Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

The iPhone X was released in November 2017, and the iPhone 8 and 8 Plus dropped right before it, but the hottest news right now revolves around the 2018 iPhone releases. The rumor mill regarding the iPhone X's successor started churning out speculations on names, cameras, display size, and more almost immediately after last year's devices, and there have been many new leaked details since.

For about a million Americans each year, a joint replacement brings relief from pain and restored mobility. But, 5–10% of those people have to endure another surgery within seven years, and most of those are due to an infection in their new joint. If doctors could treat infections more effectively, patients could avoid a second surgery, more pain, and another rehabilitation.

For a company more associated with debugging computer programs, Google's parent company, Alphabet, is making a name for itself by taking on the real thing — mosquitoes.

A new study casts real suspicion on the possibility of life on Mars. Why? It seems the surface of the planet may be downright uninhabitable for microbial life as we know it.

In the US, ticks can spread several pathogens in one bite. A new test offers physicians the ability to identify what infections ticks are carrying and can detect if one of the pathogens could be the spreading Powassan virus.

Antibiotics used to prevent diseases in livestock are creating a world of hurt for humans and the soil we depend on for food. Bacterial resistance to antibiotics is a global health issue. The overuse, underuse, and poor use of these life-saving drugs is rapidly removing them as a treatment option for serious infections in humans—plus bacteria are naturally adaptive.

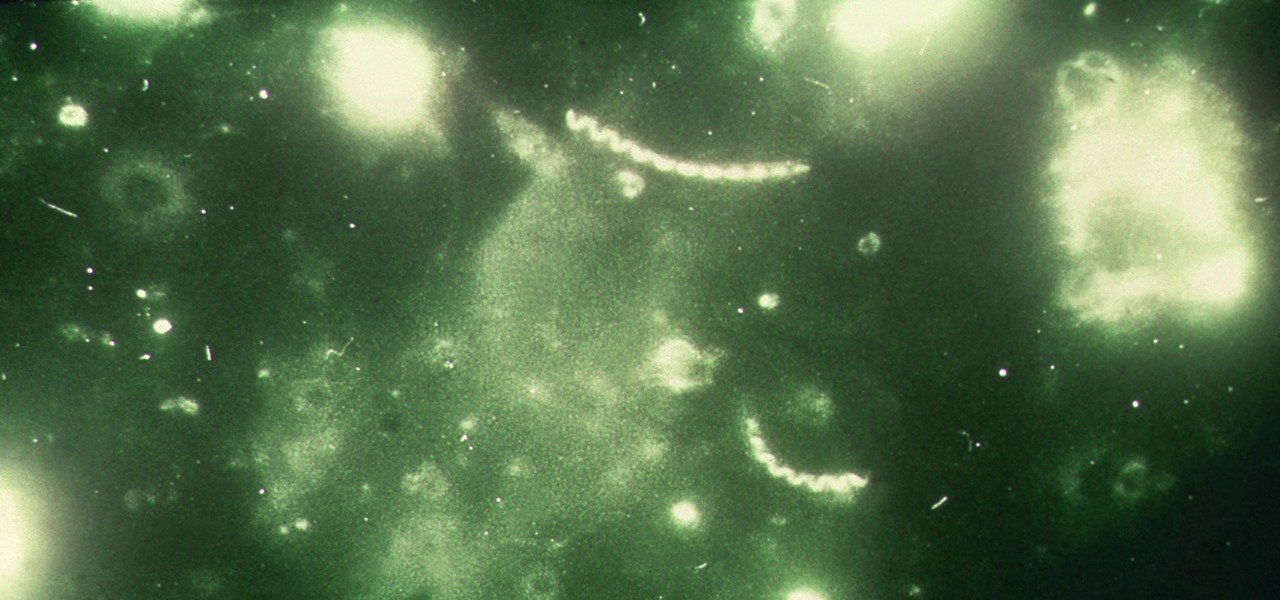
The squiggly guys in this article's cover image are Propionibacterium acnes. These bacteria live in low-oxygen conditions at the base of hair follicles all over your body. They mind their own business, eating cellular debris and sebum, the oily stuff secreted by sebaceous glands that help keep things moisturized. Everybody has P. acnes bacteria—which are commonly blamed for causing acne—but researchers took a bigger view and discovered P. acnes may also play a part in keeping your skin clear.

The office of your physician, or your local hospital, is where you go when you need medical care. But it could also be where you could pick up a life-threatening infection.

Have you ever had the stomach flu, aka the 24-hour flu? Well, chances are high that you never had influenza, but an intestinal infection called gastroenteritis.

A recent pathogen outbreak in Illinois is just one of many outbreaks of an underappreciated, but serious, viral infection passed from rodents to humans. These hantaviruses have been cropping up more frequently in the last decade or so, giving us more reason to clean out our dusty attics, basements, and garages.

After California college student Luis Ortiz blacked out and was taken to the hospital in 2015, doctors were startled to discover the reason his brain was swelling—a one-centimeter long, wriggling tapeworm living within a ventricle in the middle of his brain.

What do Leo Tolstoy (writer), Beethoven (composer), Paul Gaugin (artist), and Adolf Hitler (politician) have in common? They are all considered to have suffered from the sexually transmitted disease syphilis.

You can find chili peppers in practically every cuisine. From the sweet Italian variety to the spicy Thai bird's chili and the smoky Mexican chipotle, peppers are ubiquitous and universally loved. But if you find the range and scope of these little fireballs overwhelming, you're not alone.

United Arab Emirates is the cosmopolitan country that offers various attractions for tourists across the world. This country has buildup its image as one the fastest growing country of this region. Besides visiting worth seeing places, travelers can also enjoy tasty traditional food of UAE across the country. Whether you have chosen Dubai, Abu Dhabi, Ajman or Ras Al Khaimah, you will get the chance to enjoy best traditional food everywhere.

What Is Ferrofluid? Ferrofluid is a black, solvent-based liquid, that, in the presence of a magnetic field, becomes strongly magnetized. The fluid is made up of nanomagnetic particles coated with an "anti-stick" or surfactant compound, suspended in a "carrier", commonly an organic solvent. For mechanical applications, it is used in hard drives and speakers as a lubricant. However, it also has been implemented in artwork, as seen in the video below.

Update: this article is referring to the 1.9 pre-release beta version, which is now commonly referred to as 0.1.9, released in October of 2011.

This recipe for potatoes in a creamy yogurt sauce is just perfect for those times when you haven’t had a chance to get to the grocery store for fresh vegetables. The hardest part out of the entire recipe is boiling the potatoes. With the red of the tomatoes in the gravy and the green of the cilantro garnish, it is a visual treat. Watch this how to video to learn how to cook Indian style potatoes in a creamy yogurt sauce. This potato dish is also commonly known as dahi wale aloo.

Tandoori roti is another type of Indian unleavened bread which is usually made in a clay oven called a tandoor and commonly enjoyed with chicken, lamb, mutton or other non-vegetarian dishes. Vegetarians out there, don’t worry. It tastes just as fabulous with vegetarian curry dishes as well! Watch this how-to video to and try this easy to make at home recipe and method. You won’t need to run out and buy a tandoor!

The US Department of Treasury isn't generally known for being on the very edge of technology innovations (see the current hubbub around crypto), instead usually waiting until certain tools have been battle-tested in the mainstream or enterprise sector.

Sure, Snapchat AR Lenses can be fun, but they can help communicate complex issues as well. While our Facebook news feeds were filled with references to 311 Day, March 11 is also World Kidney Day, the United Kingdom's National Health Service Blood and Transplant (NHSBT) used the occasion to educate its constituents about organ donation.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

We all listen to podcasts differently — on the way to work, at the gym, when drifting off to sleep. If you're in the latter group and rely on Overcast to help you with your nightly routine, you're probably sick of its blinding light theme keeping you up. That's why the app features a dark mode, to keep things easy on the eyes while picking out or playing an episode.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

The word on the street is Android users want a dark mode. With the increased usage of AMOLED panels on smartphones (including some midrange devices), there is a considerable demand for dark themes and their battery saving benefits. Recently, Nova just added the feature to Google Discover.

The Galaxy S10 has finally been revealed to the masses, and it certainly doesn't disappoint. As the flagship to herald the tenth anniversary of the venerable Galaxy S line, the S10 has kept popular and familiar design elements like the immersive Infinity Display while employing new features like more advanced cameras to set a new standard for other OEMs to follow.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Samsung hopes to make a splash with the new Galaxy Note 9 to make up for the underwhelming sales of its signature Galaxy S9 series. This flagship is a radical departure from its predecessors — it's now optimized for gaming and paired with the most advanced S Pen stylus to date. Here's everything you need to know.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Every now and then, an iPhone will freeze up and become unresponsive due to a software glitch. It can be a buggy app that somehow interferes with iOS or a software update that somehow didn't install properly. Whatever the cause, it's safe to say that no iPhone is immune to this problem, not even the new iPhone X.

Now that we have installed the toolkit, set up our prefabs, and prepared Unity for export to HoloLens, we can proceed with the fun stuff involved in building a dynamic user interface. In this section, we will build the system manager.

For those of us on the fast ring of the Windows Insider Program — Microsoft's continual beta program for the Windows operating system — the constant updates can be a bit of a pain. But there is a trade-off. We get to try the new features long before they come out to the public. So if you like to see the new shinies before everyone else, and don't mind the sometimes two or three major updates in a week, then this is definitely the option for you.

With the US Department of Homeland Security (DHS) banning laptops and tablets on flights originating from 10 international airports, and the United Kingdom taking similar precautions, international travelers are faced with hours of non-productive — or far less entertaining — flight time.

Paris, girl, you are awesome, but you did not invent the selfie. If you want to spread this #newmarketingterm to the media masses, then go right ahead. It's your brand, your career, and you got the opportunity. People will listen. No one really cares about who invented the silly thing anyway. Though I got to say, the original king of the selfie did seem like one pretty chill dude ...

Stop me if you've heard this one before. You plop a marshmallow down in front of a kid and propose the following: You can eat this marshmallow now, or you can wait twenty minutes and eat two marshmallows. What do you think the kid is going to do? Better still, what do you think you would do? Personally, I'd eat the first marshmallow without hesitation. But now we're getting off track ...

A new study published on April 12 in Medscape gives us an update on the Hantavirus genus of pathogens, which spread viruses via rodents that can cause fatal diseases in humans, such as hantavirus pulmonary syndrome (HPS).