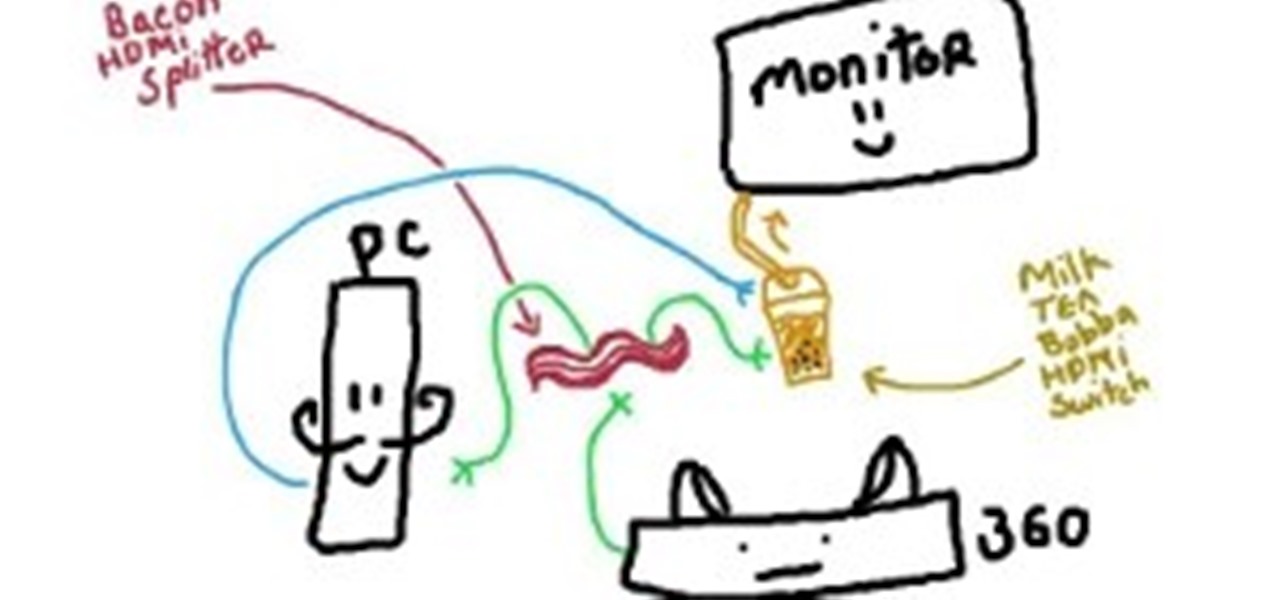
It was brought up a while back in a Community Call to Arms that *math* is handy for encryption (and let's face it, everything) so let us go over things you just have to know. "In its simplest meaning in mathematics and logic, an operation is an action or procedure which produces a new value from one or more input values."[source]

Etching your own circuit boards is tons of fun, but etching requires strong chemicals to dissolve the copper plating on blank circuit boards. The normal ferric chloride solution works well, but can be expensive and leaves permanent stains. Luckily, we can whip up our own etchant at home with everyday chemicals! Better yet, our new etchant will turn an eerie green color rather than the dull brown of ferric chloride.
Creating any object you want is as simple as point and click if you have a 3D printer at home. If you don't have one handy, there are a few companies that offer printing services online. But to help services realize your design in extruded plastic, you have to make a 3D computer model for the printing machine. For beginners, the free Google SketchUp application is the best choice of software. Using only a few tool bar buttons and a scroll wheel computer mouse, you can model literally any obje...

Graffiti is a great way of getting your message out to the masses. The earliest known graffiti dates back to 30,000 years ago and used the traditional apply-paint-to-wall technique. Though our paint now comes in cans and not from scavenged berries, the actual graffiti process hasn't really evolved from those first cave paintings.
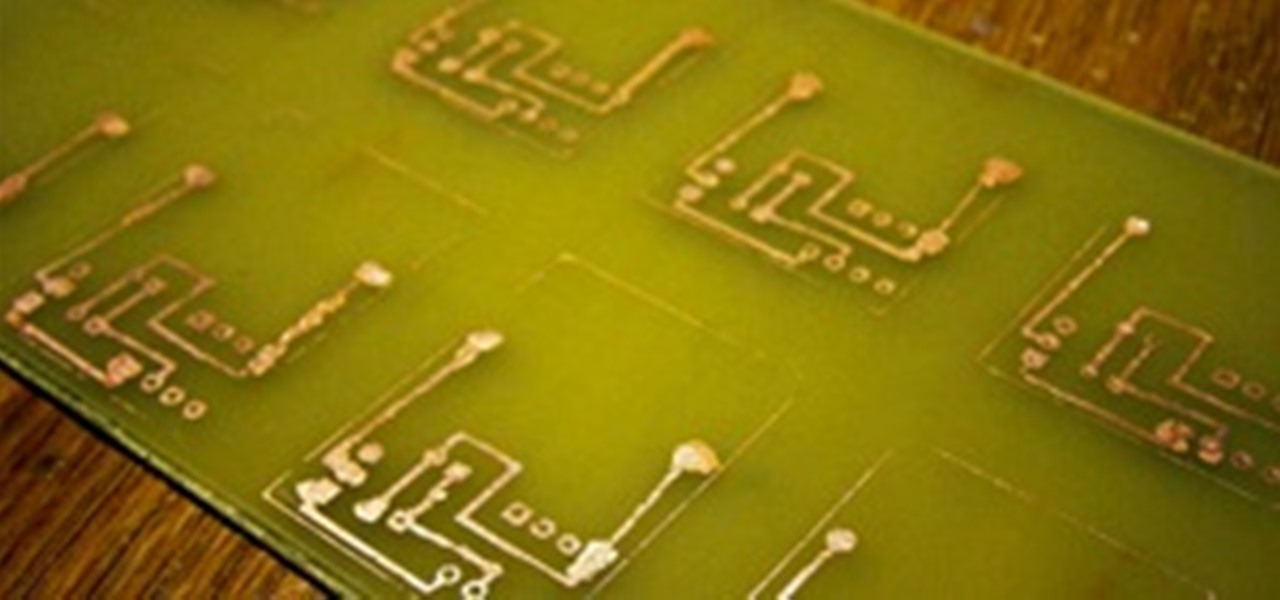
Homemade circuits are amazing. You can build any kind of circuit on a simple perfboard, as we have seen in previous projects. However, some projects require very tiny circuit boards. We could special order some boards from a printed circuit board (PCB) factory, but that will most likely involve a high price per board and a few thousand miles of delivery service to pay for.

People sometimes ask me about the IT industry here in the states. These folks are usually either trying to get into a certain field, or looking to switch or move into another one. Right now, you may currently be a Computer Science major that will be graduating shortly and are interested in the current state of IT security.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three!

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

The agents of empire do not always arrive with warning. When you are besieged, surrounded, and infiltrated, imagination is often your best weapon against the oppressors. If all you have at hand is some duct tape and a disposable camera, fear not, you have the makings of a powerful taser!

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

If you're on a tight budget for food, whether you're in college, or someone just starting out living on their own, you're probably low on money and sick of ramen noodles. Don't get me wrong, ramen can be tasty and filling, and there is almost nothing cheaper.

There’s a race on to see who'll be the Instagram of moving pictures. This makes sense, since many of our phones are clogged with video that, so far, no one is going to see. Wouldn’t it be great if there were a simple app that could take our video content, edit it for us, and then publish it to all of our networks?

Now, I know what you're thinking... "I need an extra sexy coffee table that is like no other."

The Elder Scrolls V: Skyrim set off a bang in the video game world this month. It will likely be video game of the year a few times over. Skyrim is another part to a series set in the fantasy world of Tamriel, a world filled with mystical creatures, folklore, and even its own history. It's quite the beatuiful and immersive experience. If you have not picked up the game yet, please do (my fiancée even plays!). Also, make sure to buy it new, so the hard working coders at Bethesda get the money ...

Problem: You're a PC gamer who absolutely loves The Elder Scrolls series and were eagerly anticipating the release of the newest game, Skyrim. But as much as you'd like to pick up the new game, money is tight. What do you do?

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. While mining is a basic aspect of Minecraft, it is often overlooked. Every adventure requires iron and diamonds and other ore and if you're playing in hardcore mode then you need all the help you can get.

Minecraft is not just a game. It is a creative tool. Over the past year and a half countless epic builds, servers, and community projects have been undertaken. I'm sure some of you have seen the one-to-one scale recreation of the Starship Enterprise from Star Trek or the epic server Godcraft. Countless projects such as these are being worked on as we speak, and they serve to inspire us all.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.

Camera manufacturers release new versions of the same cameras, mostly point-and-shoot models, as frequently as Detroit's auto industry upgrades minivans. They also add new lenses regularly, upgrading previous models with adjusted zoom ranges or the image stabilization feature. The same goes for tripods, portable flashes and even camera bags.

D.I.Y.: Start Your Own Cassette Label! By adam_schragin on Aug 4, 2008 at 10:56am in DIY

Night People: A Bad Vibes Label Profile

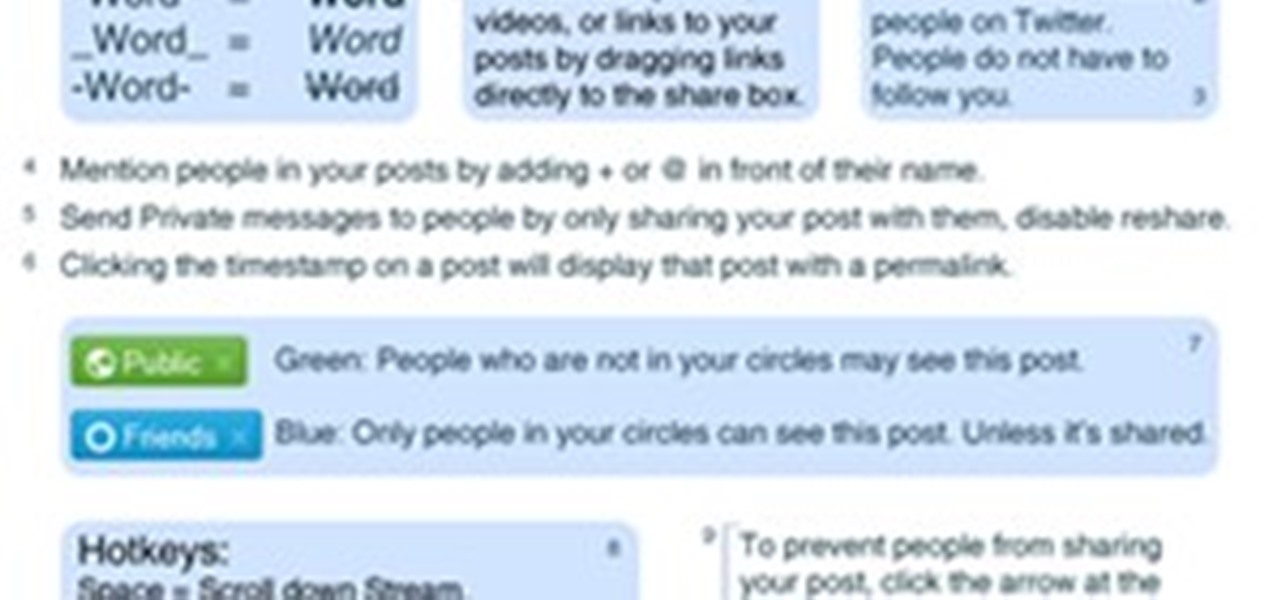
Circles. They are both the best thing and worst thing about Google+. They're great because they allow you to fine-tune who you're following and who you want to keep in touch with, making it easy to keep your family and friends separate from each other. On the other hand, they can be a pain to maintain, and you can easily become overwhelmed from the "noise" of popular posts, which make it hard to concentrate on some of the people you want to focus on. But if you invest a little bit of time in ...

Last week, I demonstrated how to go a little deeper into your Google+ profiles, photos, and introduced cross-posting. This week, I'm highlighting a bunch of different unofficial resources that have sprung up that will help improve your Google+ experience, and give you the latest updates on Google+ Photos.

Video capture... how does it work? Apparently, I have no idea. What I thought would be a simple undertaking turned out to be a slow and annoying pain. I just wanted to capture video in high definition and to lessen the time it takes to setup, record, and upload the video.

With the Google+ team members being generous and free-flowing with advice on some of the more advanced features of Google+, we'll be publishing a weekly summary of the latest pro tips. Chances are, if you've been following the Google+ team members, you've seen some of these already but you don't have them all in one handy place.

OSPD1 In 1978, the first SCRABBLE Dictionary was conceived and published by Merriam-Webster, with the help of the National Scrabble Association (NSA). The idea was to include any word that was found in one of the five major dictionaries at the time:

If you're like me, you were disappointed when NASA cut their human space flight program. No longer could children and adults in dead-end jobs dream of someday walking on the surface of the Moon or drinking floating globules of water through a straw. Homo sapiens as a species are still making it up there, but I will never be one of the chosen ones.

A game labeled as 'educational' usually spells its death among hardcore gamers. The educational game genre is mostly intended for children, and games that appeal to children often lack the sort of widespread appeal that makes them commercially successful.

Since the invention of the mechanical clock, enclosure of the commons, and proletarianization of labor, the alarm clock has been the bane of our existence. While not actually evil, it does represent the constant and uncompromising glare of our owners shaking a patronizing finger at us, telling us to get to work so they can use our labor to grant themselves bonuses.

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?