hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

Whether you call them chickpeas, garbanzo beans, or Egyptian peas, these little morsels are one of my favorite snacks—when properly seasoned, that is. Being mild in flavor on their own, they're incredibly versatile and fun to experiment with. (They're also incredibly healthy.)

Few things in life are as exciting and magical as fire. And setting things on fire while cooking? Well, now you're speaking my language. I'm not talking about grilling, though I do love some outdoor cooking. No, I'm talking about the most badass trick in any cook's arsenal: the flambé.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

Hello there, 'Flashers'! Welcome to my 8th Post. This tutorial will explain how to flash Kali NetHunter on OnePlus (Tested) and Nexus Devices (Not Tested-Should work) as a secondary ROM, so that none of your personnel data/ROM gets affected.

On Thursday morning, May 28th, Google announced an upcoming version of Android—and within a few hours, a preview build of this so-called "Android M" release was made available to select Nexus devices.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

It's an unspoken rule that diseases are not things that you want to purposely consume. So if anyone ever offers to cook you something made out of a disease, just kindly say no... unless it's huitlacoche.

There are tons of greasy drippings that can be used to flavor up any dish, but none will ever be more delicious than animal fat. The bigger and fatter the animal, the juicier and tastier their fat is. For those of you who have had your fill of bacon-anything, here's your next obsession. It's called caul and its very existence will divide those that are serious about their animal fat flavoring from the pretenders.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

If you're a sushi lover but not an expert sushi maker, you can still enjoy the flavors of sushi rolls at home with these deconstructed sushi dishes.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Somehow, we end up with a pile of leftover candy canes at the end of every December. Yet just because the enthusiastic holiday commercials are gone and the Christmas cards are on discount doesn't mean you have to let the minty sweets go to waste.

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

There's nothing worse than biting excitedly into your indulgent restaurant-style burger only to find a soggy mess of a bun on your plate. The conundrum of keeping a patty moist but bun dry has perplexed home cooks and chefs alike, and even top burger joints are guilty of soggy-bun syndrome.

We all carry a bit of anxiety around with us. Is our boss still annoyed because we could barely stay awake in yesterday's pre-dawn meeting? Will our friend hate us forever because we forgot to call them back two weeks ago? Whatever worries pop up in your mind, whether they're monumental or insignificant, it can be hard to quiet those nagging voices, but you can shut down your nonstop mind with a bit of relaxation, distraction, and action.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

If you're anything like me, you started down the Android-modding path for two distinct reasons; to run cutting-edge software and squeeze every bit of performance out of your hardware. Utilizing the new F2FS file system on your rooted Nexus 4 or 5 fulfills both of those desires at the same time.

Butter can be even more delicious than it already is. While that may be a shocking claim, it's most definitely true. Many new cooks and even seasoned chefs don't realize this, but the few minutes it takes to do these things will pay you back exponentially when it comes to that buttery taste.

Transition animations are an essential element of any mobile operating system. They give the user a sense of what's happening on the screen, where the apps are coming from, and where they're going.

Many people drink green tea for health reasons, and it's no wonder. This beverage is a superstar when it comes to antioxidant levels, and is being studied for its potentially curative properties on multiple health concerns, whether it's staving off the aging process or fighting cancer.

White or light-colored dinnerware is a classic: it looks crisp, clean, and elegant. The only problem is that after you've used it for a few years, the surfaces bear a lot of grey scuff marks from forks, spoons, and knives being dragged across the surface.

When the Nexus 5 debuted, one of its coolest features was the fact that you could say "OK Google" any time you were on the home screen to launch a Google Voice Search. This feature was ultimately made available for other devices by way of the Google Now Launcher.

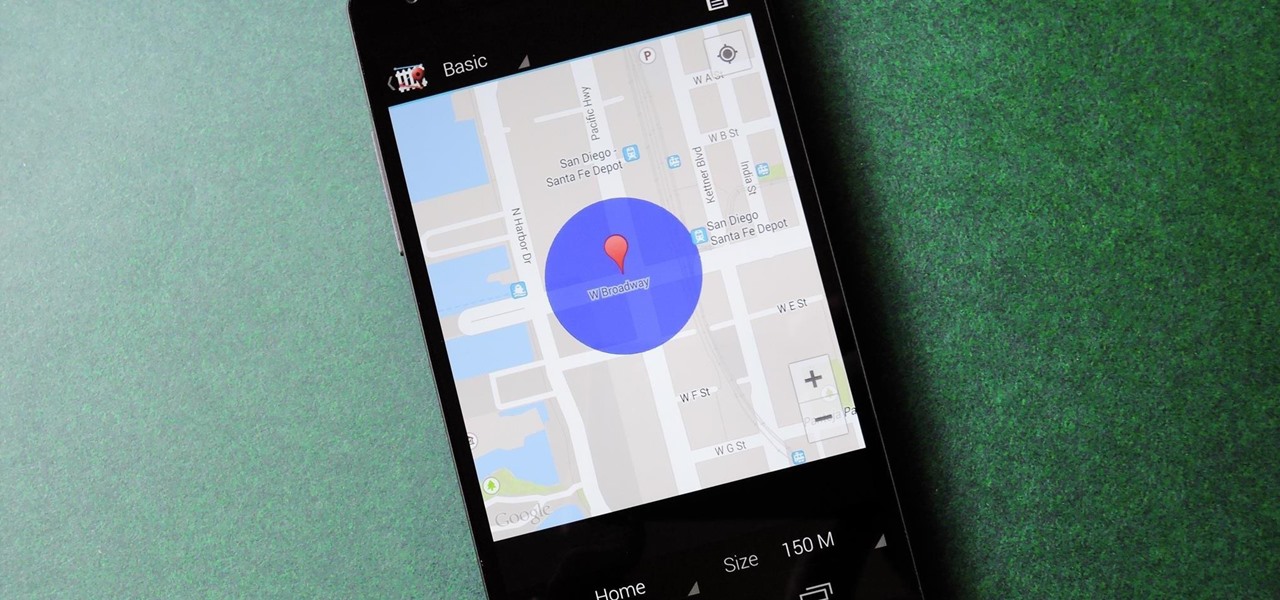
We live, work, and play in drastically different environments, so it only makes sense that we'd want our Nexus 5 smartphones to automatically adapt to our needs when in certain locales at certain times.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

If you have a good food processor or blender, there's no reason not to make your own nut butters, whether you like almond, cashew, sunflower, or the perennial classic, peanut.

Flashing ROMs can be a tricky process, and sometimes you can end up leaving yourself without a ROM at all, often referred to as a soft brick. If you accidentally wiped your internal memory before a flash or forgot to download the ROM before wiping your system partition, don't worry, there is always a way to get your phone back up and running.

If you've never played Cards Against Humanity, it's time to get initiated. Originally funded through Kickstarter, the free to download card game is basically an obscene version of Apples to Apples.

What would you say if I told you it was entirely possible—even desirable—to cook anything from a simple dinner to a great loaf of bread without using measuring cups, spoons, or a scale?

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

Recently, there have been some questions regarding networking popping up and we have decided to put together this series to try and cover this gap.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

The holiday season is almost over, bringing the year to an end, and what better way to end it than with some tonsil hockey from the dime across the room on New Year's Eve?

With all of the new features and third-party apps out there making Android better and faster every day, it's quite frustrating to me that keyboard advancements remain relatively static.

No matter what device you have, Android lag will get you down. It's our little green robot's only major downside, and you've probably noticed it quite a bit on your Nexus 7 tablet. Apps open slowly, actions stutter or pause, and loading files takes forever.