
Hack Like a Pro: Linux Basics for the Aspiring Hacker, Part 11 (Apache Web Servers)
Welcome back, my aspiring hackers!


Welcome back, my aspiring hackers!

Particles, such as electrons, have a property called spin which can be measured at any angle, but when measured always results in one of two answers—up or down.

One of the best things about the Samsung Galaxy S3 is the ability to modify the device in countless ways, as with any other Android device.

Many people that I know who have gone to see the Hobbit have come back unimpressed or annoyed with the film. I LOVED it. When those non-specific people, cough Loziers cough, gave me their reasons for not liking the movie, I was very annoyed... I considered the demands that they were placing on Peter Jackson and his team to be very high and unreasonable. So, as a method of venting my anger, here is how to watch the Hobbit. If you’ve read Lord of the Rings and the Hobbit, please, go back, and R...

There is nothing more irritating than having a nice jam session interrupted by an ad selling B vitamins, and that's exactly what Spotify does to you if you don't pay up.

Tripwires are a new mechanic released in Minecraft 1.3, and people are still trying to figure out how best to use them. Minecart returns are a great idea, but what about traps?

Every once in a while, Minecrafters want to create a simple hidden piston door to secretly hide all their valuable items. Now, it's possible with only 18 redstone, 2 repeaters, 12 sticky pistons, and ONLY 20 blocks of any kind!

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

Bokeh (which translates to "blur" in Japanese) is a photography technique referring to the blurred areas of a photograph. Basic bokeh photographs often have one point of focus, while the background falls away into a dreamy, blurred haze.
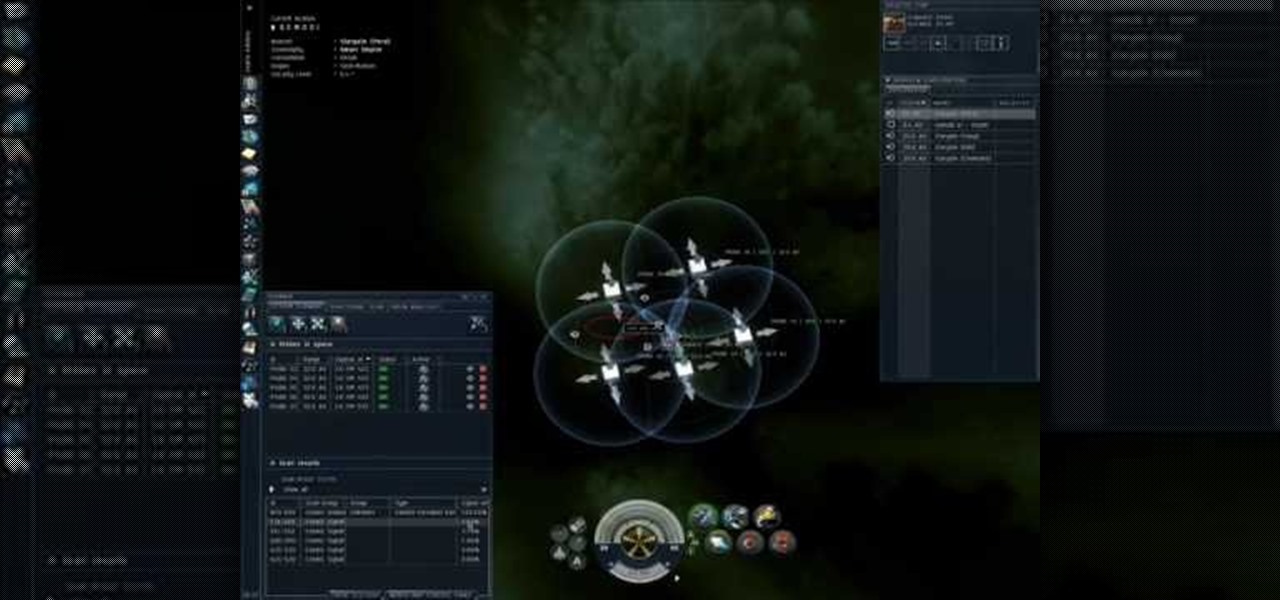
Avoid an ambush and detect what's available in a given star system! You'll need to learn how to use probes to scan the surrounding area if you want to do a lot of exploring in EVE Online. This video shows you how to set up your probes and execute the scanning function.

As an adult you will come a cross a point in time when you need to make the right impression by writing a formal letter. Follow the format and you will be able to be most effective at conveying the information in your letter.

Kung Fu refers to Chinese martial arts in all its varieties, get expert tips and advice on wushu and self defense in this free video.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.
While installing the new Android 9.0 Developer Preview is fairly easy if you're using a Windows machine, it's a little trickier if you want to use macOS instead. To help you get the latest Android OS on your Google Pixel phone, we'll break down the whole process so using your Mac can be as simple as Windows.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.
For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to differentiate camera hardware.

The international, Exynos-powered Galaxy S7 and S7 edge have had a working root method ever since a few days after release. But the North American variants—those using Qualcomm's Snapdragon 820 processor—have locked bootloaders, and have proven to be almost unrootable up until now.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

It's universally known that broccoli, kale, Brussels sprouts, cauliflower, and all cruciferous vegetables (also known as brassicas) are good for you—but you probably don't know exactly how good they really are.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

If you've been to a convention of any sort before, you know that there are good and bad panels, and that their inherent goodness or badness often has little to do with the actual content being discussed. That's because giving a panel is a skill that not everyone has. However, it is a skill that everyone could have! In this article, I'll tell you how to give a good panel on practically any subject. Image by Shannon Cottrell

Just like any meal choice you can make more or less healthy options when eating sushi. Some ingredients are particularly calorie packed. If you’re watching your weight know where the hidden calories are and if your really conscientious you can try sashimi.

With summer just around the corner make sure you are prepped and ready for all those barbeques by connecting the propane gas tank to your grill. With the hose on tight you’ll be ready for those hotdogs and hamburgers.

You can help keep your laptop cool by fixing a malfunctioning laptop fan. With a screwdriver and some compressed air you can clear away any obstructions. Think about where you are setting down your laptop as soft surfaces can block air intake.

Setting up a guitar refers to the adjustment of the intonation and action of a particular guitar. Learn to properly setup an acoustic guitar with tips from an expert in this free video series.

A miter saw used to refer either to a large unpowered backsaw or metal frame saw with replaceable blades suspended on rollers in a metal guide that allowed making accurate crosscuts and miter cuts. These types of miter saws are still sold, the Nobex brand being notable. Today, they are generally used in picture framing but have largely been displaced by the power tool in carpentry and joinery operations.
Learning to code is difficult, but the potential of a little expertise in a few programming languages grants you is worth the effort. Learning to code won't just put you on one career path; many fields, from game design to data science, use coding languages. The All-in-One Coding Skills Bundle can be your start toward mastery of some of the most useful coding languages around for $29.99.

Google, you have something that I want. You may think you have some idea of what you are in possession of, but you do not. In a few moments, it will be mine...and it can be yours, too, dear readers.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

You need a break from gloomy coronavirus updates. We all do. The unrelenting stream of doom and negative news is both helpful in terms of keeping ourselves and our families safe, but it also has the unfortunate effect of increasing our anxiety. When will this end? How bad will it get? Is there reason to be hopeful?

Whether you call it the foot shake or foot dance, videos of people tapping their feet together have been and still are blowing up all over TikTok. If you want to get in on the action but can't follow along with all of the fast-paced TikToks, we'll slow it down a bit for you and a friend.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.