One can easily get rid of acne scars without surgery by means of following steps. Identify the type of acne scars you have. See a dermatologist who can tell the difference between types of scars. For example, scars may be classified as ice pick, boxing, rolling or hypertrophy scars. Not every nonsurgical removal techniques will work with each type of scar. Get a chemical peel. A solution is applied to the skin which causes the top layer to peel off. This encourages new skin growth. Peels are ...

Dyeing your hair is a great way to change your look. But if you don't do it right, the results can be pretty ghastly. If you seek a new do without the harsh chemicals, these steps will give you the locks you’ve been looking for.

You will hear a million speeches and presentations in your life. It is helpful to know criteria for evaluating them beyond whether or not you liked it. Learn how to evaluate speeches from a professional speaker and communications instructor in this free public speaking video series.

Increasing self awareness helps to improve self esteem. Learn how to improve self awareness from a communications and public speaking expert in this free instructional video series.

Would you like your next speech to be remembered and acted upon by your audience? Learn how to give a conversational speech from professional public speaker and communications instructor Tracy Goodwin in this free video series.

Compliance gaining and resisting is basically getting people to do what you want them to do and not doing what others want you to do. Learn how to gain and resist compliance in this free video series from professional speaker and communications instructor Tracy Goodwin.

What management style is best for you? Each situation can call on a different style. Learn about each style and when to use them from a communications and public speaking expert in the free instructional video series.

A public speaker's credibility is based on their character, competence, ethics and whether or not their audience believes in what they say. Establish credibility as a public speaker with tips from a communications specialist in this free public speaking video series.

Formal business proposals are important for starting up a business or soliciting new business. Learn how to write a successful formal business proposal with tips from a communications and public speaking expert in the free instructional video series.

Breath control is the key to giving a good, clear speech to an audience. Get tips on proper breathing exercises before and during a speech from a communications and public speaking expert in this free instructional video series.

Forming a successful work group is tough but a great way to complete tasks in a shorter amount of time. Learn how to get the most out of a work group from a communications and public speaking expert in this free instructional video series.

Would you like to give a memorable speech for a friend or coworker who is retiring? Learn how to give the speech a colleague will never forget from a communications and public speaking expert in this free instructional video series.

Would you like to give a memorable retirement speech? Learn how to give the speech your coworkers will never forget from a communications expert in this free public speaking video series.

Preparing for a job interview can make or break employment chances. Learn how to prepare for job interviews in this free career advice video from a communications expert.

You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering... how would someone take down the Internet? Could they even do it?

MATLAB, an acronym for "matrix laboratory," was created over 40 years ago to service the applied mathematics community. The powerful programming language now has over four million users worldwide and is of particular import to engineers, scientists, and economists.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

Not that long ago, touchscreen-friendly gloves were an outlier accessory, something you had to track down at a specialty brick-and-mortar store or solely online. But as the smartphone has become an integral part of our lives, so, too, has the need for fashion accessories that cater to our desire to be always connected. So now, touchscreen gloves are everywhere.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Apple often cites its tight integration of hardware and software for its success. Startup Illumix is looking to do the same thing for AR gaming by building an AR platform for its apps.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

With their first attempt at the mobile market, Razer introduced a device that looks at the smartphone differently. Instead of focusing on minimal bezels or an amazing camera, Razer decided to make a phone for gamers. So how could Razer target the growing mobile gaming market, which is projected to generate $40.6 billion in global revenue in 2017? It starts with the IGZO LCD Display.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

In order for software developers to do their jobs as new hardware reaches the market, they will need the right tools to get their projects off the ground and into augmented and mixed reality devices. There have been completely new approaches to development when it comes to AR and MR, and these are some of the faces behind them.

The world of investment and finance can be labyrinthine in its very nature — and even more complicated in regards to augmented and mixed reality. While these new emergent technologies are teeming with explosive levels of unrealized potential, there's still a big layer of uncertainty in terms of return — but these investors aren't afraid to take the leap.

Our quest to find novel compounds in nature that we can use against human diseases —a process called bioprospecting — has led a research team to a small frog found in India. From the skin slime of the colorful Hydrophylax bahuvistara, researchers reported finding a peptide — a small piece of protein — that can destroy many strains of human flu and can even protect mice against the flu.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

As someone who's dependent on glasses to see on an everyday basis, losing or misplacing them is obviously a bad thing. I can't even see clearly enough to find the glasses that I just lost, so I'm pretty much blind now.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

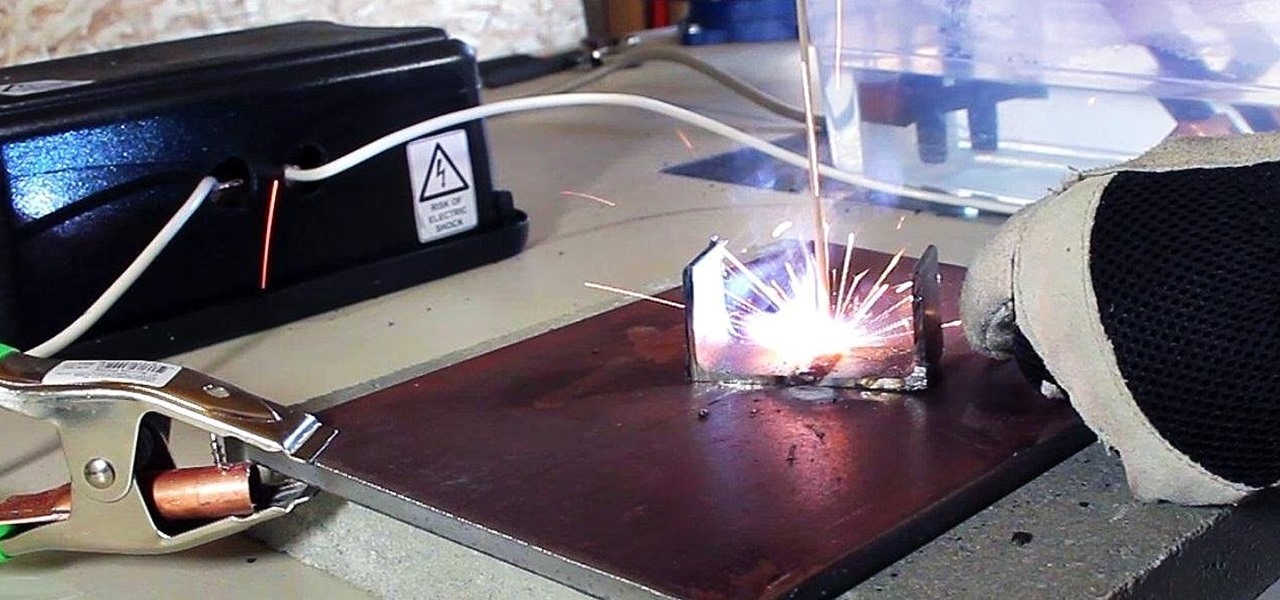
In a previous article, I demonstrated an Arc Welder made using parts from old microwave ovens. Video: .

The best part about April Fool's Day is that everyone is fair game. Even big tech companies like Google and Twitter get in on the action every year. It encourages even the most uptight, unfunny party-poopers among us to have a little fun driving each other crazy with pranks — even at work.

Not that long ago I wrote an article discussing what it would be like, realistically, if you were to accidentally travel back in time to the Victorian era. At the end of that article, I mentioned that the best thing you could bring with you on a time-traveling adventure is a Kindle, or similar e-reader, stuffed full of the knowledge of the 21st century. Why a Kindle? Well, I own a Kindle, and I love it. However, there's far more to it than that.

Stand out from the high street fashion clones with stuff you’ve fashioned yourself. It’s easy to take old pieces of electronic junk and transform them into all sorts of fun ‘n’ funky geeky accessories. Like a totally useful tote bag, a what-on-earth-is-that wallet and a bedazzling belt. It’s terribly geeky but chicy too. Here’s how…

Tired of static cling? You can make your very own dryer balls that will prevent your clothes from having static clean and it only takes some yarn and pantyhose. You can even make scented dryer balls using this method.