For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

One feature in iOS you're likely underutilizing is 3D Touch, a highly useful, unique tool for iPhones ever since it first appeared on the iPhone 6S. Apple's pressure-sensitive interactivity gives iOS an extra layer of functionality, which can be clearly seen across the entirety of your device. From the lock screen to the home screen to the apps in between, there are plenty of ways to use 3D Touch.

As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

For many of us, getting to inbox zero is the highlight of our day. But if you used your email address to sign up for various sites and services, your inbox is probably cluttered with all sorts of spam, news letters, and unimportant emails. Thankfully, Gmail has a feature that can solve this by using machine learning.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

A recent case of Powassan virus has been reported in Saratoga County and may have been the cause of the infected patient's death. It's the 24th case in New York State since 2000, and will be reported to the CDC tomorrow, the NY Department of Health told Invisiverse. The tick-borne illness has no vaccine or specific treatments and can damage the nervous system.

What would it be like to have clothing that killed microbes? Or paper that repelled pathogens? A research team from Rutgers University has developed a prototype out of metalized paper to zap the bad guys without being super expensive. Sound good? Read on.

Respiratory Syncytial Virus (RSV) is the most commonly occurring lower respiratory tract viral infection in young children and usually isn't serious, but in premature infants and babies under six months old, the infection can be severe, and even fatal.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Our canine best friends could spread our bacterial worst nightmare, according to a recent study. The problem with drug-resistant bacteria is well known. Overused, poorly used, and naturally adaptive bacteria clearly have us outnumbered. As science drives hard to find alternative drugs, therapies, and options to treat increasingly resistant infections, humans are treading water, hoping our drugs of last resort work until we figure out better strategies.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

Usually, the mucus lining of the female genital tract presents a barrier that helps prevent infections. But, somehow, the bacteria that causes gonorrhea gets around and through that barrier to invade the female genital tract.

Having a Clostridium difficile infection means stomach pains, diarrhea, fever, and loss of appetite, and if the symptoms weren't bad enough, the disease often reoccurs. Now, new research has found an increased risk of recurrence in people who take medication to treat their stomach acid, gastroesophageal reflux disease, peptic ulcer disease, or stomach discomfort.

Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.

There are a ridiculous number of onion varieties, so choosing the right onion can make my head spin sometimes. With four distinct types of "green onions" that all look almost the same, I'm guessing you have the same issue—but not once you know the secrets to identifying and properly using each of these green onion types.

Amazon just unveiled the Kindle Oasis, the latest model in its popular line of e-readers. There are a couple of nice new features, but it's pretty hard to see how any of them justify the whopping $290 price tag (or $310 if you don't want ads littering your screen).

If you're gluten-free, on a diet, or just cutting the carbs like me, eating a sandwich can be a dangerous game. There are traditional alternatives such as lettuce or egg wraps, but they have their drawbacks: they can't hold as many ingredients, they can be lack flavor when raw and un-rendered, and it's hard to layer the toppings and condiments to create your perfect bite.

As one of the most popular home screen apps on Android, the Google Now Launcher is used by millions of people across the world. The two main reasons behind this success are its integrated Google Now home page and an elegant, easy-to-use design.

While seltzer water is commonly consumed as a beverage (and a healthier alternative to carbonated soda), it is less known as a fantastic addition to many familiar recipes. The bubbles in seltzer water expand when heated, and when added to certain foods, it instantly allows them to be lighter in taste and texture.

Frozen meat is a saving grace for weeknight meals. Whenever I crave a certain protein, all I need to do is defrost it. Sometimes, I don't even need to defrost it in order to use it.

When we were kids, Saint Patrick's Day was a green-hued holiday that promised green eggs in the morning and green mashed potatoes in the evening... along with some traditional corned beef and cabbage, of course.

Frozen fruit is always in season at your local grocery store, so you don't have to wait until the farmers market starts again to enjoy delicious baked fruit desserts. Peach pie, blueberry muffins, raspberry scones... all of these delicious baked goods can be just as delectable when using frozen fruit, too.

Eating out is great, but being able to cook the delicious ethnic foods you eat at restaurants is even better. It may seem daunting to put together a bunch of ingredients with which you might not be familiar (some with names you've never even heard of!), but with the guidelines below, you'll be making your own versions of ethnic favorites in no time.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

In general, the fingerprint scanner in Samsung's 2015 flagship phones is quick and accurate, but when you get that "No Match" message while trying to unlock your phone, it can be incredibly annoying. To help curb these issues, I'll go over three tips for speeding up the unlocking process that should work wonders on your Galaxy S6, S6 Edge, S6 Edge+, or Note 5.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

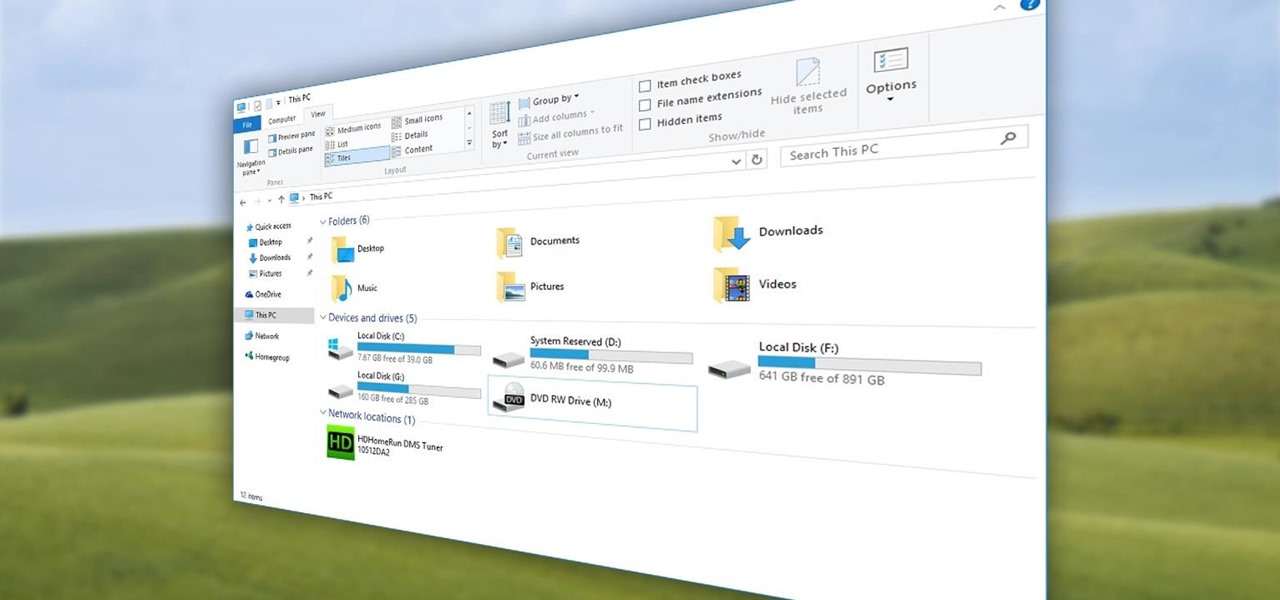
Quite a few things have changed with Windows 10, but one of the more central features that has received a makeover is the old Windows Explorer program, which has been renamed to File Explorer in this version.

Most primary cocktail ingredients just sound delicious. Lime and tonic water? Yes, please. Bitters and simple syrup? Sign me up. Egg whites and... wait... egg whites? In a cocktail?

Here's a fact that everyone knows: avocados are delicious in guacamole, salads, and sandwiches. Here's a fact that's less commonly known: avocados are delicious in desserts, too.

When you think of bivalves, such as manila clams and oysters, you tend to think of the meat as being nicely tucked in the shell. Anything else would be scary, right?

We're all familiar with the sinking feeling that happens when you cruise through a recipe, only to arrive at an instruction that calls for a tool you don't have. Some of the best food hacks (and my personal favorites) exist to combat that problem. Why spend money on a kitchen tool—or worse, avoid a recipe altogether—when you could find a new way to achieve the same result?

At its core, grilling is the simplest form of cooking. You create extreme heat, you put a piece of food on top of the heat, and then you sit back and watch the magic happen. Yet despite the inherent simplicity in grilling, there are a million ways to make it more complex, more unique, and, yes, even more flavorful.

I have a thing for citrus in any form. If I can't get a hold of oranges or clementines, I've been known to slice up lemons and limes and eat them straight with a little bit of salt—terrible for the tooth enamel, but amazing for the tongue.

Ad blocking on Android usually requires root access, but a pair of new browsers based on the open source Chromium and Firefox builds are looking to change this.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!