Does your car idle high and make an obnoxious racket every time you are stopped at a light, drawing dispproving looks from your fellow motorists? If you are into home car maintenance, you may be able to diagnose the cause of this problem yourself. This video illustrates how to test for one common problem that leads to a high idle, a faulty throttle position sensor, the contacts on which have been worn down by the throttle. You will need an analog multimeter to test the ohm load from the senso...

The great thing about having long hair, is the ability to do almost anything to it. You can flatten it, cut it short, place it in a ponytail and of course curl it. There are so many ways to curl hair, but one of the most easiest and common ways is by using a curling iron and some basic hair products such as hair spray, a comb, and of course, patience. Sit back and find out how to curl short hair easily in this tutorial. Enjoy!
In this tutorial video, hosted by harrymedan, you will learn how to fix a broken or nonfunctional select button on your iPod, as well as the common causes of the select button no longer working. According to the host this problem is usually caused by the battery in the iPod itself. He suggests opening up the back of the iPod and replacing the old battery, which is usually swollen from being charged so many times, and puts pressure on the select button causing it to become inoperable. If you a...

When you are tested for drugs, the drugs can be found in your hair and blood. There are three types of tests: hair test, blood test and urine test. The urine test, being the cheapest, is the most common drug test. Some ways to beat this unwanted drug screening is by drinking x-amount of water, this dilutes the drug within your system. The second method is to inform them that you are a user, or that you attend frequent rock concerts. (This method isn't recommended because of the outrageous amo...

Use a motor to make a fan and a speaker. People often take for granted the common items and devices they use in everyday life. Looks can be deceiving. It's not what things appear to be, it's what they can become.

It's time for some golf! What's an 18-year-old know about distance? Justin James can belt it 400 yards and more, and with his power tip, you too can tack on a few extra yards. Well, maybe not 400 yards, but you get the idea. See how to get more power out of your golf drive.

This truck repair video shows you how to remove the bed from a Chevrolet C1500 W/T truck. This needs to be done to fix certain problems, in this case the fuel lines. Whatever reason you need to remove the bed from your Chevy, this video shows you how to do it properly.

PEX, or cross-linked polyethylene, is a common alternative to copper piping. If you're looking to save time on your project (or have an aversion to soldering), PEX might be for you. In this tutorial, you'll learn what PEX is and how to decide what type of PEX is best for your application.

Learn what common time or 4/4 time is and how you can use it with this how to video. This music theory tutorial will help you understand the concept of time signatures and counting rhythm.

Dr. Ari Goldsmith discusses the diagnosis of swimmers ear and a few common treatments.

A Look into Internet Marketing including common pitfalls to avoid and how to build a userbase. Part 1 of 2 - How to Get into Internet Marketing.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Smartphones have put an end to camcorders. If you want to capture memorable moments in high quality, look no further than that technological marvel in your pocket. Recent Galaxy phones are shining examples of how far we've come — but the more capable a camera gets, the more complicated things can be.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

You may not have heard of visceral leishmaniasis, onchocerciasis, or lymphatic filariasis, and there is a reason for that. These diseases, part of a group of infections called neglected tropical diseases (NTDs), impact more than a billion people on the planet in countries other than ours. Despite the consolation that these often grotesque illnesses are "out of sight, out of mind," some of these infections are quietly taking their toll in some southern communities of the US.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

There's a common saying that separates cooks from bakers: baking is a science, while cooking is an art. When baking, one little misstep can alter the texture, taste, and consistency of any recipe.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

To say we're a nation of coffee-lovers is putting it mildly. Americans consume 400 million cups of joe in one day alone, but how well do we actually know our morning BFF? We know it comes from a bean, and that more coffee drinks exist than there are ways to skin a pig, but what else?

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

With warm weather comes bugs, and with bugs come bites, and with bites come itches. From ticks and spiders to mosquitoes and bees, insect bites come in sundry shapes and sizes, but they all commonly pull an itchy, red reaction out of our bodies.

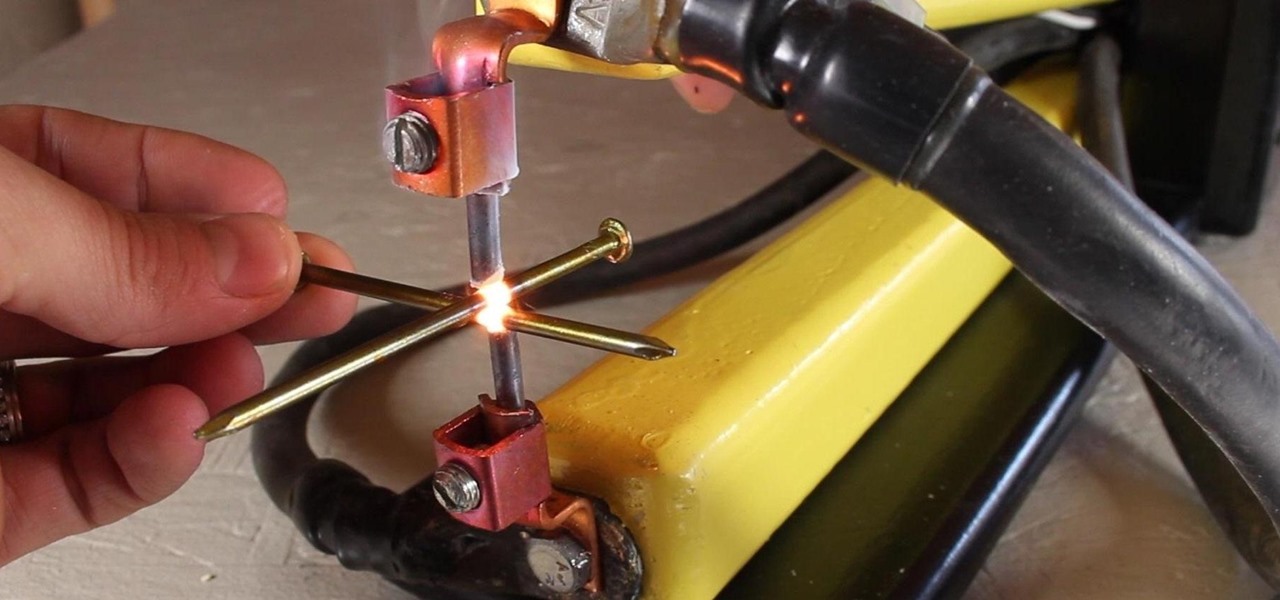
A typical resistance spot welder can range in price from about $200-$800, but with a little resourcefulness and a bit of free time, you can make one like this for about $10 or less.

In this tutorial, we learn how to do finger tutting. There are different positions in tutting to help you get to a new one, creating new paths while learning. First, place both your arms on top of each other, then move them adjacent to each other by raising them and popping them. The praying position is also very popular. When you are tutting, think about common positions that are used a lot, then think of how you can get to the tutting by doing different switches and use your fingers more ef...

This video is a simple math video showing how to add and subtract fractions using different denominators. It begins with a man explaining briefly and sitting in front of a piece of paper. He writes out a group of fractions each one with different denominators, ending in three and five. To add appropriately, on must find a common denominator, which is fifteen. So he multiplies each by five and three, raising the denominators to fifteen. This will raise the fractions to six-fifteenths and twent...

Ever want to have a friendship bracelet with your own personal saying on? Well, it's going to take a lot of experience to get there. Start off with learning the basics of friendship bracelet making, such as the basic knots and skills. When you think you are ready for a challenge, try to write your name in a bracelet. This video is ideal for learning the letter "i". "I" is a very common letter to be in first names and it is probably found in yours too! After learning how to make the "i" try to...

Ever hear of 14.1? Well, you may know this as straight pool, the pocket billiards game. This was the common sport of championship in the old days, and was immortalized in the film The Hustler. But playing a good game of 14.1 continuous means starting off good, which means a well-prepared rack.

Watch to learn how to replace the HEPA filter on a Dyson DC07 vacuum. This Dyson spare parts video we show how to remove and replace the Dyson DC07 Pre Motor Filter and Dyson DC07 HEPA Post Motor Filter. This vacuum maintenance video also outlines the Dyson airflow path as well as removal and replacement of the Pre Filter Housing, Post Filter Lid and Filter Seals. Prevent loss of suction and motor cut out by changing the filters on your Dyson.

Watch to learn how to replace the blade on a Flymo Hover Compact 330 mower. You'll remove and replace the 33cm Flymo blade on a Flymo Hover Compact 330. If your mower is not cutting properly remember you need a sharp blade for the perfect lawn. We use spacers to adjust the Flymo cutting height. This lawnmower maintenance video includes cleaning and we use a scraper tool to do this.

Watch to learn how to remove and repair a Neff oven door. You'll remove and replace parts on an oven door, as well as how to remove the oven door. This oven maintenance video demonstrates removal and replacement of the oven door outer glass, oven door inner glass, door hinges and door handle. Use a professional oven cleaner and ceramic scraper to remove burnt on stains from the oven inner door glass.

Watch to learn how to replace the fan oven element in a Neff oven. You'll remove and replace the fan oven element in a Neff oven. Oven fan working but no heat? You could have a faulty fan oven element. This straightforward oven repair video also shows how to remove the oven door.

Watch to learn how to replace the door seal on a Neff refrigerator. You'll remove and replace the fridge door seal on a Neff fridge. Replacing the fridge seal is an energy saving tip: If there is a fridge door seal gap, you will not create the correct fridge temperature to store food. To increase fridge efficiency fit a new seal. As part of this fridge maintenance video we also replace the fridge door bottle shelf and use a professional fridge cleaner.

Watch to learn how to replace the wave guide cover in a Neff microwave. You'll remove and replace the waveguide cover on a Neff microwave. Microwave sparks, or arcing in the microwave, could be the result of a damaged waveguide cover. As part of this microwave maintenance video we explain that you can replace a broken glass turntable or a melted roller ring. There are also microwave cleaning tips included.