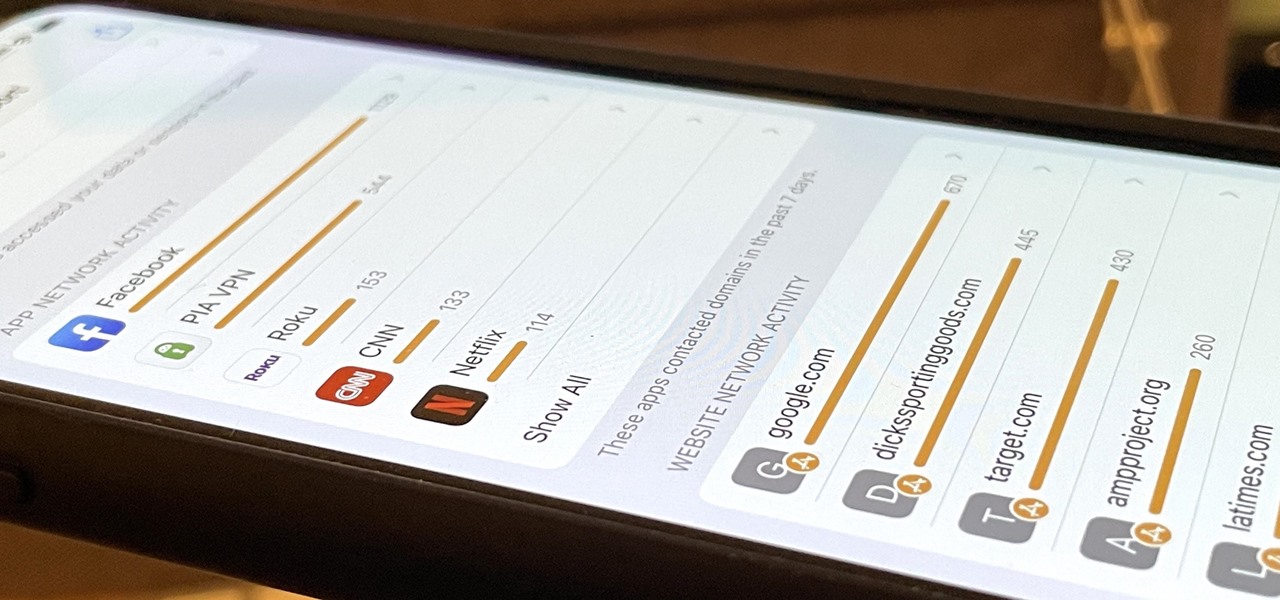
As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Augmented and mixed reality developer Arvizio is working on a suite of software solutions for enterprises that will extend HoloLens capabilities as a full-fledged collaboration and conferencing tool. The company will demonstrate its Mixed Reality Studio suite to attendees at the Augmented World Expo, which begins later this month in Santa Clara, California.

Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.

Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst of data two inches away without having any measurable impact on your battery life.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

While new features in Safari, Camera, Photos, Notes, Weather, Messages, and other Apple apps may steal the show on iOS 17, there are some impressive new features you need to know about when it comes to FaceTime audio and video calls.

With the holidays right around the corner, it's easy to miss a big software update on your iPhone, and by that, I mean iOS 15.2, which was pushed out Monday, Dec. 13. There's a surprising amount of new features and changes in the updated firmware, and there are a few big ones you need to know about.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

It wasn't long ago Apple released iOS 13.2 to the masses. The second major update to iOS 13 included 22 new features and changes that added a significant layer of depth to an already feature-filled experience. Apple isn't ready to stop the fun, however, as iOS 13.3, released Dec. 10, has a decent amount of new features too.

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

Thanks to its encrypted messaging, WhatsApp can be a platform for secure communication with friends and family. One drawback, however, is that the app would let anyone add you to a group chat, regardless of if you approved it or not. This lack of control over your own account is over, as WhatsApp now lets you decide who can add you to a group chat.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

We've shown you the best augmented reality headsets, and now it's time to show you the rest. These are the AR headsets you've probably never heard of or even seen. The AR headsets that, in some cases, have a shot at the big time, and may one day reach widespread adoption, and, in other cases, are unwieldily contraptions that look like something out of a weird science fiction movie.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

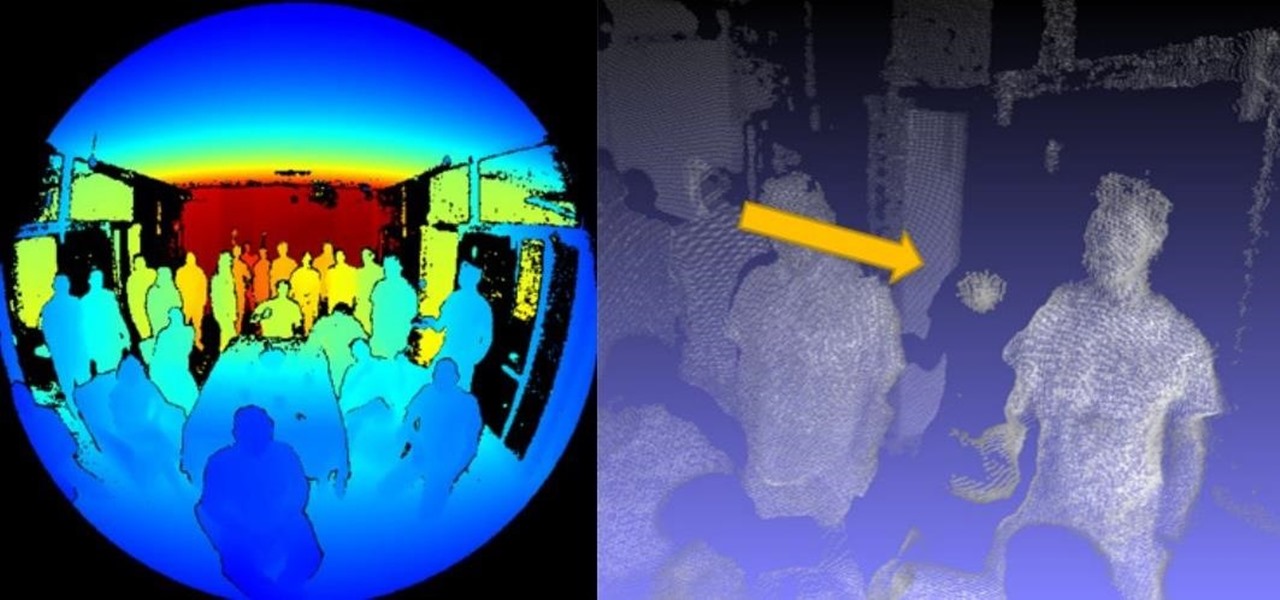
Images captured by Microsoft's next generation Kinect depth-sensing camera that will facilitate augmented reality experiences in the next version of the HoloLens and give computer vision to untold multitudes of connected devices in enterprise facilities, have made their way into the wild.

While Apple has generally been more bullish on augmented reality as opposed to virtual reality, the latest whispers about its purported AR headset suggests that it may be giving VR another look.

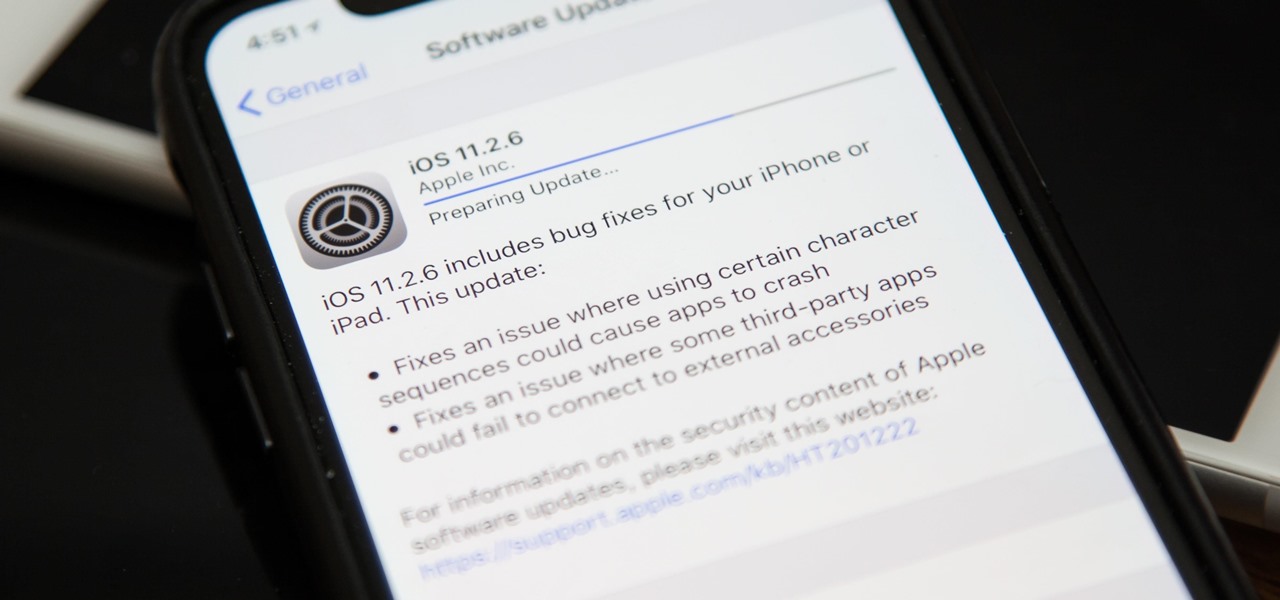
Apple released the official iOS 11.2.6 update Monday for iPhones, which comes just under four weeks after Apple pushed iOS 11.2.5 to users. This latest update was released off Apple's normal release schedule to quickly patch the "Telugu" character bug that causes erratic behavior when viewed in apps.

Lost among the latest laptops, smart assistants, VR headsets, and Motorola-branded gadgets that it brought to CES 2018, Lenovo has also introduced a new pair of augmented reality smartglasses.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Razer took to the stage this month to unveil their new flagship phone, fittingly called the Razer Phone. The device is targeted at gamers, but has a list of specs that make it an intriguing daily driver for any user. Its headlining feature is an 120 Hz IGZO display, the first of its kind in a flagship smartphone released in the US. Tonight, Razer officially opened up orders for the new phone on their website.

Lenovo has partnered with Wikitude to develop a cloud-based platform for delivering industrial-focused augmented reality content, the companies announced at the Augmented World Expo today in Santa Clara, California.

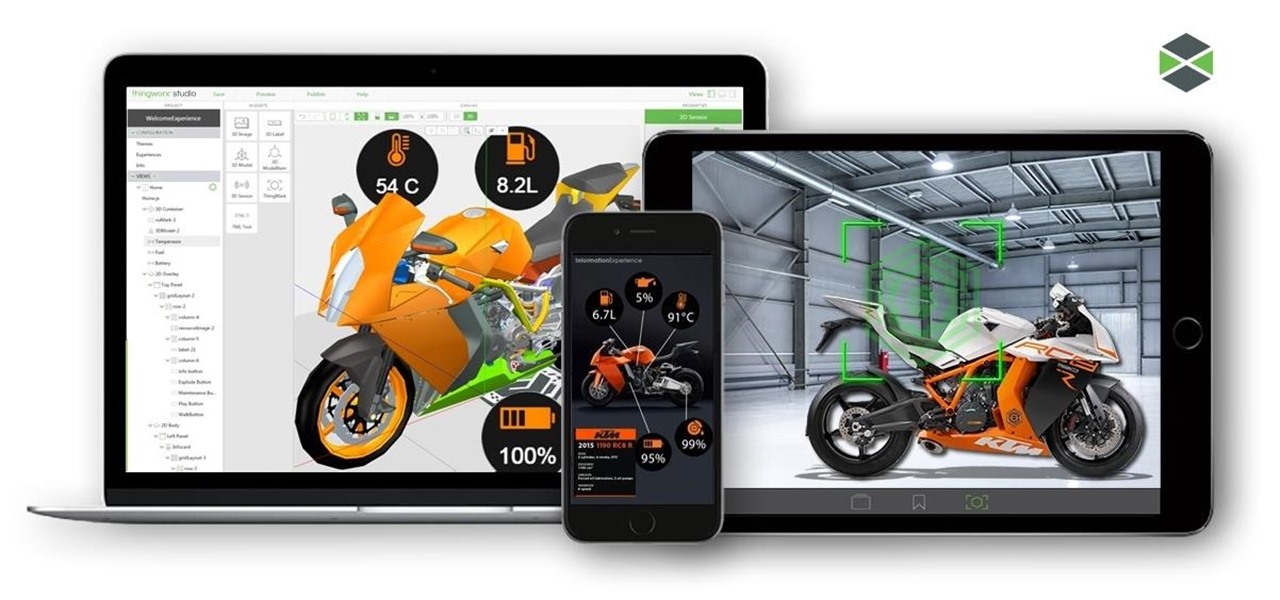
For companies wary of the temperature, PTC just made it easier for them to dip their toes in the waters of augmented reality.

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

Imagine wearing your HoloLens, then reaching out to touch a hologram and actually feeling it. Mind blown, right?! Now imagine that same hologram responding to your touch. I don't mean in the way holograms currently respond to an air tap, but a much more refined and precise touch. Maybe you touch a character on the shoulder and it turns around to see you, or maybe you hit a button in the air and it reacts accordingly.

The next generation in mobile communications has officially arrived. A new "Universal Profile" was just published to help carriers and OEMs enable Rich Communication Services (RCS) on any of their smartphones, and the standard hopes to replace SMS with a feature-rich, iMessage-like experience on all phones.

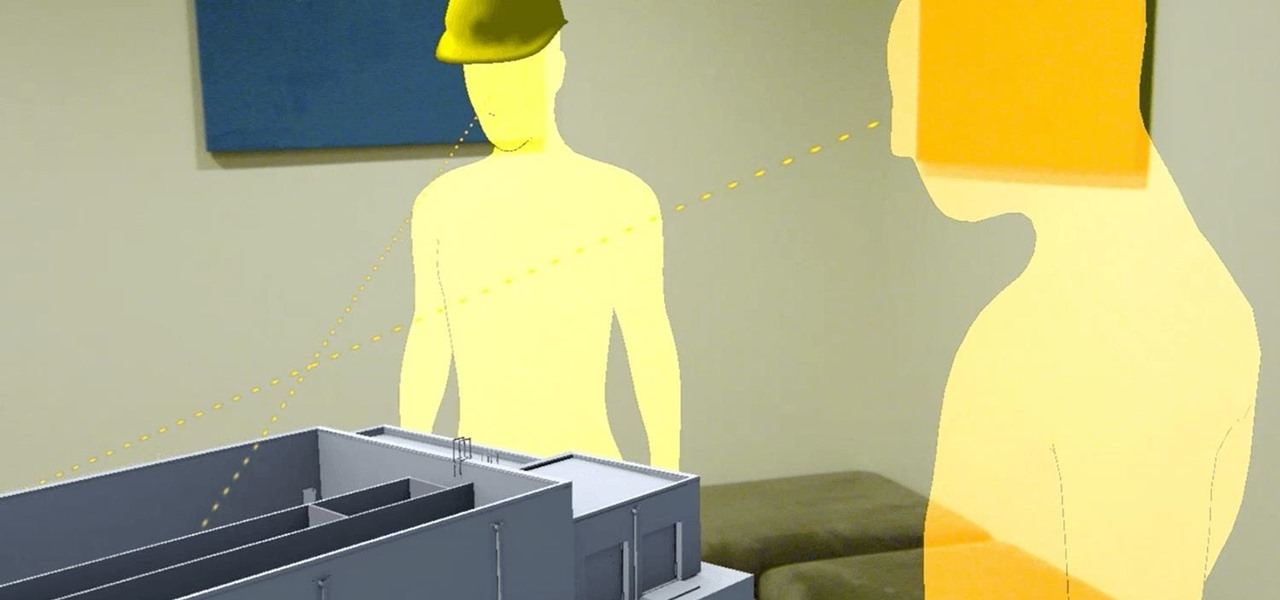
With developers already figuring out how to use the HoloLens for home improvement tasks, it's no surprise that the device has greater applications in construction. Tech blog Digital Trends points out that holograms are a natural evolution of the blueprint, and several other aspects of construction work.

Snapchat began rolling out a massive update on March 29th, dubbed Chat 2.0, that gives users a plethora of new features, basically transforming Snapchat into an all-purpose messaging app.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

If you've read any health news in the past year or so, you've probably been bombarded with headlines announcing that frequent sitters face certain death, even when you're just relaxing and watching TV at home.

Who needs to talk to a girl when you can just text them? I mean, am I right? There's even a movie about a guy who falls in love with a girl inside his cell phone (and it actually looks pretty good too). For all you clowns, the girl is not actually inside of his phone.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

Facebook has been revamping its Messenger apps these past few months, trying to lure in more users. Competing in an already crowded market of third-party messaging applications, Facebook Messenger just upped the ante, by introducing voice messaging.

Have a super secret spy communication you'd like to send out, but don't have the funds to hire your own trusted operatives to deliver the message? Then stick to what you're used to—email it. SafeGmail is a browser extension that allows you to send encrypted emails right through your regular Gmail account. While this may seem a bit unnecessary for most messages, encrypting your email can definitely be useful.

If you have an iPhone or iPad, but use a Google account for most of your communication, syncing your contacts just got a lot easier. Google recently announced that they added CardDAV support, an open protocol that lets you seamlessly integrate Google Contacts into other services. Google states that "Syncing via CardDAV is only available over SSL for Apple devices on iOS version 5.0 and above." So, if you're running an older iOS version, you'll have to use Google Sync instead.

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...