Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Surely you're aware of the Sony hacking scandal by now (here's a quick primer if you're not), as well as the multi-billion dollar company initially bowing to threats by canceling the Christmas release of the The Interview, the film at the center of the whole debacle.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

Can you tell when someone is shooting you a fake smile? Even though fake smiles are easy enough to see through, we all still do it, attempting to show others just how happy we are when we're really feeling less than fantastic. Unfortunately, every smile we fake makes us a tiny bit more miserable.

It's been a long-rumored feature, but today, VoIP calling has finally started rolling out to users of Google's Hangouts service. Essentially integrating Google Voice into the popular messaging platform, Google has given Android (as well as iOS) users an easy way to make calls without eating up their plan's minutes.

Google Now is a wonderfully powerful service—with its predictive cards and voice search, it serves as a great starting point for any searches you need done. In fact, Samsung liked it so much that they decided to build the "Okay, Google" hotword detection right into the Galaxy S5's stock launcher.

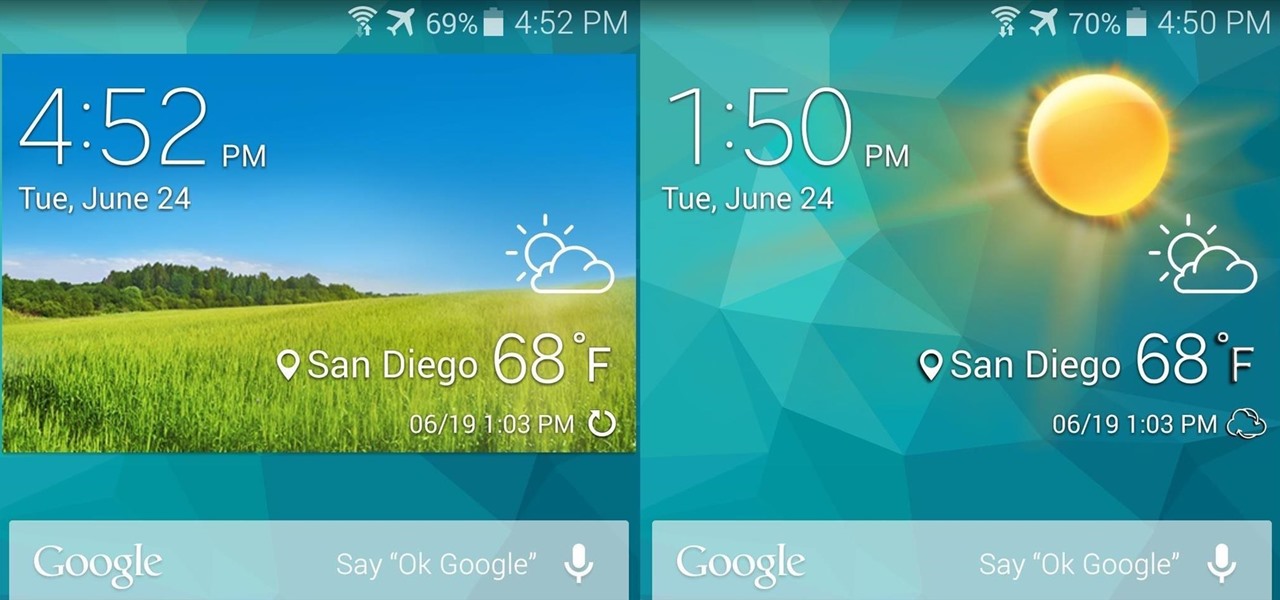
The weather widget on the main home screen of a fresh-out-of-the-box Galaxy S5 is meant to show off the screen. Super-high contrast and crisp definition on the individual blades of grass in the background let you know that the phone you're holding has one helluva display.

Geohot's Towelroot exploit made rooting the Galaxy S5 so easy that it was almost unreasonable not to try it out—even for the first-timers out there. This, of course, meant that folks who didn't truly need root for their usage went ahead and got Superuser privileges anyway.

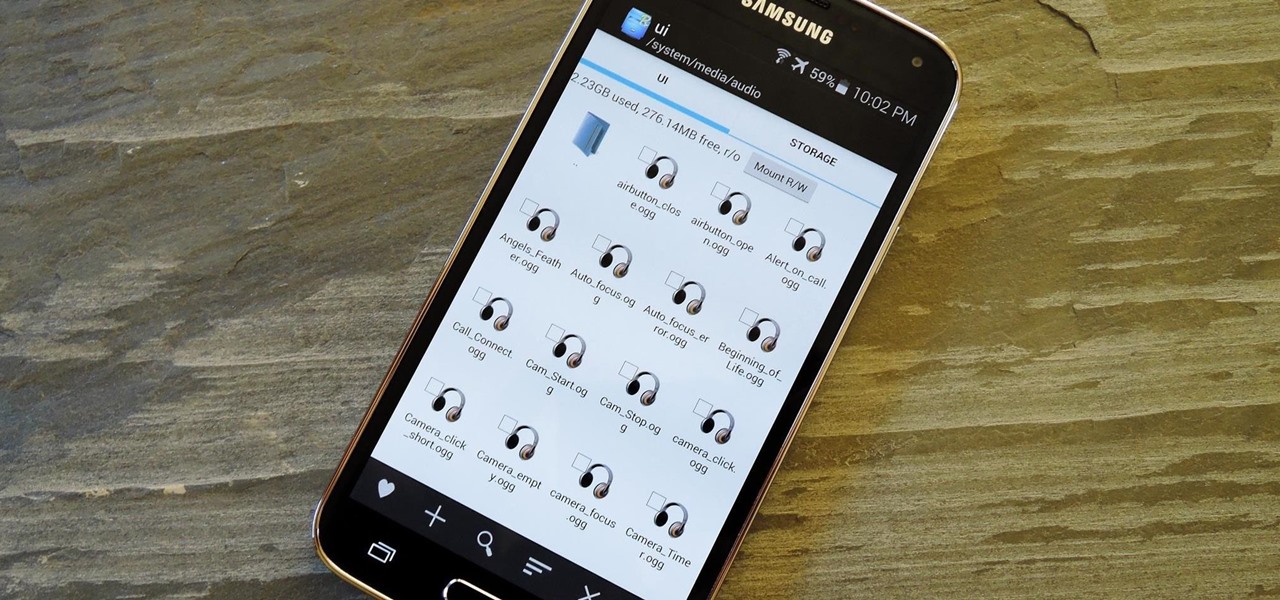
I have the AT&T version of the Galaxy S5, so every time I start my phone I get the pleasure of hearing AT&T's lovely jingle. Actually, that's sarcasm—I absolutely abhor this sound. I haven't had the chance to play around with a Sprint, T-Mobile, or Verizon variants of this phone, but I imagine they have some sort of equally annoying boot sound.

Text input on a touchscreen device is constantly evolving. From early beginnings of pecking out each individual character to today's predictive text and gesture keyboards, we've already come a long way.

Admit it, you wish Siri was on your Mac, and so do I. She stole my heart on iOS, and now every time I open up my MacBook, I feel something missing. Wouldn't it be great if we could, I dunno, hack Siri onto our Macs? Yeah, it would!

The desktop layout in Mac OS X Yosemite is undeniably beautiful—it's sleek, simple, and easy to admire. Thing is, I do too much on my Mac to install a developer preview as my main OS (even though I can make a bootable install drive and dual-boot it), but I do want the aesthetics of the new build.

Is social media ready to make the jump to the big screen? The developers behind the Android app Stevie think so.

There are a lot of instances where we find ourselves typing virtually the same phrase that we've typed many times before. Whether it's the standard spousal reply of "I'll be home in a few", or a work-related phrase like "I'll have that to you by the end of the day", typing phrases like these can feel very redundant at times.

Welcome back, my greenhorn hackers!

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

Changing your wallpaper and downloading icon packs is nothing new to the HTC One, but some people will go overboard with remapped keys, icon layouts on custom grids, and extensive wallpaper cropping—processes that could take hours to get just right.

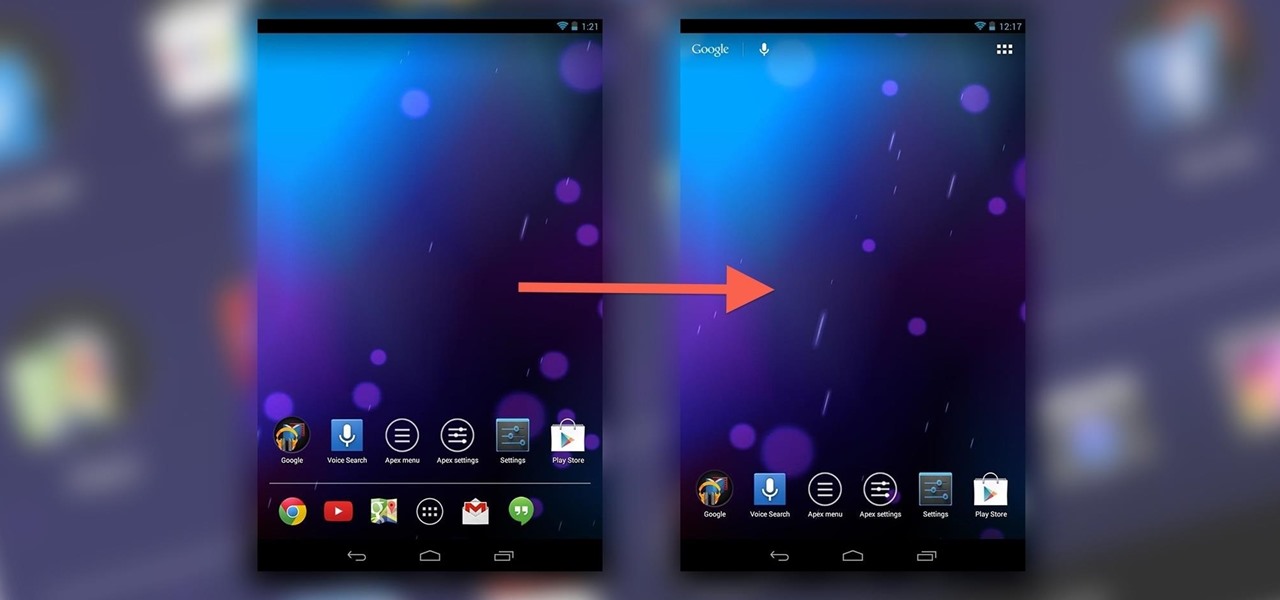
If you've never played with a Nexus 10 tablet, then you probably have no idea that your Nexus 7 actually has a different user interface. For some reason, Google decided it was better for the Nexus 7 to use a phone UI instead of a tablet one, but luckily for us, we don't have to accept that.

Apple may have unabashedly lifted their upcoming "Control Center" from Android devices, but visually speaking, it's an awesome take on Quick Settings that would look pretty good on a Samsung Galaxy S3.

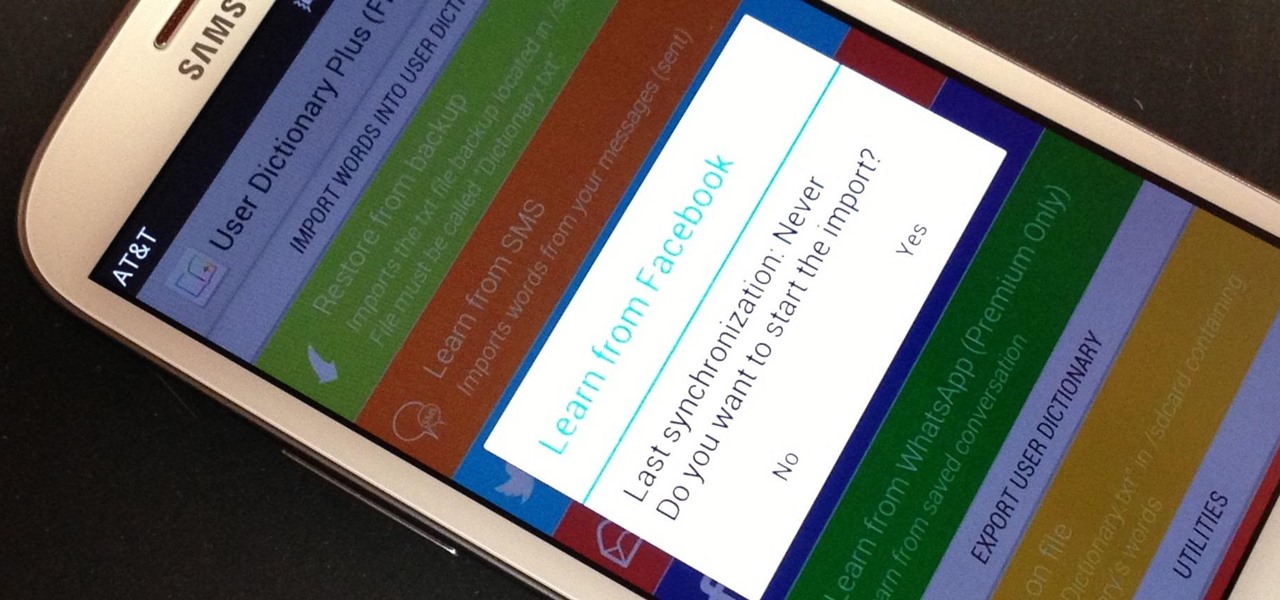
My standard text greeting to friends is something along the lines of "Wazzup biznitch?"—but apparently the auto-correct function on my Samsung Galaxy S3 has a problem with that. Time after time I have to retype it or just add all my made-up words to the word list—and I use a lot of made-up words, because that's what bosses do. But texting isn't the only way I communicate. I also use email, chat, and social media on a daily basis—and I don't always use my phone. So, wouldn't it be awesome if m...

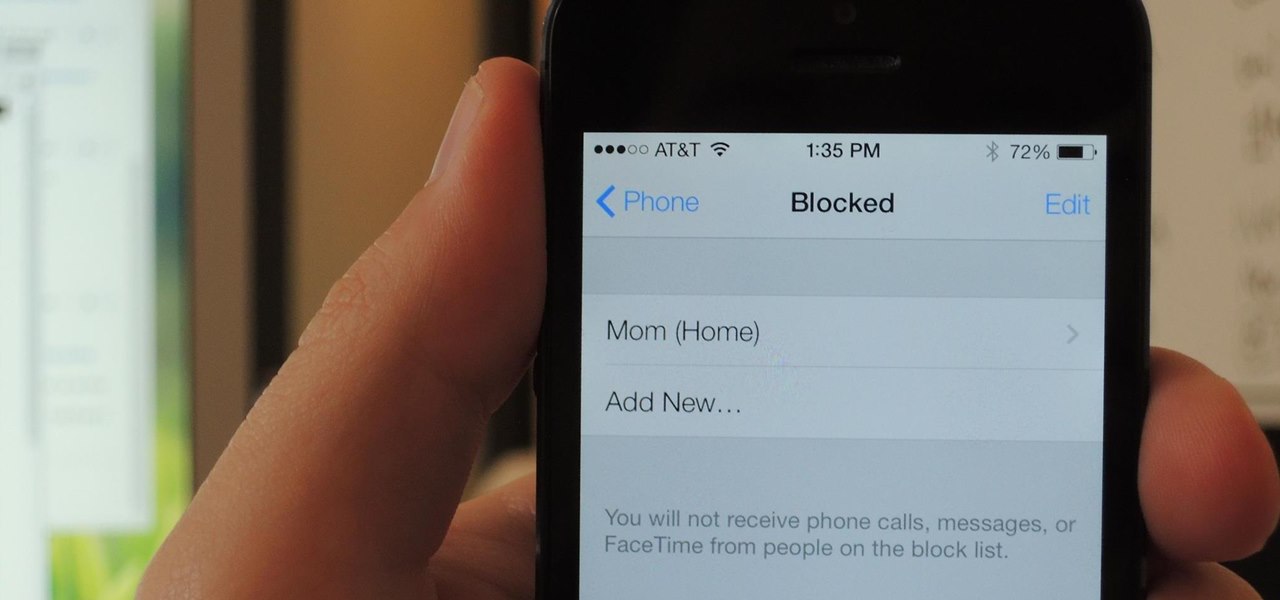
One of the most useful new features in iOS 7 is the ability to block phone calls, FaceTime calls, and text messages by blocking any phone number.

It starts innocently enough, with a nosy friend hovering over your shoulder to see what you're texting. Somehow, that doesn't satiate their inexplicable thirst for curiosity, so the first chance they get, they're rummaging through all of your super private photos—even though you told them not to.

All across the world, Nexus 7s have been secretly living a double life. The clean, simple look of the stock Holo user interface is nice if minimalism is your thing, but to softModders like me, Holo is bare, lacking style, overly blue, and an eyesore. It gets the job done, but I want something more customizable and visually stunning.

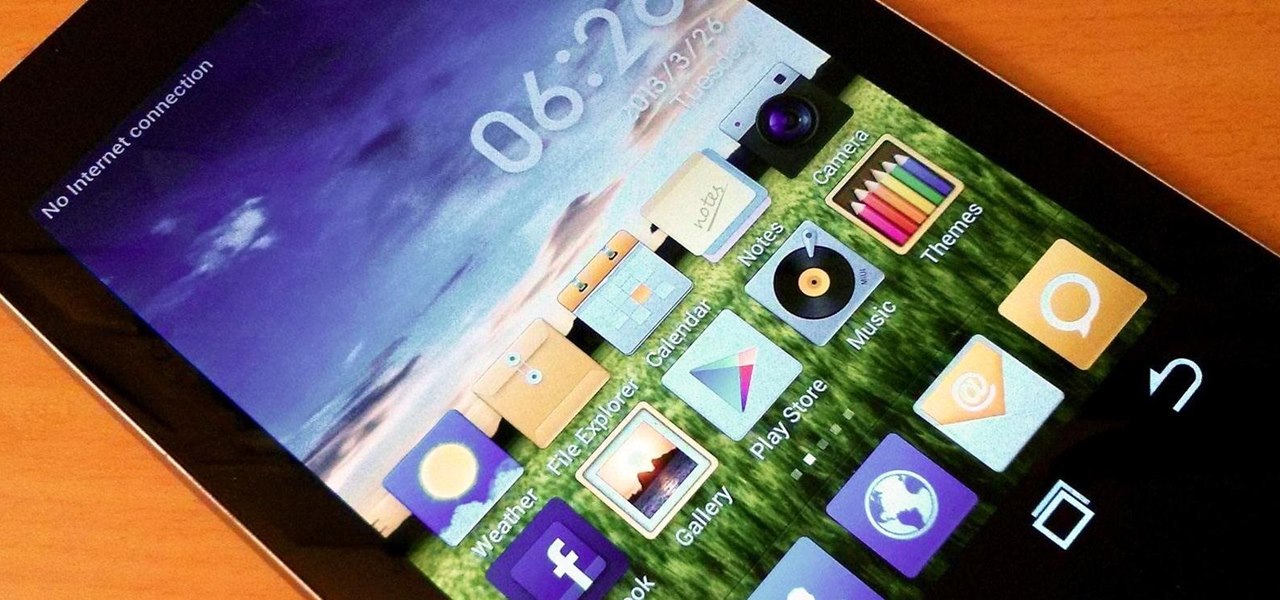
Do you like Samsung's TouchWiz and the iPhone's user interface, but wish you could bring the best of both worlds together onto your device? You can! MIUI (pronounced me-you-eye) is a heavily modded custom ROM that brings a different UI experience never before seen on stock Android devices. Over in the Nexus 7 SoftModder forum, Shashou Jian mentioned MIUI as a ROM every user should try out. The interface is a fresh mix of Apple’s iOS and Samsung’s TouchWiz elements—with a large dose of customi...

A car is stolen every 33 seconds in the United States, and from that, the percentage of vehicles recovered in the first day is a whopping 52 percent. Over the next week, that number rises to around 79 percent, but after those initial seven days are up, it's unlikely the vehicle will be found.

There are tons of situations that require you to give out your phone number, and I think just about everyone has regretted doing so at some point. It can be incredibly convenient to have a secondary or temporary number on hand, so if you don't want to provide your real digits, you can still get the call without revealing your true numbers. And that's where Burner comes in. Burner is a mobile app for iPhone and Android that lets you create alias phone numbers that you can take out of service a...

Lots of designer purse companies, especially Coach and Kate Spade, LOVE attaching beaded charms to their purses and clutches. Sparkly little bits and pieces add extra pizazz to anything they're attached to.

Let's face it ladies: All of us come with some baggage. While some of us have emotional baggage, we all have the physical kind: undereye baggage. This sagging and drooping of your undereye area is further aggravated by fine lines, wrinkles, and purple or blue circles. Ah, the loveliness of getting older.

Tom Pecheaux, Estee Lauder's new creative director, came to the company with a vision in mind: Bold, more unexpected drops of color for their eyeshadow palettes, lipsticks, and glosses. And bold is the only way to describe his Blue Dahlia palette, which is filled with intense electric blues, blacks, and silvers.

We all love primping products, but what girl doesn't want to save a few bucks when she can? While lots of beauty companies will advertise that they have the best curling iron for you to achieve those Kate Hudson beachy waves, the truth is that you really don't need a curling iron at all. In fact, to get your hair bouncy and curly, all you really need is a flat iron.

Have you ever been in a situation when you needed to remember something real important, but you didn't have you didn't have your trusty cell phone or other electronic savior with you?

Maya and Photoshop CS4 may be made by different companies, but that doesn't mean they can't work together. This video will teach you how to take a 3D model from Maya, import it into Photoshop, and then use Photoshop CS4's new 3D editing tools to overpaint the rough texture seams in the model. The end result will be much prettier than the model that you could have created with Maya alone.

Although not has highly popular as Call of Duty: Modern Warfare 2, Battlefield: Bad Company 2 is one of the few shooter games that is able to seperate itself from the arcade style of COD:MW 2. In B:BC2 you rely on strategy and teamwork in order to win multiplayer matches and the game. But if you're looking for something that will make you smile, check out this tutorial. In the video, you'll find out where the Sandcastle Easter egg is on one of the maps. It's just a small little thing, but is ...

Is there any character in the history of cartoons more iconic than Mickey Mouse? You'd be hard pressed to think of one, and in this tutorial, you can become part of the legend by learning to draw him!

This helpful video explains how to use letters when dialing on a Blackberry. Many companies have words in their phone numbers so Darci Larocque shows us how to dial those letters. All you have to do is go to the call log, and hold the key in, and type in whatever word you are trying to dial. She also shows us another tip: if you are calling an office and you need to enter in someone's last name, you can do that the same way. Blackberry users should definitely view this video.

Ana Maria, an origami artist, shows you how to make an origami angelfish. Her video explains in step-by-step detail how to make one of these cute paper folded creatures. By viewing her high-resolution video you can create an angelfish in less than 5 minutes. The video is by Hawk vs. Pigeon company, which specializes in video production. Their videos are always crisp, so demonstration videos are easy to follow. Make your origami angelfish today.

Club Penguin is a flash-based website with an a virtual world of online games for kids to play. Learn how to hack Club Penguin with tricks and cheats. Watch this video tutorial to learn how to find hidden items in the Club Penguin catalog (09/29/09).

Having trouble with people snatching your stuff? Did someone take your lunch from the company fridge? Here is an inexpensive, sneaky gizmo you can make to keep those sticky fingers away. This is a junk drawer hack from Make Magazine's Kipkay. It's activated when an item is moved from it, triggering a clothes pin to close and activate the voice command. See how to make a talking booby track in this video tutorial with KipKay!

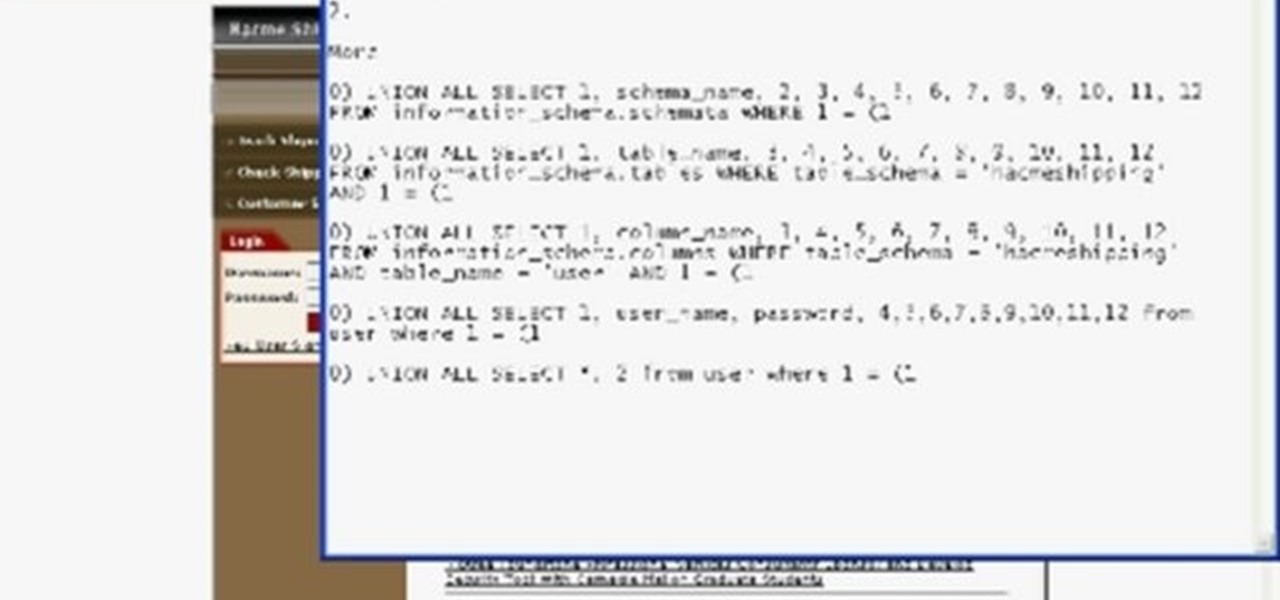
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...