Letter formation can be fun! Few children enjoy traditional handwriting practice. Copying the same black letters over and over again with a pencil is boring! Here is how you can make letter formation fun while practicing with your child at home.

If you've been wondering why you're so unlucky, maybe it's because you haven't been following the New Year's Day tradition like everyone else in the world. So, if you want your luck to change in 2011, you better grab the black-eyed peas and make some Hoppin' John!

Choosing the right axe for you There are many choices and factors when it comes to buying a new electric guitar. Price, style, quality and comfort are major players.
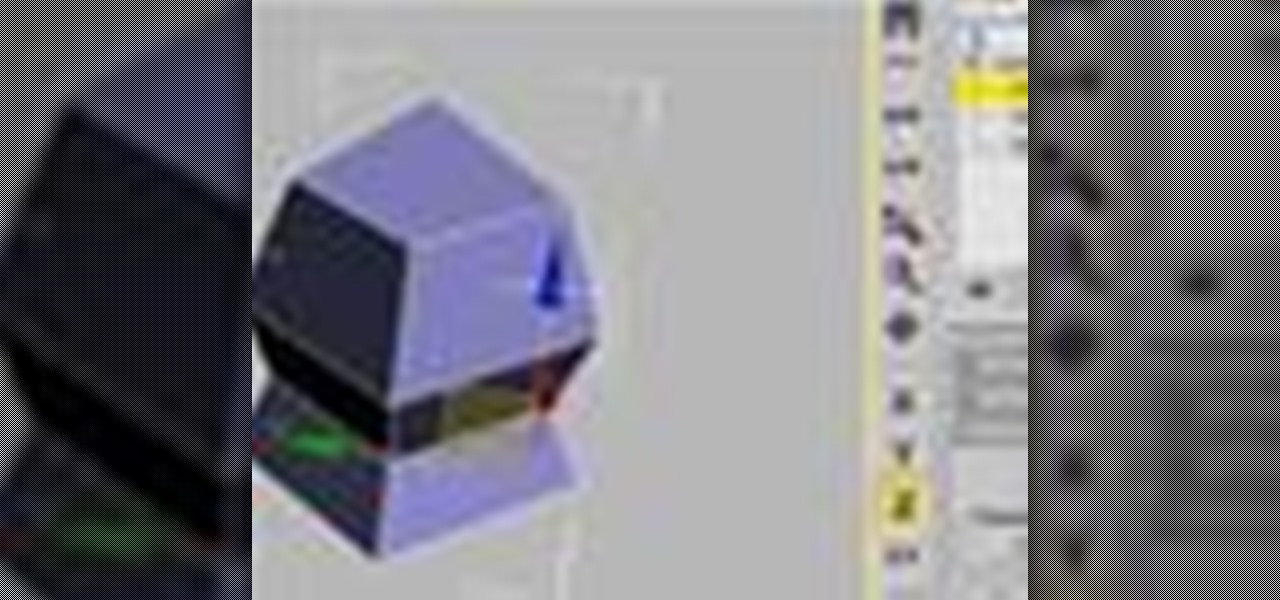
This short 3D software tutorial shows you how to use the bevel modifier in 3ds Max. The Bevel modifier extrudes shapes into 3D objects and applies a flat or round bevel to the edges. A common use for this modifier is to create 3D text and logos, but you can apply it to any shape. Bevel takes a shape as the base of a 3D object. You then extrude the shape up to four levels and assign an outline amount for each level. What Bevel allows you to do is extrude and bevel a spline in 3D Studio Max up ...

Tension in the trapezius muscle, located in the shoulder, is very common. At the end of a long day, do you find your shoulders up around your ears? Learn how to strengthen your lower trapezius to keep loose and limber. Strengthen your lower traps for better posture.

Wall studs are both critical for maintaining the structure of your home and supporting items of weight and function on the interior walls (e.g. cabinets, shelves, plasma TVs, etc.). With wall studs playing such a critical role, consistently being able to find them is important. The problem with finding them is that drywall and wallboard isn't exactly see-through.

This method is easy, intuitive and requires very little math. You will need:

Insecticides are widespread products which are used daily in our lives. Organophosphorus is the main compound in these products and has toxic effects on our health that may be fatal in some cases.

How To Sing Without Lifting Your Larynx

Especially today, with the internet making information so readily available, people of all ages, all around the world, are trying to learn magic tricks. Unfortunately, going about this the wrong way won't make you into a magician at all, but will instead make you into someone who simply knows how a few tricks work.

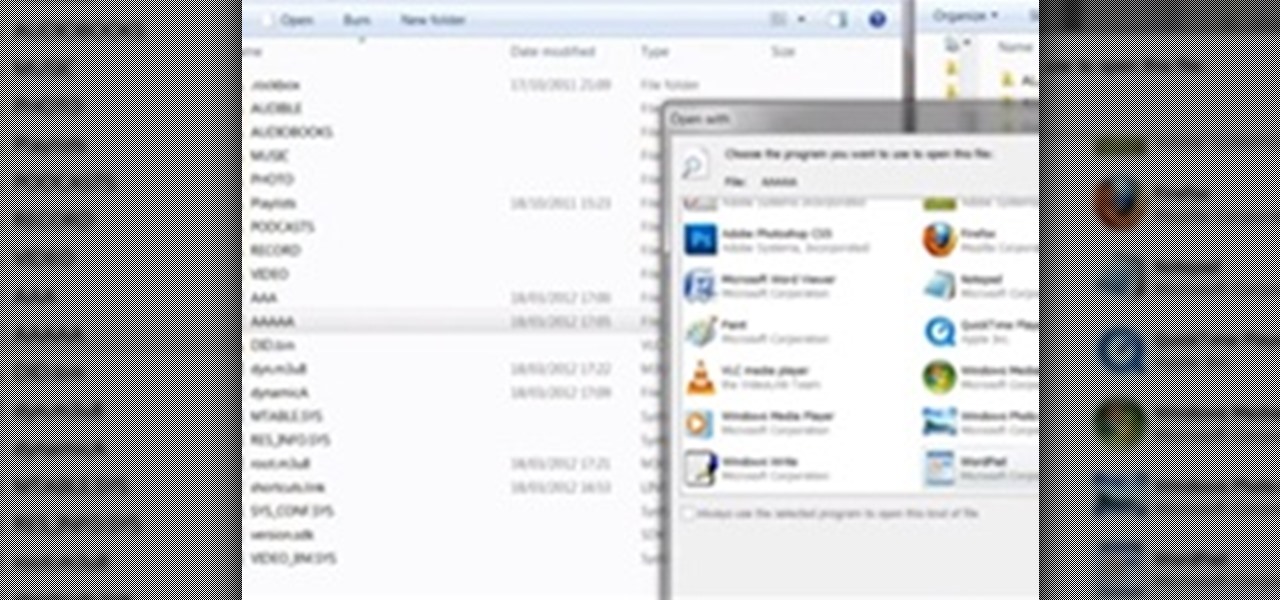
A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc.

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?

You're sitting in front of your grandmother's Windows XP machine that has the worst infection you've ever seen. Safe mode? No dice. Restore points? They're compromised. Even worse, all of the files are hidden and none of the executables will run! This leaves her computer in a bricked state. Without some serious CPR, it will be lost to you. Sure, you could just reinstall the system, but then you might lose all of that valuable data.

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. While mining is a basic aspect of Minecraft, it is often overlooked. Every adventure requires iron and diamonds and other ore and if you're playing in hardcore mode then you need all the help you can get.

Spam is everywhere and Facebook is no exception. In fact, spammers are constantly stepping up their game by tricking unsuspecting Facebook users to participate in quizzes, games, apps, or "new features" that are actually dangerous computer viruses, spyware, or other trojan horses in disguise. Their attempts even trick people into unknowingly becoming spammers themselves.

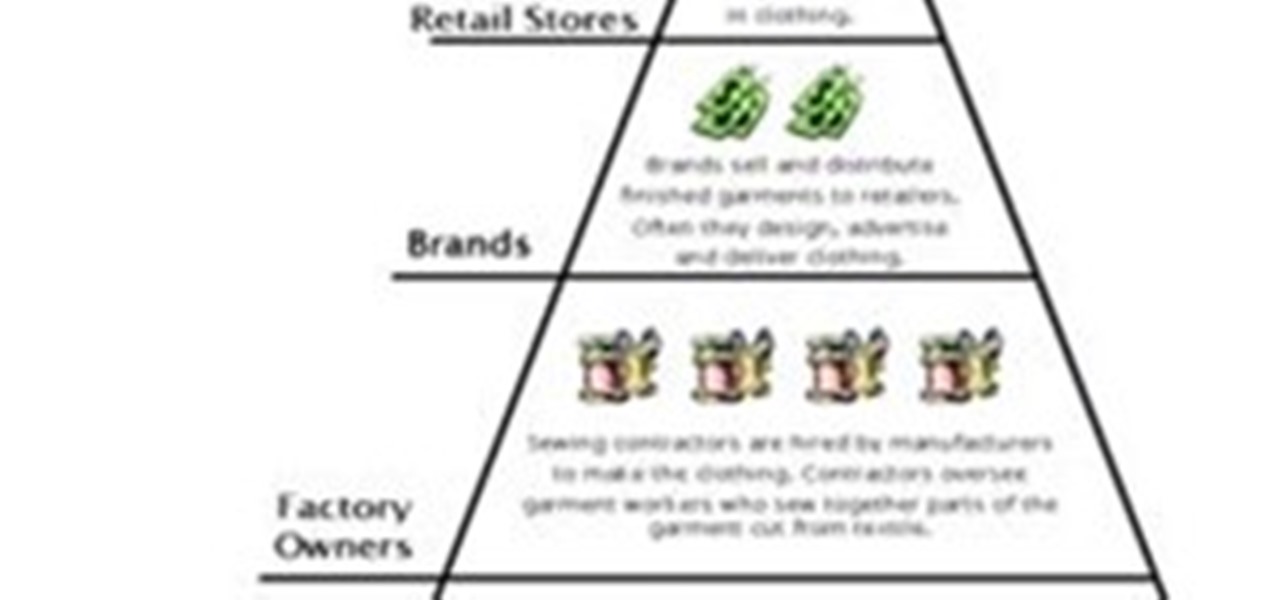
The United States is a hierarchical country where the weak ones are at the bottom and the powerful ones are at the top. Garment workers are at the bottom of the list although they are the most important. Without them there would be no fashion industry. They sew and cut the garments that people buy, the raiment that models wear on the runways. After the garments are sewn, factory owners send the garments to contractors to get make the clothing. Contractors make sure the garment workers sew the...

OSPD1 In 1978, the first SCRABBLE Dictionary was conceived and published by Merriam-Webster, with the help of the National Scrabble Association (NSA). The idea was to include any word that was found in one of the five major dictionaries at the time:

Watch this video from This Old House to learn how to install attic stairs. Steps:

Redstone and electricity have much in common. They both have what's called resistance. That is, they only travel a certain distance before the signal degrades to the point where it's unusable, and they take a certain amount of time to get there. With electricity, that time is nearly instantaneous because electricity is extremely fast. Redstone, on the other hand, is pretty slow.

A playlist is simply a list of songs which can be played in sequential or shuffled/random order. Many people tailor-make playlists to suit a particular style of music or atmosphere, so being able to share these between people is great.

Science-fiction writer Jules Verne predicted many scientific breakthroughs, including the moon landing, tasers, and nuclear submarines. In his 1874 book The Mysterious Island, Verne writes:

Cryptography is a quintessential part of computer security in the modern world. Whenever you buy something on eBay or log into Facebook, that data is encrypted before it's sent to the server in order to prevent third parties from eavesdropping and stealing your sensitive information.

I recently posted a link to what seemed to be a very useful guide on Lifehacker for creating a TOR button in Chrome. However, when I tried it myself, it did not work. Also, it lacked a warning on the limits of Tor, which I think are important. Therefore, I decided to create an updated and more comprehensive tutorial.

We had a blast during last week's social engineering calls. One of our attending social engineers was so clever that she convinced several people on Craigslist that lost items were hers, even if it seemed she couldn't be trusted. But females are better social engineers, naturally. Some say that females have a special knack for manipulating men, but I think that's preposterous. I can't see why that would be true in a million years (note my sarcasm).

I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could use Fake Name Generator, but if you get caught, you will have your account suspended. I don't have a law degree, but to my understanding the United States recently passed legislation that gives the authorities the power ...

Following the first part in this series on advanced cracking techniques, we are going to go over how we can intelligently crack passwords using the old-fashioned bruteforce method. These unique cracking techniques aren't widely used, because most crackers are Script Kiddies who have no idea what the concepts are behind cracking passwords, thus, word won't get around too quickly.

With the purchase of my latest computer, installing Linux turned into a nightmare from Hell. The graphics drivers are probably the biggest issue that anyone with a newer computer will run into when installing Linux. AMD and NVIDIA are the dominant ones on the market, both of which have awful support.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Missed the other guides? Click on the links!

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. No self-respecting Minecraft house is complete without a state of the art automatic cobblestone generator. But what does the average Minecrafter need with a bunch of cobblestone? To put it simply, sometimes you just need a bunch of blocks. I cannot tell you how many times I have been in the midst of a trap, animal pen, or basement only to find myself short on the second most common block of them all.

Flash memory can be a tad unpredictable at times. I have had 4 flash drives die out on me over the last few years, and they usually die without warning. When a flash memory based device dies, the data is likely impossible to recover. Adversely on an HDD, or Hard Drive Disk, even if the disk dies out, someone will probably be able to fix it and get it back to working order—at least long enough for you to back up your data. Hard drives are a bit more forgiving. As you can guess, due to the unpr...

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

Having a custom Linux distro can be the coolest thing ever. Most of you will probably be satisfied with any particular Linux distribution, but I know I'm not the only one out there who wants it to have custom configurations and programs preloaded while leaving the bloatware behind.

Cross-Site Request Forgery (CSRF, pronounce "sea-surf") is a common web exploit. However, for unknown reasons it's not used very often. It plays on a given website's trust in a web browser by executing another website's form action, for example, sending money to another person. It's usually placed in abnormal places like HTML image tags.

You may have asked yourself, "How do hackers take my password, if the website owner can't?" The answer is simple. When a website stores your login password for the site, it is run through a cryptographic hash function before it enters the database (if the website isn't Sony).

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...