One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

When I review apps, I'll oftentimes end up downloading at least one or two "bad" apps that either lied about their functionality or were riddled with ads. These apps, while not as harmful as malware, can still be a major headache. This got me thinking about the other bad apps on the Play Store and how to avoid them.
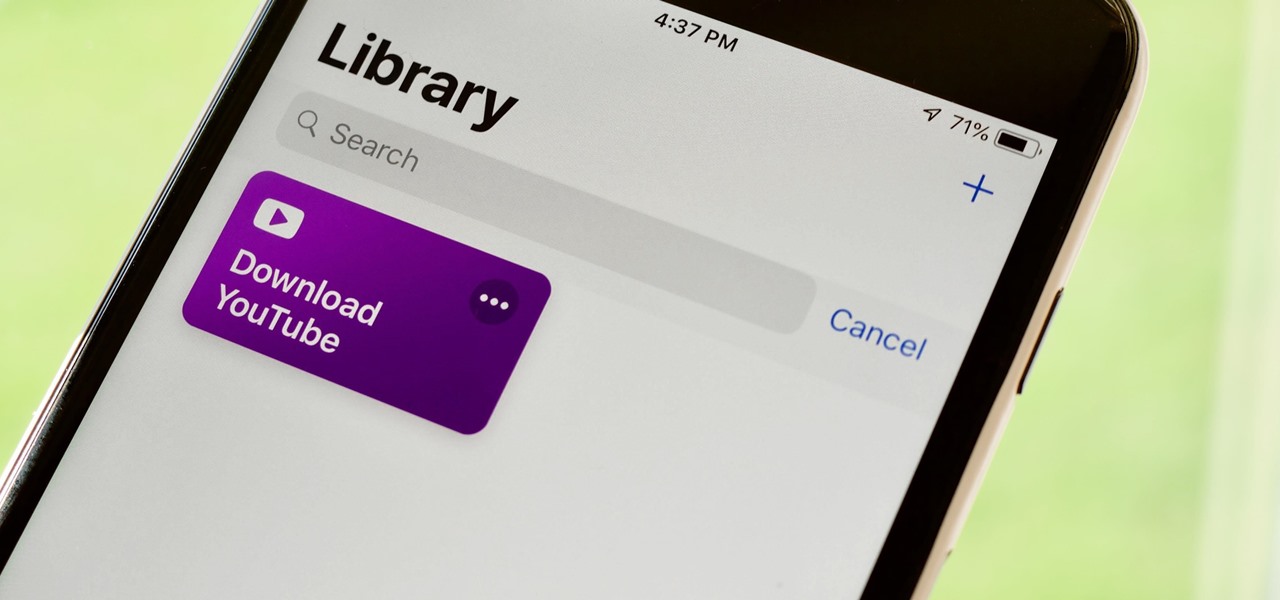
If you've ever wanted to download YouTube videos directly to your iPhone, there's an easy solution — just update to iOS 12 and install Apple's new Shortcuts app. With the Workflow-replacement app, you can add a shortcut that lets you download any YouTube video you want, without needing to jailbreak or use shady third-party tools.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

The new iPhone XR, XS, and XS Max have everyone buzzing. But, at first glance, the XR and XS look pretty similar in almost every way. So, what's the difference? It comes down to the XR's "Liquid Retina" LCD screen vs. the XS's "Super Retina" OLED display. How do they compare, and why does it matter when considering which new iPhone to preorder?

They're finally here. Apple announced three new iPhone models at their "Gather Round" event in Cupertino, and they're all absolutely gorgeous phones. With bezel-less screens and polished titanium edges, the iPhone XS, XS Max, and XR are truly marvels of engineering — but perhaps the most impressive design feat Apple pulled off is the fact that two of these models are rated IP68 under the IEC standard 60529.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

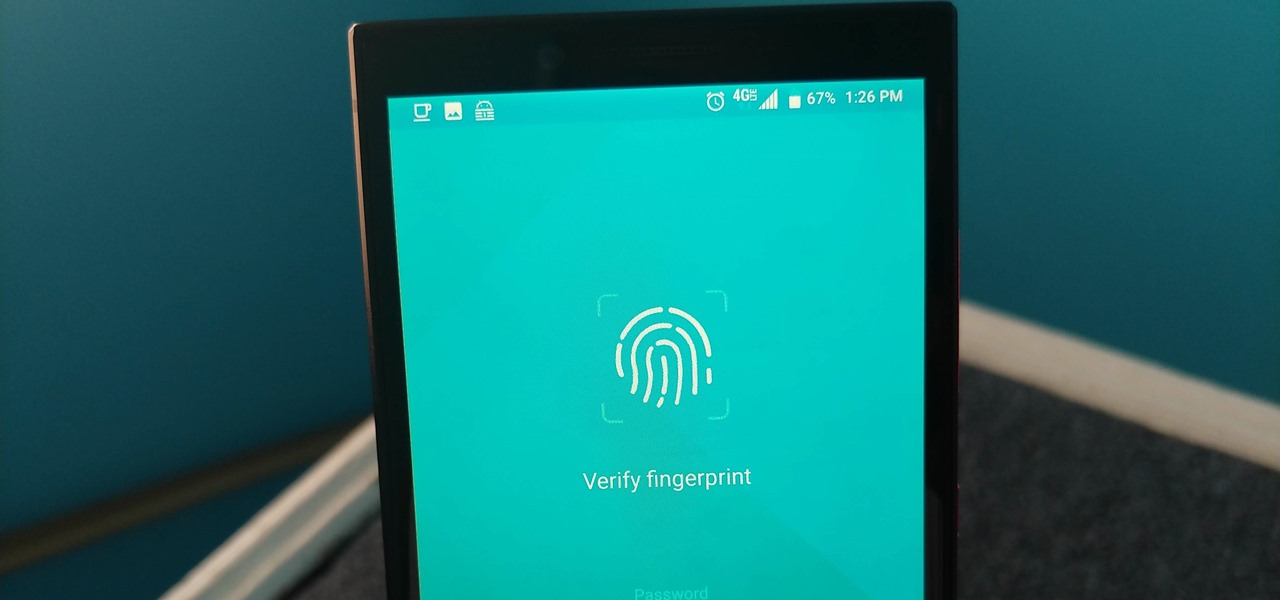
Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

There's a feature in the Gboard keyboard that enables people who cannot talk, type, or swipe normally to still have a way to communicate in the digital age on their smartphones. While it's mainly an accessibility feature for those who actually need it, it's a good way for anyone to learn or brush up on their Morse code skills — and it works on both Android and iOS.

There are some nasty iOS bugs out there, many determined to crash the Messages app. For example, in February 2018, we saw a Telugu character render the iPhone messaging app totally useless. While that bug has been fixed, the nightmare continues in a new bug, aptly dubbed the "Black Dot."

Bookmarks and favorites are handy options for saving interesting websites you come across while surfing the web on Android but are far from ideal when it comes to instant access. Thankfully, Google Chrome gives you the added ability to save webpages and progressive web apps directly to your home screen for added convenience.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

It doesn't matter how cool or groundbreaking a particular technology is, if it doesn't offer the promise of big returns on investments, you'll have trouble drawing interest from both Silicon Valley and Wall Street. That's why we're increasingly seeing existing augmented reality players doing everything they can to focus in on revenue generation, which was the message coming from Snap Inc. this week.

If you can't afford an unlimited plan, you're limited to a certain amount of data each month on your iPhone. Even some unlimited data plans have carrier-imposed mobile data caps that throttle the user if they exceed them. Keeping track of your exact usage each day will help make sure you don't get billed more or throttled like a chump near the end of the month.

With the reveal of Magic Leap's developer documentation last week, many questions have been answered—and several new ones have been raised as well. But since the Magic Leap One (ML1) isn't simply called the "Leap One," these are questions that the company probably has no interest (at least for now) in answering. Understandably, Magic Leap wants to keep some of the "magic" under wraps.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.

In this series, we are going to get you to the edge of building your own cloud-based, cross-platform augmented reality app for iPhone, Android, HoloLens, and Meta 2, among other devices. Once we get the necessary software installed, we will walk through the process of setting up an Azure account and creating blob storage.

Now that we've had a chance to jump into the Lumin SDK documentation at Magic Leap's Creator Portal, we now have much more detail about how the device will function and utilize software than any single piece of content released by Magic Leap to date.

One of the biggest improvements with the Galaxy S9 and S9+ is the redesigned camera, with the latter scoring an impressive 99 overall on DxOMark. But with an abundance of features and enhancements, tweaking the camera's settings for optimal performance can be a little confusing.

Because augmented reality is still so new to so many people, there are a number of would-be experts opining online, often repeating basic facts anyone with a spare 15 minutes can find on their own. That's why it's important to point out when someone delivers what could be considered the ultimate cheat sheet for ramping up your AR IQ if you're unfamiliar with the finer points of the space.

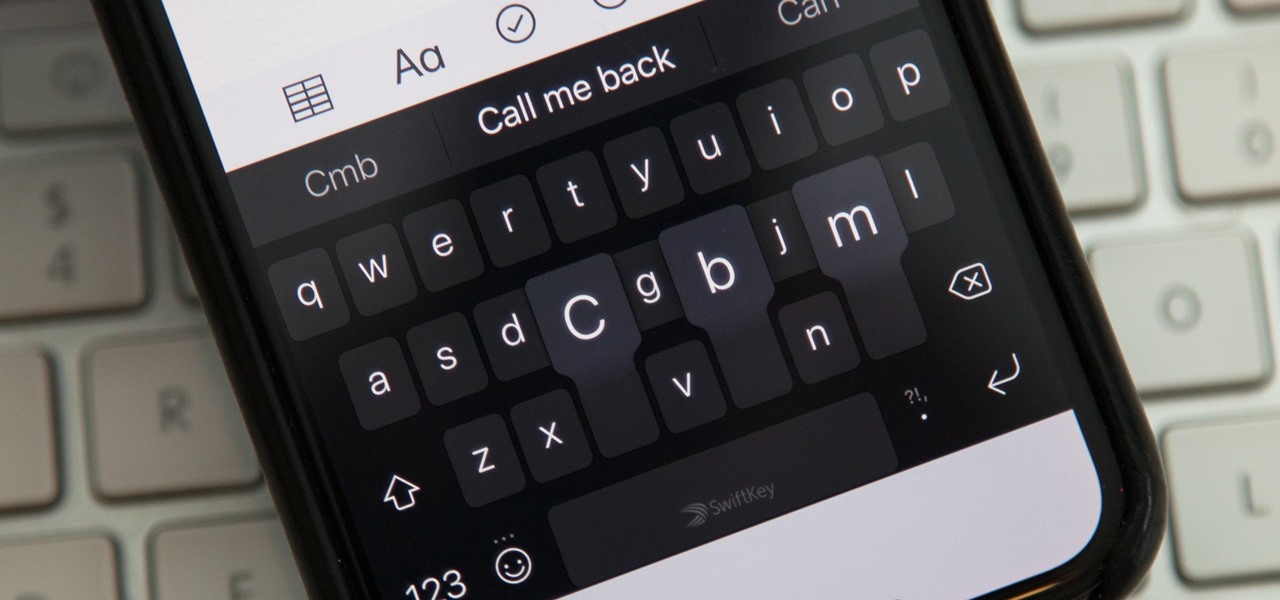
While you're probably already used to the keyboard on your iPhone, you'll likely never be able to type on it as fast as you can on a computer keyboard. But that doesn't mean you can't get any faster at typing on your iPhone. By using keyboard shortcuts to auto-populate commonly used phrases, email addresses, and other big-character items, you can drastically speed up your virtual keyboard skills.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

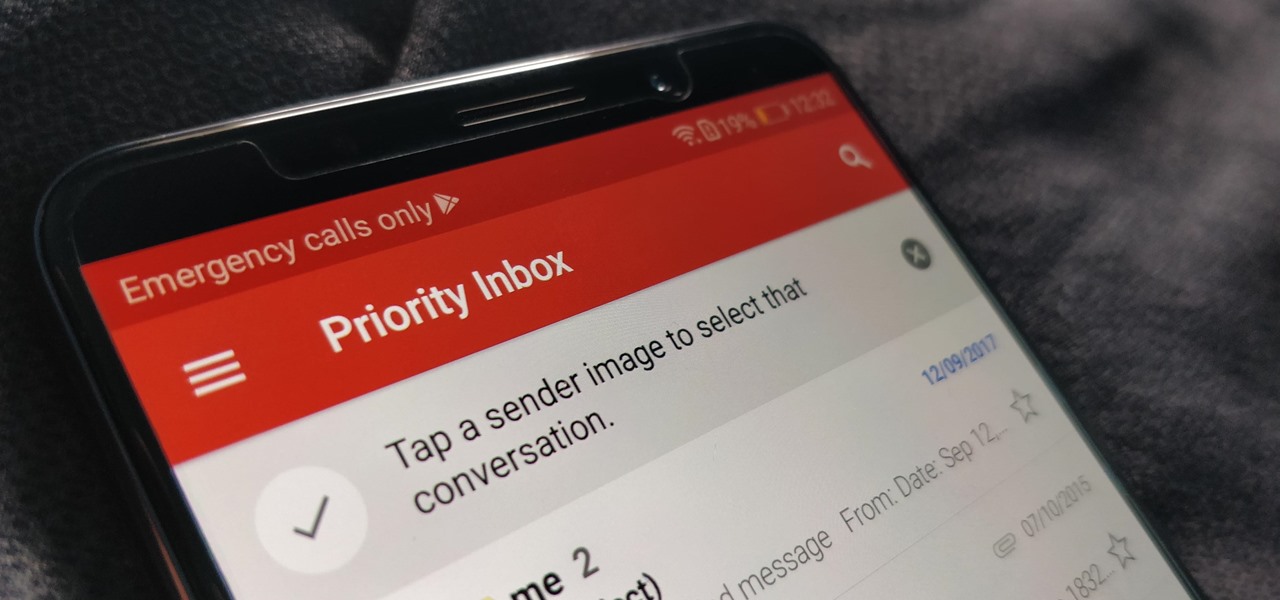
On average, an office worker receives 121 emails a day. Many of these emails are trivial and don't require immediate attention. While Gmail's automatic spam filters catch plenty of irrelevant emails, some still make their way into your inbox. Fortunately, Gmail's tools aren't limited to just spam filters.

Most of us have probably used a GIF at least once or twice to respond to a message, and that's why a lot of messaging services and keyboards have GIF search tools readily available to use. Now, Google wants to take GIF responses to a more personal level, by allowing you to create your own selfies GIFs to instantly sent to family and friends.

In its goal to push the visual quality of real-time rendering to a new level, Unity is starting the new year off right by releasing a sneak peek at its upcoming interactive rendering improvements via a short, three-minute first-person interactive demo called "Book of the Dead."

Google's launchers are some of the most polished home screen apps out there, but they lack the ability to customize. With the old Google Now Launcher, we had Xposed GEL Settings to add options for tweaking the layout, but that project was abandoned when the Pixel Launcher came out. Now, a new root mod will give us some key customization settings for Google's latest launcher.

Coming into this year's Consumer Electronics Show (CES), the common sentiment among observers was that this was expected to be the big year for augmented reality.

The greatest pain in owning a high-powered gaming PC is the simple fact that you can't play it all the time. Sometimes you have work or school, and other times, you may just want to go mobile. When something like this impedes your ability to play PC games, you may end up settling for mobile games. What if, instead of doing that, you were able to play your PC games from your iPhone?

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Unscheduled pit stops go hand in hand with road trips, no matter how well-planned they are. In the past, making a stop due to low fuel or an emergency bathroom break may have snowballed into massive delays when you went off course on your own, but thanks to a feature in Apple Maps, you can do this in the most efficient manner possible.

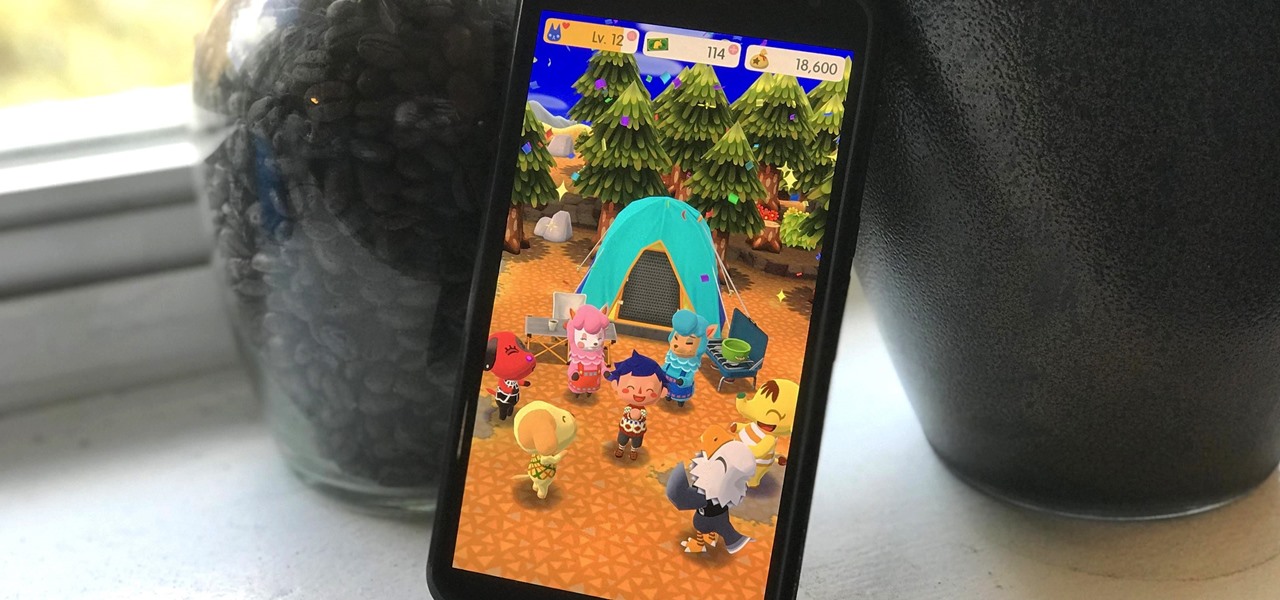
For a friendly mobile game, Animal Crossing: Pocket Camp has an overwhelming number of items and collectibles — from fruit to fish to friends. Even though it can be difficult to keep up, this guide will be a great stepping stone to creating the campsite of your dreams without spending a dime.

It looks like the dust is finally starting to settle on Google's POLED PR nightmare. The Pixel 2 XL — one of the most hotly-anticipated phones of the year — has been plagued by screen issues and worries. While it is certainly not without its faults, Google has created several software fixes and is offering a 2-year warranty for screen burn-in, so we can rest a bit easier about purchasing Google's latest Pixel.

Google Trends says that "unicorn" costumes are among the Top 5 searches for 2017, holding steady onto the no. 4 spot, trailing only Wonder Woman, Harley Quinn, and clowns. Seeing as how this year, unicorns made the full leap back into our lives, its popularity when it comes to Halloween costumes is not surprising.

More than a year after Harley Quinn made her splash in the summer of 2016, her popularity has not waned one bit. According to Google Trends, the Harley Quinn costume remains ever popular, trailing only Wonder Woman in searches. These two DC Comics characters provide a powerful one-two punch, a mix of superhero and supervillain.

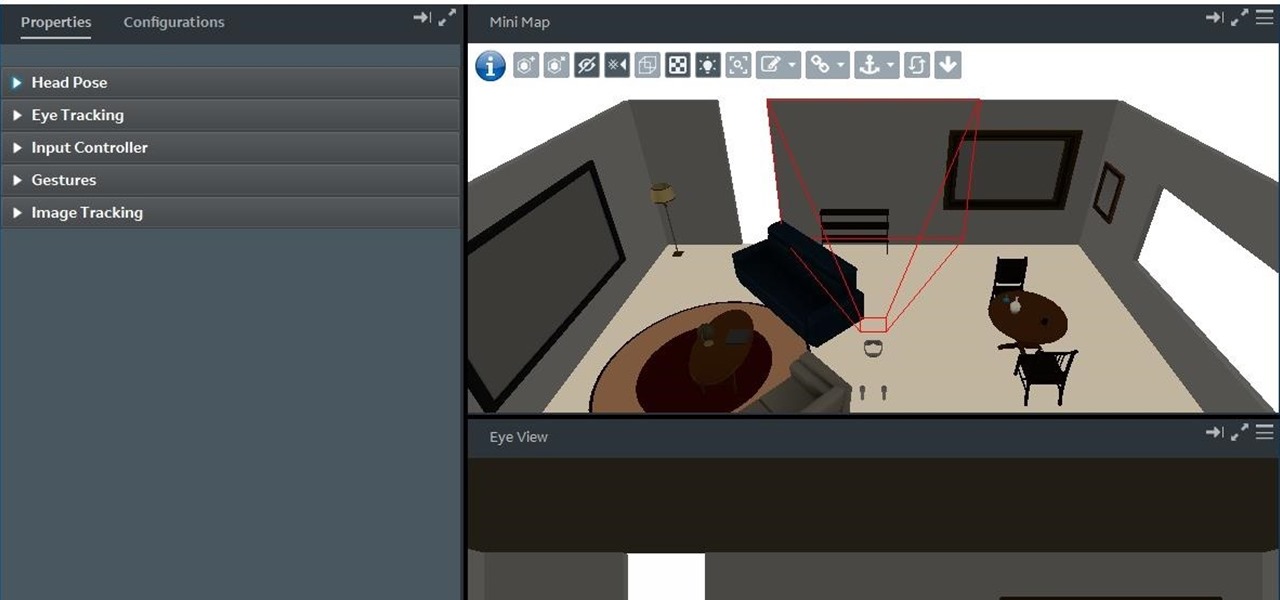
In this chapter, we want to start seeing some real progress in our dynamic user interface. To do that, we will have our newly crafted toolset from the previous chapter appear where we are looking when we are looking at an object. To accomplish this we will be using a very useful part of the C# language: delegates and events.

Not to be outdone by Apple and it's new line of flagship phones, Google has followed suit and finally announced the followup to their highly regarded Pixel line of handsets — the aptly named Pixel 2. Thankfully, the tech giant has also joined in on the trend towards more durable devices, and has engineered both the Pixel 2 and Pixel 2 XL to have a rating of IP67 under the IEC standard 60529.