
How To: Teach your dog to be caught when loose
Dog trainer Emily Larlham of Dogmantics, goes over some good clues on how to grab your dog when it's running around loose.


Dog trainer Emily Larlham of Dogmantics, goes over some good clues on how to grab your dog when it's running around loose.

From Dogmantics, dog trainer Emily Larlham visits pitbull specialist, Jessica Wheatcraft to get some tips on how to understand and train your pitbull. .

Dogs are smart. We don't need to punish them every time they don't do a trick. Through positive reinforcement training, dogs can learn almost anything. From Dogmantics, dog trainer Emily Larlham shows a few tricks she taught her dog!

From Dogmantics, dog trainer Emily Larlham gives a us tips on how to get your doggy to stop barking. By first changing your dog's emotional response to the stimuli, then working from low levels of criteria to higher levels, then finally, adding full criteria you're dog will get comfortable around the bark-worthy source and remain calm.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Answer “Why should we hire you?” in a job interview John Heaney from The Job Shopper discusses how to handle one of the toughest questions you will face in a job interview: “Why should we hire you?”

Interested in chakras? Boost the seven energy centers from the base of your spine to the top of your head for optimum health and vitality. Learn how to awaken chakras with help from this video.

Having trouble coping with the fact your son picked a less than stellar choice to marry? Not too fond of your son’s taste in women? That’s his problem; don’t make it yours.

As Shakespeare said, "All the world’s a stage" – step on up and play your part! You Will Need

Discovering your partner's affair can be devastating, but it doesn't have to mean the end of the relationship.

Communication is a two-way street that will quickly become a dead end if no one is actually listening.
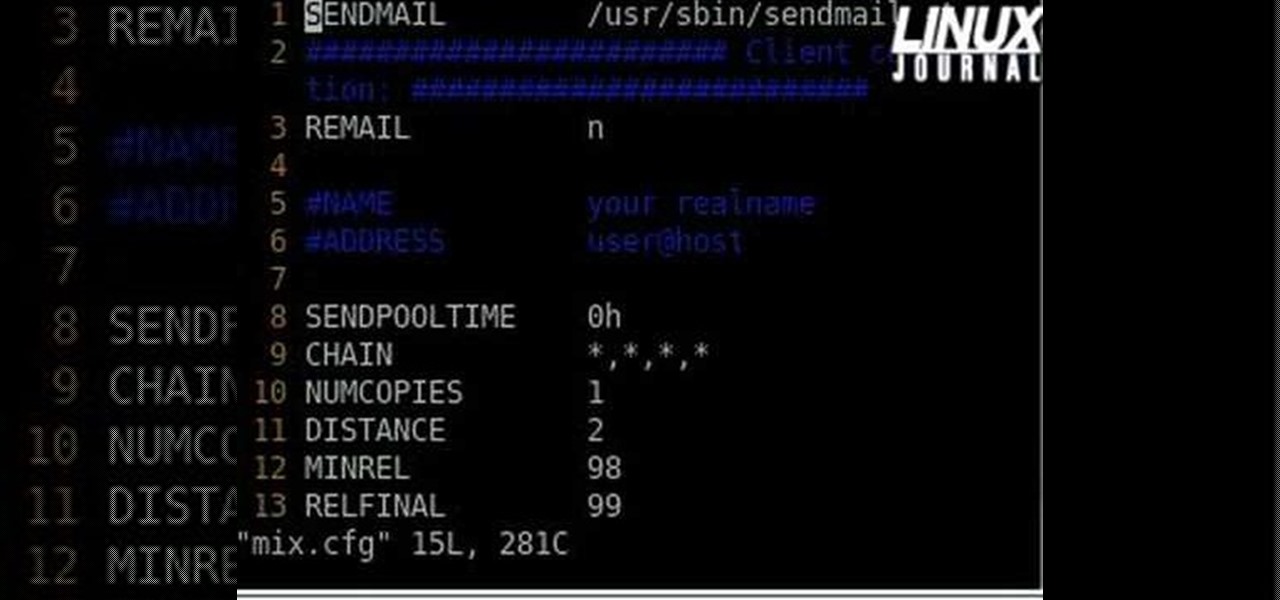
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.
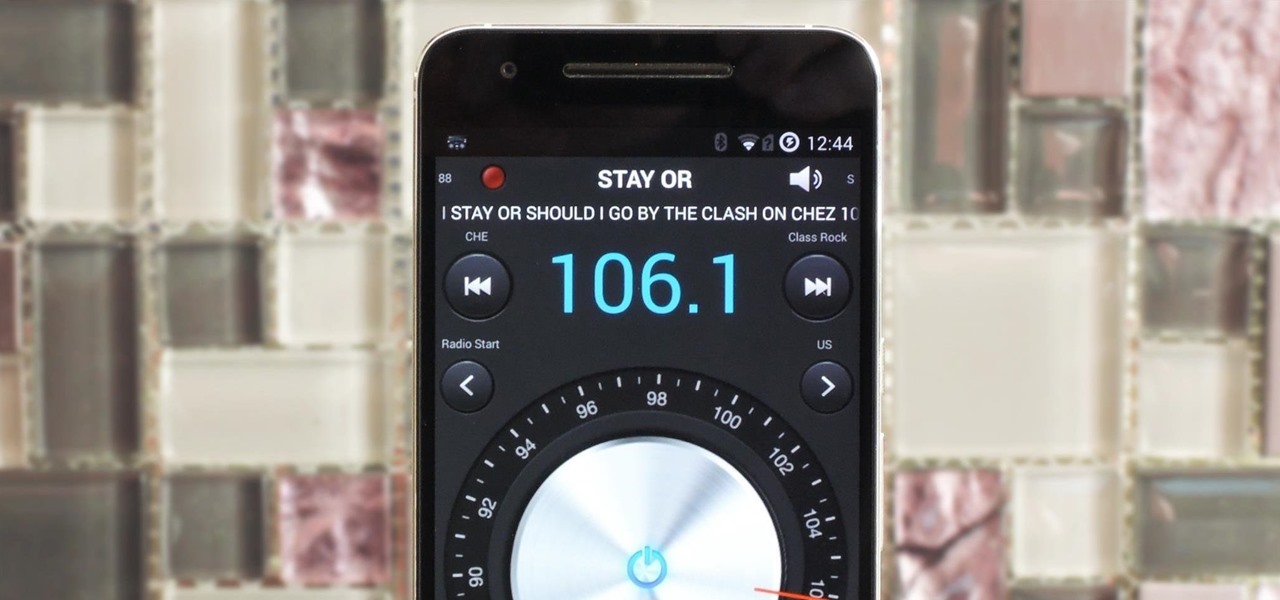
Android smartphones have all sorts of connectivity chips built in, including Bluetooth, Wi-Fi, GPS, NFC, and mobile data. But what about AM or FM radio, two of the most common methods of wireless communication?

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

E-mails has become an everyday medium of communication, but rules and etiquette still apply. Learn e-mail etiquette and popular e-mail features in this free communications video.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

Google is on a mission to bring a better messaging experience to Android users. We've seen them try and fail over the years with various messenger apps, but this time, they're taking a different approach by working with industry leaders to create a new messaging standard. The result is RCS Universal Profile, or simply Chat, and it's finally catching on.

This video is about combining Microsoft Project 2010 and SharePoint 2010. This combination helps project teams to collaborate and share project information. Information can be displayed on a dashboard. We will also discuss various levels of project management such as starting the project, planning, tracking and reporting on the projects progress.

After nearly two months of beta testing, Apple is finally pushing the iOS 15.6 software update to all iPhone users. While it's not as feature-rich as the iOS 15.5 or iOS 15.4 that came before it, there are still a few things you'll want to know about it.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Because it takes two to tango, your dancing Bitmoji World Lens on Snapchat is getting a dance partner.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

As you already know, Hong Hong has been rocked in recent weeks by protests against their Beijing overlords. Promised free and fair elections, Beijing has reneged on this promise and is now telling Hong Kongians (that's what they're called, aren't they?) that they will only be able to vote on Beijing-selected candidates. All that is interesting from a political perspective, but from a technological perspective, the more intriguing story is how the protesters are communicating. Faced with their...

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.
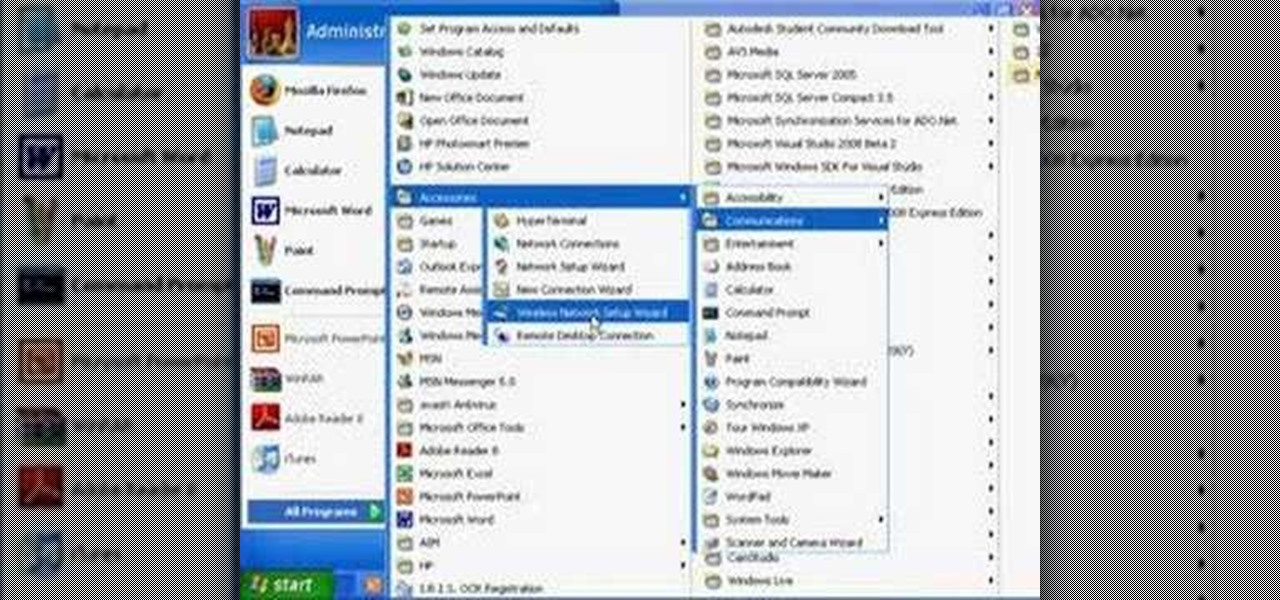
Wartex8 demonstrates how to use remote desktop in Windows XP. Remote Desktop is a useful utility that you can use to control another computer and its applications.The necessary steps that are adopted to activate remote desktop are:1) Right click on my computer icon (either the icon on the desktop or the one on the start menu list) and select properties, and a new dialog box called system properties will pop up on the window.2) In the System Properties, select the computer name tab and write d...

Stuttering is a communication disorder affecting over 3 million Americans. Stuttering can make school and other social interactions difficult. Although there are no instant cures, these tips will help your progression toward speech fluency.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

Welcome back, my greenhorn hackers!

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Just months after we previewed the augmented reality, volumetric video conferencing powers of Mimesys, the company has undergone a major change — it's now a part of Magic Leap.

I was in college, and my 15-inch Sony Vaio laptop was my prized possession. It was my first PC and probably the most important thing I brought with me to my dorm — it was both how I completed my assignments and my primary source of entertainment. How could it turn its back on me in my time of need?
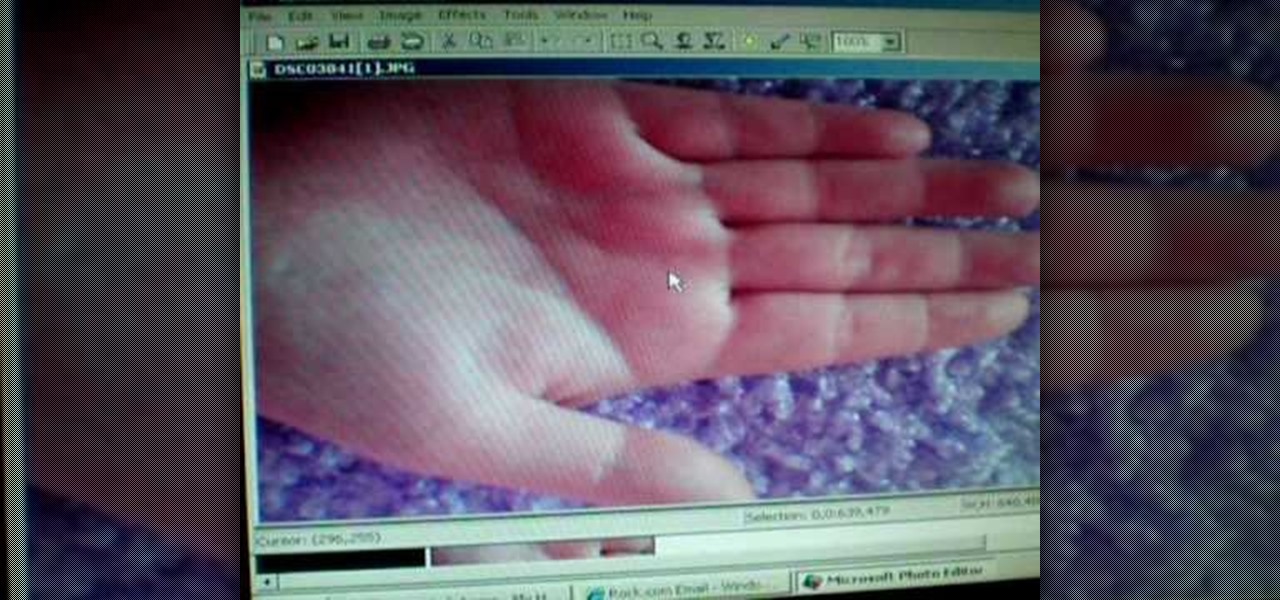
Peter John, an accomplished expert in palmistry, demonstrates how to properly understand what it means when your palm reading subject has a long hand and long lines on the palm. He indicates what to look for to indicate intelligence and good communication skills in your subject.

In this video,examine the differences between wolves and the dog as it relates to human-to-canine communication.

Deaf people primarily communicate through sign language, so understanding spoken languages can prove challenging. To bridge that gap in communication, the HoloHear team built a mixed reality app at a Microsoft HoloLens Hackathon in San Fransisco that translates the spoken word into sign language.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Air New Zealand is looking for a spokesperson for the Antarctica: No Ordinary Place, No Ordinary Assignment project, a two-week adventure in Antarctica, where the chosen candidate will join National Geographic photographer Jason Edwards to document environmental issues and important research being conducted by research teams sponsored by Air New Zealand and Antarctica New Zealand.

Japan is in the process of curbing its aging population and mature workforce. According to The Diplomat, the country's population has been declining at a steady rate. To meet future productivity demands in commercial and industrial sectors, local officials are turning to self-driving technology, including truck platooning, where three or five vehicles travel autonomously in a string formation. This practice, according to a study by MIT, can reduce fuel consumption by up to 20% (more about thi...