The Consumer Electronics Show (CES) is the first big tech event of 2018. This year, if the early news is any indication, augmented reality could be the big star of the show.

Update 1/17: Tim Cook chimed in about the upcoming iOS upgrade with expanded battery health data. We'll expand on that below.
Nowadays, with the convenience of online shopping, brick-and-mortar retailers and malls have to work harder to draw shoppers to stores. This year, many of them are turning to augmented reality for assistance.

Who likes to buy apps? The answer is no one, of course. Unfortunately, as in life, the best apps and games don't come free. That's why it makes sense to wait until those apps go on sale before handing over your hard-earned cash. And what better day to find discounts in the iOS App Store than Cyber Monday?

Amazon Web Services (AWS) opened its re:INVENT developers expo with a bang by launching Amazon Sumerian, a new tool that could become the dominant platform for building cross-platform augmented and virtual reality applications.

To the best of my recollection, Fruit Ninja was one of the first touchscreen games that appeared to really take advantage of the new paradigm of user input, turning the player's finger into a produce-slicing katana.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.

Since the very first moment I saw the iPhone X track a human face and display the results in real-time on an Animoji character, I've been waiting for the first great hack of this new iPhone feature.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Razer just made a big step into the mobile industry by releasing an absolute beast of a smartphone. The gaming-centric Razer Phone tries to provide the best experience for its target audience: Gamers. With that in mind, they created a top-tier device with some of the best specs available on Android. But how does it compare to the current spec champion, the Samsung Galaxy Note 8?

With technology giants like Apple and Google finally entering the fray, the move toward mass adoption of augmented reality is ramping up. Apple's ARKit and Google's ARCore will allow entirely new categories of apps to be made. Unfortunately, in a world of heavy competition, getting these two frameworks to work together wasn't a priority for either company.

If you need a Halloween costume posthaste, you really can't go wrong with a LEGO man costume. And one made from cardboard that is fully functional, well, you'll probably win the "Best Costume" contest hands down. Not only will this mecha-esque costume wow everyone you meet, but it eliminates the need to apply Halloween makeup, style your hair, and get your outfit just so. With a LEGO man costume, you're ready to roll.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

A development duo has concocted an iPhone app that displays related tweets based on objects recognized by the device's camera.

With the recent launch of the LG V30 and the Pixel 2 XL, LG has reintroduced the world to POLED. This display tech was showcased at CES 2015 and billed as a rival to Samsung's AMOLED displays, then promptly disappeared from the market for two years. But now that two of the biggest flagship phones this year are using the technology, many folks will be wondering what makes POLED different.

The HoloLens has become a frequent sight in medical facilities around the world, but a new demonstration shows just how seamlessly it can be integrated into traditional medical procedures to improve the experience for physicians and patients alike.

OnePlus surprised the mobile industry last year when it revealed the OnePlus 3T in November, an improved version of the OnePlus 3 that came out just months earlier in June. While many thought this was a fluke, history has repeated itself with the arrival of the OnePlus 5T.

Mobile apps themselves are not always the end product or service for generating revenue. More often, they are deployed as tactics within a larger marketing or public relations strategy.

The Free App of the Week is as cool as it sounds. Apple features one app every week on the front page of its App Store that comes completely free. Once you download it, you have access to all future updates, just like you would if you purchased the app in full. Sounds great right? There's just one problem — it's missing.

You have a lot of choices when it comes to your next smartphone. iPhone, Galaxy, Pixel, G6, V20, and many more all vie for your wallet. Each of these phones are great for different purposes, but what if your main interest is mobile gaming? Which phone will give you the longest Minecraft session, or the best performance for Pixel Gun 3D?

Clearly, the next big battlefield for tech gamesmanship between Apple and Google will be augmented reality.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

The launch of the latest line of iPhones came and went without major revelations for advanced AR hardware other than the next iteration of processors and cameras.

It has been an interesting few days in developer news. The Microsoft blog has been busy with information relative to the augmented reality space. Meta 2 has also announced an interesting development this week. Here is a collection of various tidbits that have been collecting up.

The staff at Next Reality News is legitimately excited about the prospects that Google's ARCore could bring not only to smartphones and tablets running Android, but also to Android-based hardware such as smartglasses.

This morning Google announced ARCore, an SDK for Android devices that will allow augmented reality developers to add new functionality to Android 7.0 and up, all without any special hardware other than the camera of a phone.

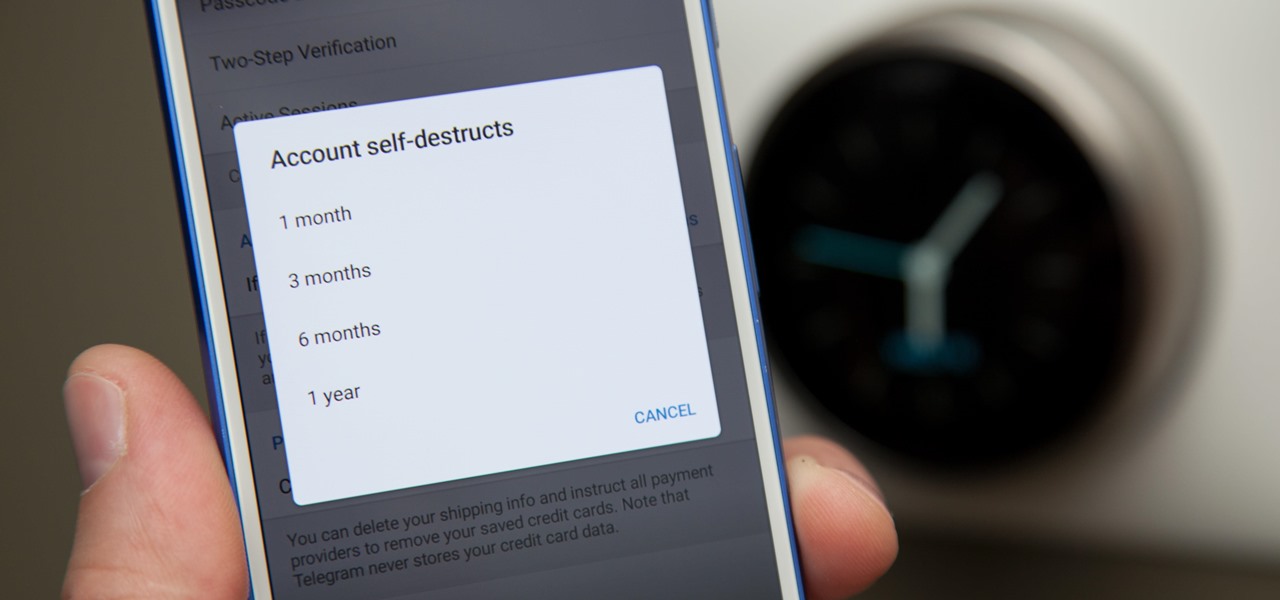
You can send self-destructing messages in Secret Chats, but that's not the only thing that can destroy itself in Telegram after a specified amount of time. Your whole account can disappear after a certain amount of inactivity, so it's important to adjust these settings to give you more time or to kill your account even quicker.

Former Google and Uber engineer Anthony Levandowski's scathing accusations challenging the physics behind Tesla CEO and founder Elon Musk's claims about Autopilot should force Musk to make his case that self-drive cars don't need LiDAR in the next few months.

An update to the iFramed social media gateway app for iOS adds an augmented reality feature called JuxImage that gives its users Snapchat-like photo and video effects.

Tesla founder and CEO Elon Musk said during the Model 3 launch party Friday night that all Tesla cars in production have the same driverless hardware, signaling that Tesla's jump to Level 4 hinges on a software update — but Musk didn't exactly say that.

Tesla's Autopilot self-drive interface in its new Model 3 signals the carmaker is already prepping its cars for Level 4 driving years ahead of the competition.

If you've ever wanted to scour the basement of a Hollywood hotel looking for evidence of a gruesome murder spree, this new AR experience might be the game for you.

Results of an early-stage clinical trial of an HIV vaccine could mean a hoped-for breakthrough in the battle against AIDS.

After watching Samsung's exploding phone fiasco this past year, I took comfort knowing that the likelihood my iPhone would suddenly combust was slim. However, after hearing about a recent incident in Wisconsin, iPhone owners may have reason to worry.

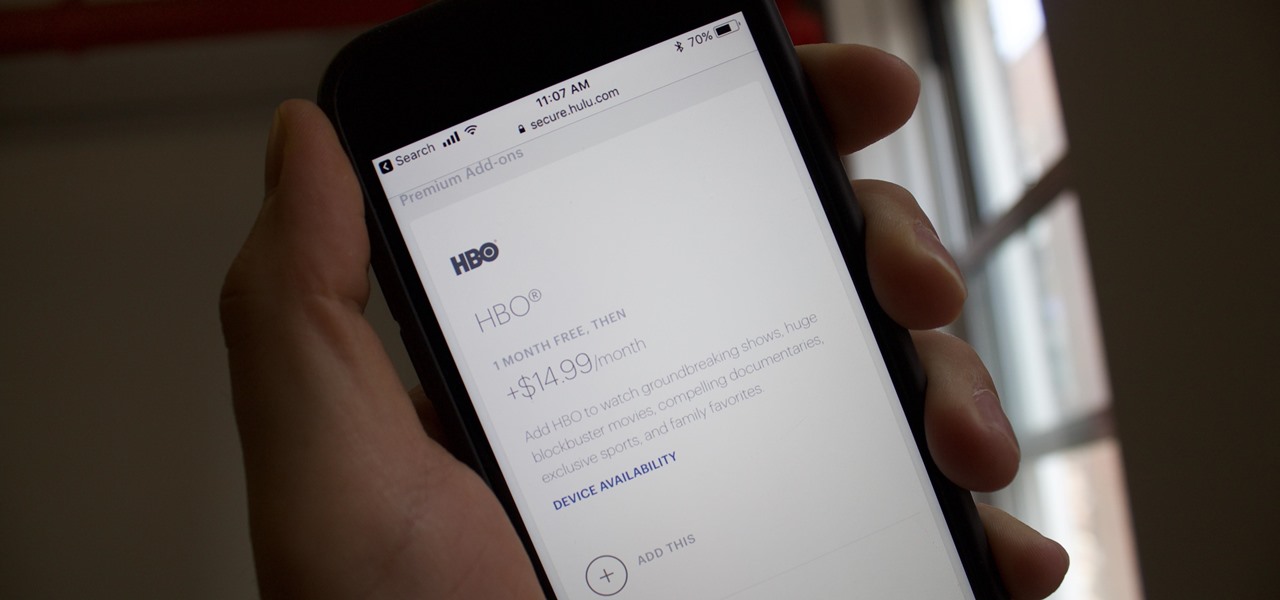
What's better than having access to Hulu's entire catalog on any device you wish? Having HBO's as well, obviously. Hulu recently began offering subscribers the option to either subscribe to HBO through their Hulu account, or to link a prior HBO subscription to their Hulu account. It's just one way to make binge-watching a little more convenient for you and your fellow Targaryens — the Starks can join, too.

Cytochrome P450 (P450s) are proteins found in nearly all living organisms, which play roles that range from producing essential compounds and hormones to metabolizing drugs and toxins. We use some of the compounds synthesized by P450 in plants as medical treatments, but the slow growth and limited supply of these plants have put the drugs' availability in jeopardy and jacked up prices.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

When the iPhone first came out, using them seemed like an impossibility to the visually impaired. Luckily, the iPhone now provides a multitude of resources to make sure that the visually impaired have accessibility to the phone.

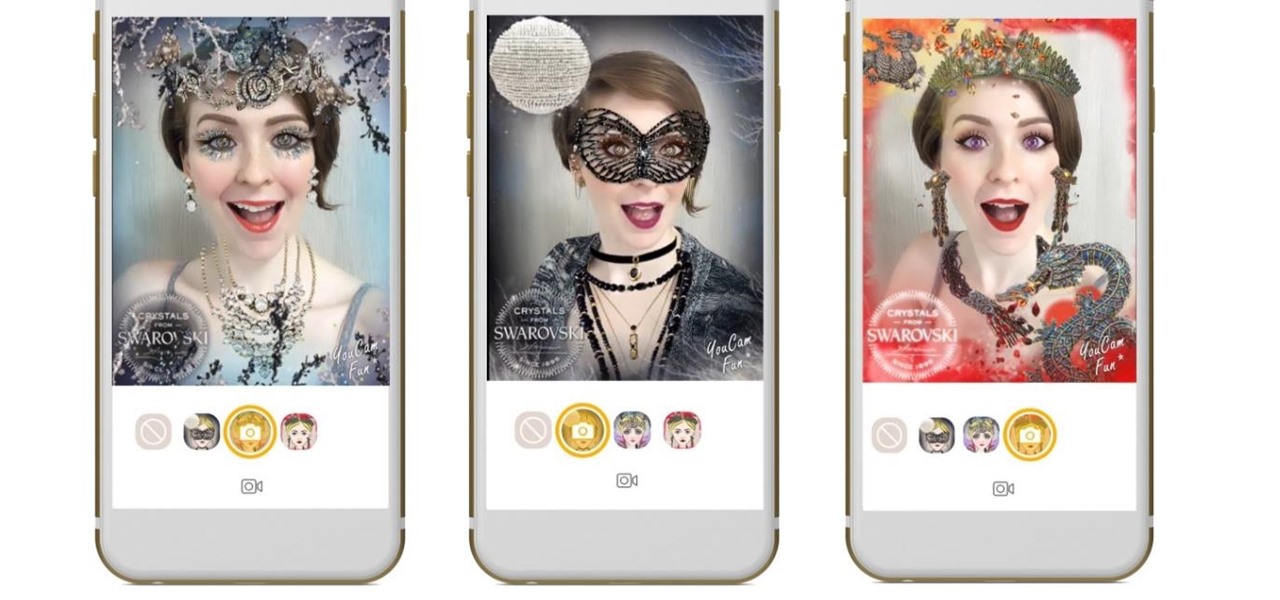
When it comes to differentiating from the competition, brands are continuing to leverage augmented reality to give consumers to the point that there are few "firsts" left to achieve in the marketplace. While L'Oreal jumps on the augmented reality bandwagon for cosmetics, Acura finds a new way to make augmented reality a spectacle in the automotive industry.

Natural remedies used through the ages abound, especially in Asian medicine. The willow-leaved justicia plant, found throughout Southeast Asia, has traditionally been used to treat arthritis, but scientists have just discovered it contains an anti-HIVcompound more potent than AZT. AZT was the first drug approved to treat HIV, and is still used in HIV combination therapy today.