As a former English major, I have a love/hate relationship with many books. And when I saw that this NFC-enabled charging dock project included a little book mutilation, I was suddenly more interested. Now, for those of you who have nothing against books, this is still a great project to add some style to your tech devices.

It's September 1st, 1859, and the Earth looks more or less like something out of an apocalyptic movie or Sci-Fi novel. All communications have failed, it's so bright outside at midnight that people are getting up and making breakfast, and people all over the world are seeing auroras. The solar storm that produced the electromagnetic pulse and caused all this mayhem is known as the Carrington Event, and storms like it happen about about once every century.
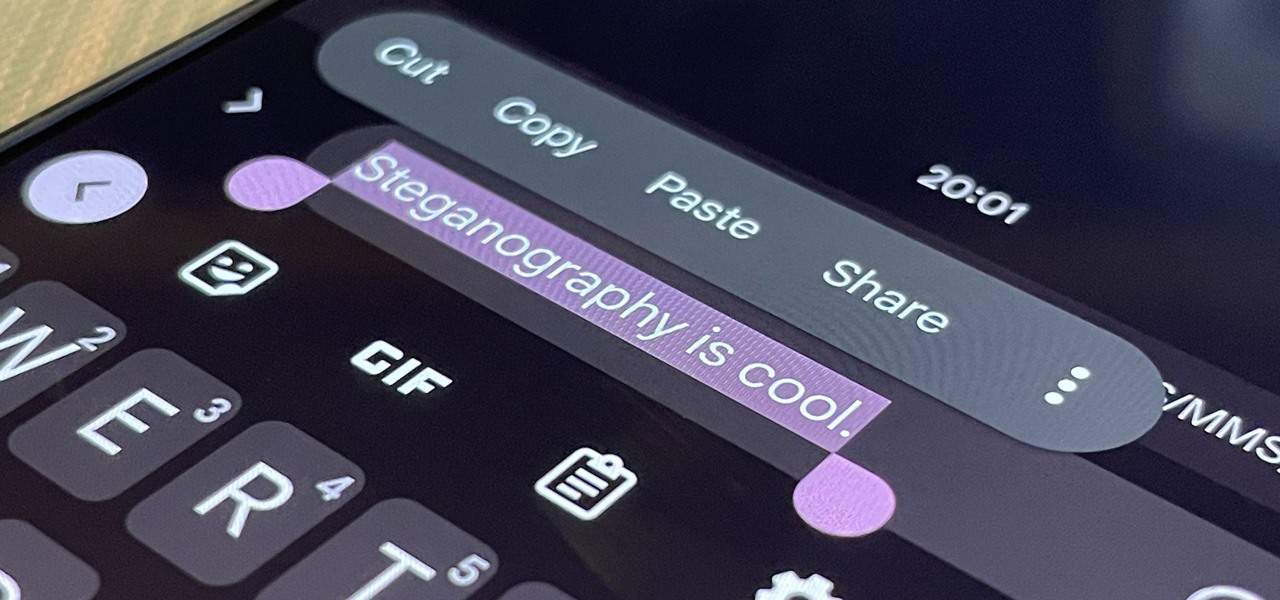
With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser.

I was in college, and my 15-inch Sony Vaio laptop was my prized possession. It was my first PC and probably the most important thing I brought with me to my dorm — it was both how I completed my assignments and my primary source of entertainment. How could it turn its back on me in my time of need?

In this eight minute video the host of the video conveys the methods and techniques that can be used for hacking the "Urban Rivals" video game. By use of Microsoft Word, the host types out the methods that are being used. This typing makes for a clear and easy to understand communication system to the viewers. The first step that is thoroughly explained by the host is simply to make and account. This makes it possible to play Urban Rivals in the first place. Throughout the rest of the video, ...

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

You will hear a million speeches and presentations in your life. It is helpful to know criteria for evaluating them beyond whether or not you liked it. Learn how to evaluate speeches from a professional speaker and communications instructor in this free public speaking video series.

Increasing self awareness helps to improve self esteem. Learn how to improve self awareness from a communications and public speaking expert in this free instructional video series.

Would you like your next speech to be remembered and acted upon by your audience? Learn how to give a conversational speech from professional public speaker and communications instructor Tracy Goodwin in this free video series.

Compliance gaining and resisting is basically getting people to do what you want them to do and not doing what others want you to do. Learn how to gain and resist compliance in this free video series from professional speaker and communications instructor Tracy Goodwin.

What management style is best for you? Each situation can call on a different style. Learn about each style and when to use them from a communications and public speaking expert in the free instructional video series.

A public speaker's credibility is based on their character, competence, ethics and whether or not their audience believes in what they say. Establish credibility as a public speaker with tips from a communications specialist in this free public speaking video series.

Formal business proposals are important for starting up a business or soliciting new business. Learn how to write a successful formal business proposal with tips from a communications and public speaking expert in the free instructional video series.

Breath control is the key to giving a good, clear speech to an audience. Get tips on proper breathing exercises before and during a speech from a communications and public speaking expert in this free instructional video series.

Forming a successful work group is tough but a great way to complete tasks in a shorter amount of time. Learn how to get the most out of a work group from a communications and public speaking expert in this free instructional video series.

Would you like to give a memorable speech for a friend or coworker who is retiring? Learn how to give the speech a colleague will never forget from a communications and public speaking expert in this free instructional video series.

Would you like to give a memorable retirement speech? Learn how to give the speech your coworkers will never forget from a communications expert in this free public speaking video series.

Preparing for a job interview can make or break employment chances. Learn how to prepare for job interviews in this free career advice video from a communications expert.

Getting over a breakup is a difficult thing to do. Learn about dealing with a relationship breakup in this free dating video from a communications expert.

Self disclosure forms friendships with active listening and sharing, telling others about yourself, your thoughts, fears, and goals. Learn how to improve self disclosure and trust in this free communication video series.

Eulogies are speeches or written acclaims of a person given mostly at funerals, but can celebrations of life. Get tips on preparing and giving a eulogy from a communications and public speaking expert in this free instructional video series.

Learn all about body language signals for lying, confidence, flirting, and insecurity and how to read other body language in this free video series on body language communication skills.

After nearly two months of beta testing, Apple is finally pushing the iOS 15.6 software update to all iPhone users. While it's not as feature-rich as the iOS 15.5 or iOS 15.4 that came before it, there are still a few things you'll want to know about it.

Have you ever admired those individuals that get so much accomplished in a day and wonder how the heck they do it? Now's your chance to learn their secrets. The Productivity & Motivation Master Class Bundle brings you everything you need to life-hack your way into leading a more productive lifestyle at home and work.

Cloud computing has come a long way since the days of simple online storage and server networking. Virtually every major company in the world now relies on complex cloud computing infrastructures to reach customers, innovate products, and streamline communications. Their reliance on advanced cloud computing platforms is only going to grow in the coming years.

There's a seemingly endless list of downsides that come with the coronavirus pandemic — ranging from canceled trips abroad and sunny days spent inside to limited communication with friends and family. But one of the undeniable upsides is that there's simply never been a better time to start your own online business since most people will be working from home for the foreseeable future.

While there are many advantages to working from home, properly managing your time can be a real issue. Working remotely requires a particular skill set, including an ability to focus, self-motivate, and communicate from a distance. Thankfully, all of these skills are teachable.

Linux has been one of the most popular desktop operating systems for nearly three decades, ranking fourth in the world behind Windows, macOS, and Google's Chrome OS. The open-source operating system is loved for its quick, powerful, text-based interface and efficient communication tools.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

Ever since Microsoft sunset Windows Phone, they've been working with Android to tap into the growing mobile device market. The tech giant has uploaded over 80 apps to the Play Store for any Android user to download, but some features Samsung has hoarded for themselves.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

In a stunning end-of-year twist to the Magic Leap versus Nreal legal saga, the China-based startup is now filing a motion against Magic Leap.

It wasn't long ago Apple released iOS 13.2 to the masses. The second major update to iOS 13 included 22 new features and changes that added a significant layer of depth to an already feature-filled experience. Apple isn't ready to stop the fun, however, as iOS 13.3, released Dec. 10, has a decent amount of new features too.

When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show.

At Next Reality we mostly focus on augmented reality, but that doesn't mean we're not also absolutely obsessed with virtual reality, too. If the thing that's been keeping you from diving into the deep end of VR has been clunky tethered headsets or the expensive but necessary gaming PCs, then it's time for you to try the Oculus Quest, which is currently available to buy here for less than most gaming systems on the market.