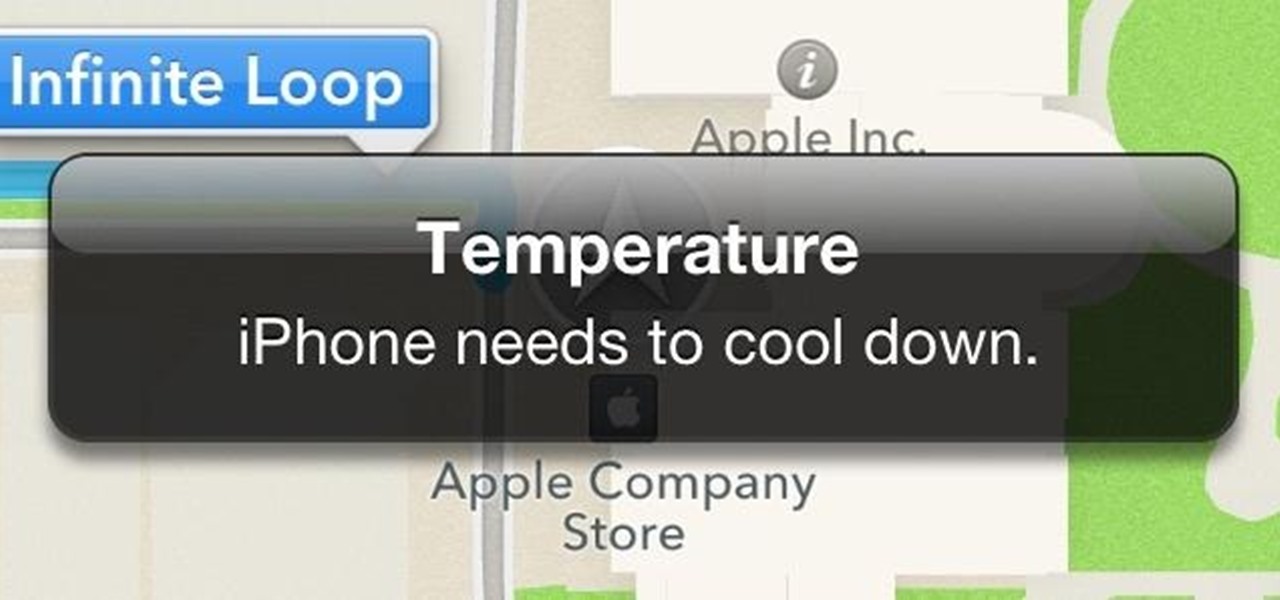
A few months ago I was driving around trying to find a store using Apple Maps (a terrible situation in and of itself), when my iPhone decided to shut off in the middle of giving me directions. I had no idea what happened, and when I looked at the screen, I saw this: My phone had never overheated and I really didn't know what to do. Needless to say, I couldn't really get to where I was trying to go without those directions. I pulled over and waited for the phone to cool back down, which took a...
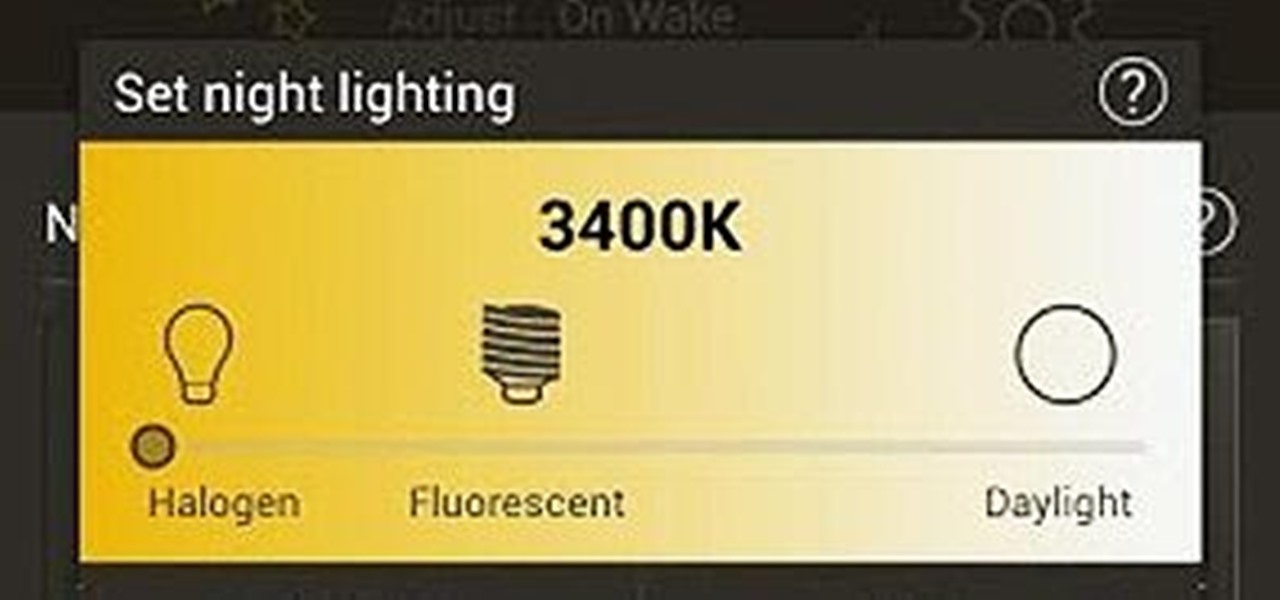
When it comes to our smartphones and tablets, we're always on the lookout for ways to beat the oh so common rapid battery depletion problem that affects practically every mobile device. We'll do anything and everything to keep our battery life at an optimum, from turning off certain features (Wi-Fi and Bluetooth) to removing widgets and applications that use an exorbitant amount of CPU. One of the most popular and efficient ways of saving battery is to lower the screen brightness. Usually, we...
The world is surrounded by negative vibes, everyone of us needs to be positive in a way to have a balance in life. I will share with you, what are the steps to be an optimistic person.

If I could win a trophy for waking up to go to work or for eating a bowl of Frosted Mini-Wheats without any of the biscuits getting soggy, I think my life would be so much more awesome. The gaming industry has cornered the market when it comes to achievement-based rewards, because they know that we love challenges.

I had my wallet stolen a few months ago, and I knew I would never see it again. My biggest gripe was not the credit cards in there, since they're easily cancelled, but the gift cards. I had some pretty good gift cards in there, and there's no way to get those back.

Life has many perils: parasites, predators, and pitfalls. Eventually, any organism will succumb, and if that organism has not first passed on its genes, those genes will face extinction.

Believe it or not, capturing a beautiful shot of a vehicle is more difficult than you think. Sure, you can just snap a photo, but capturing the design, detail, and essence of the car is a whole other story. Lighting, location, settings, and angles are play into how well the photographic representation turns out.

The PlayStation 3 is a sweet gaming system, and even though Blu-ray discs didn't really live up to all the hype and there is still no HBO GO app available, I love my PS3. One of the coolest things about it is that you can customize it to look however you want. One of the most common ways to do this is by changing the wallpaper, but most people use their computers to transfer wallpaper images over.

It only takes a minute for something well intentioned to turn into something sinister. Facebook created 'memorial pages' as way for friends and family to share their thoughts and feelings for those that are no longer with us.

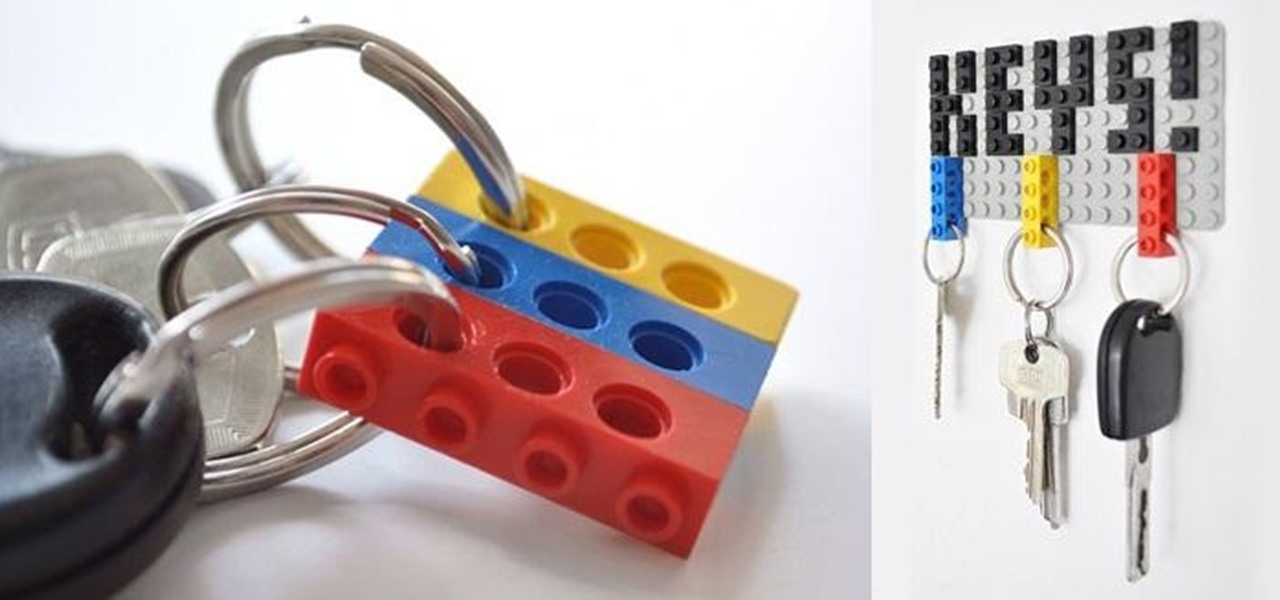
LEGO may no longer be in its heyday, but those colored building blocks of joy can still make some really cool and creative things. I mean, take a look at these pieces from LEGO artist Nathan Sawaya. While making something like that is undoubtedly impressive, it could be just a little too difficult for the common LEGO enthusiast—and expensive (LEGOs aren't cheap these days). So, for the regular LEGO-builders, usefulness is more important that extravagance.

Link shorteners like TinyURL and Bitly are great for Twitter (or anytime you're limited on space), but they're also great for hackers. It's easy to hide a malicious link in an innocent-looking shortened URL, which increases the chances that people will click on it.

Firstly, I'd like to say that I have nothing against iPhoto; it's a great application that works wonderfully in Mac OS X. Unfortunately, when you no longer have iPhoto on your MacBook—and you don't want to pay for it—looking for an alternative is a necessary endeavor. I could sit here and try to explain to you how I updated to Lion and then inexplicably dragged the iPhoto application into the trash—and proceeded to empty said trash. I could tell you guys that story, but I fear you might judge...

In an effort to appease iPhone fans eager for an NFC-equipped device, an option that is available on many other smartphones, Apple created Passbook, their version of a digital wallet.

Collodion—it's one of those things that you probably never heard of before, but have actually come across many times in life. It's used for all kinds of applications, from photography to special effects, and it even has a few medical uses. So, what exactly is collodion? Photo by Bostick & Sullivan

At the recent DefCon conference in Las Vegas, researchers opened many of the top commercially available gun safes with simple tools like a straw or a paper clip, and in one case, just by shaking it a bit. The investigation began after the researchers, Toby Bluzmanis, Marc Tobias and Matt Fiddler, learned that certain Stack-On safes, issued to some law enforcement officials to secure their firearms at home, could be opened simply by jiggling the doorknob.

Wish your home wireless network was faster? You can always buy a signal booster, but if you'd rather not spend the money, here are a few tips and tricks to speed up your wireless connection, including how to make a homemade signal booster with things you probably already have lying around.

RFID cards are becoming a fairly common way to purchase goods, but they're already widely used to pay fares on buses, trains, subways, and trolleys across various cities. TAP cards are quick and reliable, but it can be a real pain to remember to bring them with you, especially if you weren't planning on using public transportation that day. Luckily, an intrepid tinkerer at Adafruit has managed to find a way to embed an RFID card into her phone, something you're far less likely to leave at home.

Poor alignment of cabinet doors will cause a kitchen to look run-down and may be embarrassing to the homeowner. Luckily, with a single screw driver and a little ambition, the door alignment can look brand new.

Does your car idle high and make an obnoxious racket every time you are stopped at a light, drawing dispproving looks from your fellow motorists? If you are into home car maintenance, you may be able to diagnose the cause of this problem yourself. This video illustrates how to test for one common problem that leads to a high idle, a faulty throttle position sensor, the contacts on which have been worn down by the throttle. You will need an analog multimeter to test the ohm load from the senso...

The great thing about having long hair, is the ability to do almost anything to it. You can flatten it, cut it short, place it in a ponytail and of course curl it. There are so many ways to curl hair, but one of the most easiest and common ways is by using a curling iron and some basic hair products such as hair spray, a comb, and of course, patience. Sit back and find out how to curl short hair easily in this tutorial. Enjoy!

In this tutorial video, hosted by harrymedan, you will learn how to fix a broken or nonfunctional select button on your iPod, as well as the common causes of the select button no longer working. According to the host this problem is usually caused by the battery in the iPod itself. He suggests opening up the back of the iPod and replacing the old battery, which is usually swollen from being charged so many times, and puts pressure on the select button causing it to become inoperable. If you a...

When you are tested for drugs, the drugs can be found in your hair and blood. There are three types of tests: hair test, blood test and urine test. The urine test, being the cheapest, is the most common drug test. Some ways to beat this unwanted drug screening is by drinking x-amount of water, this dilutes the drug within your system. The second method is to inform them that you are a user, or that you attend frequent rock concerts. (This method isn't recommended because of the outrageous amo...

Use a motor to make a fan and a speaker. People often take for granted the common items and devices they use in everyday life. Looks can be deceiving. It's not what things appear to be, it's what they can become.

It's time for some golf! What's an 18-year-old know about distance? Justin James can belt it 400 yards and more, and with his power tip, you too can tack on a few extra yards. Well, maybe not 400 yards, but you get the idea. See how to get more power out of your golf drive.

This truck repair video shows you how to remove the bed from a Chevrolet C1500 W/T truck. This needs to be done to fix certain problems, in this case the fuel lines. Whatever reason you need to remove the bed from your Chevy, this video shows you how to do it properly.

PEX, or cross-linked polyethylene, is a common alternative to copper piping. If you're looking to save time on your project (or have an aversion to soldering), PEX might be for you. In this tutorial, you'll learn what PEX is and how to decide what type of PEX is best for your application.

Learn what common time or 4/4 time is and how you can use it with this how to video. This music theory tutorial will help you understand the concept of time signatures and counting rhythm.

Dr. Ari Goldsmith discusses the diagnosis of swimmers ear and a few common treatments.

A Look into Internet Marketing including common pitfalls to avoid and how to build a userbase. Part 1 of 2 - How to Get into Internet Marketing.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Smartphones have put an end to camcorders. If you want to capture memorable moments in high quality, look no further than that technological marvel in your pocket. Recent Galaxy phones are shining examples of how far we've come — but the more capable a camera gets, the more complicated things can be.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

You may not have heard of visceral leishmaniasis, onchocerciasis, or lymphatic filariasis, and there is a reason for that. These diseases, part of a group of infections called neglected tropical diseases (NTDs), impact more than a billion people on the planet in countries other than ours. Despite the consolation that these often grotesque illnesses are "out of sight, out of mind," some of these infections are quietly taking their toll in some southern communities of the US.