
How To: Create the Smartest Design for a Spiral Staircase (Drop Down in Center)
Did you ever want to have a Free-Fall drop with water at the end inside of a Spiral Staircase? Well, you got it! With a Smart Design. =)


Did you ever want to have a Free-Fall drop with water at the end inside of a Spiral Staircase? Well, you got it! With a Smart Design. =)

Anna The Red is the greatest Bento artist I have come across on the web. She's so highly regarded she even did an ad for Google. Check it out: For those of you who don't know, Bento is a "single-portion takeout or home-packed meal common in Japanese cuisine". When bento is arranged in an elaborate style (such as people, animals, characters, plants, etc.) it is referred to as kyaraben or charaben (a shortened version of character bento).

When President Obama mimics your move, it's gold. Beyoncé's iconic Single Ladies dance has made history in a bevy of ways. For months, it has hovered atop the Billboard charts.

tell if she is a hooker or a cop. His arrogance too great. Above the law. Not even this tutorial would have slowed him.
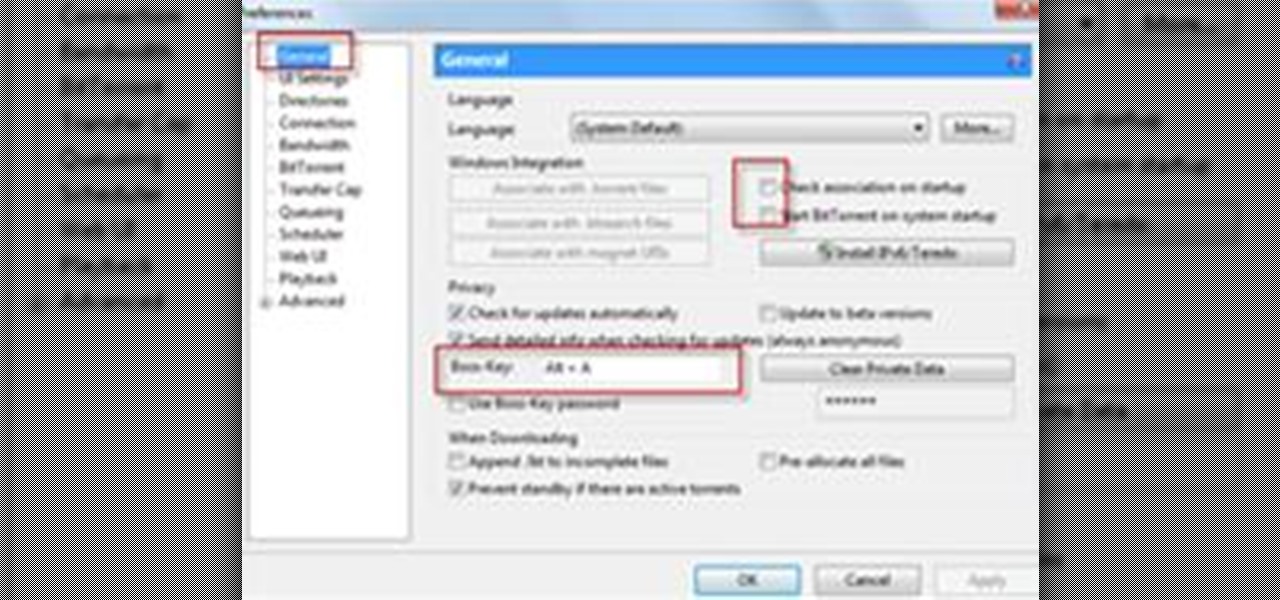
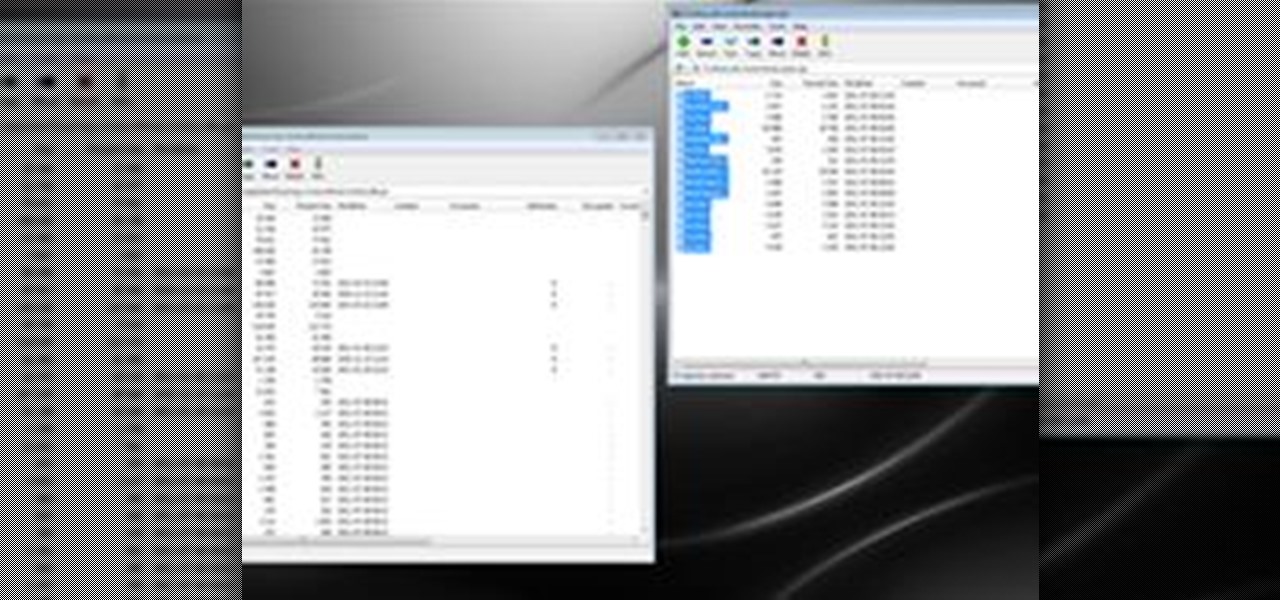
Completely Hide UTorrent and Bittorrent Software in Your PC While It Is Still Running!.

There are always those days when bread-lovers want a hearty savory bread to eat, but there isn't quite enough time to make a yeast bread. After all, yeast breads take anywhere from an hour to a full day for the first rise. Well, that's where this whole-wheat beer bread comes in! It doesn't take long to throw together and bake, but tastes delicious and is relatively healthy due to the use of whole wheat flour. If you don't like whole wheat flour, you can always substitute the same amount of pl...

You've probably heard about Rep. Greg Walden (R-WA) tweeting in Morse code back in December. .-- .. .-.. .-.. / -.-. .... .- .. .-. / -.-. --- -- -- / .- -. -.. / - . -.-. .... / ... ..- -... / --... ...-- ... / .-- --... . --.- ..
Minecraft is a great game as it is, but there are many mods out there that make it even more fun to play. Installing these mods may seem difficult, but with a little practice, it becomes extremely easy.

Reading crochet instructions for beginners isn't exactly the easiest thing to do. But fear not, I'm here to help! :)

Scrod sounds good, right? This fish will satisfy your seafood craving. But wait… is scrod even a fish? No. If you're not from the New England-area, you probably would never know this, but scrod is not a fish at all. It's often misconceived as being a type of fish. However, scrod is a New England term that refers to any white fish that has been split and boned before sale, typically cod or haddock.

Bananabells are very popular and can be used for most body piercings. They are most commonly used for navel piercings and ear piercings. This how to video teaches you how to insert a bananabell, and what type of bananabell will be right for you. There are many different sizes of bananabell depending on the gauge of your piercing, so make sure you know your measurement before you purchase new body jewelry. Watch this tutorial and you can be wearing a bananabell in no time. Choose and insert ba...

Flash is commonly used to create animation, advertisements, various web-page components, integrate video into web pages, and more recently, to develop rich Internet applications. In this Flash 8 video tutorial you will learn how to import sequential images. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Use sequential images to create animation in Flash 8.

Many cooks refer to well-seasoned cast iron skillets as the original non-stick pan. A cast iron skillet is a versatile piece of cookware, going from the top of the stove to the oven with ease, provided the handle is also cast iron. The secret to a non-stick skillet is in the seasoning and cleaning process. Improper seasoning, cooking acidic foods and incorrect cleaning methods can all remove the non-stick capabilities. Achieving and maintaining a non-stick cooking surface is uncomplicated and...

There are many different types of prepared catfish baits for catching channel and blue catfish. These baits are often referred to as "stink baits", but while they might smell quite foul to some anglers, the smell really attracts catfish.

Summary

Learn how to tie overhand knots from the people who make sure no rope goes untied. Actually, you probably already can since this name refers to the first step in tying your shoe! Tie overhand knots.

Also called a running knot, the slip knot actually refers to any knot that "slides" along the rope, or can be untied by pulling both ends. Watch and learn how to tie one type of slip knot. Tie a slip knot.

Hello! Today, I will show you how to add captions to your YouTube videos. Captions help people understand when the video itself does not entirely explain your tutorial.

Professionally and academically speaking, I am a computer scientist, but I also enjoy lock picking as a hobby, so I thought I would share what knowledge I have with this. Before we start doing anything, first we need to understand the fundamentals of how locks work and then acquire and familiarize ourselves with basic lock-picking tools.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

The only thing better than successfully pulling off a new experiment is doing it with household materials. You get to laugh in conceit as professional scientists everywhere spend all their grant money on the same project you just accomplished with some under-the-sink chemicals! However, there are times when DIY gets dangerous. Some household chemicals are not pure enough to use and some are just pure dangerous. Let's take a look at two problems I have encountered in the course of mad sciencing.

Everyone dreams of having super powers. Flying, invisibility, and x-ray vision are popular, but my favorite is fire power! I've always wanted to be Wheeler from the Captain Planet kids show, and now I can with these handheld fireballs of awesomeness. The fireballs burn at a low temperature, so they are safe to hold in your hand and throw (shoot) at imaginary enemies.

In this article I am going to take a look at the Google keyword tool, which is one of many keyword tool programs that you can use to find your keywords.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

As my in game name (TehGeekFather) would suggest I tend to like things on the Geekier side of things. Games being one of them. (duh I'm on a Forum dedicated to Minecraft) That being said I am a huge Fallout fan. (NO! not the band. <Sigh>) I'm referring to the post apocalyptic series first developed by Black Isle Studios, the roll playing game division of Interplay, back in 1997. Fallout 1 and 2 were pretty big back then open game play, being able to complete tasks in different ways depending ...

Following the first part in this series on advanced cracking techniques, we are going to go over how we can intelligently crack passwords using the old-fashioned bruteforce method. These unique cracking techniques aren't widely used, because most crackers are Script Kiddies who have no idea what the concepts are behind cracking passwords, thus, word won't get around too quickly.

TCP/IP Client / Server Application Hello! Today's blog post will be about coding a very rudimentary Client and Server application duo, which will communicate by using TCP Sockets.

Scrabble Bingo of the Day: CABRESTA [n/pl.] A cabresta (also cabestro or cabresto) is simply a lasso, a rope formed with a running noose that's used on ranches and Western plains for catching horse and cattle. Cabresta comes from the Spanish word halter, which refers to the headgear used for leading or tying up livestock and other animals. But halter also used to mean to hang someone by roped noose, which could be how it became popular as a term for a noosed lasso.

About Today's topic Today we will talk about diagnosing and fixing connection problems. Let's face it - the truth is everyone who uses a computer and has an internet connection will have to deal with this at some point. Connection problems often occur at the wrong time and it is a real pain.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

BANSHIE n pl. -S banshee 62 points (12 points without the bingo)

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. While mining is a basic aspect of Minecraft, it is often overlooked. Every adventure requires iron and diamonds and other ore and if you're playing in hardcore mode then you need all the help you can get.

Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds.

VERONICA n pl. -S a handkerchief bearing the image of Christ's face 63 points (13 points without the bingo)

Improve your bingo skills with a roundup of this week's Scrabble Bingo of the Days. What exactly is a bingo? It's when a player empties his or her rack in one turn, placing all seven of their letters on the board to create a word that's at least seven letters long.

On October 7th, the IndieCade Conference will open its doors to some of the most innovative minds in the independent gaming industry. The three day event located in Culver City, California includes presentations by notable indie designers, workshops, galleries, and mixers. On the following day, however, the IndieCade Festival begins. Unlike the conference, the festival includes events targeted at gamers and the general public. While a $15 wristband will grant you access to keynotes, events, a...

MACHZOR 73 points (23 points without the bingo) Definition: mahzor; a Jewish prayer book [n]

Dead Island is known for having the most successful trailer of any game ever. It was a beautiful cinematic experience. But sadly, as details of the game itself emerged, and after it was shown at conventions around the world, doubt began to set in about whether this five-year-long project would live up to the hype.

There are over 250,000 apps in the Android Market, ranging from free productivity programs to a ridiculous $200 for a vuvuzela horn effect. But chances are you don't have the vuvuzela app on your Android smartphones right now, but you are likely to have one of the ten most popular apps in the Android Market.