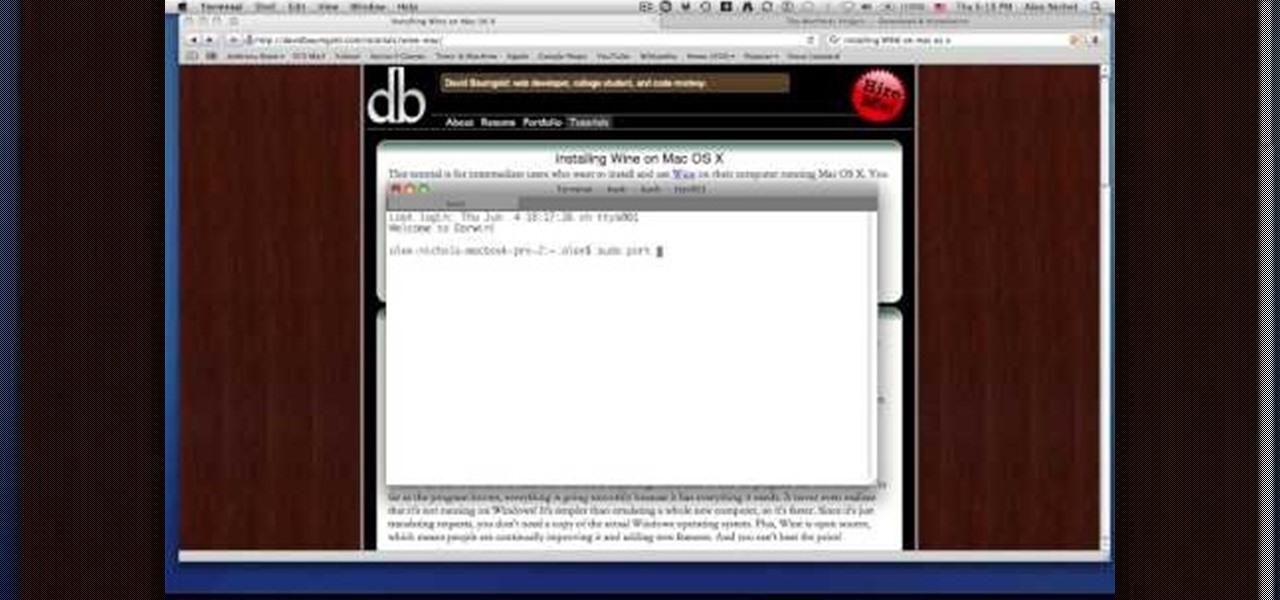
Macheads demonstrates how to install wine on mac. What is wine? Wine allows you to run and install windows program on Intel based machine. This program will work only on Intel and wont work on power PCs,unfortunately. First, we have to install macports which is something similar to installing unix programs on mac. The following are a bunch of requirements in order to install wine - an intel mac, admin account, X code installed, X11 (which comes mostly with intel macs). First of all we have to...
In this video, Gary from MacMost demonstrates how to select items on a Mac computer. He explains that there are different ways of selecting items, both with the mouse and with the keyboard. Click to select a single item, and click an empty space to clear the selection. Hold Command or Shift to add to a selection or remove items from the selected group. Drag around an area to select multiple items, and use Command and drag to add more areas. To select items in a list, click to select a single ...

When used together with the "sit!" command, "stay!" can form the foundation for more complex tricks.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Welcome back, my aspiring hackers! As mentioned several times in previous Linux tutorials, nearly everything in Linux is a file, and very often they are text files. For instance, all of the configuration files in Linux are text files. To reconfigure an application in Linux, we simply need to open the configuration file, change the text file, re-save, and then restart the application and our reconfiguration is applied.

This how-to video is about how to use command prompt to view the blocked websites at school. This step by step instruction will help one to open the blocked websites at school.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

Android 11 won't be available as a beta update for Pixel devices until May 2020. Until then, the only way to try the latest Android version is by manually installing it. Usually, this means carrier models are left out since their bootloaders are locked, but there's still a way to get it done.

Because of the way Android is laid out, you automatically lose a portion of the top and bottom of your screen thanks to the status and navigation bars. The thing is, you don't always need the navigation buttons. By hiding them, you can enjoy more of your Galaxy S10's big, beautiful display.

Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool!

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Android used to have a notification ticker, but those days are long gone. Now, important new messages pop up on the top half of your screen with what's known as a "heads up notification." If you're in the middle of something, these popup notifications can be pretty annoying — luckily, it's pretty easy to turn them off.

Some computers might now have a working DVD drive and in such cases you can use a USB pen drive to install Windows 7 on it. To do this first connect the USB drive to your computer. Now go to the command prompt and run the 'diskpart' command to find the details of the hard drive. Use the 'List Disk' command to list all the drives on you computer. You can also find the USB drive in the list. Now use the Select disk command to select the disk. Perform a clean command of the disk. Next create a p...

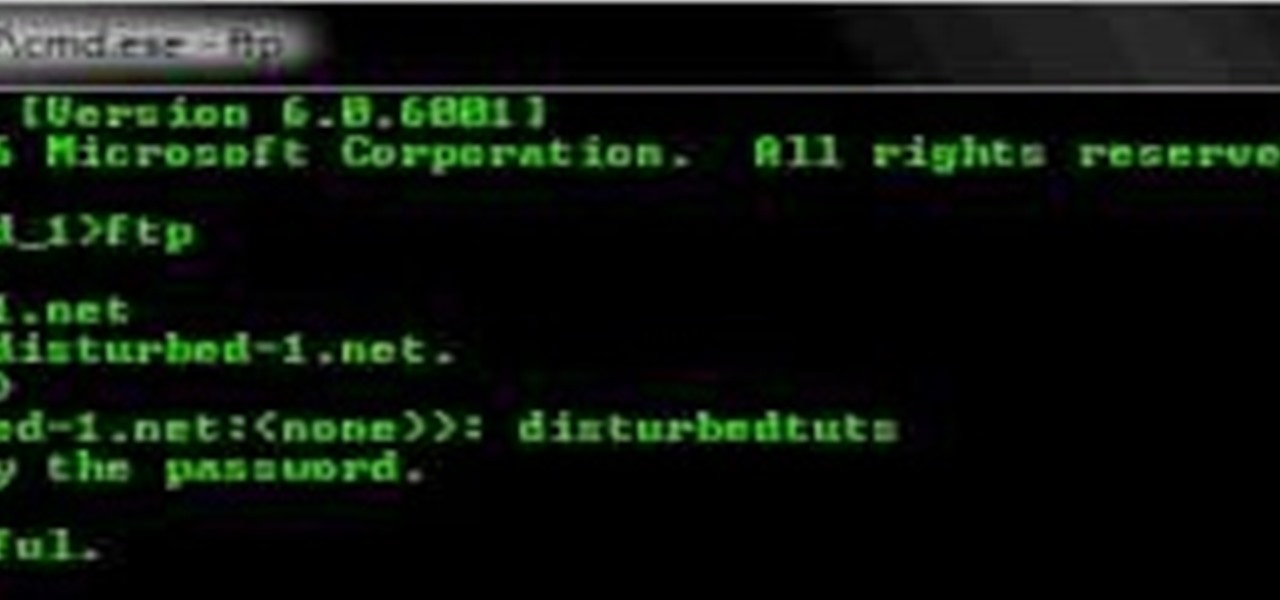
You can connect to an SSH server or connect to an FTP server from you windows computer. Open the run dialogue in your windows and type in cmd. Press OK to open the command prompt. Type in ftp command and press enter. This brings up the ftp prompt. Type o to connect to a server. Next type in the server name you want to connect to. Now you will need the authentication credentials to connect to the server. First enter the user name and then the password. Up on successful log in it shows the same...

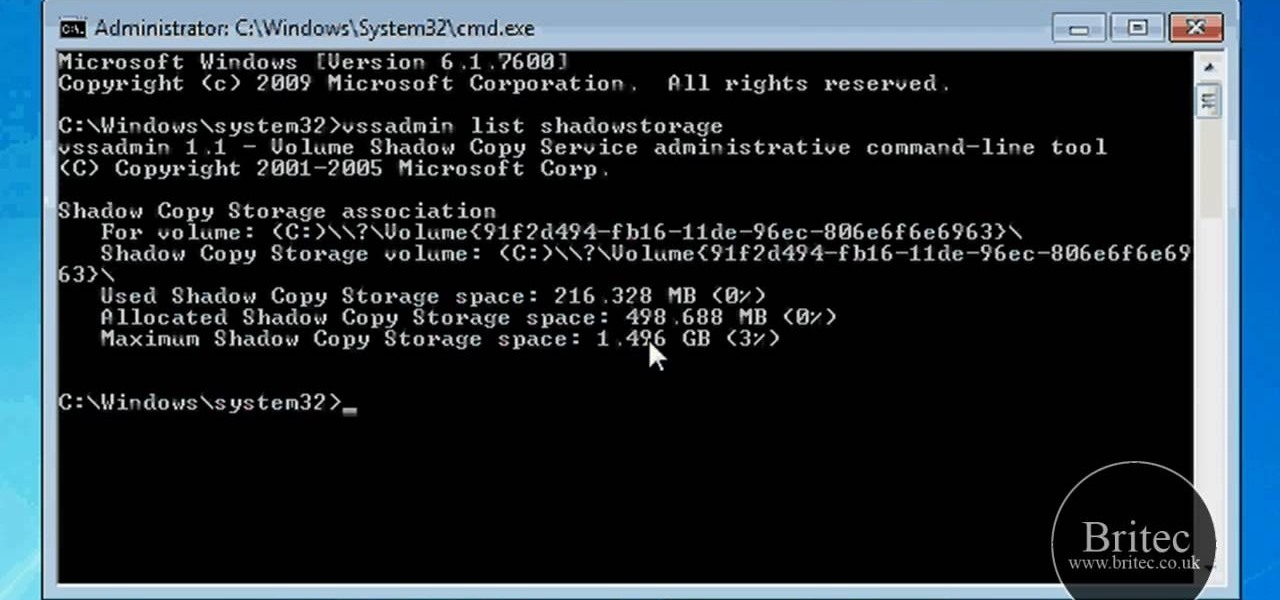
Is your computer getting up in its years and running slower than when you first purchased it? Your problem may lie in the machine's System Volume Information. Watch this video to see how to reclaim or resize disk space from SVI.

Teaching your dog to sit establishes trust and also creates a foundation for other tricks. Learn how to teach your dog to sit with this dog training video.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

While installing the new Android 9.0 Developer Preview is fairly easy if you're using a Windows machine, it's a little trickier if you want to use macOS instead. To help you get the latest Android OS on your Google Pixel phone, we'll break down the whole process so using your Mac can be as simple as Windows.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

In this video tutorial, viewers learn how to quickly copy a folder's content list in Windows. Begin by clicking on the Start menu and open the Run program. Then type in "cmd" to open the Command Prompt window. Now navigate the desired folder and type "dir | clip" beside it. Press Enter and it will automatically copy the directory to the clipboard. Essentially, it is a tool that will the command prompt command to the clipboard. This video will benefit those viewers who use a Windows computer, ...

Learn how to use the Web Capture and Compare Documents commands in Acrobat 9 Pro with this tutorial selected by experts at Adobe. You can use this command to compare the differences between two versions of a web page. First, you have to convert the pages to PDF files using the built-in Convert-to-PDF command in Acrobat 9. Then, select the Compare Document command from the Document menu, choosing the settings. The program will run through the two files, compare them and present the results in ...

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal.

One vital part of Android 10's new navigation system is the "QuickStep" gesture. Swipe up from the bottom of your screen, then pause. You'll see your recent apps along with a dock containing a handful of icons for quick access. This dock is provided by the phone's launcher, which means your home screen is now integrated into the multitasking UI. So what happens if you change your home screen app?

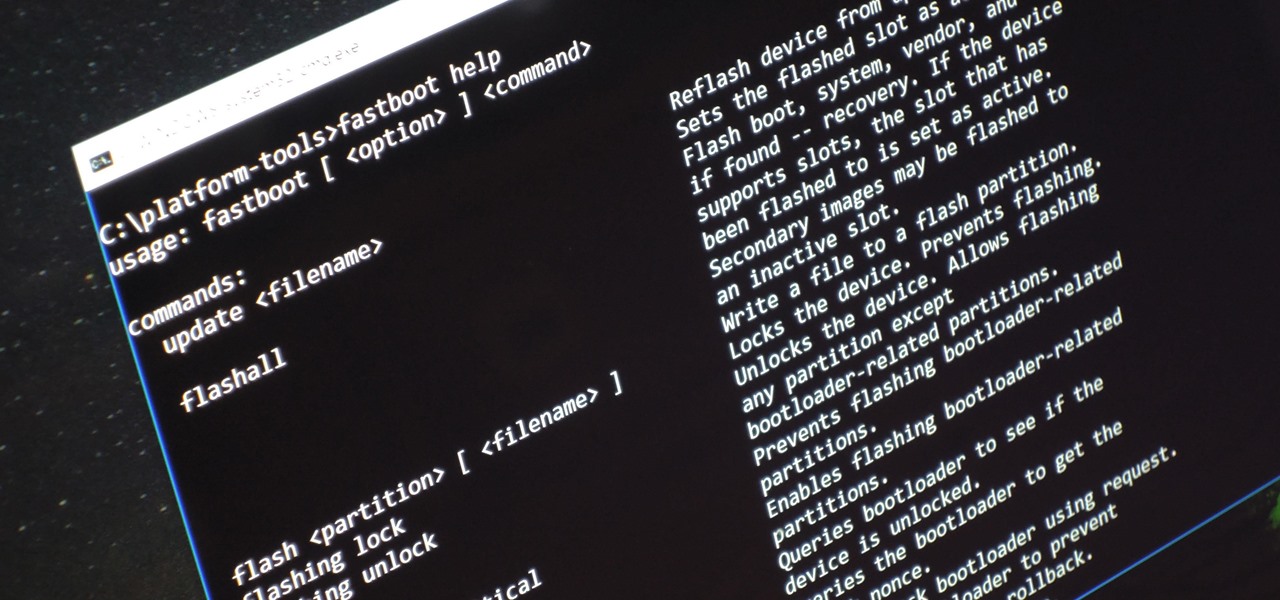
Unless you're experienced using the Linux terminal, running ADB and Fastboot commands can get confusing very fast. The problems often stem from having to hunt for various files — usually IMG or ZIP files that you need to mod your Android phone — and then move them to your platform-tools folder, which, depending on how you installed ADB in the first place, could be anywhere.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

When setting up a new Mac, there can be a bunch of settings that need to be changed in order to get the system running the way you like it. That usually involves going through tons of System Preferences panes and app settings—but it doesn't have to.