Audiobooks are great because they require little-to-no effort on your behalf. When driving in traffic, why not listen to George R.R. Martin's lengthy A Feast for Crows instead of repetitive, commercial-laden radio? Maybe it harks back to prepubescent bedtime readings, but having things read to me is a very satisfying experience.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.
Two years ago, driven by a good friend of mine i decided to give it a try on timelapse photography. I had a DSLR camera but didn't had an intervalometer, so i assembled a small electronic circuit on top of an Arduino Uno, made some basic code and did my first timelapse movie. The result was awful, but for some reason I was hooked.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

If you've ever seen one of those Samsung commercials from about a year back, you know that the Galaxy S series of phones come with a feature that allows you to do certain things by making gestures in front of your screen. They call this feature Air Gesture, and it enables you to perform certain functions without even touching your phone.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

Unless you're a pretty avid home cook, you probably don't know a lot about sous vide. Sous vide is a low-temperature cooking method where food is cooked in vacuum-sealed plastic bags in a water bath for a prolonged period of time.

It may not be as large as the Samsung Galaxy Note 2, but the Galaxy S3's screen size is still big enough to make iPhone owners cry themselves to sleep. The 4.8-inch AMOLED display with 720 x 1280 pixels makes the GS3 a great mobile companion—and an even better portable gaming device.

Microsoft recently released "Seeing AI," an app aimed to help the blind understand their surroundings. As Microsoft puts it, "the app narrates the world around you by turning the visual world into an audible experience."

Facebook promised that it would release a pair of smartglasses in partnership with Ray-Ban sometime this year and now it looks like we have our first look at the device.

The average business person likely recognizes Epson for its printers or even its projectors, not the futuristic AR wearables.

The COVID-19 pandemic forced many businesses into remote work models, whether they were ready or not, making Zoom a household (or home office) name for its video conferencing service.

To assist developers and researchers in their efforts to create apps and services for automobiles, Volvo Cars has launched a new Innovation Portal with useful new tools and assets.

I must admit, upon learning that the NFL was broadcasting the contest between the New Orleans Saints and Chicago Bears on CBS, Amazon Prime Video, and Nickelodeon, the latter was the only option I wanted, purely for the novelty of the experience.

The latest generation of Spectacles aren't AR smartglasses per se, but Snap is intent on demonstrating that the wearables are capable of storytelling powered by augmented reality.

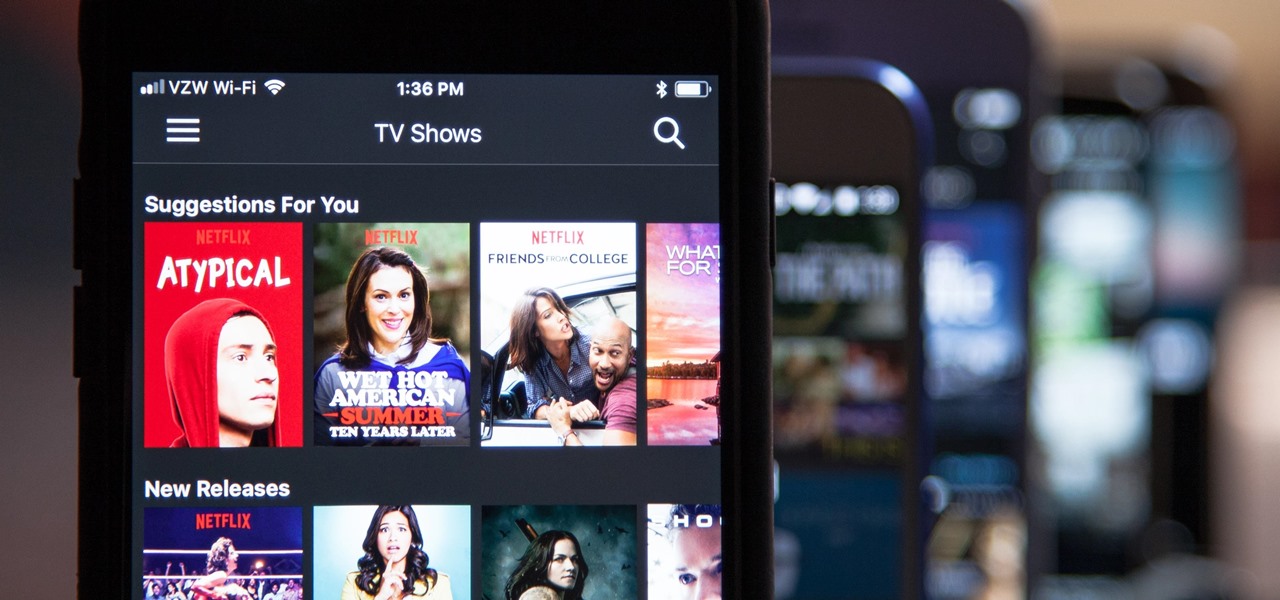
Who here binges TV on a regular basis? I know I do. Never before have we had so many options for watching our favorite shows, especially when you consider how easy it is to stream from anywhere on a mobile device. But sometimes, all that choice gets a little overwhelming. What services are really worth the money? Where should you be investing your Friday-night binges?

The worlds of augmented reality and virtual reality are closely linked in many ways. That means it's smart for AR insiders to keep a close on new developments in VR. If you have been paying attention, you know that Oculus CTO John Carmack is one one of the most important thinkers in the VR space.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

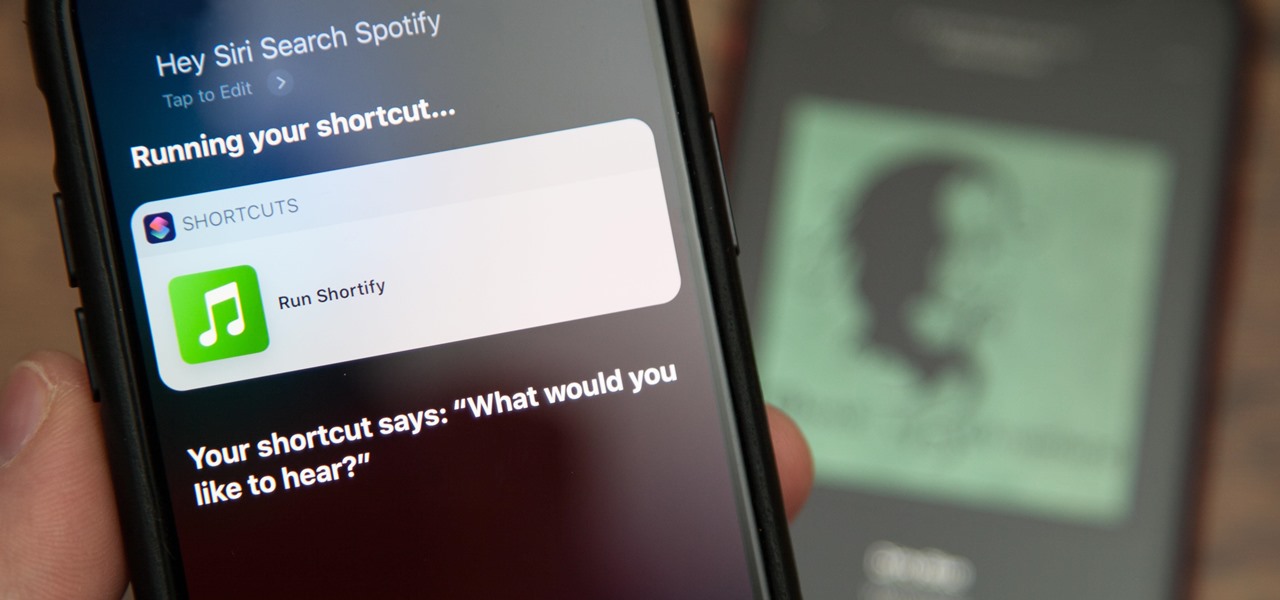
In iOS 13 and later, Spotify supports Siri commands, something we've wanted ever since Siri and Spotify were things. But if you're on iOS 12 still, you're missing out. All you can do is open the Spotify app, then pause and skip tracks with Siri after you start playing a song manually. There is a workaround, however.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

If you want the ability to play YouTube videos in the background as you multitask on your iPhone, you'll have to shell out $11.99 a month for the privilege of doing so with YouTube Premium. Not all of us can afford nor justify such an expense, but if your iPhone is jailbroken, you can get your hands on this sought-after feature — and much more — without spending a dime.

Following the launch of the Magic Leap One earlier this month, the device and the company took a few hits from early reviewers. But it turns out those were just love taps compared to the absolute scorched earth acidic screed penned this weekend by someone well credentialed to dissect Magic Leap One: Oculus Rift creator Palmer Luckey.

The hype train that left the station years ago has reached its first stop, and now we finally have access to the Magic Leap One, the device many have claimed would revolutionize the augmented reality space at launch. But is that really true?

Apple released the iOS 11.2 update for the iPhone to the masses early morning on Dec. 2, and here are all the new features and important bug fixes you need to know about.

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

YouTube is so famous it needs no introduction, but its mischievous clone, YouTube++, sure does. The latter's been tweaked to include hacks not found in the regular version, including background playback, ad blocking, and the ability to download videos directly onto your iPhone, iPad, or iPod touch.

In the past, to see a pre-constructed state of the house that you would one day live in, you had to be able to read blueprints or hire an artist to sketch it out. Later came the ability to have a 3D rendering of that house on a screen, but you'd still have to work hard to envision it in real life.

I've been an Android user almost as long as the operating system has existed, so when I received my first iPhone in April, I felt like I was in a foreign land. Sure, it runs most of the apps I'm used to, and the phone itself feels about the same in my hand as any similarly-sized device, but everything else is just different.

The start of a new year is generally thought of as a chance to start over, a time to improve or "fix" things in your life. Yet most people who set stringent New Year's resolutions find themselves failing within weeks—or even days—of setting their lofty goals.

My bathroom is like my own private arcade room. Whenever I'm seated comfortably on the toilet, no one is going to disturb me, so I can play anything I want on my smartphone. You probably do it, too — and your parents, kids, friends, colleagues, and boss — so don't be afraid to admit it.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

The world of spices can be bewildering. They promise to make your food more flavorful if you know how to make the most of them. Unless you know a couple of essential tricks, however, it just seems like you're adding bits of colored powder to your food.

Even as someone with super pale skin that burns instead of tanning, I don't use sunscreen nearly as often as I should. Or, uh...ever. My skin cancer prevention routine mostly involves hiding from the sun as much as humanly possible. If you're like me and hate the greasy feeling of sunscreen, there are other ways you can protect your skin by increasing your sun tolerance. Your diet actually has a lot to do with how easily you burn, so by getting enough of a few key nutrients, you can decrease ...

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.