No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.

If you've read Alex Long's last two articles in this series (Part 1 and Part 2), you know by now that making money rarely is risk free, and generally plays out to be a high risk-high gain/loss scenario. The best way to make money is to have money, so for this article, lets assume a financial backing of about $10,000 dollars. For the sake of simplicity, I'm going to be working with online trading systems in this article. Some stocks are traded on exchanges, where buyers meet sellers and decide...

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Sometimes it's easy to get overwhelmed with the sheer scale or complexity of a build or group project on your favorite server. Too much stress from any creative endeavour can lead to mistakes, discouragement, or fighting among a community. What better way to relieve stress and entertain the troops than some old fashioned competition?

Microsoft has had a pretty bad wrap with their Xbox 360 gaming console. Right from the start, the console has suffered a multitude of different hardware failures and design flaws. These problems cause the parts to get too hot and become faulty. I'm sure everyone who's had an Xbox 360 has gotten at least one Red Ring of Death or E74 error.

Halloween will be here in just over a week, which means next week these Scrabble Bingo of the Days will become more horrific. This week, there's just a few relevant Halloween seven-letter words for your Scrabble vocabulary, referencing witchcraft and one of the eeriest horror movies of all time, The Thing (not this year's version).

It's a question I've been pondering a lot lately. Technically, children under the age of 13 are not allowed to join Facebook. But according to a Consumer Reports in May, 7.5 million children 12 and younger are already on the site. Currently, federal law prohibits websites from collecting personal data from children without parental permission. The Children's Online Privacy Protection Act, or COPPA, as it is more commonly known, has been in effect since 1998, but has not been updated since.

There's only a few week left until costumes and candy take over the streets, which means they'll be more and more seven-letter words in the Scrabble Bingo of the Days that relate to the Fall season, horror movies, and of course… Halloween. Below you'll find bingo words relevant such films as Halloween, Children of the Corn and The Wicker Man.

From the onset of the popularization of apps for the iDevice, users have experimented with creating original artwork on their iPhone/iPad/iPod Touch. And when famed British artist David Hockney christened the iDevice with his painterly digital drawings, the trend exploded even more.

For most Americans, the bane of the hangover is typically remedied by lots of water, painkillers, greasy food, and a day wasted on the couch. But if you're tired of potato chips and fried eggs, perhaps it's time you enter unfamiliar territory. Below, a combination of unorthodox methods for taming the beast, derived from science, sparkly Whole Foods new ageism, and the far East.

Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as this list from the Wall Street Journal of the fifty most common passwords gleaned from the 2010 Gawker hack. If your password is on one of those lists, you need to change it. Right now.

If you found the world renown Body Worlds exhibition gnarly and perverse, perhaps you'll find this latest parade of plastination a little less so—considering we don't share the same DNA as these specimens of jerky-in-the-name-of-science. The Koerperwelten der Tiere—or Animal Body Worlds–doesn't showcase preserved corporal matter, but rather 20 odd plastinated mammals, currently on display at the Cologne Zoo in Cologne, Germany.

At the beginning of every class, or almost every class, we do a series of exercises. The Japanese word for this sort of calisthenic exercise isundo. These exercises derive from the Goju style of karate created by Miyagi Sensei in Okinawa in the early part of the 20th Century. In devising these exercises Miyagi no doubt borrowed liberally from the Chinese, whose influence on the southernmost island of the Japanese archipelago was immense.

Using a location thats already being utilized, It could be a house or an apartment, mount cameras in various hidden areas throughout. Some at chest level and some up near the ceiling for good shots. Be sure that the windows and doors can be locked FROM THE OUTSIDE.

Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and malware to spread. And while there's a plethora of antivirus tools for Windows, sometimes infections (such as certain scareware) can disable the install and/or use of antivirus systems and render your OS unusable until cle...

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Amazingly, a lot of people I know haven't even heard of SOPA or PIPA. Now, every English-reading person with an internet connection will finally have those two four-letter acronyms emblazoned in their minds. For the entire day today, Wikipedia's English-language site will be in total blackout in protest against the proposed legislation in the United States. And that's not all. MoveOn, Reddit, BoingBoing, Mozilla, WordPress, TwitPic and other popular websites are down today in protest.

Let's face it, not every logophile is addicted to Scrabble. Without the use of a timer, Scrabble can be a pretty slow game. Even in clubs and tournaments where the standard time limit is 25 minutes per person for a two-player game. Now, take away time restrictions and add two other players and you've got a game that could take up to 2 hours! It all really depends on who the competition is.

WELCOME & THANKzZz For Your Contribution, Support And Time...! ...Hello, zZz~AKA~StanDP Here...;

Technology: The Less You Know the Better?

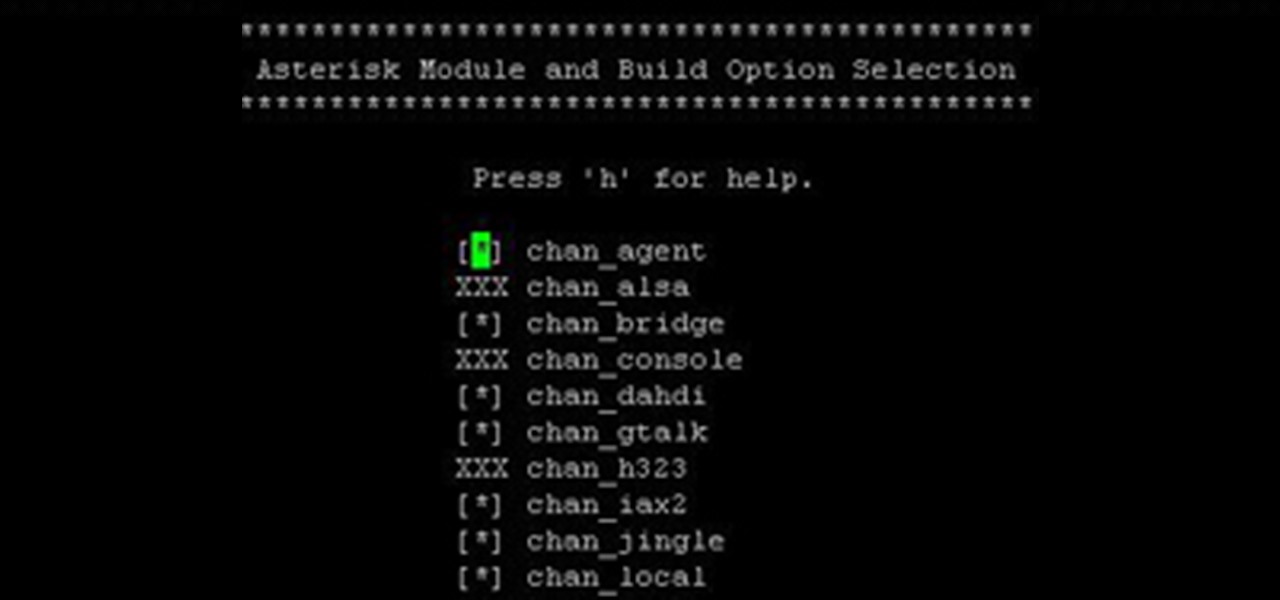
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.

You're sitting in front of your grandmother's Windows XP machine that has the worst infection you've ever seen. Safe mode? No dice. Restore points? They're compromised. Even worse, all of the files are hidden and none of the executables will run! This leaves her computer in a bricked state. Without some serious CPR, it will be lost to you. Sure, you could just reinstall the system, but then you might lose all of that valuable data.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

Imagine you're in Paris and you need to get to Versailles. Looking around for directions, you come to a cold realization—you do not speak a lick of French! How are you going to get to Versailles and what happens if there is a detour? It will be a difficult struggle, and you'd probably get lost and eventually fail. This is why it's important to know some of the country's language before taking that trip in the first place.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

When you first become interested in learning how to program, it can be difficult to find a place to start. A lot of questions come up, especially if you're new to the idea of programming entirely. After you pick which language you want to learn, you have to worry about how you're going to write the language.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

No matter what word game you're playing, whether it's Scrabble or one of its near-homogeneous counterparts like Lexulous, Wordfeud or Words with Friends, one of the easiest ways to stay on top of your opponent is knowing all of the legal two-letter words you can play. You're not going to win by only playing two-letter words, but there are definitely occasions when the game could slip from your hands by not playing them.
Setting up shadows takes just as much time and attention as setting up lights. You can think of all of your illumination as one half of your lighting design, and shadows as the other, equally important half. Shadows can add richness to the tones and shading of your image, tie elements together, and improve your composition. Besides their artistic importance, rendering shadows is a key technical area to master. This chapter will explore both the visual and the technical sides of shadows and oc...

Making your way into an online community can be really exciting. Some life-long friendships and lasting romances begin in humble chat rooms and message boards. But for the novice internet user, one of the biggest hurdles can be trying to figure out just what people are saying to one another.

QI and ZA. QI n pl. -S the vital force that in Chinese thought is inherent in all things

If you're looking to acquire the newest iPod model or latest Xbox without breaking the bank, your first stop would probably be eBay, maybe even the Amazon Marketplace, or any of the other reputable online marketplaces and auction sites. But you probably haven't hit up the penny auctions yet, and that could be a good thing, depending on how you go about it.

Introduction I will not go into some time-waster of a story about how I came to build this app. It was a prerequisite in a bigger project I am still tinkering with from time to time.

Like the press covering film and many other specialized fields, video game journalists use all sorts of jargon to convey to their knowledgable readers as much information about a game as quickly as possible. For non or newbie gamers, this can be extremely confusing.

Choose the Right Path Making a choice

I am writing this quick post in response to the recent earthquakes and tsunamis that are affecting Japan. As soon as the news broke, and we began to hear of tsunami warning for our area, I immediately realized how under prepared I was for a natural disaster. The thing that drove this point home even deeper was the number of people asking me for advice on what they could do to prepare for the possibility that we are hit by one of the resultant tsunamis. Many thoughts raced through my mind, and...

When you're aiming to set up a scavenger hunt, you might be pondering how much time frame you are committing oneself to. It's a great thought, and one which does not have a single size that matches everyone's resolution. But this unique guideline will furnish the facts you need so that you can figure out just how long implementing a scavenger hunt or clue hunt will take. You might want to be aware of a small amount with regards to which variety of quest you are preparing. Is it a common scave...

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.