Watch to learn how to replace basket wheels in an Electrolux dishwasher. You'll remove and replace upper basket wheels and lower basket wheels on an Electrolux dishwasher. Broken dishwasher basket? Perhaps you have a missing basket wheel. As part of dishwasher maintenance we replace the wheels and explain that you can also get a replacement cutlery basket.

Watch to learn how to replace spray arms in an Electrolux dishwasher. You'll remove and replace spray arms on an Electrolux dishwasher. Dishwasher not working properly? You may have a broken upper spray arm or blocked lower spray arm. As part of dishwasher maintenance we also explain that you can replace a broken drainage channel or fit a replacement cutlery basket.

Watch to learn how to replace a knob on a Neff gas hob. You'll remove and replace a gas hob knob on a Neff gas hob. Replacement knobs as well as burner caps and flame spreaders are easy hob spares to replace. As part of hob maintenance we also use a specialist hob cleaner to get a nice clean hob. This hob maintenance video clip illustrates the many different hob parts

Watch to learn how to replace an AEG fridge freezer door seal. You'll remove and replace the freezer door seal on an AEG fridge freezer. You will have a more efficient freezer and prevent energy loss if you replace a worn freezer door seal. One of many simple freezer maintenance tips that will help ensure you have the correct freezer temperature.

Watch to learn how to replace the HEPA filter on a Dyson DC04 upright cleaner. You'll remove and replace the Pre Motor Filter and the Post Motor HEPA Filter on a Dyson DC04 vacuum cleaner. It is important to change the filter regularly as part of regular vacuum maintenance and to prevent loss of suction.

Watch to learn how to replace the HEPA filter on a Vax VEC04 vacuum cleaner. See how to remove and replace the central HEPA filter and the post motor anti-bacterial filter on a Vax VEC04 vacuum cleaner. It is important to change the filter as part of regular vacuum maintenance and to prevent loss of suction.

Alopecia is also known as hair loss. he most common form of alopecia or hair loss that we see is alopecia areata. It usually shows itself as round patches of hair loss on the scalp, however, it can affect the facial hair and body hair. Learn some tips on how to slow and treat the loss of hair in this medical how-to video.

This how to video is designed for people who wanted to start glowstringing but has never done it before. The tutorial starts by answering some of the most common questions such as how to tie the strings and how to hold them, then moving on to teach the Weave, Windmill, and Butterfly. All you need is a pair of shoelaces and a pair of 6 inch glowsticks (either used or unused) then you can start here. Some people like their shoelaces round and thin, some like theirs flat and thick. It doesn't ma...

In these videos, you can see how 3 minute chess blitz games are for the greats, because if you're a beginner, you spend too much time analyzing the moves, when they should come almost as second nature. See some common follies in rushed games, and see some good defenses, here and there.

Spanish is the biggest and most used language, right next to English. It's even one of the six official languages of the United Nations. Make sure you're up to date and bypass the language barrier. Learn to speak Spanish phonetically. With these 35 videos from WatchMojo, you'll be speaking Spanish in no time. Translate English words into Spanish!

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

Dave shows you how to diagnose common plant diseases, specifically the Rhododendron.

Wireless headphones are convenient, comfortable, and more common than ever before. With the massive proliferation of wireless earbuds, it's hard to identify which ones are good and which ones just want to look like they're worth the price. Avanca T1 Bluetooth Wireless Earbuds are high-quality wireless earbuds with excellent functionality and a low price of $29.95 now that they're 50% off.

We're all feeling the impact of the economic recession underway due to the coronavirus. With millions of Americans filing for unemployment benefits, now more than ever should we focus on the best deal rather than the best model. And in no industry is that more evident than smartphones.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

As a native of Alabama, Apple CEO Tim Cook has a special place in his heart for the state. He also empathizes with the struggles that African-Americans have historically faced in the state, particularly during the 1950s and '60s civil rights era.

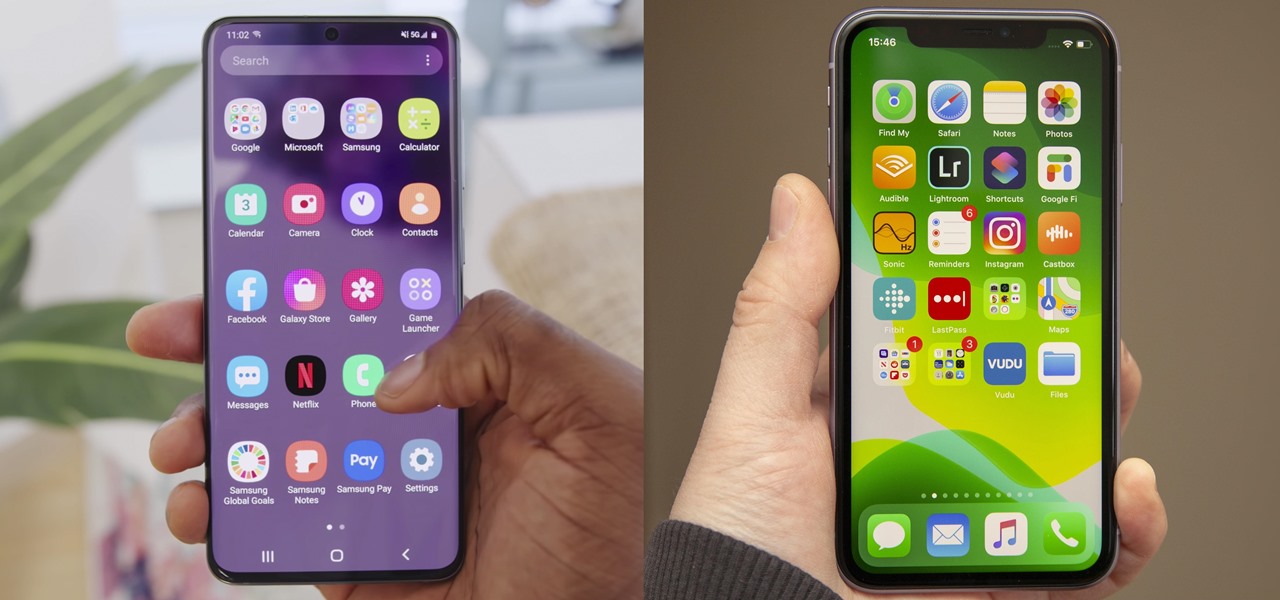
Apple has their regular iPhone 11, then two higher-end "Pro" models. Samsung went the other way — they have the Galaxy S20 and S20+, then there's the S20 Ultra. But one thing these smartphone lines do have in common is the base model flagship. How do they compare?

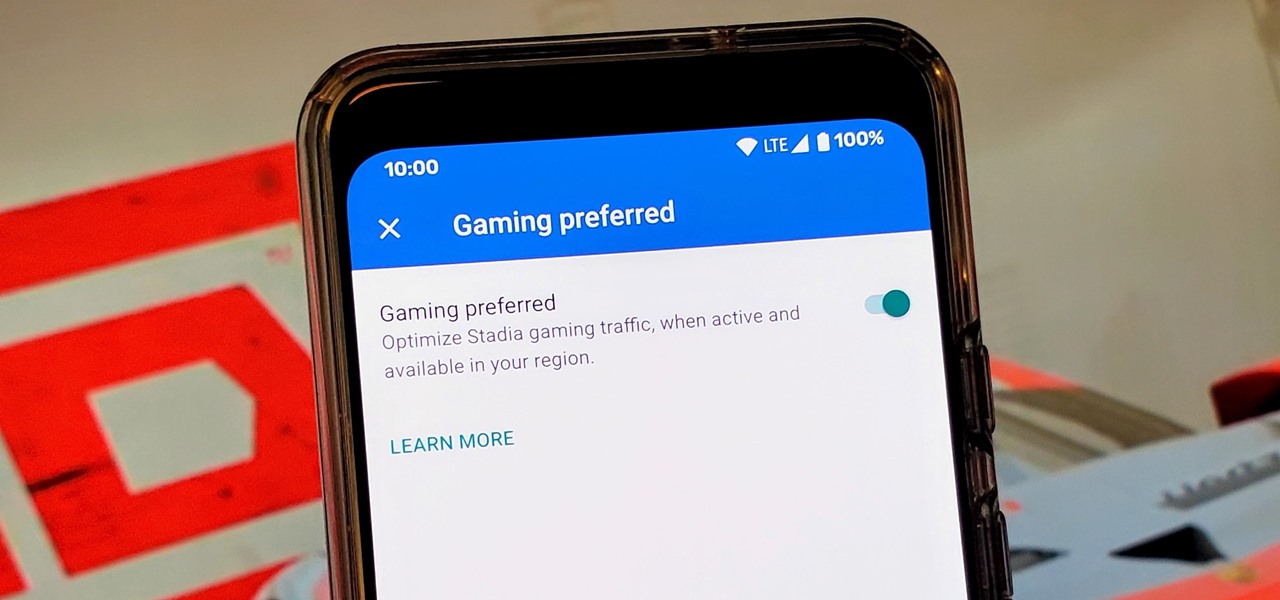
Although not quite as common today with the always-connected world we live in, you still might be having bandwidth wars in your home right now. If the internet connection in your area is mediocre, you know the feeling well. Google Stadia recommends having a 25 Mbps connection for playing in 4K, so you can expect to need at least that much to maintain a smooth, high-quality gaming session.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

Let's be honest, nobody enjoys doing cardio — they tolerate it. That dreadful, loathsome feeling you experience when you're doing cardio workouts isn't unique to you, it's almost universal. Sure, it gets easier the more you do it, but there are some ways to make it better now.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

After opening up its Spark AR platform on Instagram for all creators, Facebook is already expanding the platform's capabilities on its Snapchat killer.

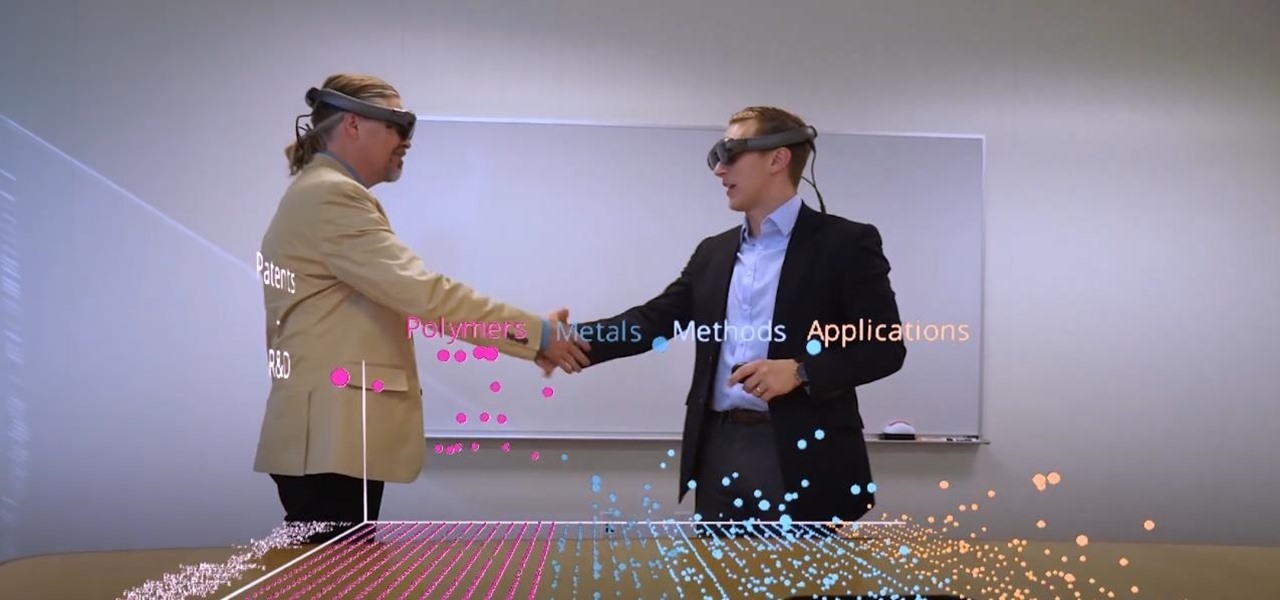
Thanks to the expanding universe of augmented reality tools being made available, increasingly, anybody can liven up sleepy office meetings with immersive computing.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

All those Apple commercials encouraging people to use their iPhones to make their smartphone movies look amazing, but how can you achieve some of the same looks? That's the question many often ask after plunking down over $1,000 for a brand new iPhone, shooting some video, and getting somewhat mediocre results.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Samsung's not one to make drastic changes to what already works. They've continued on with the IP68 rating under IEC 60529 first given to the Galaxy S8 all the way to the the Galaxy Note 10. If you're a little confused as to what this rating means, don't worry, it's actually pretty simple once you get to the meat and bones of it.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Learning Chinese is hard, but it can be a lot easier with the help of a few great apps. As a native English speaker who's currently living in China, this is a process I've recently gone through. After playing the field, here are the three apps I personally think will help you the most with your Chinese learning adventure.

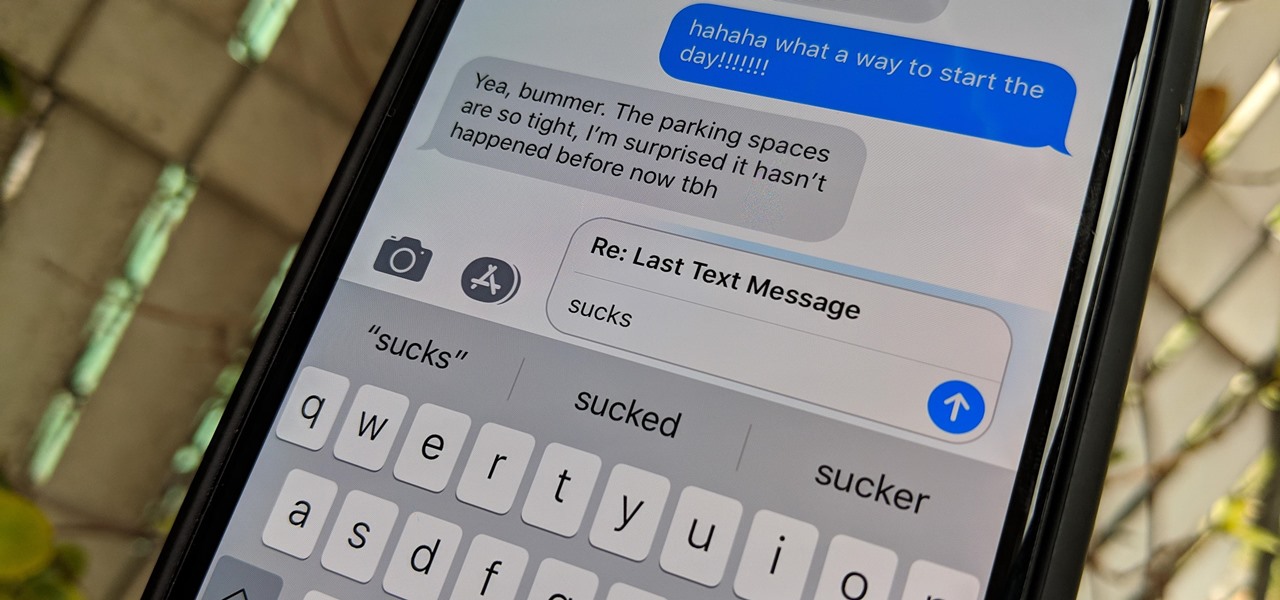
The subject line is a crucial part of an email, but you don't see it very often in texts. That's mostly because many people don't even know it can be done, and even if they do, why would they use it? Just like with emails, subject lines can make iMessages and SMS texts seem more important and more professional. Plus, they can help with organization and searching past messages, as well as make text bold.

Two years ago, Facebook founder and CEO Mark Zuckerberg kicked off the F8 Developers Conference keynote with augmented reality and the introduction of Facebook's AR camera platform, now known as Spark AR.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

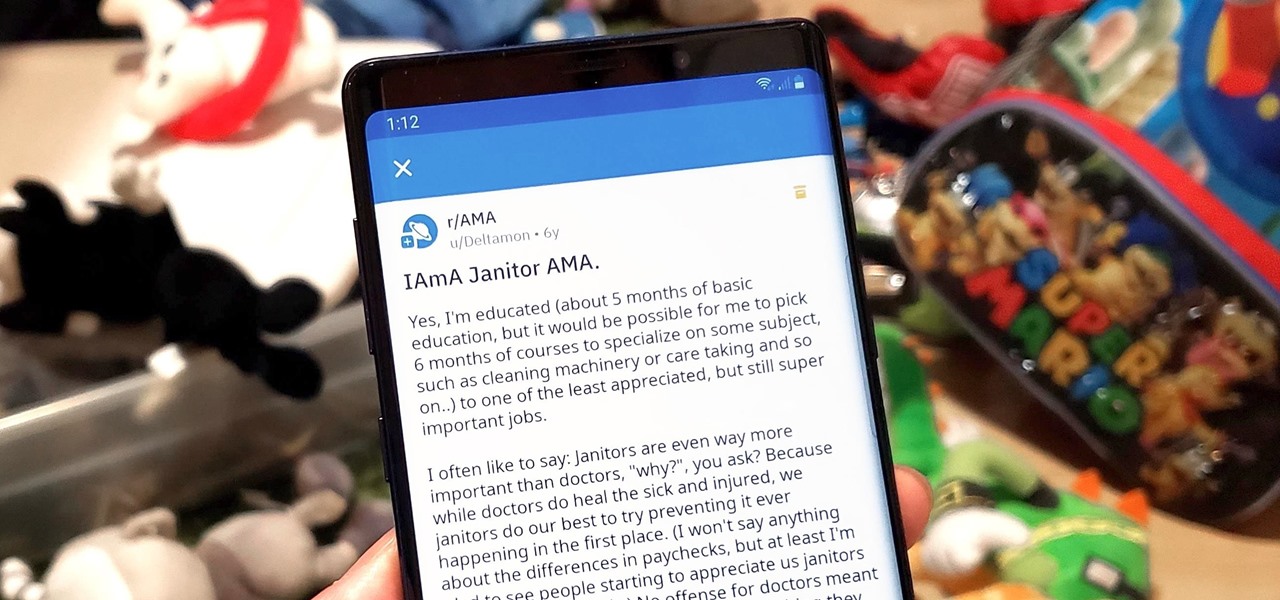
Short for Ask Me Anything, AMA threads are one of Reddit's signature features. They enable you to directly interact with a whole range of interesting personalities, from common folk with amazing life experiences to influential celebrities that help shape politics and culture.

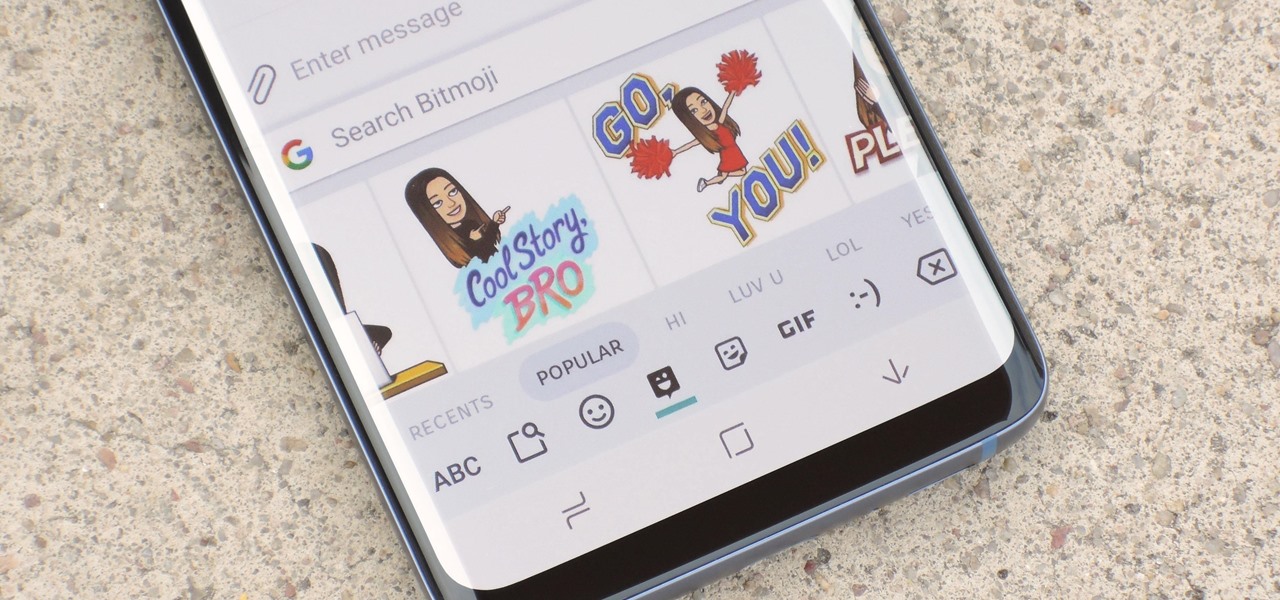
Bitmoji are personalized emoji that look like you and can be used to make funny memes or snappy replies. Normally, you have to find one of these reaction emojis in the Bitmoji app, then use Android's share menu to send it to the app where you ultimately want to post it, but there's a much better way.

The release of Avatar Chat for Magic Leap One and Spatial for HoloLens during the fourth quarter of 2018 appeared to revolutionize video calling via augmented reality.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

This year's holiday shopping season is shaping up to be fertile ground for augmented reality to show its worth, as both Walmart and Target have crafted immersive experiences designed to engage shoppers in the coming weeks.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.