Air New Zealand is looking for a spokesperson for the Antarctica: No Ordinary Place, No Ordinary Assignment project, a two-week adventure in Antarctica, where the chosen candidate will join National Geographic photographer Jason Edwards to document environmental issues and important research being conducted by research teams sponsored by Air New Zealand and Antarctica New Zealand.

Looking to transmit some super-secret audio communications to your other spy buddies? A laser is the perfect tool for getting your sounds heard from a small distance—without anyone intercepting them— even if it's just a cover of your favorite pop song. A laser audio transmitter uses light rather than radio waves to transmit sound. This is a much more secure way to send audio communications because the laser is a focused beam of light, whereas radio waves are not controlled, so they can be pic...
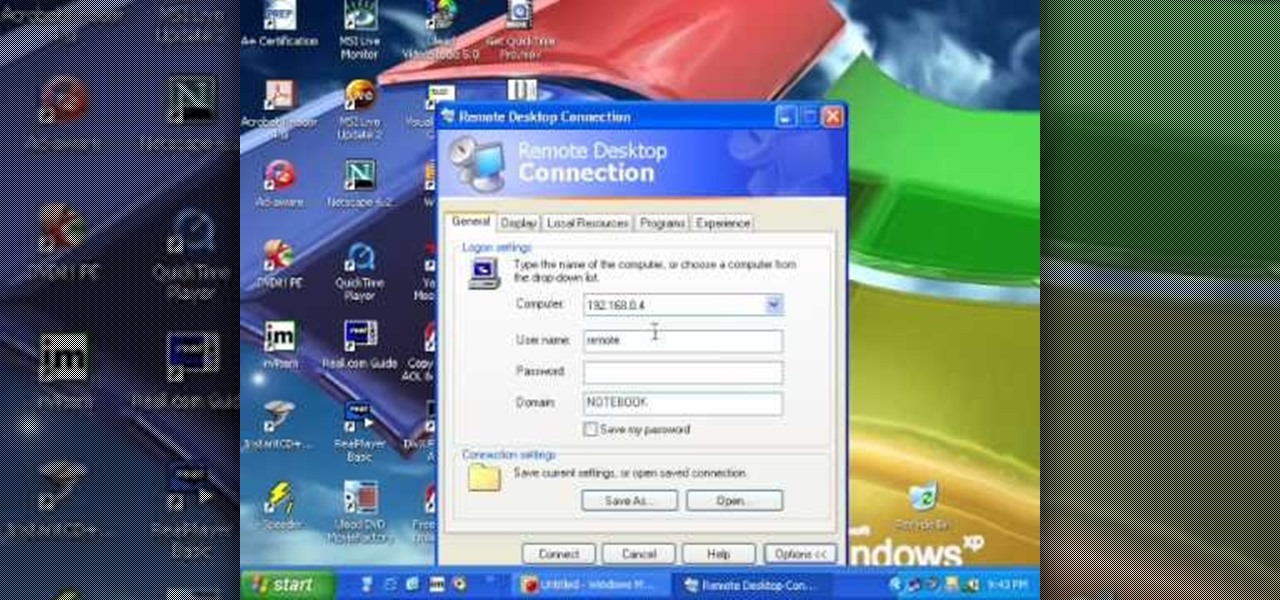
This video from Michael presents how to establish a Remote Desktop connection in Windows XP Professional.This type of connection allows you to access your computer via Internet from any place and manage files, local resources, or perform any other remote activity.To establish Remote Desktop connection click Start button, right click My Computer, from the opened menu select Properties. System Properties window will open. Choose Remote tab. Check Remote Desktop - Allow users to remotely connect...

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

There is only one chance to make a first impression. Learn the many facets of non-verbal communication and how it affects everyday life from a communications and public speaking expert in this free relationship building video series.

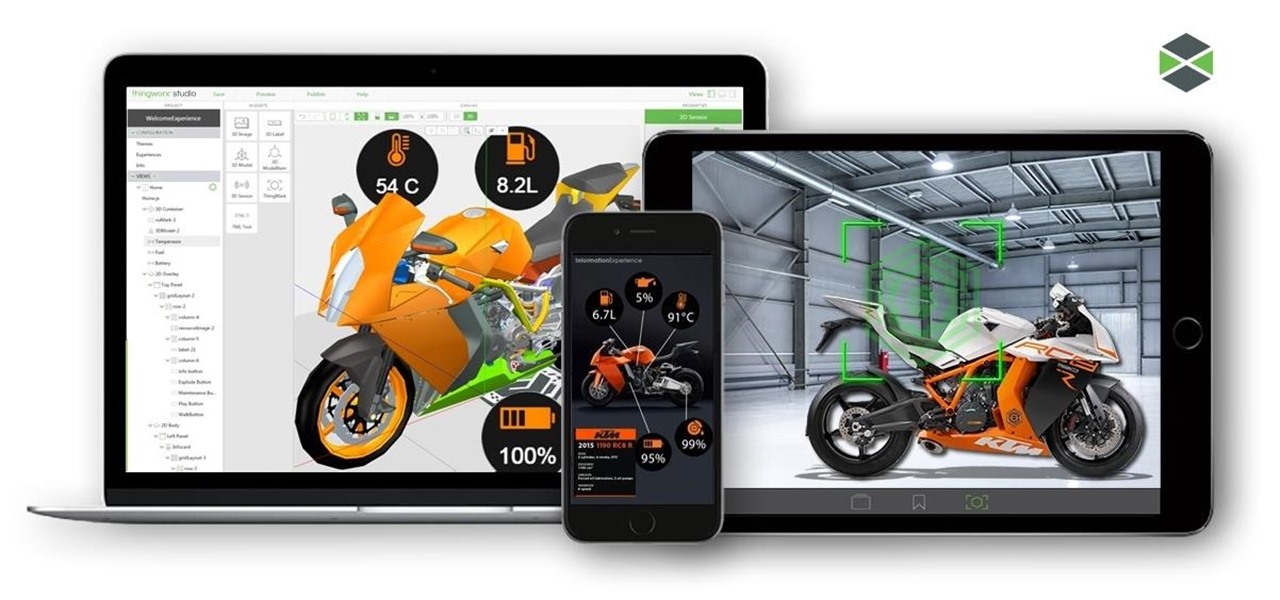
The Visual Prototyper is a wireframe design solution that allows you to design a fully functional application wireframe and simulate it.

Learn how to give an impromptu speech with expert tips on speech, communications, and etiquette in this free public speaking video.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

In recent years, the US military has been utilizing augmented reality as a training tool, giving officers and soldiers an opportunity to train and hone their decision-making, tactical efforts, and weapons accuracy via virtual scenarios.

Until self-driving cars become mainstream, augmented reality might be the next big technology to hit your dashboard.

When it comes to augmented reality smartglasses, for now, it's still a mostly enterprise world, since the form and function of most are more acceptable on a job site versus your local cafe, and the still high price tags are far more palatable to major companies rather than individuals.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

Communication is the key to any healthy relationship, and when I say any, I mean human and non-human. Previously, one of the biggest culprits for not understanding what you meant was Siri, but now it looks like it has some competition with the new Kinect system, which can control practically everything on your Xbox One—if it can understand you.

Making little robots with a LEGO Mindstorms NXT set is already cool, but putting one underwater? Now that's just crazy. That didn't stop this engineer, who built a LEGO submarine that can not only maneuver around his fish tank, but can also be remotely controlled with his Xbox controller. The craft has a sealed battery compartment, exposed Power Functions motors, and features real-time communication between it and a laptop using a NXTbee wireless module.

A lack of good communication is the cause of many relationship problems. Learn about communications barriers in relationships in this free video from an expert on interpersonal communication.

On March 13, President Trump announced during a briefing in the Rose Garden that Google was building a COVID-19 screening website to help Americans understand if they might have the new coronavirus. If likely infected, the site would also include the location of a local drive-through testing site to visit. So how can you access the screening website?

While the automotive industry is moving towards adopting AR displays in future models, BMW is already shifting into the next gear with its vision of the technology.

Norway-based production tools company Vizrt is putting the real into augmented reality with its broadcast AR solution that's designed to keep sports fans (and other audiences) watching.

In a LinkedIn post published on Tuesday, Microsoft's leading advocate for the HoloLens made a prediction that the mixing of immersive technologies will define augmented reality in 2018.

For companies wary of the temperature, PTC just made it easier for them to dip their toes in the waters of augmented reality.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

Imagine wearing your HoloLens, then reaching out to touch a hologram and actually feeling it. Mind blown, right?! Now imagine that same hologram responding to your touch. I don't mean in the way holograms currently respond to an air tap, but a much more refined and precise touch. Maybe you touch a character on the shoulder and it turns around to see you, or maybe you hit a button in the air and it reacts accordingly.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

The Academy Awards, commonly referred to as The Oscars, are airing this weekend. If you're a movie buff or just want to watch the dimes walking on the red carpet, The Oscars is not to be missed.

In 1958, Patrick Flanagan invented the Neurophone, a device patented in 1962 that allows radio signals to be picked up by the human nervous system. The skin is the organ that receives the signal, converting it into a modulated molecular vibration, which the brain interprets into sound. Basically, it gives one the ability to 'hear' through the skin, making it sound like the audio you're hearing is actually in your head. It's kind of like having headphones in your brain. The only problem was th...

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

Cancer cells do a pretty good job of flying under the radar of our immune system. They don't raise the alarm bells signaling they are a foreign invader the way viruses do. That might be something scientists can change, though.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

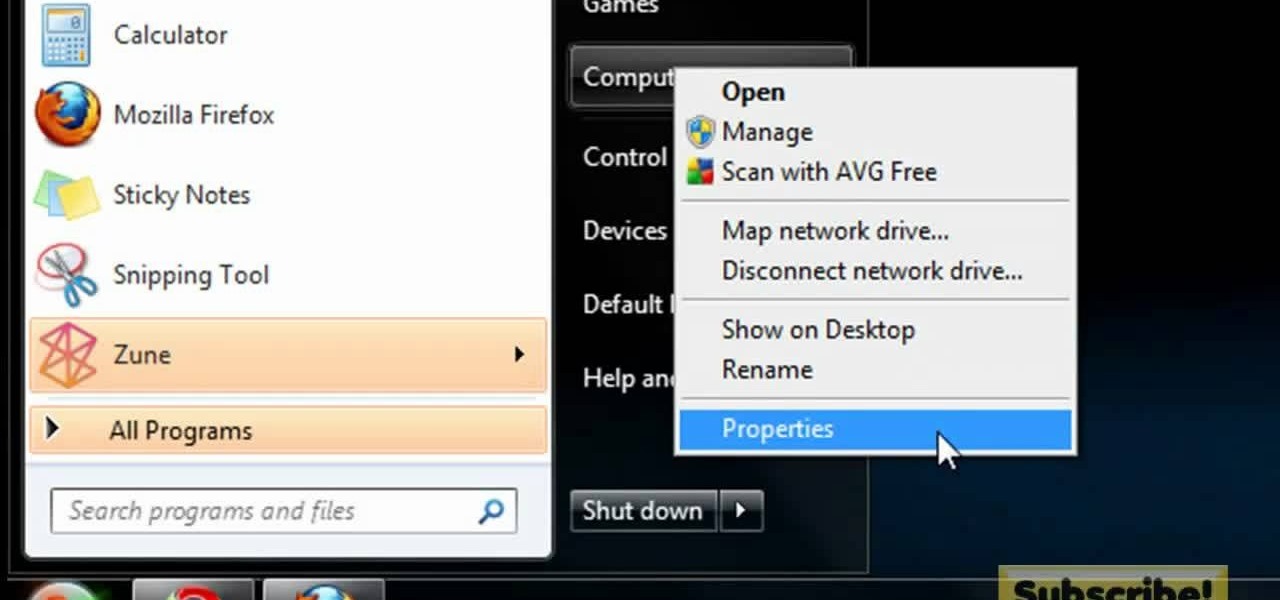
In this video tutorial, viewers learn how to make the System Restore feature use less space in Windows 7. Begin by clicking on the Start menu. Right-click on Computer and select Properties. Under Tasks, click on System protection. In the System Properties window, select the hard drive and click Configure. Under Disk Space Usage, drag the slider to the left for a lower amount. Then click on Apply and OK to confirm. This video will benefit those viewers who have a Windows 7 computer and would l...

Next to map data overlays, one of the most often discussed concepts for apps that could propel augmented reality smartglasses into the mainstream is a real-time language translation app.

Snapchat and Snap Camera aren't the only augmented reality apps available for couples to use on Valentine's Day.

On Thursday, yet another piece of the Magic Leap puzzle fell into place at Twilio's Signal developer and customer conference in San Francisco.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Augmented reality device maker Vuzix has filed a defamation lawsuit asking for $80 million in punitive damages, money damages, and interest against a short seller who has publicly claimed that the Amazon Alexa functionality of the company's Blade smartglasses is fraudulent.

Snapchat has broken new ground in its augmented reality advertising efforts, as BMW has opted to show off its new X2 model in AR with the Augmented Trial Lens.

Influenced by the growth of augmented and virtual reality technology as well as 3D computer vision, Ericcson Ventures invested in Matterport, whose hardware and software help companies create AR/VR experiences.