
News: One Drop of Blood Could Save Your Life from Sepsis with New Test
With a death rate of one in five, sepsis is a fast-moving medical nightmare. New testing methods might improve your odds of survival if this infection ever hits you.


With a death rate of one in five, sepsis is a fast-moving medical nightmare. New testing methods might improve your odds of survival if this infection ever hits you.
Forget Waymo, Uber, Tesla, and other other heavily mediatized driverless contenders — German premium carmaker Audi AG has become the first OEM to introduce a Level 3 car sold in retail channels.

Everything from disposed of drugs to hormones and disease-causing bacteria — anything that is rinsed or flushed down the drain — can contaminate wastewater.

The de Blasio Administration of New York City has announced that the NYU Tandon School of Engineering will be hosting the country's first publicly funded VR/AR facility.

The leading platforms enabling augmented reality technology lead our headlines in Market Reality this week.

We fight cancer in a variety of ways, but no matter whether drugs, biologics, or our immune cells are part of the battle, they can do a better job fighting back cancer if we can help them find the tumors.
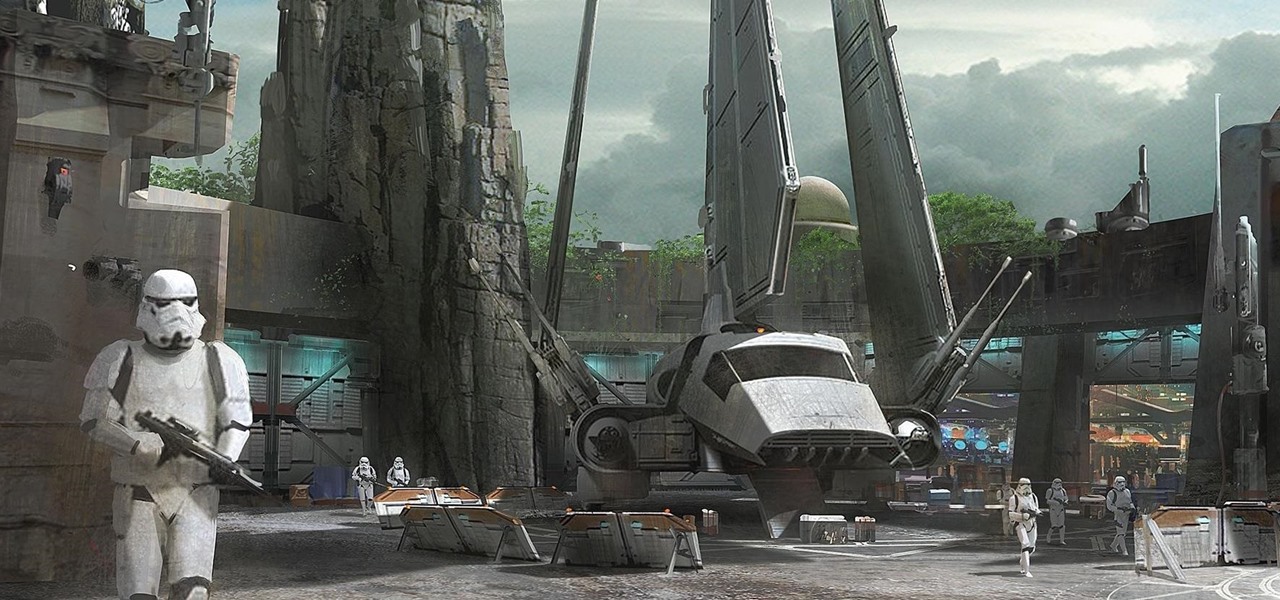
Disney Parks are hard at work bringing the technology from a long time ago in a land far away to life for the opening of Star Wars Land parks in Anaheim and Orlando in 2019.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

It has become hard to decipher where your digital imprint ends and your true self begins in today's tech-dominated world. Scrolling through news feeds and endless updates is not conducive to a good night's sleep, nor does it help you lead a well-balanced life.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

Arsenic occurs naturally in the environment, but it is also one of the most commonly found heavy metals in wastewater, deposited there by inappropriate disposal and arsenical pesticides, for example.

A rose by any other name may smell as sweet, but one annoying invasive weed may hold the answer to treating the superbug MRSA. Researchers from Emory University have found that the red berries of the Brazilian peppertree contain a compound that turns off a gene vital to the drug-resistance process.

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

Lighthouses and signal fires may have been the first social media. Without the ability to share language, a distant light meant "humans here." A new study from the University of California, San Diego, finds that bacteria can also send out a universal sign to attract the attention of their own, and other bacterial species.

One thousand feet under the ground, extremophile microbes that have not seen the light of day for four million years are giving up some fascinating facts to scientists who go the distance.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

The end of a weekend can be depressing knowing just how bad Monday morning will be when you get back to work, but that feeling is tenfold when coming back from a lengthy vacation with zero work responsibilities.

Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect something new and exciting practically every week.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.
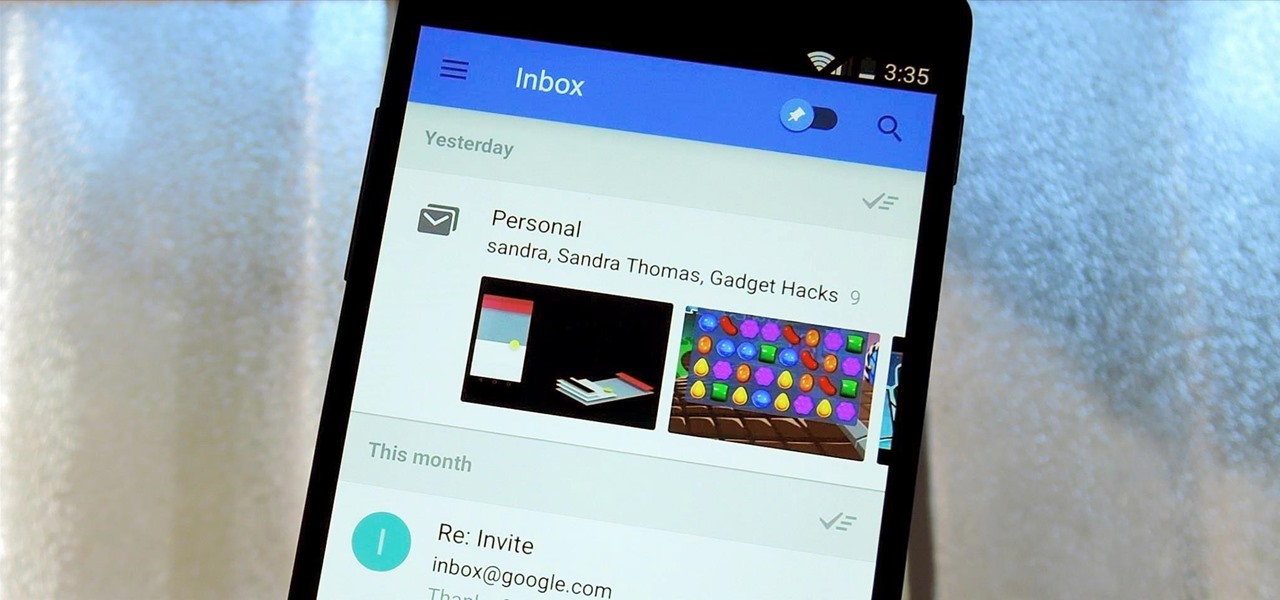
Google's new Inbox by Gmail service wants to fundamentally change the way you handle email, so a bit of a learning curve is to be expected when you're first using the utility. As of right now, the service is invite-only, but if you were lucky enough to get in on the ground floor, you're probably wondering, "How the heck do I use this thing?"

Emojis have transformed the way we laugh and cry, tell stories, give responses, and express excitement to get a drink after work — without any actual text required. Heck, in an incredibly meta move, the Oxford Dictionary even named the "Face with Tears of Joy" emoji as their word of the year at one point. So how could you not want to be an emoji character for Halloween? Emojis are everywhere. The ubiquitous symbols are already on smartphones, tablets, and social networks, so why not help them...

Complete silence or a non-stop Pandora playlist? People are often divided on what type of work environment they prefer. Whether you're a frequent loud music listener or you can't stand any kind of background noise, chances are you're pretty set in your ways.

If you've read any health news in the past year or so, you've probably been bombarded with headlines announcing that frequent sitters face certain death, even when you're just relaxing and watching TV at home.

If browsing speed is important to you—and it should be—you'll probably be interested to know that there are ten simple flag modifications you can make in Google Chrome in order to achieve the fastest browsing speed possible.

This is evil and it destroys people. Let's just get that out of the way. Nonetheless, suppose you need to make someone distrust their own memory and perception of reality. Suppose you want someone to believe in you more than they believe in themselves.
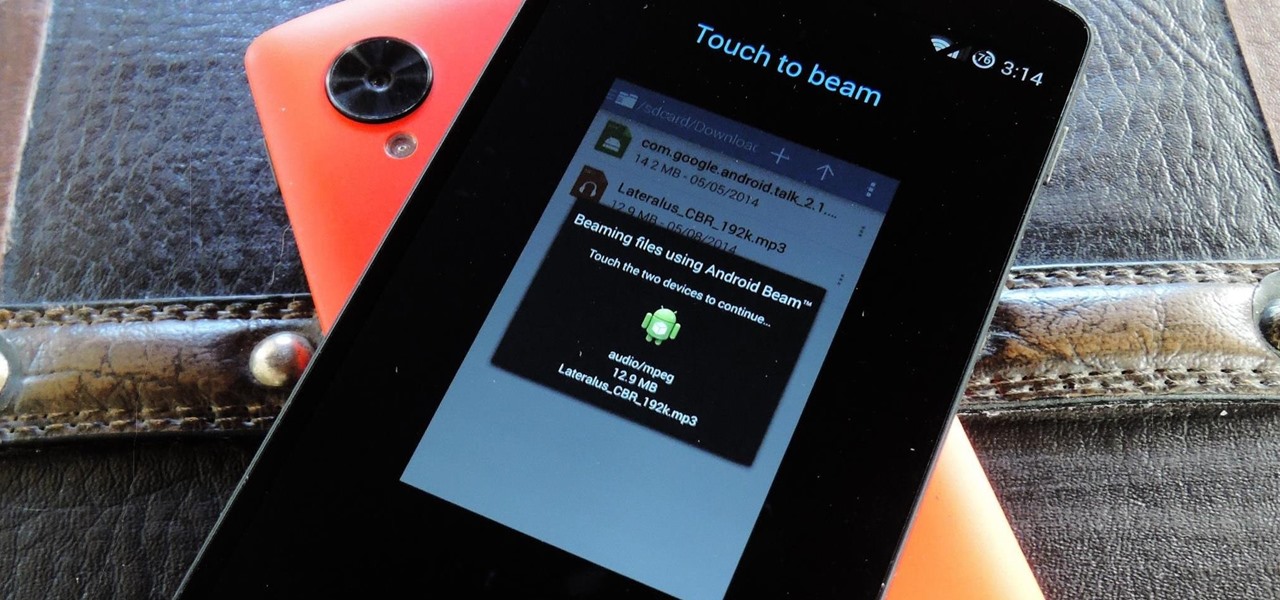
Your Nexus 5 comes with a pretty cool feature baked in called Android Beam. Using NFC, or Near Field Communication, this functionality allows you to send information to another compatible device by simply touching the two together. Most flagship devices have NFC built into them these days, so there is a broad range of devices that your Nexus 5 is capable of sharing information with wirelessly.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.
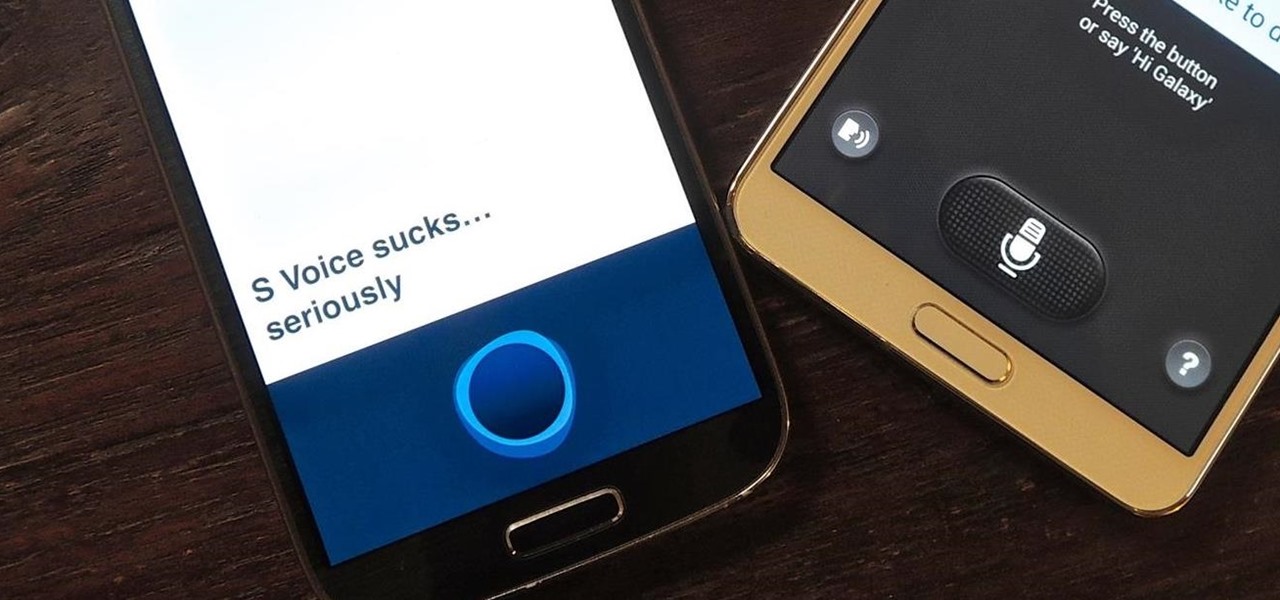
One feature of Samsung devices that's less useful than I had expected is S Voice, the voice assistant that ships with all new Galaxy devices. The voice is annoying, the features are lacking, and it's an all around subpar product. With Google Now, Siri, and now Microsoft's Cortana, Samsung needs to really step up their game—even on the new Galaxy S5.
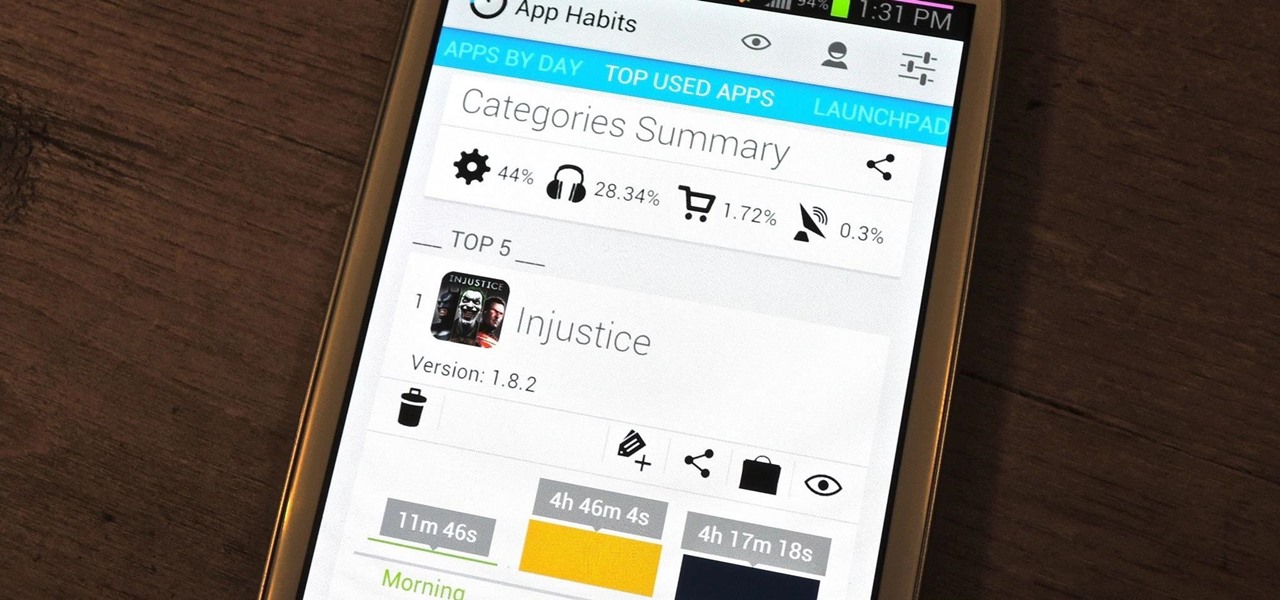
In today's dog-eat-dog world, every minute matters. Whether you're in school or working for the Man, a huge amount of your day is consumed by tasks, assignments, and other kinds of work. Then there's the time you spend playing video games, watching TV, or screwing around on your Samsung Galaxy S3.

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

With this article, I'll be continuing the series I started with my recent plague doctor article. That is, examining tropes that may at first appear to not fit into Steampunk.

Getting over a breakup is a difficult thing to do. Learn about dealing with a relationship breakup in this free dating video from a communications expert.