
TypoGuy Explaining Anonymity: Secure Browsing Habits
to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?


to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Hello everyone. I've recently made the annoucement of the Null Byte suite of tools, and we've covered how to download and install it. Now it's time we cover how to submit a tool for inclusion into the suite. It's relatively simple, but we need to get a few ground rules out of the way.

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

Yes, there's already a way to jailbreak iOS 9 on your iPad, iPhone, or iPod touch, but given the fact that it's only been out for about a week means that not all developers have had a chance to make their tweaks fully compatible yet. That doesn't mean they won't work, but that they might not be as smooth as they should be.

Reddit, the self-proclaimed "front page of the internet," continues to take a big bite of my free time each and every day, as well as millions of its other users'. The clicking and scrolling through page after page never gets old, but you could speed things up with a few browser extensions and double your Reddit knowledge in half the time. Here are my favorite extensions you can try out for the Chrome, Firefox, and Safari web browsers.

KNOX is a major pain for Samsung owners who like to modify their devices. Its combination of hardware and software security measures make things rather difficult when you're trying to modify system-level files and functions without voiding your warranty.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

Video: . Project Overview

If you've ever wiped your computer without having a proper backup of your operating system, or just wanted to cause some havoc online, chances are you've had to rely on Linux to help you out, specifically the Ubuntu distro.

Sitting in a cubicle and never seeing sunlight during the workday is unpleasant to even think about—and sitting in a flourescent-light cube can have terrible effects on both our work performance and overall attitude. Yet there are ways to counteract the effects of cubicle sitting, even if you can't sit in a sunny office or work from home.

Better sleep, smartphone news, and changes to your favorite forms of entertainment. There's been a lot going on over the last couple of weeks in the world of tech, and we thought we'd show you all of the need-to-know products, updates, and ideas that we think are most important.

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.
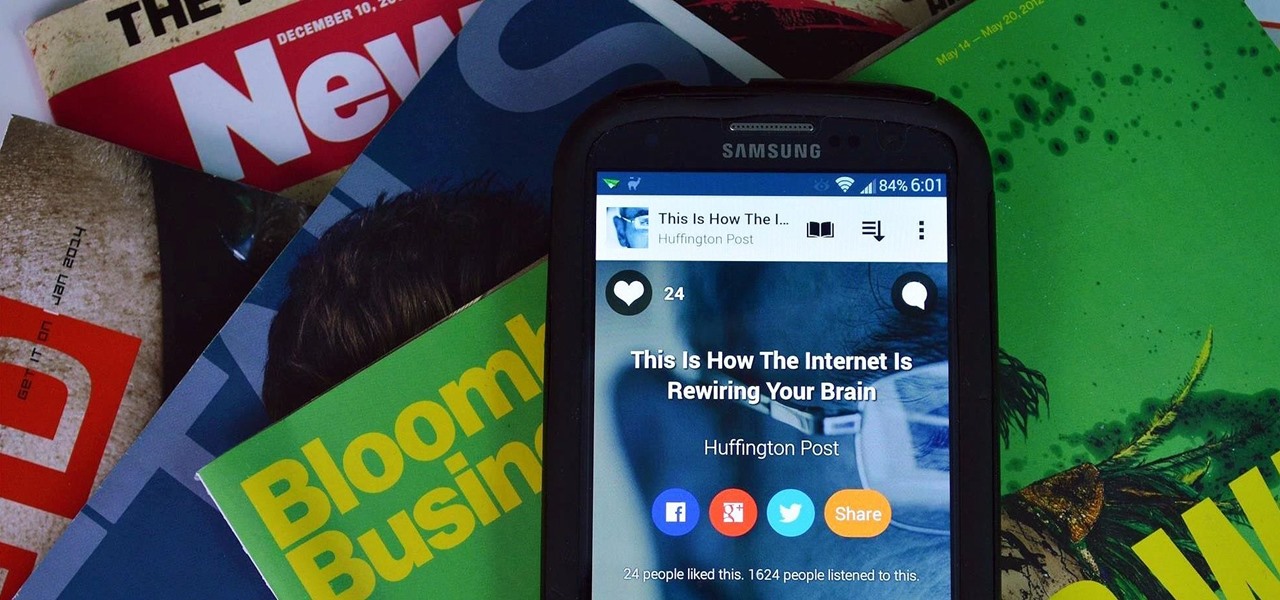
Keeping up with current events is a good step towards becoming a well-informed person, but sometimes it's a chore. In-between work, school, commuting, social lives, and hobbies, it can be extremely hard to find time to pick up a newspaper or browse CNN to find out what's going on in the world.

We Nexus users are fairly spoiled. There's a ton of third-party development for our phones, which translates to a virtually endless stream of custom ROMs being made available to us.

April Fools may be over, but any day is a good day to prank someone, and the best time to do it is when everyone's eyes are glued to the television.

If you've never played Cards Against Humanity, it's time to get initiated. Originally funded through Kickstarter, the free to download card game is basically an obscene version of Apples to Apples.

You've probably used Google to search for recipes, or to find out what the heck that mystery food on the ingredients list is. But with all its built-in features, there are plenty of other ways the search engine can help you out in the kitchen.
Pretty soon, every restaurant and store you walk into will know exactly what you're doing. Retail analytics companies like Euclid, ShopperTrak, RetailNext, and Prism Skylabs have penetrated hundreds of food shops and retail stores across the country, installing sensors that track and log customers' moves while they dine and shop.

The @DesignGears guys have been busy today, leaking an unofficial KitKat build (Android version 4.4.2) for the AT&T Samsung Galaxy Note 3. The latest is a peek into what the international variants are beginning to see, although this build is far from official. Still, if you want to give it a shot, I'll show you how to install it, but make sure to check out the details below the how-to to see what you can expect, good or bad.

Let's get one thing straight: CyanogenMod is one hell of a ROM. They've got a great community, a great product, and getting it on your HTC One couldn't be easier with their CyanogenMod installer, which does all the hard rooting and bootloader unlocking for you.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

You (or your partner, or both) are a Steampunk. Let's get away from all the mindless, unfeeling commercialism for a few minutes and think about dates instead of gifts—where do you take your significant other for Valentine's Day? What would be the ultimate Steampunk Valentine's Day date?

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

Your entire life has been a lie. Mario does not hit blocks with his head, footlong subs are never really 12 inches long, and those paper ketchup cups at fast food joints aren't just little cups. And that's not the worst of it. What I'm about to tell you next is the revelation of all revelations.

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.
Apple's Shortcuts app lets you make and use custom icons for any app on your iPhone, but it won't actually replace any icons. If your goal is to change the official icon for the app itself without any redirects, there's a growing list of third-party apps that'll let you do just that.

Although the enterprise use cases for the Microsoft HoloLens 2 continue to impress, the arts community just can't stay away from the best augmented reality headset on the market.
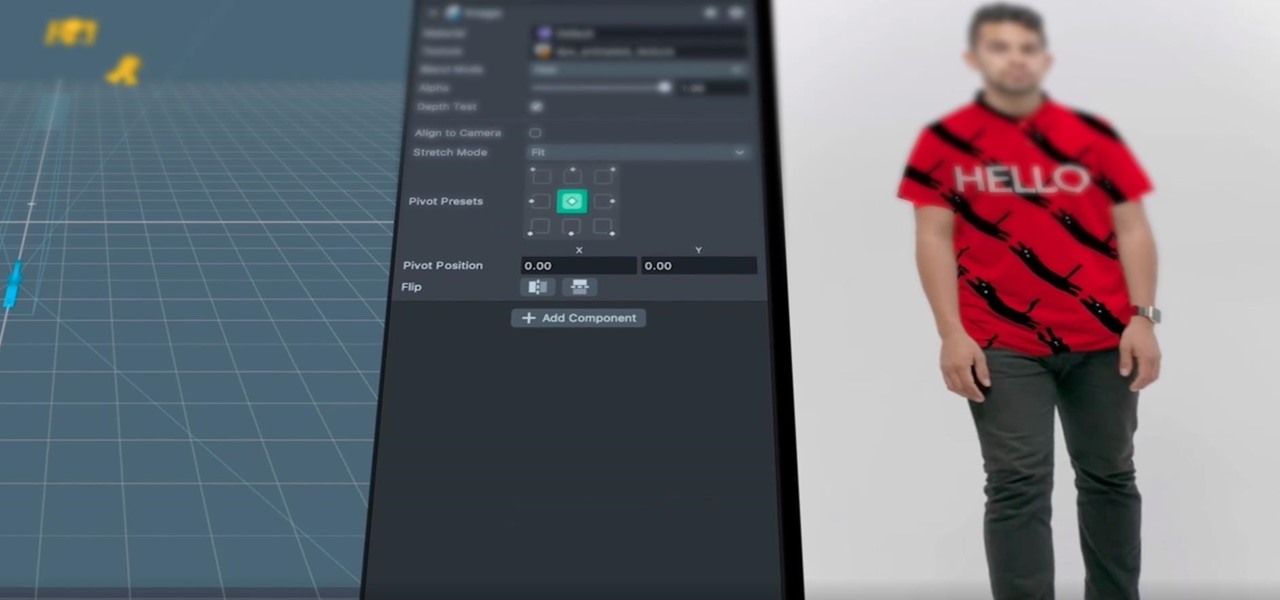
After adding full-body tracking and 3D body mesh in its past two Lens Studio updates, Snap continues to supply creators, particularly apparel retailers, with tools for creating clothing-centric AR experiences.

Some tried to call it a brief cryptocurrency-fueled fad, but it looks like NFTs are here to stay. Now, one of the biggest sneaker companies on the planet, Japan's Asics, is getting into the game with its own set of NFTs, and there's a virtual object component included.

Improving your experience online is getting easier every year. Browsing can be safe, easy, and boundary-less with the right VPN, and gaming online is working better than ever to connect and compete with other players.

Snapchat parent company Snap may finally be taking the big step into the fully-functioning augmented reality wearables realm with the next iteration of its Spectacles devices.

One of Apple's best features is AirDrop, which easily lets you send files to other Apple devices with a simple tap. That said, it might be a little too easy to use since just about anyone can send a file to your iPhone, whether you know them or not. The difference between AirDrop as a useful tool among your contacts and an open channel for the entire iPhone community comes down to one setting.
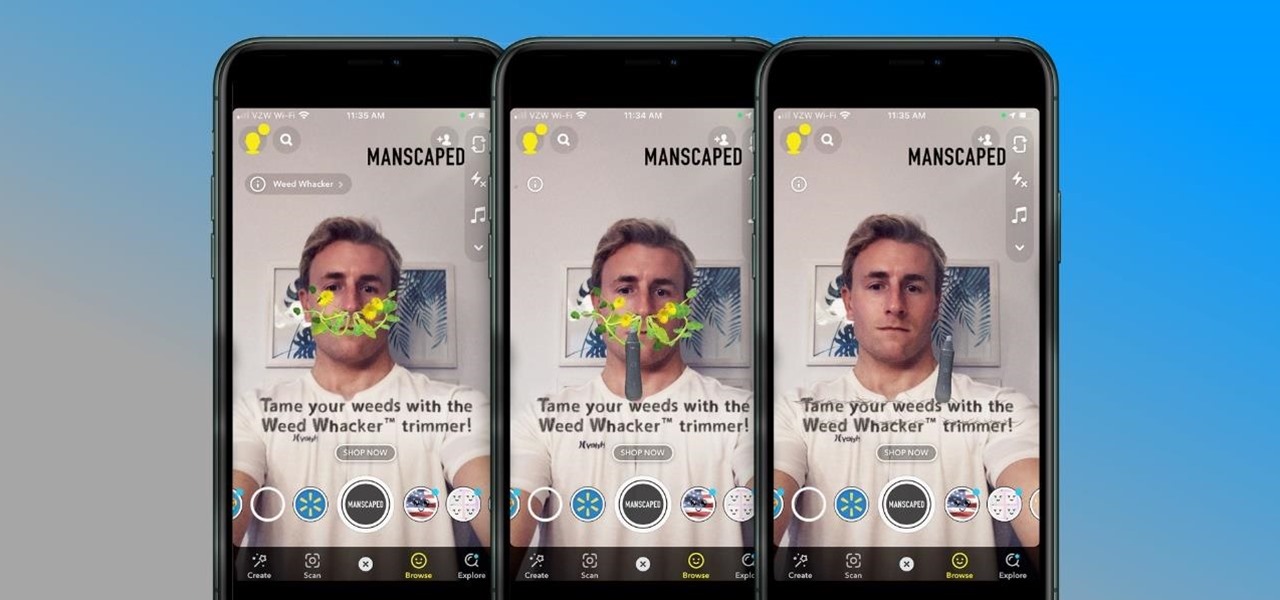
If you're a man and subscribe to podcasts or YouTube channels that cater to masculine interests, then you've almost certainly encountered sponsorships from Manscaped. And that means I don't have to explain what the company is selling you (for the uninitiated, it's a company dedicated to helping you trim your body hair—most notably, your nether regions, in addition to other areas).

If there's anything we've learned during 2020, it's that working and learning from home is going to shift the way we do business. With Microsoft announcing that its staff will be allowed to permanently work from home, expect more businesses to follow suit.

Niantic recently added a new Field Research task type called AR Mapping that challenges players to capture video footage of PokéStop landmarks and upload them. In return, players receive rewards in the form of in-game items.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.