Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

Despite legends to the contrary, it appears that the saliva of a Komodo dragon is not teeming with pathogenic bacteria that kills their prey. Its reputation to survive while colonized with lots of horrible disease-causing bacteria, true or untrue, has made it the subject of research in pursuit of natural antimicrobial agents and led scientists to some remarkable findings.

When shopping for a new smartphone, you'll encounter comparisons and spec sheets that are filled to the brim with values like mAh, GB, and GHz. To the average consumer, however, these values are meaningless, so we end up looking at which device has the specs with the highest actual numbers.

Brand loyalty is one of the main factors behind our decision to choose a particular mobile device, but it doesn't have to be the entire equation. Educated consumers know that certain devices simply fit their budget and usage better than others, which means you can't always let a logo dictate what kind of phone or tablet you buy.

Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day and night, haunting you.

The older I get, the more my Friday nights involve watching Netflix at home with a bottle of Maker's Mark and a box of Oreos. Netflix is a big part of my life, and I'm not alone. YouTube and Netflix make up over 50% of all activity on the Internet, so it might be worth your time to understand why Netflix seems to cause so many headaches and what can be done about it.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

We see Steampunk props all the time and wonder where the maker found all their pieces. In fact, for some people it's almost like a game to examine each prop and see if they can name all of the original parts.

Sweet potatoes are a popular side dish, especially around the holidays. Save some money and start growing sweet potatoes at home. Not only will they be cheaper, but you'll be able to enjoy them year-round.

The physical Camera Control button on the side of the iPhone 16, 16 Plus, 16 Pro, or 16 Pro Max is great for launching Apple's Camera app and adjusting settings like exposure, depth, and zoom with press and swipe gestures. But it's not just for the Camera app. Camera Control also works with supported third-party camera apps, allowing you to quickly snap photos, record videos, modify settings, and more.

Apple's spring event, where the company will announce a new iPad model, is just around the corner. We also expect to see the long-awaited Apple Pencil (3rd generation), also known more simply as Apple Pencil 3, with several significant enhancements that promise to make it an indispensable tool for anyone who uses their iPad for note-taking, sketching, illustrating graphics, and more.

Whether it's everybody or just a specific contact you can't hear during audio and video calls when wearing headphones, your iPhone has hidden, little-known tools to help you catch every word they say in the conversation. Even if you can normally hear everyone during calls, customizing these headphone preferences can make conversations crystal clear.

When Steve Jobs introduced the first iPhone, he pointed out that the biggest problem with physical keyboards on mobile phones is that they're always there, whether you need them or not. Now, 17 years later, a new company is bringing us full circle, giving us the best of both worlds: a physical keyboard for iPhone that can disappear whenever you want.

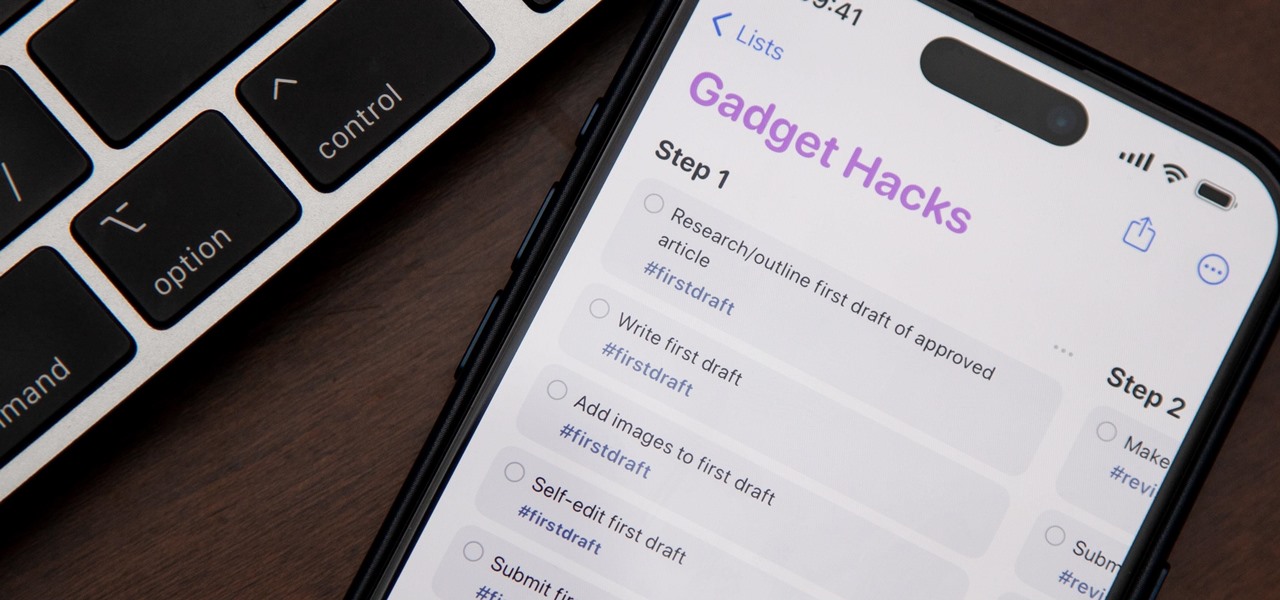
If you're still using a third-party task manager on your iPhone, you might want to check out Apple's updated Reminders app. With each new update, Reminders gets more powerful yet remains one of the simplest task managers to use, and iOS 17's new to-do list features reinforce that statement.

Now that Vision Pro, Apple's mixed reality headset, has been announced, Apple can free up some R&D resources to commit to its upcoming foldable iPhone, which has been rumored for just as long as Vision Pro has. Will it be a flip-style or a larger foldable? Let's see what all the industry experts and Apple leakers have to say.

There's a feature that every Apple Watch owner should know about — one that makes navigating menus, tapping tiny icons, and interacting with complications, among other things, much easier on the small display.

In the past, Apple never really put much work into its Contacts app for iPhone, making the tool much less useful than its Mac and iCloud counterparts. But now the Contacts app for iOS is a force to be reckoned with. Packed with new features (some hidden), it's finally good enough to beat all of the third-party contacts apps that previously reigned supreme.

You may not realize it, but most of your apps include third-party tracking services that monitor your activity in other apps and websites to serve highly-targeted ads to you. But now you can stop the creepy behavior on an iPhone and Android phone.

One of the most useful new features Apple included on iOS 16 lets you instantly lift the subject out of a photo, separating it from the background. Once extracted, you can paste, save, or drop the cutout wherever you want as a new image, and you can even make it a sticker in messaging apps.

You can set a GIF as the wallpaper for your iPhone's lock screen, but it won't animate like it does when looking at the image in the Photos app. It's an annoying limitation on iOS, but one that's easily bypassed with a tiny bit of work.

If you're like me, you don't have time to sit down and leisurely read an entire article from start to finish — but you still want to be informed throughout the day. Instead of just browsing the daily headlines, there's a free service that will summarize any article you throw at it, giving you a better idea of what's going on without committing to reading an entire article.

Whether you drop your iPhone into a toilet or your dog's water bowl or regularly take it into the shower or pool, water will likely become nestled inside its speaker grilles. Water exposure causes audio playback through the speakers to soften and sound muffled, and getting that water out is no easy task. Luckily, there's an app for that.

Unless you have unlimited cellular data, you probably connect your iPhone to every Wi-Fi network you come across. It could be a local coffee shop, public library, or just a friend's place. Wherever it is, you'll need to ask for the access point's password if it's a secured network, and that can be a hassle if the place is busy or the owner forgets the credentials. Luckily, Apple has a solution for this problem.

Gaming on smartphones has grown considerably since the days of The Impossible Game and original Temple Run. Mobile games can be just as in-depth as console and PC video games, but some of those require external controllers for the best gameplay possible. One controller you can use is the PlayStation 5's DualSense wireless controller, and it pairs nicely with most Android devices.'

If you have a PlayStation 5 and an Android phone running Android 12, you can stream and play your PS5 games right from your mobile device using PS Remote Play. While simply pairing your PS5's DualSense wireless controller with your phone will give you the basic controls to play third-party games, Remote Play takes a little bit more work to set up.

Sure, Microsoft has mostly marketed its HoloLens headsets towards enterprises and developers, but we learned this week that, like every other tech giant, the company is working on a consumer-grade AR wearable. Speaking of consumer smartglasses, Apple made another strategic investment this week that has implications for Apple's AR future.

Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many fingerprinting tools available, such as httprint and WebTech, but there are even more that can aid us in reconnaissance.

The Metaverse, or AR cloud, has been a sci-fi dream for decades, but only recently have companies begun to actually develop the technology to build it. With its latest funding round, Epic Games is suddenly a front-runner in this pursuit.

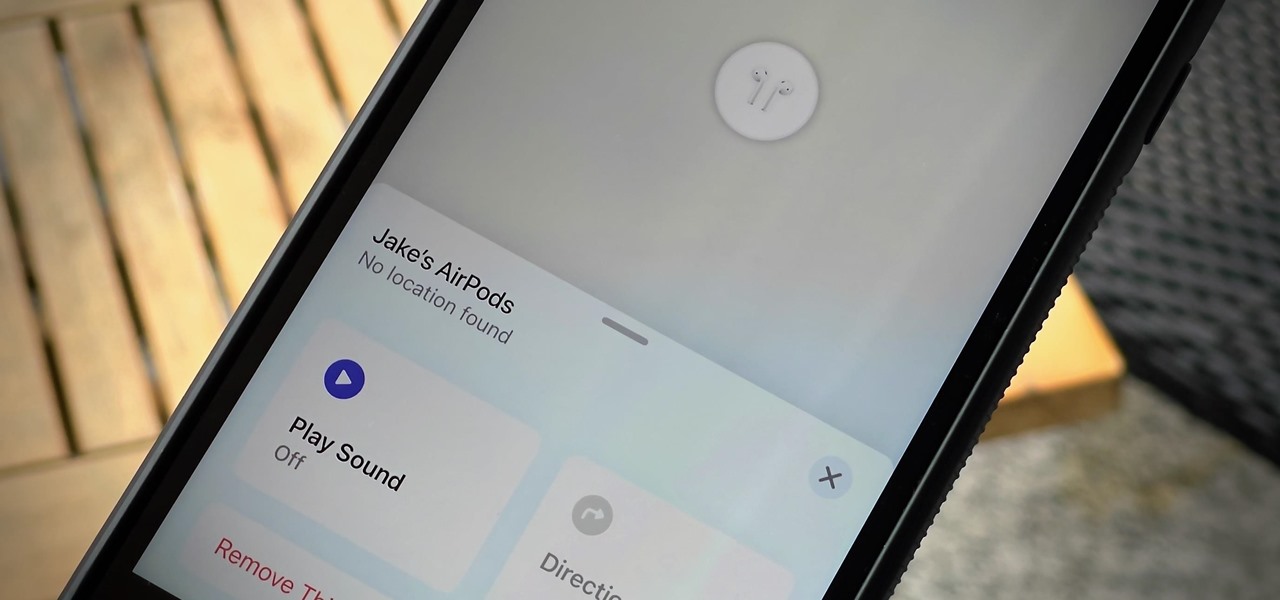
If you lose your AirPods, AirPods Pro, or AirPods Max, you can turn to Find My to locate them. But sometimes, things don't go according to plan, and many things can go wrong. For example:

The augmented reality industry has grown steadily over the past four years, but now it is on a collision course with uber-popular non-fungible tokens technology, with Looking Glass and music artist Reggie Watts among the latest to strike while the iron is hot.

I always keep my iPhone's Portrait Orientation Lock on so that my screen doesn't randomly rotate while I'm lying down. However, there are certain apps that I do turn it off for. It's kind of a pain since you have to swipe down the Control Center and toggle the orientation lock — but that ends now. Instead of doing it manually, a new iOS update can automate app orientations for you.

Apple wants to support the advertising economy, but its primary focus of late has been user privacy and security. In Safari, cross-site tracking, which lets content providers track you across websites and apps to show you more targeted ads, is disabled by default. However, content providers can get around that using less privacy-invasive ad measurements, but you can stop that too in iOS 14.5.

If you just got an iPhone 12, 12 Pro, 12 Pro Max, or 12 mini, and you've never owned an iPhone before, some of the most basic tasks can be baffling. Shutting it down, force-restarting it, quitting apps, and even viewing the percentage of battery remaining sound simple but aren't very intuitive for new iPhone owners. Another big question mark is screenshots, and there are several ways to take them.

Few apps on the iPhone give you ways to change their color scheme aside from Dark Mode in iOS 13 and later, but that doesn't mean you can't give an app a new color theme or filtered look. With the Shortcuts app in iOS 14 and later, it's totally possible, and it'll work in practically any app.

GTFOBins and LOLBAS are projects with the goal of documenting native binaries that can be abused and exploited by attackers on Unix and Windows systems, respectfully. These binaries are often used for "living off the land" techniques during post-exploitation. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line.

The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stumble upon. But with enough patience and persistence, it is possible to escape these restricted environments.

Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus and firewall software is installed.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.