MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

Mobile augmented reality developer Blippar has updated its mobile app for iOS and Android with an augmented reality face profiles feature based on the company's real-time facial recognition engine.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

It was definitely a shocker when Microsoft proposed cross-network play between the Xbox One and PlayStation 4 last month. After all, Microsoft and Sony have been competing for the same user base for more than a decade now, and this new feature might actually decrease console sales as a whole.

To me, the term muffin tin is a lot like Voldemort—it should never be uttered. Not for being evil, however... instead, it's because it's inaccurate.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

You'd think the ability to block calls from certain numbers would be built in to most phones by now, but that's certainly not the case with the iPhone.

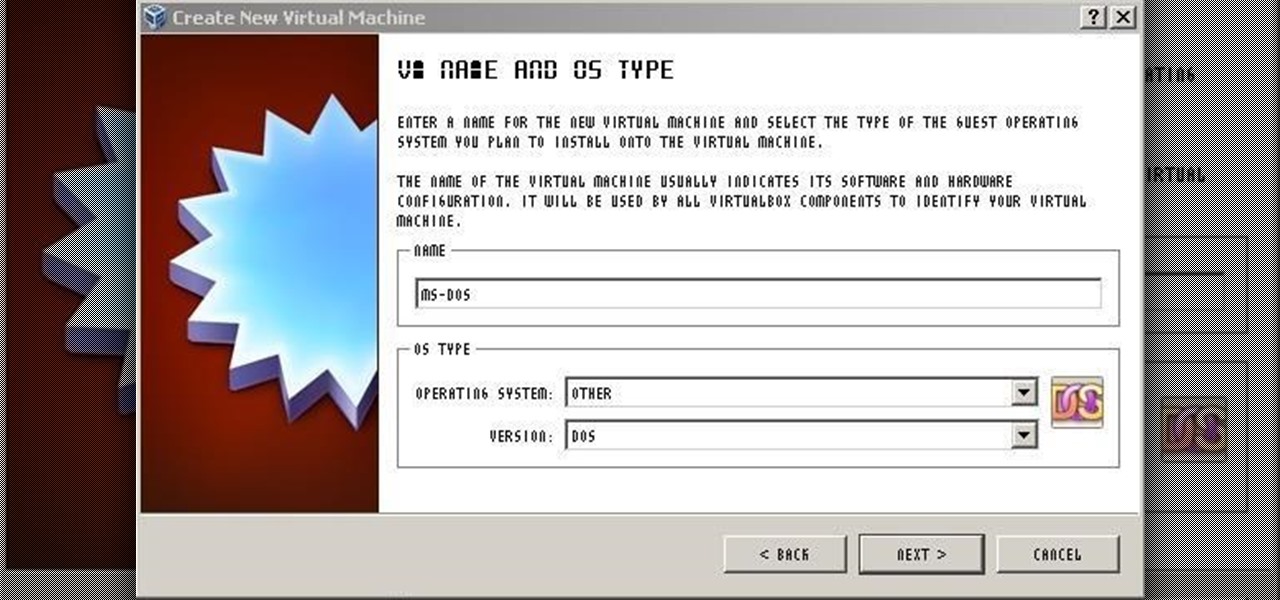
For those needing to replace old controller hardware on cutting mills, those into native retro gaming, or for those who want to see what all the fuss was about in the 1980's, or for those who just want a play with old but great technology, this tutorial shows you step-by-step processing getting the breakthrough desktop operating system running on the latest greatest hardware.

Steampunking Nerf guns by painting them is a pretty common practice among Steampunks, but unfortunately, the really amazing-looking ones involve literally taking the gun apart, painting it, and then screwing it all back together.

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Many of us in the Steampunk community have pets that we love and cherish, myself included, and we want those pets to share our joy of Steampunk. In reality, they couldn't care less, but for some reason we still love to dress them up. Their reactions usually range from bemused acceptance to temper tantrums, but the awwwws we get from onlookers usually makes it worthwhile.

What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense.

If you're looking to get a new iPhone 14 Pro or 14 Pro Max, which model should you choose? What makes the iPhone 14 Pro different than the 14 Pro Max? Find out.

The original iPhone SE was, for some, the perfect iPhone. It brought back the popular one-handed form factor of the iPhone 5 but packed in the internals of the then-new iPhone 6S. Now, the second-generation iPhone SE is here for 2020, but can it live up to what made the first-generation iPhone SE so popular?

Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for traveling, no matter the duration.

Apple's successor to the iPhone X is a beautifully made smartphone with much of the same characteristics, including a 5.8-inch OLED screen, two storage choices, and Face ID. But many features set the iPhone XS apart from its predecessor, as well as the other 2018 lineup of iPhones, making it a worthy choice to upgrade to if you're in the market for a new mobile device.

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

As Apple prepares to potentially introduce its (mostly) secretive AR headset for possible introduction later this year and launch next year, the company has made a strategic investment to ensure its supply chain can support it.

The Apple rumor drumbeat is getting louder: a wearable augmented reality device is almost certainly coming, very soon.

The COVID-19 pandemic has increased the demand for virtual and remote collaboration, and Microsoft has a solution that may serve as the catalyst for more such apps for augmented and virtual reality in the near future.

Despite the unfortunate social media-driven association of Corona beer with the virus behind a global pandemic, beverage maker Constellation Brands has pushed its marketing forward like a lime through the mouth of a beer bottle.

The past year has revealed a gaping hole of opportunity in the world of business called virtual meetings. Some existing players like Zoom hopped on that opportunity, while others like Skype seemed stuck on the sidelines, and Google Meet just managed to catch up in time to snag some of the shift in remote work.

At the opening of its virtual Lens Fest, taking place Dec. 8-10 and open to the public, Snap is furthering its facilitation of AR development with new tools for Lens Studio version 3.3 and a planned investment into its AR creator community.

Google is making its Phone app, the default dialer for Pixel and Android One devices, available to many other smartphones via the Play Store. If you're enticed to replace your factory-installed dialer to take advantage of the spam-filtering capabilities, you don't want to miss out on other features like the ability to customize canned responses for declining calls.