Everyone dreams of having super powers. Flying, invisibility, and x-ray vision are popular, but my favorite is fire power! I've always wanted to be Wheeler from the Captain Planet kids show, and now I can with these handheld fireballs of awesomeness. The fireballs burn at a low temperature, so they are safe to hold in your hand and throw (shoot) at imaginary enemies.

In this article I am going to take a look at the Google keyword tool, which is one of many keyword tool programs that you can use to find your keywords.

Following the first part in this series on advanced cracking techniques, we are going to go over how we can intelligently crack passwords using the old-fashioned bruteforce method. These unique cracking techniques aren't widely used, because most crackers are Script Kiddies who have no idea what the concepts are behind cracking passwords, thus, word won't get around too quickly.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

REVENANT n pl. -S one that returns 61 points (11 points without the bingo)

Bingo! No, this isn't the game where balls fly around in machines and players dab their cards with daubers. In a game of Scrabble, bingo refers to the bonus a player receives when emptying their rack in one turn, which gets them an extra 50 points on top of whatever their play was. Even if you had two blanks on your rack and didn't utilize any premium squares on the board, you'd still have an impressive 56-point turn (at least) by using all 7 of your letters.

As Google+ became available to more people, it started running into issues of accounts being suspended due to names that did not sound "real". According to Google+'s community standards, names that users "commonly go by" were encouraged, but not pseudonyms. Those who were using pseudonyms in their Google+ profiles quickly found themselves suspended from using Google+.

Last week, we discussed whether Google should require you to use your real name for Google+ profiles. Google is working on eliminating fake profiles, and in the process, they've booted some real people, including actor +William Shatner. If you find out that your Google+ account has been suspended, you can appeal the suspension and get your profile reinstated.

While a lot of internet threats are rather over-hyped, there are some serious things to be cautious of when going online. Probably the biggest risk to the average internet user is malicious software. Commonly knows as "malware," this term refers to any program that exists solely to do harm. This may include damaging your computer or accessing your data without you knowing. Viruses, trojans, and spyware are all forms of malware. Now, malware can seriously mess up your system, and the idea of s...

What Hand Do I Read - And Why ?This is the first tumbling block for some budding palmists, so let me give you some real begginning tips.

Hi OLers read the following article to gain some great insight into the mischevious advertising ways of food labels. Thanks to the New York Times for this great article below. Happy Eating6 Meaningless Claims on Food LabelsAlthough food labels are supposed to tell us exactly what’s in the food we’re buying, marketers have created a language all their own to make foods sound more healthful than they really are.Today’s “Consumer Ally” column on AOL’s WalletPop site explores misleading food-labe...

Artist Austin Houldsworth of the UK has come up with a device that drastically speeds up the process of fossilisation. Entitled Two Million & 1AD, Houldsworth is capable of creating a fossil in a few months (which otherwise might require thousands of years). Houldsworth is currently experimenting with objects such as a pineapple and phesant, but ultimately hopes to fossilize a human. Houldsworth proposes:

You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.

If you've read Alex Long's last two articles in this series (Part 1 and Part 2), you know by now that making money rarely is risk free, and generally plays out to be a high risk-high gain/loss scenario. The best way to make money is to have money, so for this article, lets assume a financial backing of about $10,000 dollars. For the sake of simplicity, I'm going to be working with online trading systems in this article. Some stocks are traded on exchanges, where buyers meet sellers and decide...

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Sometimes it's easy to get overwhelmed with the sheer scale or complexity of a build or group project on your favorite server. Too much stress from any creative endeavour can lead to mistakes, discouragement, or fighting among a community. What better way to relieve stress and entertain the troops than some old fashioned competition?

Microsoft has had a pretty bad wrap with their Xbox 360 gaming console. Right from the start, the console has suffered a multitude of different hardware failures and design flaws. These problems cause the parts to get too hot and become faulty. I'm sure everyone who's had an Xbox 360 has gotten at least one Red Ring of Death or E74 error.

Halloween will be here in just over a week, which means next week these Scrabble Bingo of the Days will become more horrific. This week, there's just a few relevant Halloween seven-letter words for your Scrabble vocabulary, referencing witchcraft and one of the eeriest horror movies of all time, The Thing (not this year's version).

It's a question I've been pondering a lot lately. Technically, children under the age of 13 are not allowed to join Facebook. But according to a Consumer Reports in May, 7.5 million children 12 and younger are already on the site. Currently, federal law prohibits websites from collecting personal data from children without parental permission. The Children's Online Privacy Protection Act, or COPPA, as it is more commonly known, has been in effect since 1998, but has not been updated since.

There's only a few week left until costumes and candy take over the streets, which means they'll be more and more seven-letter words in the Scrabble Bingo of the Days that relate to the Fall season, horror movies, and of course… Halloween. Below you'll find bingo words relevant such films as Halloween, Children of the Corn and The Wicker Man.

From the onset of the popularization of apps for the iDevice, users have experimented with creating original artwork on their iPhone/iPad/iPod Touch. And when famed British artist David Hockney christened the iDevice with his painterly digital drawings, the trend exploded even more.

For most Americans, the bane of the hangover is typically remedied by lots of water, painkillers, greasy food, and a day wasted on the couch. But if you're tired of potato chips and fried eggs, perhaps it's time you enter unfamiliar territory. Below, a combination of unorthodox methods for taming the beast, derived from science, sparkly Whole Foods new ageism, and the far East.

Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as this list from the Wall Street Journal of the fifty most common passwords gleaned from the 2010 Gawker hack. If your password is on one of those lists, you need to change it. Right now.

If you found the world renown Body Worlds exhibition gnarly and perverse, perhaps you'll find this latest parade of plastination a little less so—considering we don't share the same DNA as these specimens of jerky-in-the-name-of-science. The Koerperwelten der Tiere—or Animal Body Worlds–doesn't showcase preserved corporal matter, but rather 20 odd plastinated mammals, currently on display at the Cologne Zoo in Cologne, Germany.

At the beginning of every class, or almost every class, we do a series of exercises. The Japanese word for this sort of calisthenic exercise isundo. These exercises derive from the Goju style of karate created by Miyagi Sensei in Okinawa in the early part of the 20th Century. In devising these exercises Miyagi no doubt borrowed liberally from the Chinese, whose influence on the southernmost island of the Japanese archipelago was immense.

You're sitting in front of your grandmother's Windows XP machine that has the worst infection you've ever seen. Safe mode? No dice. Restore points? They're compromised. Even worse, all of the files are hidden and none of the executables will run! This leaves her computer in a bricked state. Without some serious CPR, it will be lost to you. Sure, you could just reinstall the system, but then you might lose all of that valuable data.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

Imagine you're in Paris and you need to get to Versailles. Looking around for directions, you come to a cold realization—you do not speak a lick of French! How are you going to get to Versailles and what happens if there is a detour? It will be a difficult struggle, and you'd probably get lost and eventually fail. This is why it's important to know some of the country's language before taking that trip in the first place.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

When you first become interested in learning how to program, it can be difficult to find a place to start. A lot of questions come up, especially if you're new to the idea of programming entirely. After you pick which language you want to learn, you have to worry about how you're going to write the language.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.
Setting up shadows takes just as much time and attention as setting up lights. You can think of all of your illumination as one half of your lighting design, and shadows as the other, equally important half. Shadows can add richness to the tones and shading of your image, tie elements together, and improve your composition. Besides their artistic importance, rendering shadows is a key technical area to master. This chapter will explore both the visual and the technical sides of shadows and oc...

Making your way into an online community can be really exciting. Some life-long friendships and lasting romances begin in humble chat rooms and message boards. But for the novice internet user, one of the biggest hurdles can be trying to figure out just what people are saying to one another.

QI and ZA. QI n pl. -S the vital force that in Chinese thought is inherent in all things

Apple shipped their first batch of iPhone X's with an outdated and unpatched version of iOS. Be sure to check for updates and install iOS 11.1 first thing after you open your new iPhone or it'll be susceptible to the KRACK vulnerability for wireless connectivity.

If you ever need an emergency finger splint for a broken or sprained finger, use a popsicle stick. Wrap medical tape around your broken finger to the side of a popsicle stick until you can receive proper medical attention.

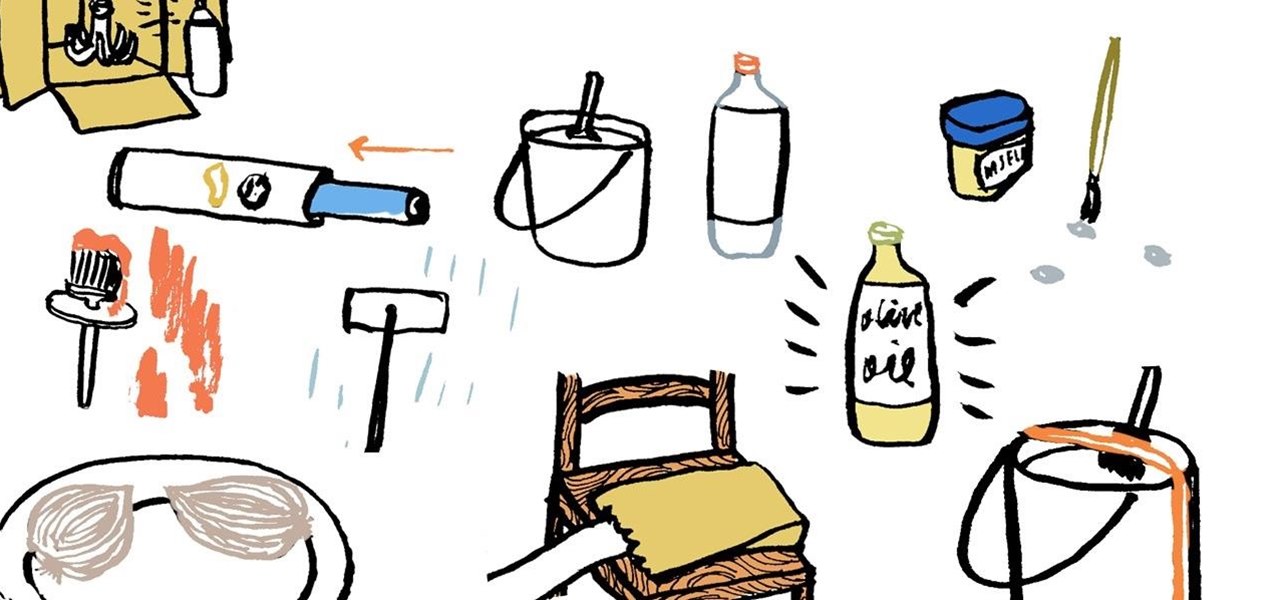
Raw onions are commonly associated with bad breath, but when it comes to wet paint, instead of creating toxic smells they help remove them. If you just painted inside your home, slice a few raw onions in half and place them alongside the walls to absorb noxious fumes. Just make sure to discard onions afterwards, as they would be poisonous.

The lock screen is your friend. It shows you the most basic information (time, date, battery life) and hides your apps and contacts until you wish to access them. But the lock screen is also a great place to open up commonly used apps very quickly. And that's where Shipoopi comes in.

Altruism was first explained as kin selection: "I would lay down my life for two brothers or eight cousins", as J.B.S. Haldane put it.