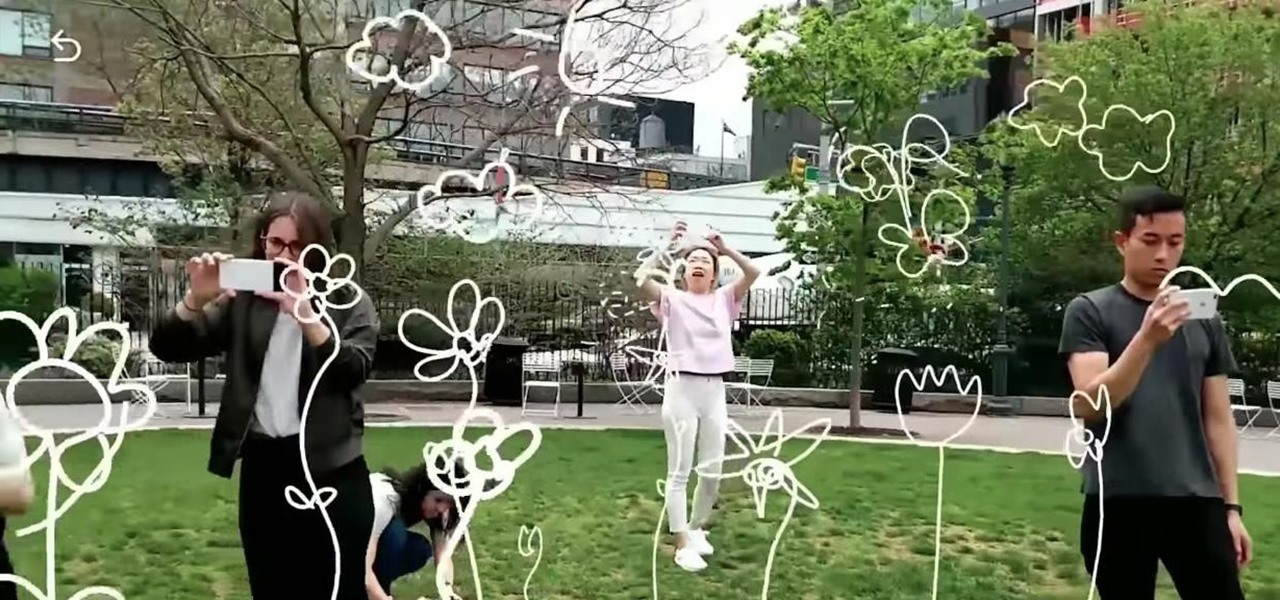Samsung's not one to make drastic changes to what already works. They've continued on with the IP68 rating under IEC 60529 first given to the Galaxy S8 all the way to the the Galaxy Note 10. If you're a little confused as to what this rating means, don't worry, it's actually pretty simple once you get to the meat and bones of it.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Learning Chinese is hard, but it can be a lot easier with the help of a few great apps. As a native English speaker who's currently living in China, this is a process I've recently gone through. After playing the field, here are the three apps I personally think will help you the most with your Chinese learning adventure.
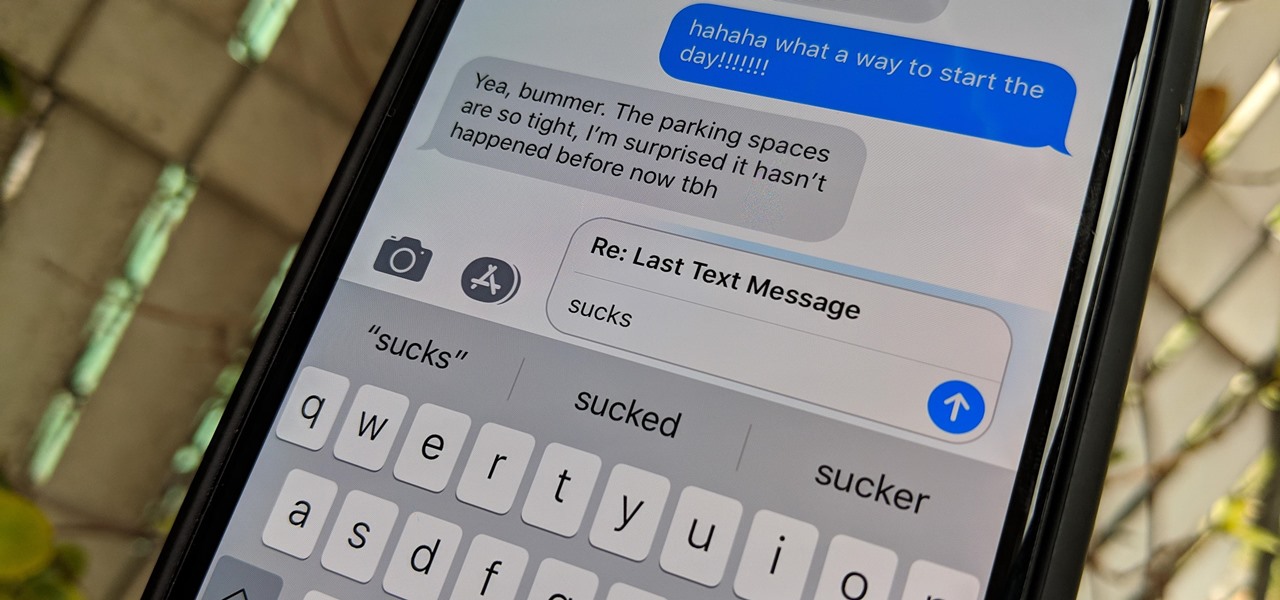
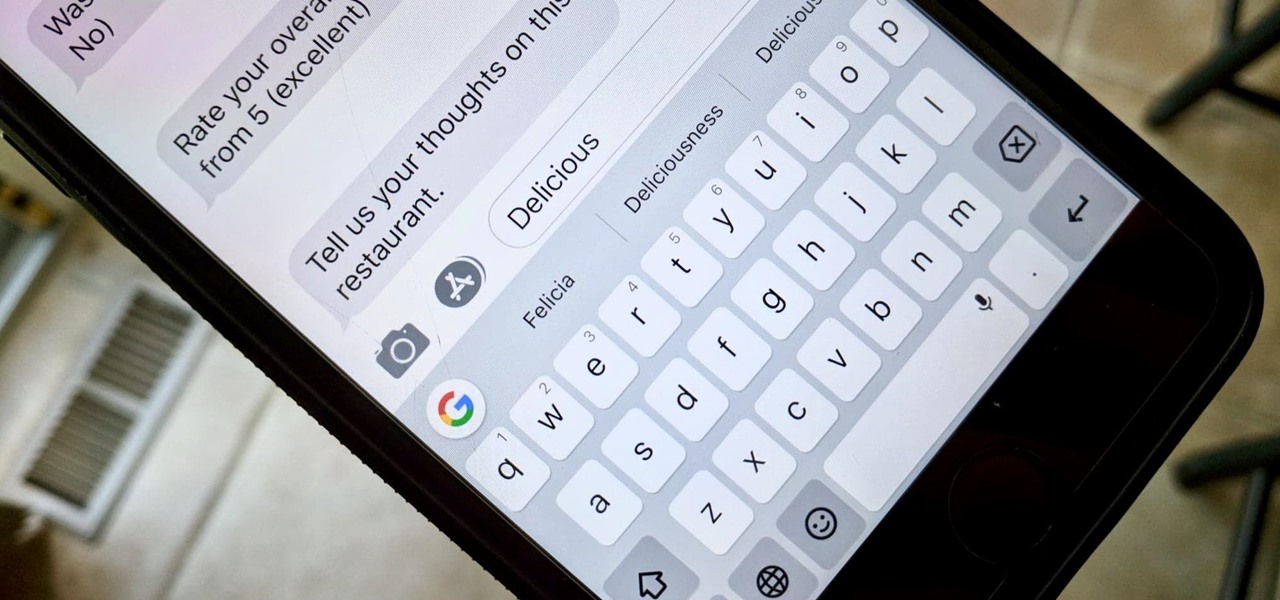
The subject line is a crucial part of an email, but you don't see it very often in texts. That's mostly because many people don't even know it can be done, and even if they do, why would they use it? Just like with emails, subject lines can make iMessages and SMS texts seem more important and more professional. Plus, they can help with organization and searching past messages, as well as make text bold.

Two years ago, Facebook founder and CEO Mark Zuckerberg kicked off the F8 Developers Conference keynote with augmented reality and the introduction of Facebook's AR camera platform, now known as Spark AR.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

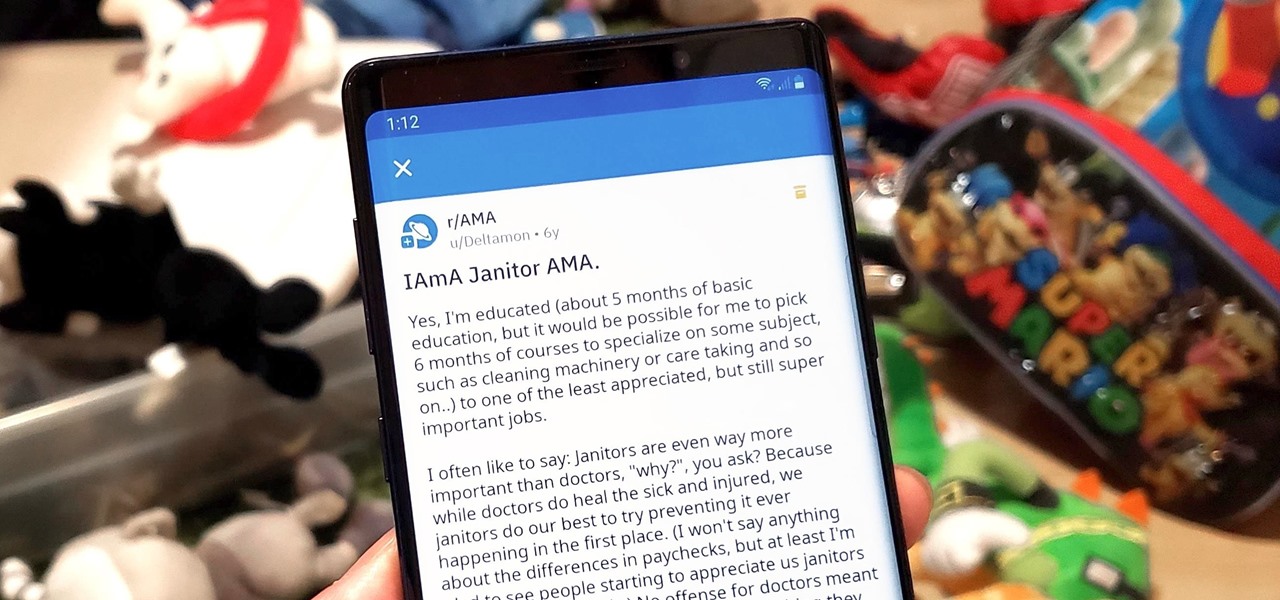
Short for Ask Me Anything, AMA threads are one of Reddit's signature features. They enable you to directly interact with a whole range of interesting personalities, from common folk with amazing life experiences to influential celebrities that help shape politics and culture.

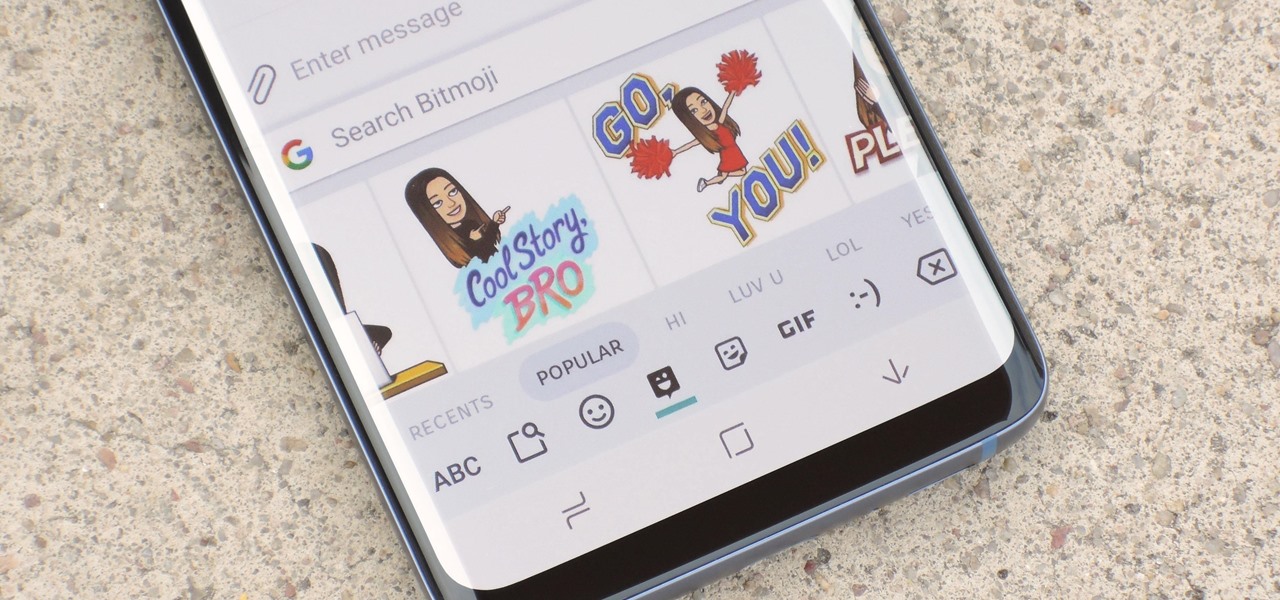
Bitmoji are personalized emoji that look like you and can be used to make funny memes or snappy replies. Normally, you have to find one of these reaction emojis in the Bitmoji app, then use Android's share menu to send it to the app where you ultimately want to post it, but there's a much better way.

The release of Avatar Chat for Magic Leap One and Spatial for HoloLens during the fourth quarter of 2018 appeared to revolutionize video calling via augmented reality.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

This year's holiday shopping season is shaping up to be fertile ground for augmented reality to show its worth, as both Walmart and Target have crafted immersive experiences designed to engage shoppers in the coming weeks.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

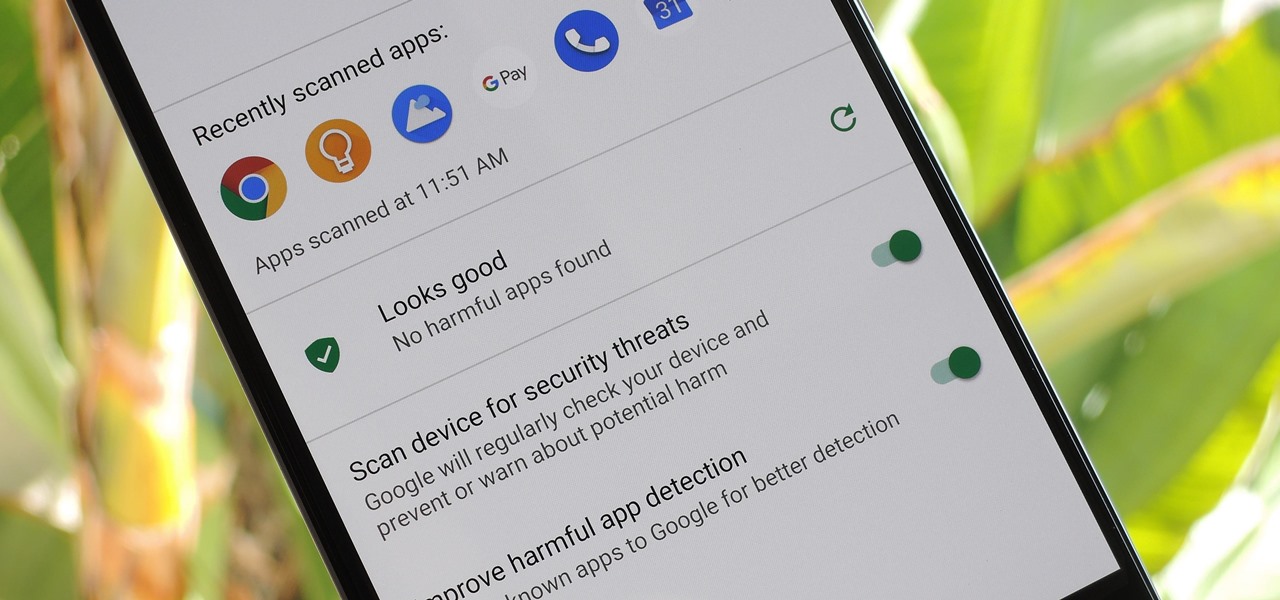
According to Google's new Android ecosystem transparency report, you're eleven times more likely to be infected by malware if you're running Android Lollipop (5.0) as opposed to Android Pie (9). The same report shows that if you sideload apps, you're almost seven times more likely to be infected than if you stick to Google Play as your app source. All of the data provided in the report is quite interesting, but there's a clear pattern among malware-infected users.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

In 2018, notches are the hot trend with smartphones. Essential was first to release a phone with a notch in mid-2017, but Apple kicked off the fad in earnest with the iPhone X. Unfortunately, unlike the iPhone X, every Android phone with a notch has a noticeable bottom chin. Let's take a deep dive to find out why.

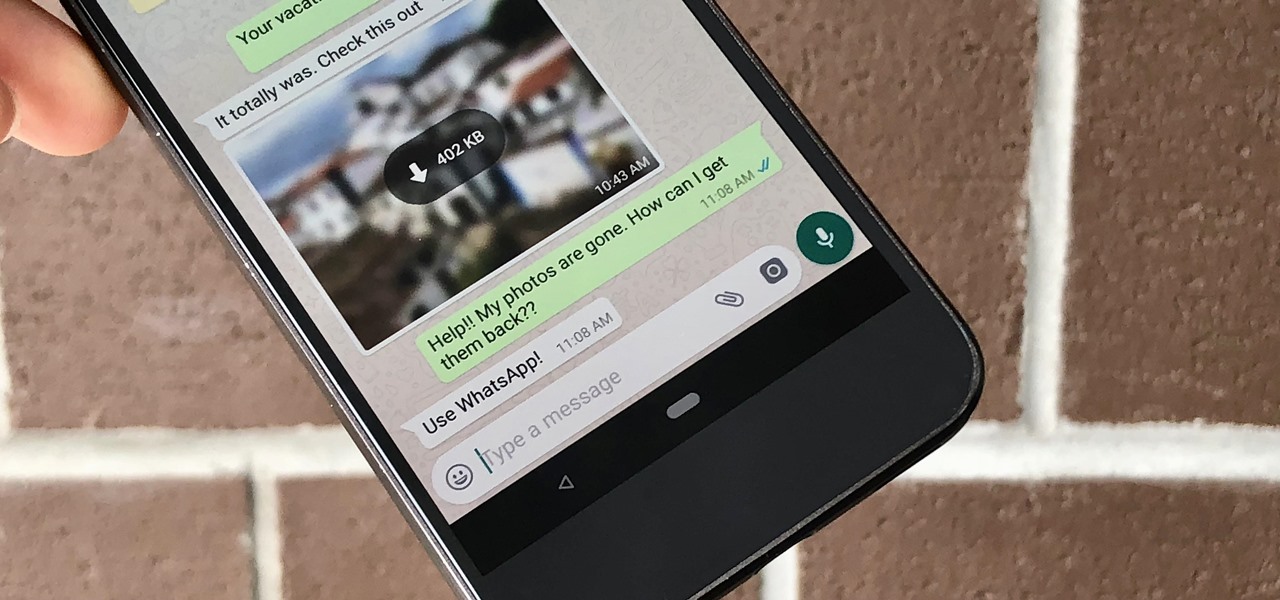
Thanks to cloud storage's increasing accessibility, permanently losing photos is becoming less and less common. Still, if you accidentally delete a picture from your smartphone without first making a backup of some sort, that data is pretty much toast — unless we're talking about photos from WhatsApp.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

As summer is upon us, new musical Snapchat lenses are as well. This week has entries from Maroon 5, Simon and Garfunkel, and Snow Tha Product with entertaining visuals to match. As kids start to leave school for the summer, expect the lens scene to be kicked up a notch with anticipation.

Predictive text is a common feature in most mobile keyboards these days. However, many times, its guesses are way off, sometimes hilariously so. As absurd as it can be, predictive text can also continuously suggest the same wrong word over and over. Thankfully, Gboard offers users a way to quickly remove these suggestions for good on both iOS and Android.

In the arms race between ARKit and ARCore, Google scored a big win with the announcement of its Cloud Anchors shared AR experiences platform at Google I/O on Tuesday.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

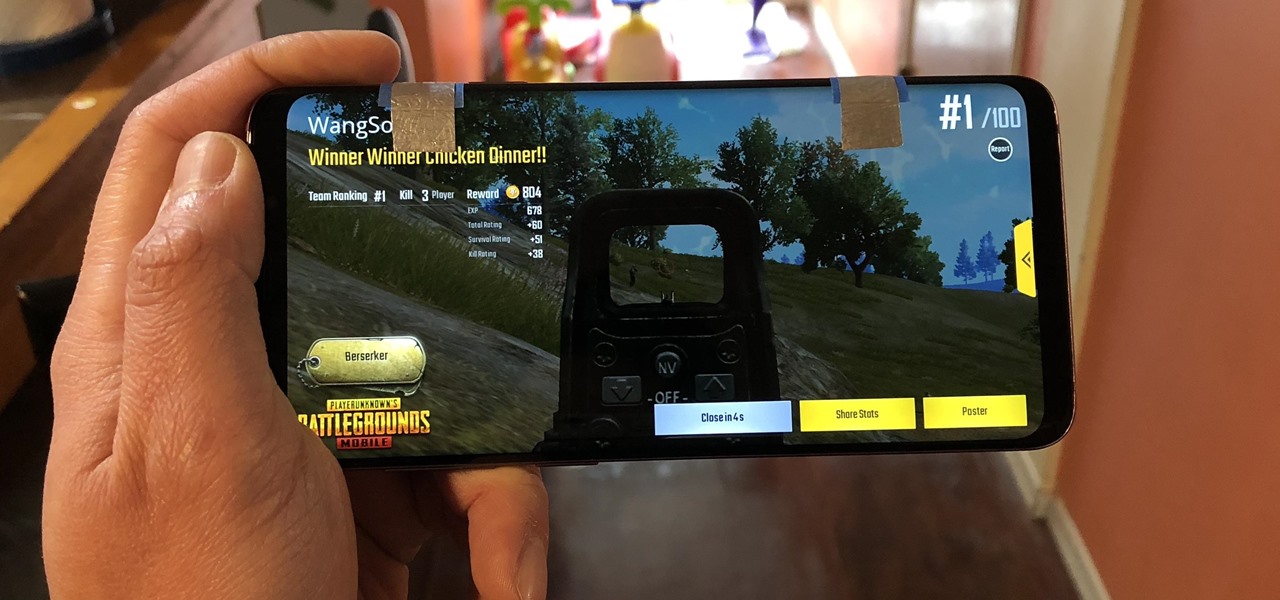
With ultra competitive games like Fortnite Battle Royale and PUBG taking the mobile world by storm, gamers are looking for ways to get a leg up on the competition. One of the biggest advantages you can give yourself is the ability to aim and shoot while on the move, but that's not exactly easy with a touchscreen.

As the week of the Game Developer's Conference hits the mid-point, we've already had some major announcements hit the AR space. The specific timing of these announcements are thanks in part to a conference within a conference called VRDC, aimed at VR, AR, and MR developers. And while the week is hardly over, the announcement that is still having a big effect on the developer population is the reveal of the Creator Portal for the long-awaited Magic Leap One device.

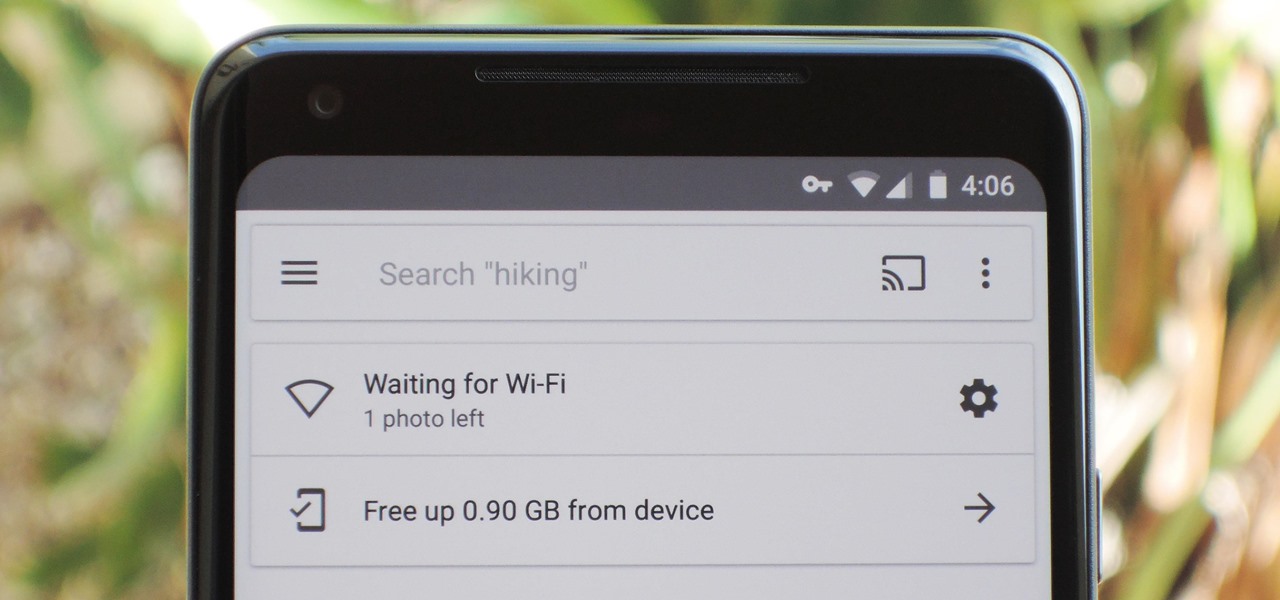
If you're on a limited data plan, you no doubt set Google Photos to only back up over Wi-Fi on your Android device. In recent months, however, there have been many complaints that Photos won't actually back up your pictures when you get back home and connect to your network. Thankfully, the fix is fairly simple.

Not content to just be a provider of rugged smartglasses for enterprise users, DAQRI has made the jump into the AR software side of the industry with its new Worksense productivity suite.

Apple's Animojis took the world by storm with their ease of use and fluidity. They added new life to your emojis by mapping your face with the technology that lives inside the iPhone X. Now, Samsung is also adding new life to emjojis with the introduction of AR Emojis in the Galaxy S9 and S9+.

Not all microwaves are created equal, so when you use the recommended cooking time on any microwaveable meal, chances are you're actually cooking the food too much or not enough. And unless you're really good at mental math or have a virtual assistant that's smarter than Siri and Google, you have to do things the long way — but not with these helpful apps for iOS and Android.

When it comes to media players, few are more capable than VLC. With its extensive codec support, VLC is able to play almost any video file. Partly due to its open-source nature, features are constantly added. This trend has continued with a new update that added native Chromecast support.

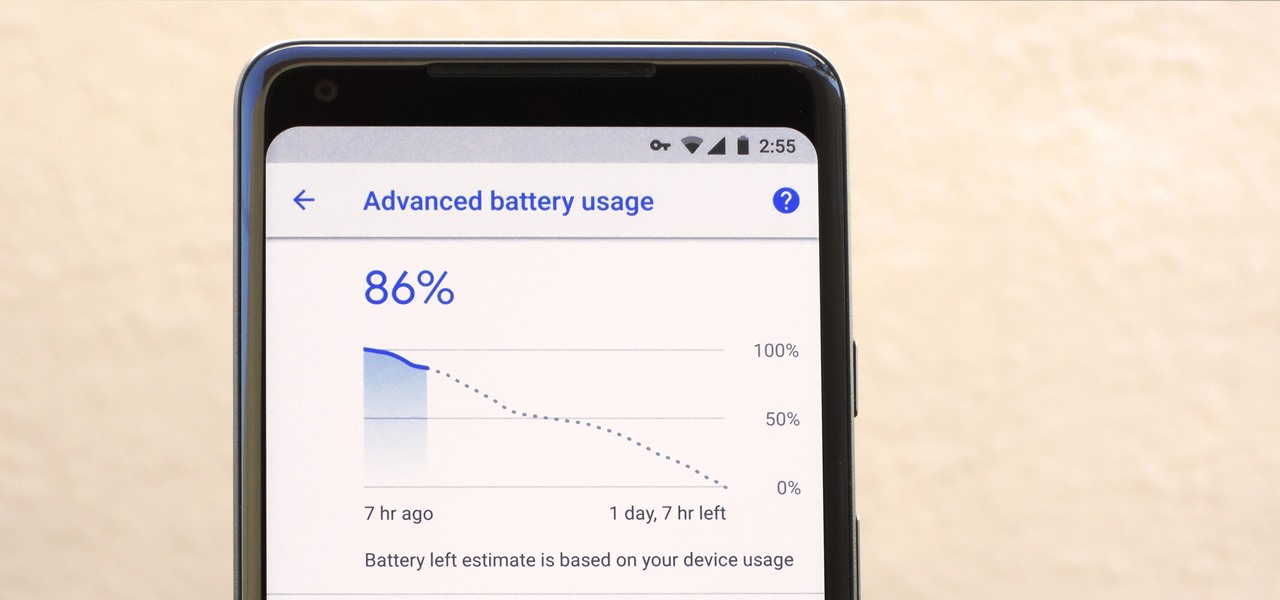
After Apple's recent fiasco, it's now common knowledge that smartphone batteries degrade over time. But aside from causing terrible battery life, a degraded battery can also trick your phone's software into thinking the device has more juice left than it actually does.

Just a week after news leaked out about Intel's 2018 plans for smartglasses, the company revealed what the device looks like and how it works in a new video (bottom of this page) released on Monday.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

A new survey of game developers paints a somewhat less than rosy future for augmented reality gaming, but there's still some hope for its long-term prospects.

Apple didn't invent the concept of photos with videos embedded (that credit goes to HTC and their Zoe feature), but they sure did popularize this functionality when they came out with Live Photos. If you're jealous of iPhone users, you certainly don't need to be — there are several great ways to recreate Live Photos on Android.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Just in time for the holiday season, Lenovo has released its Mirage AR head-mounted display with the Star Wars: Jedi Challenges game and accessories. Unfortunately, while its price point is a fraction of most other AR headsets, at the moment, it does have a few issues with the setup process.

We may have to wait a few years before they arrive, but reports of Apple's headset taking shape in Cupertino gives the tech world hope that its white knight for consumer AR is on its way.

With technology giants like Apple and Google finally entering the fray, the move toward mass adoption of augmented reality is ramping up. Apple's ARKit and Google's ARCore will allow entirely new categories of apps to be made. Unfortunately, in a world of heavy competition, getting these two frameworks to work together wasn't a priority for either company.

Google's new Pixel 2 and Pixel 2 XL have a new camera mode called "Motion Photos." As the name implies, it's quite similar to Apple's Live Photos feature or HTC's Zoe before it. For every picture you take, a few seconds of video footage from before and after the shot was taken will be embedded in the file, which gives you two ways to relive that moment.

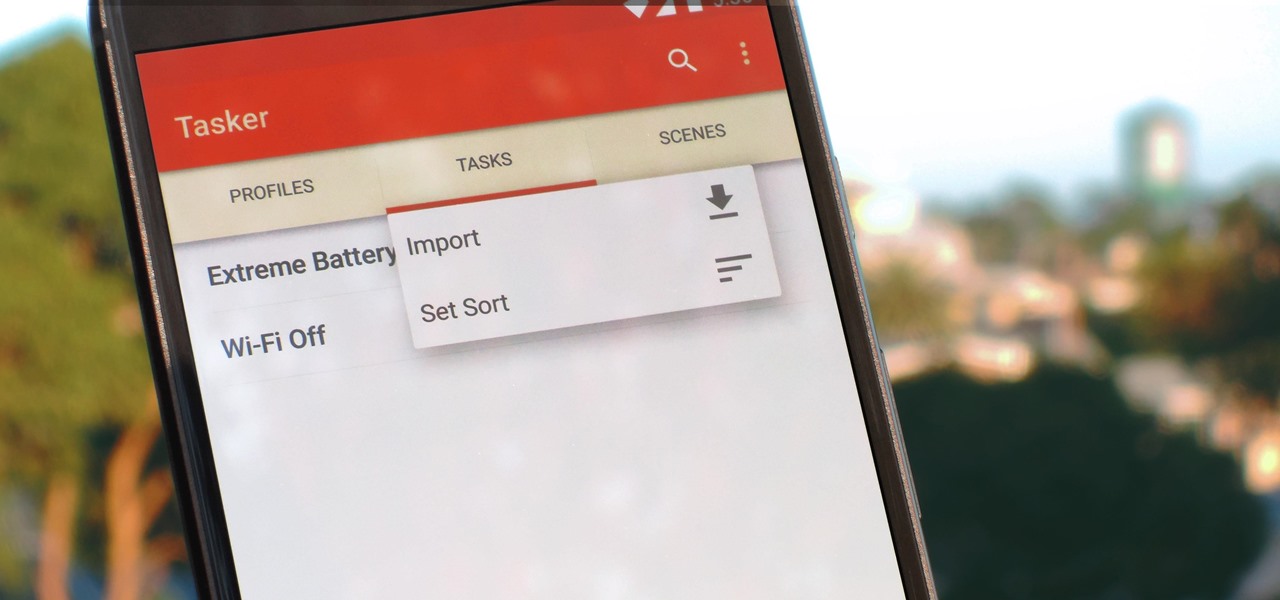
Regardless of what you're trying to accomplish with Tasker, there's a good chance that someone else has already walked through the same steps. If you're unfamiliar with creating tasks and working with profiles, simply importing someone else's work would be a great shortcut. After all, there are 2 billion Android devices out there, so someone must've created a setup that suits your needs, right?

Google just bought a huge chunk of HTC for $1.1 billion. They're bringing in around 2,000 employees, mostly from the hardware division, and these folks will presumably work under hardware chief Rick Osterloh. There's a massive patent portfolio involved, too, so stop me if you've heard this before — Motorola, anyone?