Worried about your constant bad breath? Bad breath or halitosis is a common and embarrassing problem. This how to video explains why you might have bad breath and how you can get rid of it. Watch this tutorial and you'll have fresh breath in no time.

Sagging screen doors are a common annoyance. This how to video shows you some simple solutions to fixing those sagging doors on the outside of your house.

Watch this how to video to learn how to make a sachet with common safe and natural household items. Use an old t-shirt, or any other old piece of garment, and your favorite sent

Pharmacist Sue Brenan answers common health questions.Watch this video to learn how to tell if you're dehydrated.

The Gorilla Guard trailer coupler lock (part # 63229 from Tow Ready is covered in this video. This is a trailer lock that fits common 1 7/8 couplers. This video shows you the operation of this lock

Here are a few tips on how one may think about overcoming a very common problem: Stagefright! Enjoy!

With InDesign's Dynamic Spelling you can check/correct your spelling as you go. Also with Autocorrect you can correct your common mistyped words automatically as you type them. In this video Terry White will show you how to enable Autocorrect and enter your own Autocorrect words.

This instructable shows you how to easily make a pressurized rocket from some common household materials.

Ever need ice right away but do not have time to run to the store? Here is an easy way to make water turn into ice instantly. Using a few common household products, produce ice from water in the matter of seconds and enjoy a nice tall glass of a chilled beverage.

Kickboxing is a great form of exercise, but to maximize the benefits of any exercise, you must observe proper form. This video demonstrates nine common mistakes in form and nine tips for preventing these mistakes.

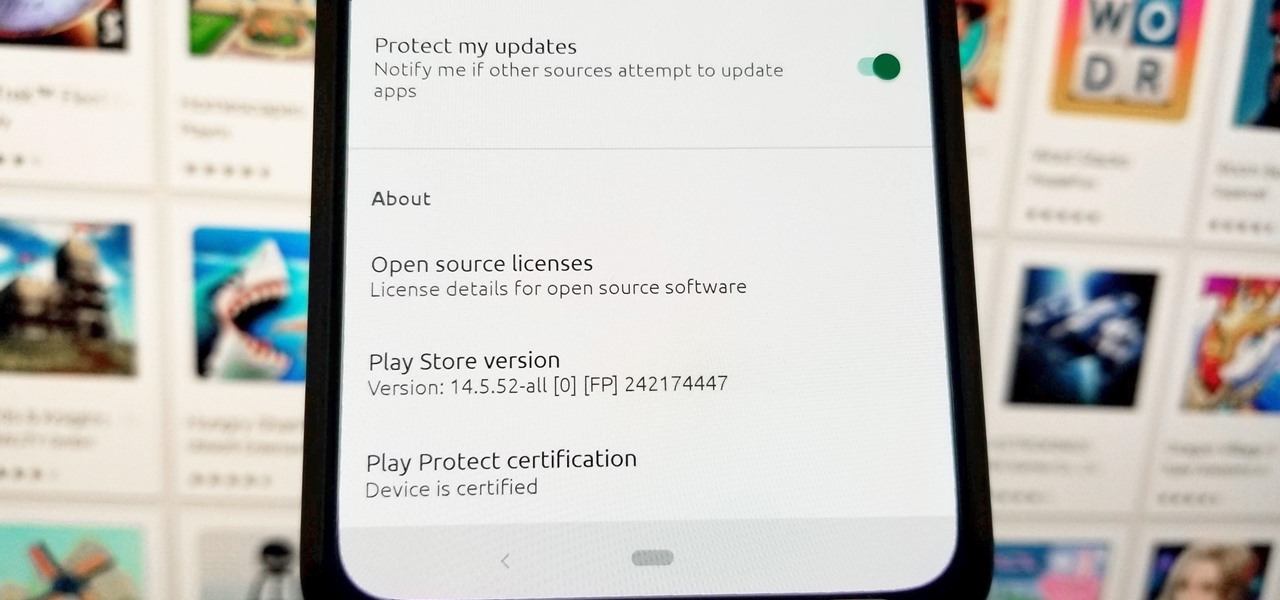
While Apple is full steam ahead on iOS 18, which is expected to drop sometime next month, it hasn't forgotten about iOS 17, which still dominates most users' iPhones. On Aug. 19, Apple issued a rerelease of its iOS 17.6.1 software for iPhone.

As the iOS 18 beta continues, Apple's still investing time into fixing up iOS 17. Compared to iOS 17.4 and iOS 17.5, which both had over 30 new features and changes, iOS 17.6 is a relatively small software update for iPhone. But there are still some important things to know about.

The new Google Meet integration in the Gmail app isn't quite subtle, to say the least. The feature takes up a huge chunk of the display, screen real estate that would otherwise be occupied by, you know, emails. While Google doesn't require you to live with the integration, it doesn't make it clear how to disable it. That's where we come in.

Apple released iOS 13.5 for iPhone on Wednesday, May 20. The update came just two days after the company seeded beta testers iOS 13.5's GM (golden master), the build everyone would get if all went well. While only available to beta testers, the GM is the same software as iOS 13.5's stable release.

Apple just released iOS 13.5 for public beta testers today, Monday, May 18. The GM (golden master) for iOS 13.5 arrives just three hours after Apple released it to iPhone developers, and 12 days after the release of iOS 13.5 dev beta 4.

Apple just released iOS 13.5 for iPhone developers today, Monday, May 18. This GM (golden master) update comes 12 days after the release of iOS 13.5 dev beta 4, which introduced updated COVID-19 exposure notification logging settings and the ability to share your Medical ID with first responders when placing an emergency call.

If you're considering purchasing Apple's new 2020 iPhone SE, which brings many modern components into the compact body of an iPhone 8, you should know what its dust and water resistance rating means. Just how dirty and wet can the iPhone SE get without breaking any functionality?

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

The still-unfolding story of China's Nreal augmented reality startup continues to develop, with each turn uncovering another unexpected wrinkle.

We've been so worried about volumetric scans possibly robbing celebrities and performers of their agency and right to control their image that, somewhere along the way, we forgot that scans may not always be necessary to produce passable holographic performances.

What could Apple be planning here? Are we going to see some revolutionary new features for the iPhone? Will we see mostly bug fixes and security patches? It's time to find out, as Apple just released the first developer beta for iOS 13.4.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

While the automotive industry is moving towards adopting AR displays in future models, BMW is already shifting into the next gear with its vision of the technology.

The Pixel 4 is one of the most talked-about phones of 2019, so you know there will be lots of third-party developer support. Mods are already popping up, so you'll want to get Magisk installed as soon as possible to get root access. The current method used to gain root is the quickest way yet, thanks to the recent TWRP custom recovery support for the Pixel 4.

Beta testing Apple's mobile OS has never been more interesting. After eight seeds of iOS 13.0, Apple unexpectedly released the first beta for iOS 13.1, a whopping 23 days before iOS 13.0 made its public debut. Since 13.1, however, we haven't had any betas to sink our teeth into. That is, until now, as Apple just released the first developer beta for iOS 13.2 today, Wednesday, Oct. 2.

Former soccer star and current celebrity David Beckham has the augmented reality abilities of Facebook and Instagram as allies in the effort to eradicate malaria from the world.

Gboard is often considered the best keyboard for iPhone or Android. Google made sure to jam-pack it full of features, and you should expect nothing but the best when it comes to Google's own first-party software. But with so many capabilities, a few things might slip through the cracks.

It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

The long-awaited Dark Mode may have grabbed all the spotlight with iOS 13, but Apple has made subtle changes across the whole platform to make your iPhone even more user-friendly. A small option aimed at people who are sensitive to motion is one such example — a feature that can also be a godsend for the rest of us.

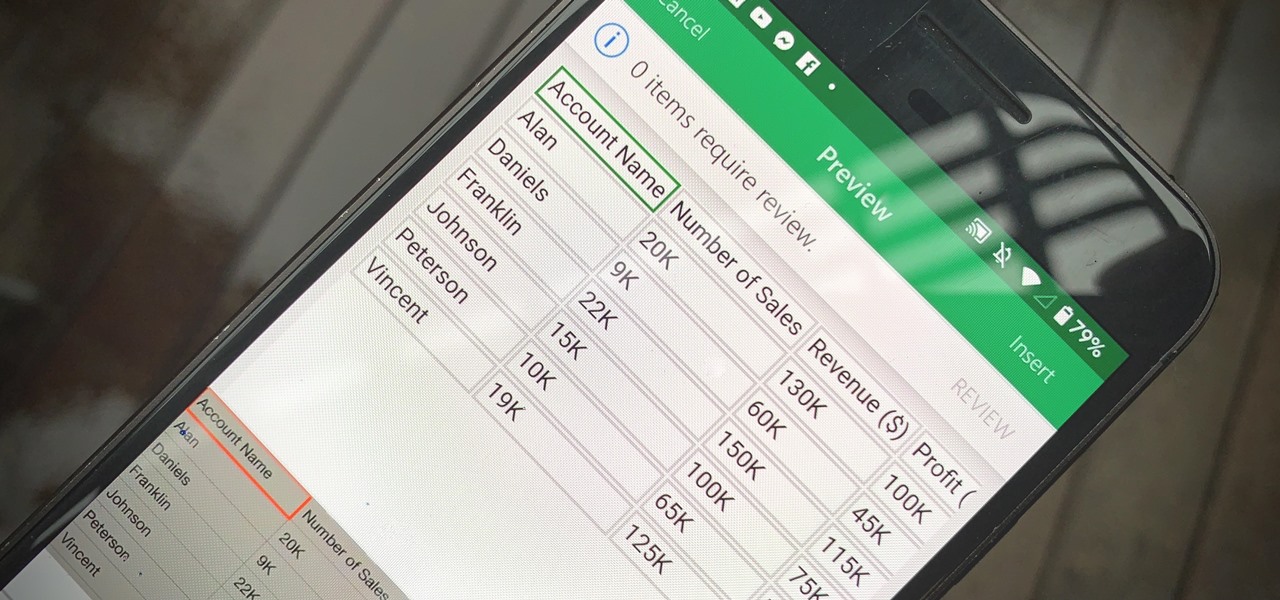
Creating a digital spreadsheet by hand can certainly be tedious, especially if you're copying a printed paper table word for word, number for number. Instead of typing information that's already there, however, use Microsoft Excel on Android or iOS to snap a photo of that printed chart and import it directly into your digital one.

When it comes to customizing Android, there's no better way to make it your own than by installing a custom ROM. You gain new features that were not accessible on the stock firmware that came with the phone, and you get complete control over how your system looks and feels. But there's definitely a learning curve.

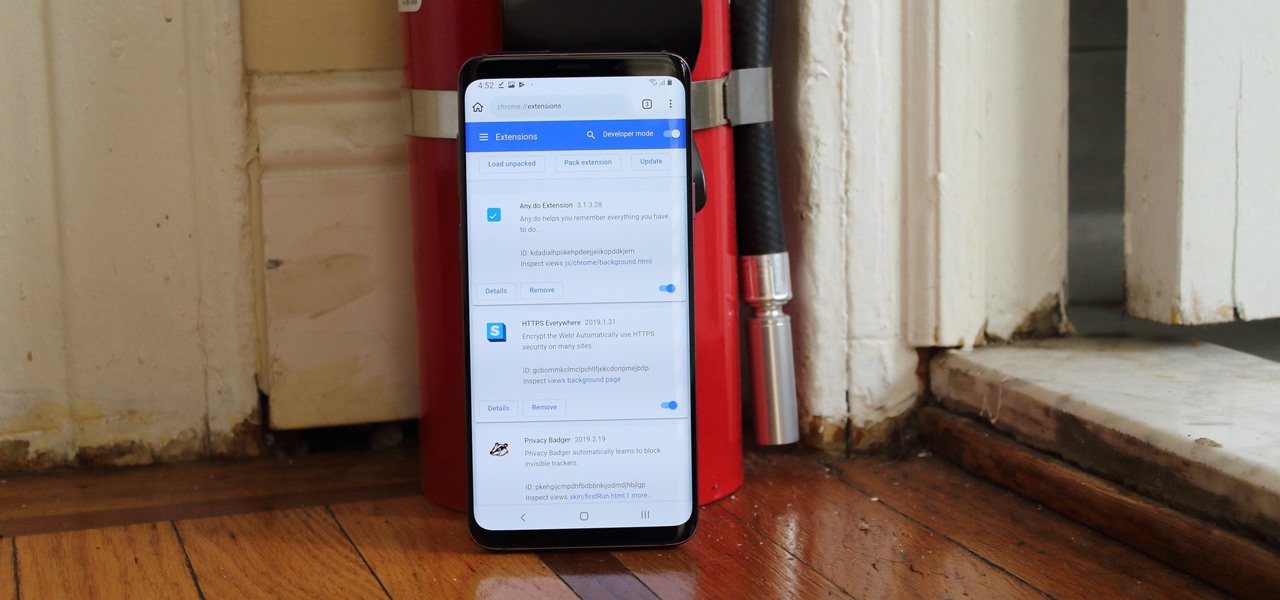
For years, there has been a disconnect between the Chrome app on your smartphone and the Chrome browser on your computer. The latter was a powerfully fast browser which could be enhanced with extensions to add new features and functionality, while the former was just a fast browser. Well, that all changes now.

The camera punch hole on the S10 has gotten our creative juices flowing more than any notch ever could. First, we saw wallpapers that served to camouflage the cutout or even accentuate it. Now, if you want to go the opposite direction and highlight your S10's camera hole, there's an app that turns it into a circular battery meter.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

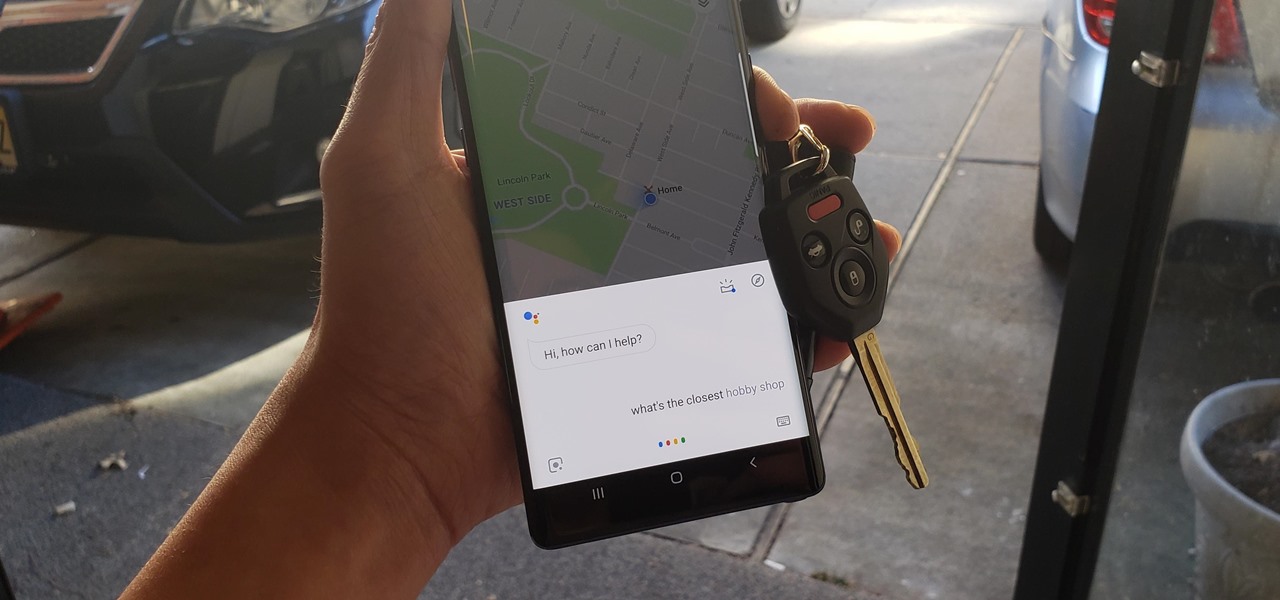
Millions depend on Google Maps for directions, and it's easy to see why. The app comes with tons of features like offline navigation, location sharing, and more. Google is far from done, however, and continually improves upon its navigation app to make it even more efficient and safer to use.