
How To: Fun with OSX Terminal
Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.


Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

One of the lesser known features brought along by the roll-out of Android 4.4 KitKat is the ability to screen record from within the device. This features isn't overtly obvious, nor is its implementation the most streamlined, but if you were ever looking for a way to capture video of what's happening on your screen, this is now the best way to do it.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including the Essential PH-1.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.
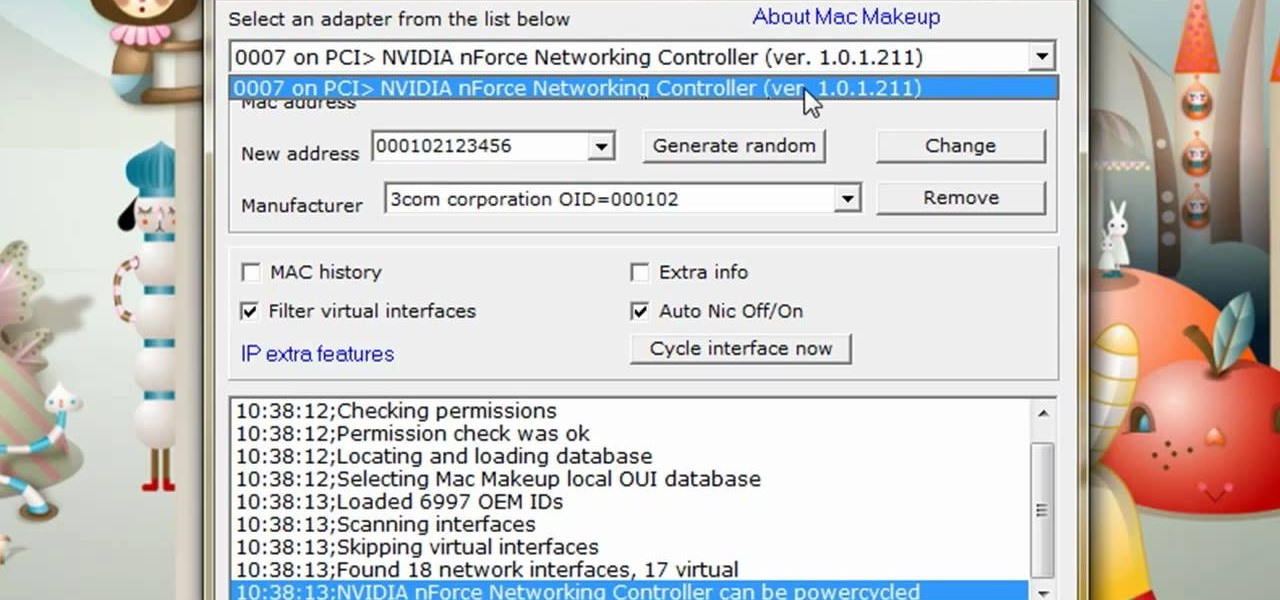
The video is about how to change the IP address. MAC address is the unique identifier a site of the most network adapters. MAC address is used to determine what IP address the computer will have and one way to change the IP address is by changing the MAC address. The method is only applicable for the windows systems and for the MAC systems you need to look at the link provided. In Windows in the start menu, type cmd in the run/search box, which will launch the command window. Type ipconfig/al...
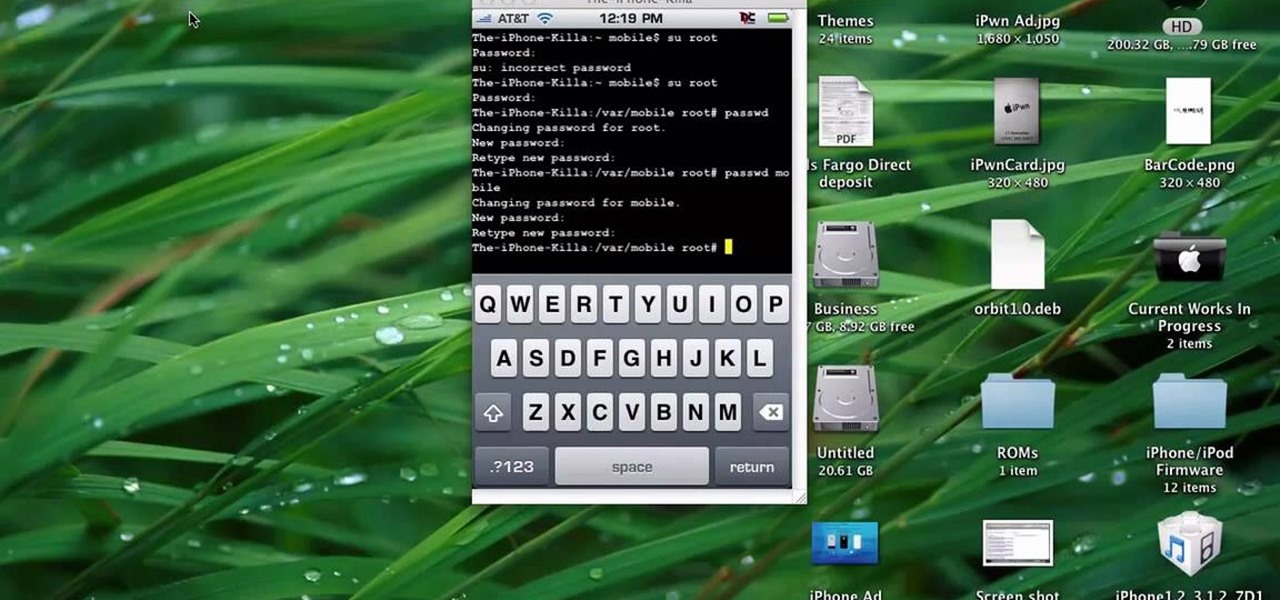
This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them.

Rolling over is a simple trick that any dog can master, and it will help you build confidence in your dog. Learn how to teach your dog to roll over with this how to video.
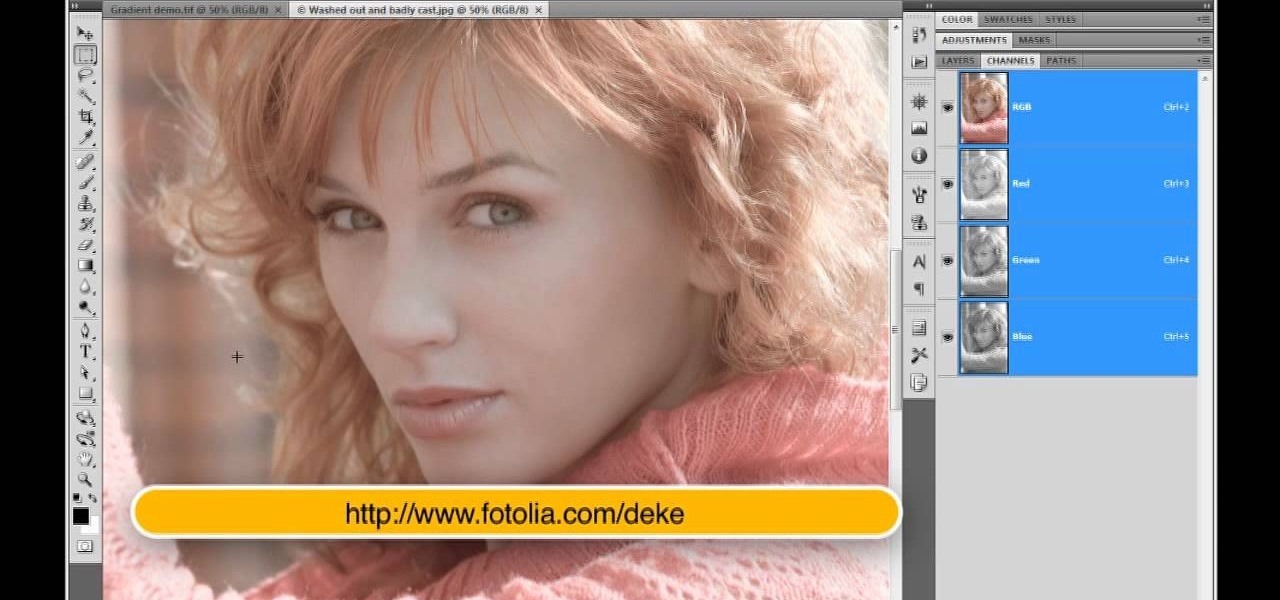
Deke McClelland explains what the Levels and Histogram commands can do in Photoshop in this video tutorial. Levels allows you to adjust the luminance levels allowing you to adjust the contrast and colors within each color channel of an image. Thus, Levels allows you to adjust the individual colors that can be found within a gradient. This command is very similar to the curves command but to a less powerful extent. It is also more efficient than the curves command. The Histogram is another col...
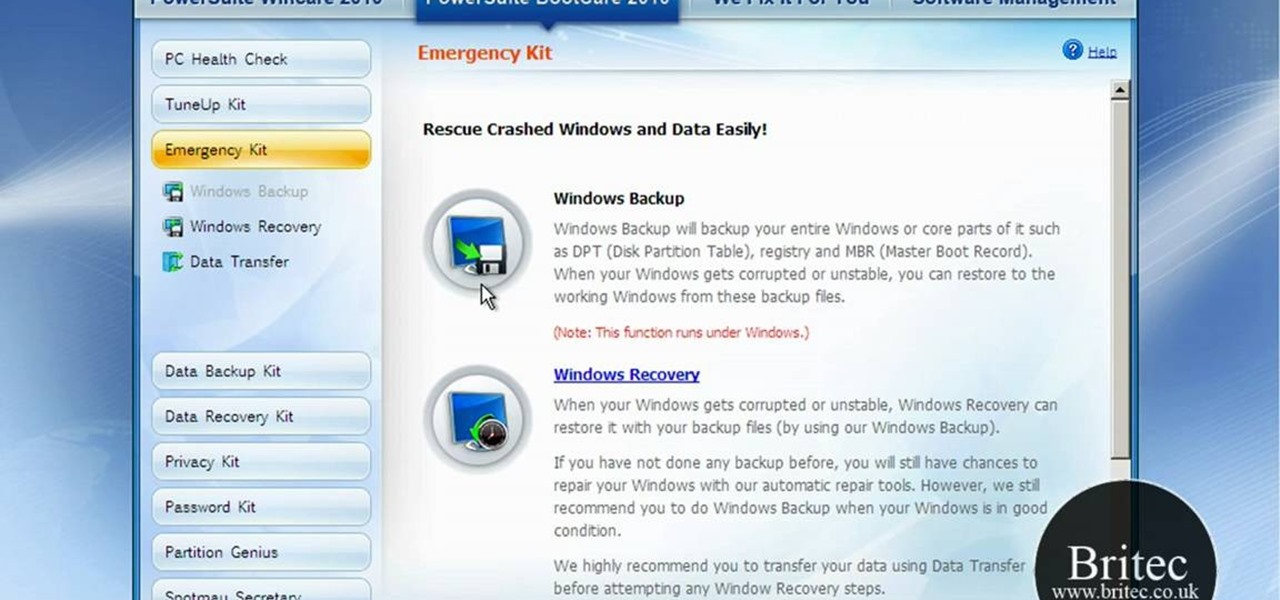
If you've received the "hal.dll is missing or corrupt" error message from your Windows machine, then you're in luck! This video will show you how to correct that problem with the Recovery Console tool that comes with the Windows 2000 and XP CDs.

After learning the foundation tricks of "sit!" "stay!" and "come!" have your dog try their paws at a jump.

Sharpen your listening skills and coordination by playing a round of Mother May I. You Will Need

From housebreaking to traveling, crate training a puppy or dog can have long-term rewards for both owners and pets. Watch this how to video to learn how to teach a dog to shake hands.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

Revision3 Internet Television and Tekzilla Daily with Veronica Belmont demonstrate how to unlock Vista's super user mode. First, open the start menu and type CMD. Right click the command prompt and select the run as administrator option. Type the code net user administrator / active:yes. Hit enter. Your system should reply with the command completed successfully message. Then, the next time you restart your system, you'll see the administrator as an option in the welcome screen. If you use th...
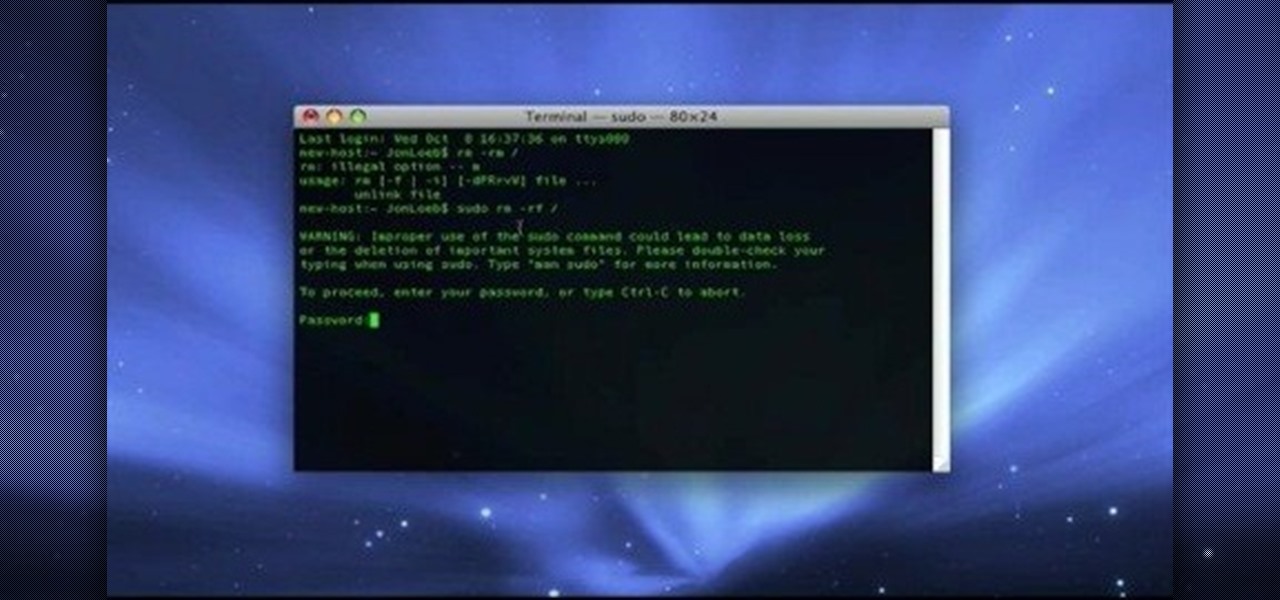
Macheads101 shows us a simple command to erase your entire hard drive in a MAC OS x terminal. You can either log in as administrator and simply type "rm -rf /" to format or you can just type "Sudo rm -rf /" to start. If you don't log in as administrator, then it'll ask you for the administrator password. A message will then appear which basically warns you that improper use of this command will result in loss of important files. Next type in "sudo mount -uw /" to edit the file command system....

In this how-to video, you will learn how to use the zoom function in the Mac OSX. This will help if you are visually impaired. Next to the space bar, there are two keys. There is the command key and the option key. Hold them both of them down at the same and press the number eight key. Once this is done, the desktop will be zoomed in. To zoom in even further, press control, command and plus. Do the same except with the minus key to zoom out. Press option, command and the number 8 to reset the...
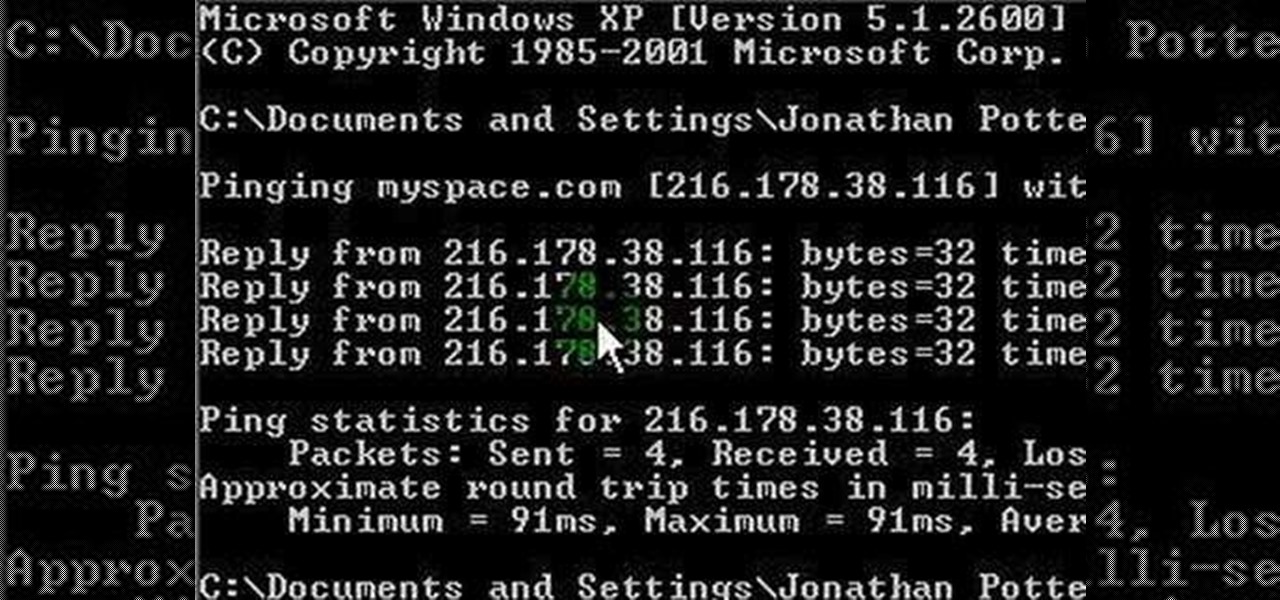
This video describes how to access websites that may be blocked by your school. To begin, on the desktop go to the Start menu and select Run. Type in "cmd" and hit okay to open the command prompt. If that doesn't work go to Start, My Computer, C drive, Documents and Settings, Default User (or the name of the user), Start Menu, Programs, Accessories, and finally click Command Prompt. From the command prompt enter "ping" and then a space followed by the website. The website entered will display...
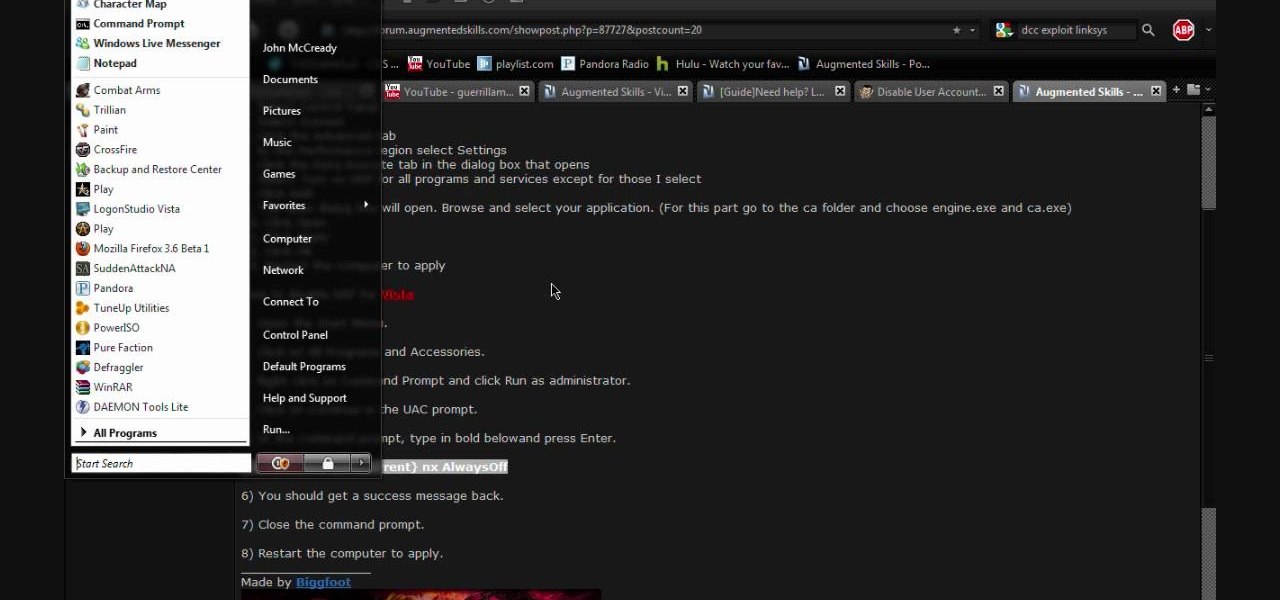
This video contains instructions about how to disable or enable the user accounts on Windows Vista. It is very simple; just go to control panel -> user accounts and safety -> user accounts. You can click the check box on or off to disable or enable the user accounts. This can also be done by using command line. Open run and type the following command:

As a hacker, the final stage of exploitation is covering their tracks, which involves wiping all activity and logs so that they can avoid being detected. It's especially crucial for persistence if the target will be accessed again in the future by the attacker.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.

In the first part of my containers series, we learned how to install Docker on our local machine, pull down "hello-world" and Ubuntu containers, SSH into containers, and install software when in a container. Now, we're going to work on building, customizing, and storing our refined hacking Ubuntu container. Before we dive right in, though, let's make sure we still have a functional Docker installation.

You know what's awesome? You own a Nexus. That means, with Google's blessing, you have easier access and control over your device than other manufacturers allow. You can really dig in and do some interesting things if you root.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

In this video tutorial, viewers learn how to zoom in and out on a Mac computer. To access the zooming tool, begin by clicking on the Apple menu and select System Preferences. Under System, select Universal Access and check On under Zoom. In Options, users are able to set specific settings such as the maximum and minimum range of zoom. The keyboard shortcut for zooming in is: Option, Command and =. The keyboard shortcut for zooming out is: Option, Command and -. This video will benefit those v...

In this how to video, you will learn how to teach your dog to retrieve. First, you should teach your dog the a regular retrieve. You will toss the object so that the dog sees where it lands. Next, give it the command to retrieve. Next, attempt the semi blind retrieve. This involves tossing the object, allowing your dog to see where it has gone. Next, distract the dog for a bit before giving it the command to retrieve. The full blind retrieve should now be attempted. This is done by hiding the...

Open your first image and go to the rectangular marquee tool and select all of the image. Next click command or control C to copy image. Then go to your second image and click command or control V to paste the image. Select both the layers (hold down shift when clicking the layer), then go to edit, auto align layers and choose the top option then click ok. Last add a mask to your top layer, this is done by selecting the gradient tool (make sure its set black to white, the mode is normal and o...