If you've ever been inspired to try out 3D modeling after enjoying computer-generated imagery in video games and movies, chances are you've checked out an paid applications like 3ds Max (previously called 3D Studio Max), or even free ones like Blender, then just went "No Way! It's way too complicated."

With the release of the HoloLens, Microsoft has put itself in both a great position while giving the competition a serious target to aim for. This is normally the case for anyone that is first to the market with a new idea, and now we've finally got a good competitor HoloLens coming. Stereolabs, a company known for its impressive 2K stereo camera, will be entering the mixed reality head-mounted display space with a Developers Kit as soon as early-2017.

No one ever said you had to be a culturally-relevant pun for Halloween, you know—or a scantily-dressed version of the inmates from Orange is the New Black.

While visiting the Made by Google pop-up shop in New York City this morning, I had a chance to try out the new Daydream View virtual reality headset. First impressions are important, and Google's new mobile VR product makes a good one. The headset is made of a soft fabric that most evokes a beloved old college sweater that's well worn but properly cared for. The demo only featured the Slate (darker gray) model, though customers will ultimately be able to choose from either Slate, Snow, and Cr...

We're on the verge of an amazing evolution of technology where we can work and play in virtual worlds that merge with our own—or let us escape into our imaginations entirely. But creating virtual, mixed, and augmented reality experiences requires resources and hardware that not everyone has access to. If you want to build something awesome with the Microsoft HoloLens (or one of the other awesome platforms), we want to help you do just that.

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

When you think of all the fun and games smartphones have to offer, it's easy to forget that they also make a great tool for getting things done. With utilities like document scanners, calendars, to-do lists, office apps, and password managers, that little computer you carry around in your pocket has the potential to increase your productivity levels in all aspects of life.

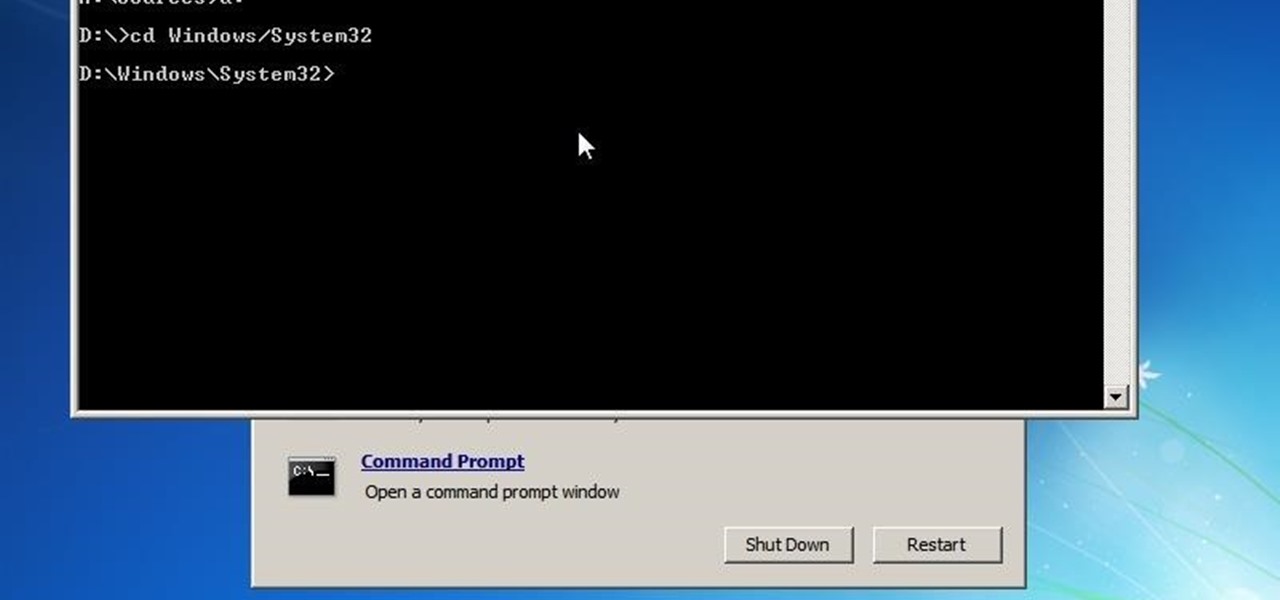
Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

It should come as no surprise that, according to Details Magazine, nearly half of all people who make New Year's resolutions pledge to lose weight, eat healthier, and/or get fit. There are innumerable companies out there that are ready and willing to take advantage of this momentum: from those hocking "magic bullet" pills that will increase your energy or reduce your belly fat to the myriad shake- and juice-based diets that put you at a near-starvation calorie input—and will probably have you...

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

I held the orange packet in my hands and presented it to my friend, Seth, as though it were a plastic-wrapped jewel—rather than three ounces of dehydrated noodles.

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

Hello everyone! I'm glad to post my first tutorial and hope you will appreciate it.

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

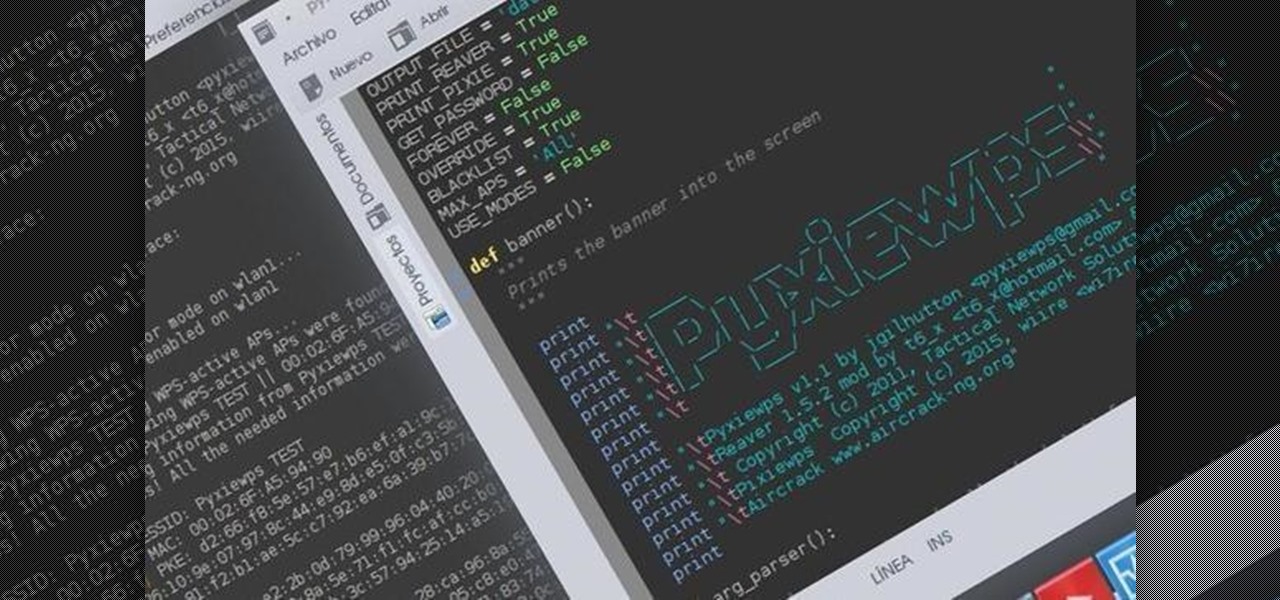
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago.

Coffee beans are one of my favorite things in the entire world. They smell intoxicatingly perfect. And when ground up and steeped in hot (or cold) water, they somehow taste even better than they smell.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

While its hardware may already be a little outdated compared to newer flagship phones, the OnePlus One is still a great value thanks to the dedicated community that continues to develop ROMs for it. Cyanogen 12 and Oxygen OS are the two most popular ones, but neither offers the type of unique experience you get with Xiaomi's MIUI (pronounced "Me You I").

As glorious as a good drink (or five) can be, the aftermath of alcohol on the body is one of life's least enjoyable features. A few hours of fun can come at the expense of a day or two of feeling dead to the world, with an upset stomach, an aching body, and a headache that makes it feel as though your friends used your head for a piñata.

Ask ten different people how they feel about boxed cake mixes, and you'll likely get ten different answers. Some baking purists will berate them and throw them in the same category as garlic presses and knife sets sold on infomercials. Many people will say that they prefer not to use mixes, but keep one in the pantry just in case. And I dare you to find a college student that doesn't sing their praises.

Food waste is a topic near and dear to my heart, but the truth is, no matter how dutiful we are about finding ways to double-down on food scraps, a lot of stuff goes into the trash needlessly.

Confession: I love bagels. I love to make them, but above all, I love to eat them. In college I ran a mini-bagel business from my kitchen, and on bagel-making day, it wasn't uncommon for me to eat the circular goodies for breakfast, lunch, and dinner. Yet even with my obsession I can't always eat bagels fast enough to keep them from going stale. That's why I started learning ways to use bagels even when they're a day or three past their prime. As it turns out, there are a million and one thin...

As a lover of food, I'm often asked, “If you could only have one food the rest of your life, what would it be?” My answer is always the same: sourdough bread. (Okay, it's not always the same... I usually cheat and say sourdough, fancy cheese, and a good beer.) Admittedly, I'm biased by my own sentimentality. My mother is an expert bread baker, with a major in making sourdough. Her sourdough starter is older than I am, and in all honesty, she's made thousands of loaves, each better than the ne...

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

The Galaxy S6 won't hit shelves until later this spring, but that didn't stop the Android community from working its magic and pulling a handful of apps from the device's stock firmware. Several of these apps rely on framework elements that aren't present on current-generation Samsung Galaxy devices, but the new version of the Smart Remote app can be installed without much difficulty.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

You've heard the old saying, "When life gives you lemons, make lemonade." Well, the same goes true for snow. When Mother Nature dumps loads of the white stuff onto your neighborhood, then make the most of it with treats like maple snow candy, snow ice cream, and snow cocktails.

Smartphones like the Nexus 6 and those in the Samsung Galaxy Note series border on being called tablets due to the sheer size of their displays. They are essentially "phablets," i.e., devices too large to be a typical smartphone, yet too small to be a tablet.

Due to their large size and added screen real estate, Apple included a new feature for the iPhone 6 and 6 Plus known as "Reachability." Essentially, this function makes reaching the top part of the display easier by double-tapping the home key to shift the screen down closer to your thumb.

Christmas trees, once decorated and brightly lit, are the penultimate holiday decoration, but authentic pines lose their brilliance fast without any nourishment. Plus, they are major fire hazards without regular hydration. But watering one requires a lot of sliding around on the floor, and it can be hard to tell how much water is in the bowl beneath the dark, prickly branches. These five hacks can help!

From parents and other family members to friends and peers, personalities are built by environment. Though people are important in the development of our own individual personality, there are other, different influences, including what you choose to read. The books you take the time to enjoy can make you nicer and more understanding, or leave you overall unchanged.

Google's latest Nexus device is big, bold, and beautiful—and now it's got root. Thanks to some quick work by legendary Android developer Chainfire, the Nexus 6 already had a clear-cut root method before most stores even had it in stock.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

I have never been a morning person, and that's a trait that I don't think is going away. Combine my distaste for early hours with being a heavy sleeper, and it adds up to a lot of alarms being dismissed in a haze, with no real intention of ever waking up.

Mirror, mirror on the wall, who is the fairest of them all? Besides being one of the most notorious misquotes of all time (the line is "Magic Mirror on the wall, who is the fairest of them all"), it's a question that men and women probably have asked themselves more than once.

Google's upcoming Android release hasn't even received a name or version number yet, but the third-party development community is already having its way with the firmware.

Although your friends might roll their eyes every time you talk about playing Clash of Clans, Call of Duty, or Candy Crush Saga, your excessive gaming habits might actually be making you healthier than everyone else.