Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.

I am officially breaking up with my daily breakfast of avocado toast and embarking on a promising new relationship with savory oatmeal. Yes, you read that right—savory oatmeal.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

There are many hacks for increasing productivity, but so many depend on tricking your own mind or behavior. When it comes to motivation in the workplace, though, sometimes the space within which you work dictates how you behave and the work you produce. So if you want to increase your ability to get more done in a single workday while doing a better job, consider changing your surroundings in the following ways.

Often, despite your favorite makeup mecca's rows and rows of endless colors, applicators, and brands, it's hard to find the perfect shade of lipstick—especially one at the price you want. Rather than resorting to what's available in stores, turn to your stovetop and a box of crayons.

One of my favorite things to do when I visit my parents is cook. Aside from the fact that I adore cooking with my mom, there's something comforting about returning to the kitchen that I first started playing in 20 years ago. Nearly all of the tools and appliances are the same ones that I used as a kid, and the familiarity is palpable.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

Any beer aficionado who's been to Ireland will always talk about how the Guinness there "just tastes different." But save your eye rolls, skeptics: it turns out your favorite lagerhead actually has a valid point.

There's nothing more jarring than the sound of your morning alarm. Even hearing it on others' phones, hours after your own abrupt wakeup, can cause you to flinch in fear. Though we depend on that shrill sound to get up each morning, it's actually better to wake up naturally—so don't even think about hitting that snooze button.

Being the bearer of bad news is unpleasant; there's nothing more uncomfortable than offering up a spoonful of negativity. Whether you're a supervisor who spends a lot of time interviewing and rejecting candidates, or simply someone who has to say "no" to a friend, it's never fun to break bad news. But sharing unpleasant words or feedback with another person can become less of a burden with a few simple steps.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

It's easy to take the food we eat for granted, but the truth is, there are a lot of bizarre, wonderful, and just plain weird things about what we eat and drink, the effects it has on our bodies, and vice-versa. Read on to learn how bugs provide food dye, the Japanese grow square watermelons, and more.

Pretty soon, every restaurant and store you walk into will know exactly what you're doing. Retail analytics companies like Euclid, ShopperTrak, RetailNext, and Prism Skylabs have penetrated hundreds of food shops and retail stores across the country, installing sensors that track and log customers' moves while they dine and shop.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

Sugru is some pretty versatile stuff. The company's slogan is "Hack things better," and for good reason. It sticks to aluminum, steel, ceramics, glass and plastics, it's waterproof and heat-resistant, and it can be molded into any shape you can imagine. Anything from your kitchen cabinets to your bicycle can be improved with some Sugru and a little creativity, and gadgets are no exception. Here are 10 of the coolest hacks to fix or upgrade your smartphone, tablet, or camera.

It's always a good idea to have a pack of mints on hand, especially right after a cup of coffee or a lunch made with loads of garlic. Whether you're going on a date, to the dentist, or to an interview, bad breath is a major faux pas and totally avoidable. Simply pop a mint! But not just any old mint — homemade ones not only freshen your breath but can give you a sense of pride every time you need one.

These days, you can find a digital version of almost any form of entertainment. Being able to download or stream content is convenient for a lot of reasons—you can avoid going to the store and you never have to worry about late fees on rentals.

Gus Cawley shares the ways to make a video resume with the help of free online tools. 1. Log in to YouTube. 2. Click upload and select quick capture. 3. Click the record button (be sure to have good lighting, good background and a high quality microphone for a more effective recording) 4. State the information of your resume. 5. Click the red square button to stop the recording then choose publish. 6. Edit the information of the video. In the description, put your contact details and informat...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

Moving is such a hassle! Packing is a big job but this video shows and easy way to pack out pots and pans. You will need 4-5 cubit foot cartons. You can get these from your mover or you can purchase them from a moving company. You will also want to get clean newsprint, packing tape, a moving blanket, and a permanent ink marker. Prepare your 4-5 foot carton by putting crushed paper on the bottom. This will act as a cushion for the pots and pans. Put the moving blanket or a protected pad on the...

This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

Looking at homes is the fun part. But before you go house hunting, make sure you have your financial ducks in a row.

Everybody knows it really shouldn’t matter, but sometimes entering a school cafeteria without a lunch mate can seem like walking the plank. Here’s how to survive the stroll.

Hook-billed birds are the ones in the parrot family—from petite parakeets to massive macaws. Here’s some stuff you should know if there’s going to be a hookbill in the house.

If things are getting a bit stuffy at your desk, don’t fret. A cool breeze is just a USB slot away. Watch this video to learn how to make a USB fan.

Watch this video tutorial to learn how to calculate your carbon footprint. A carbon footprint is an equation that estimates just how much you, personally, are contributing to global warming—and all you have to do is plug some info into an online calculator. Figuring out how to make your footprint smaller, of course, is another matter.

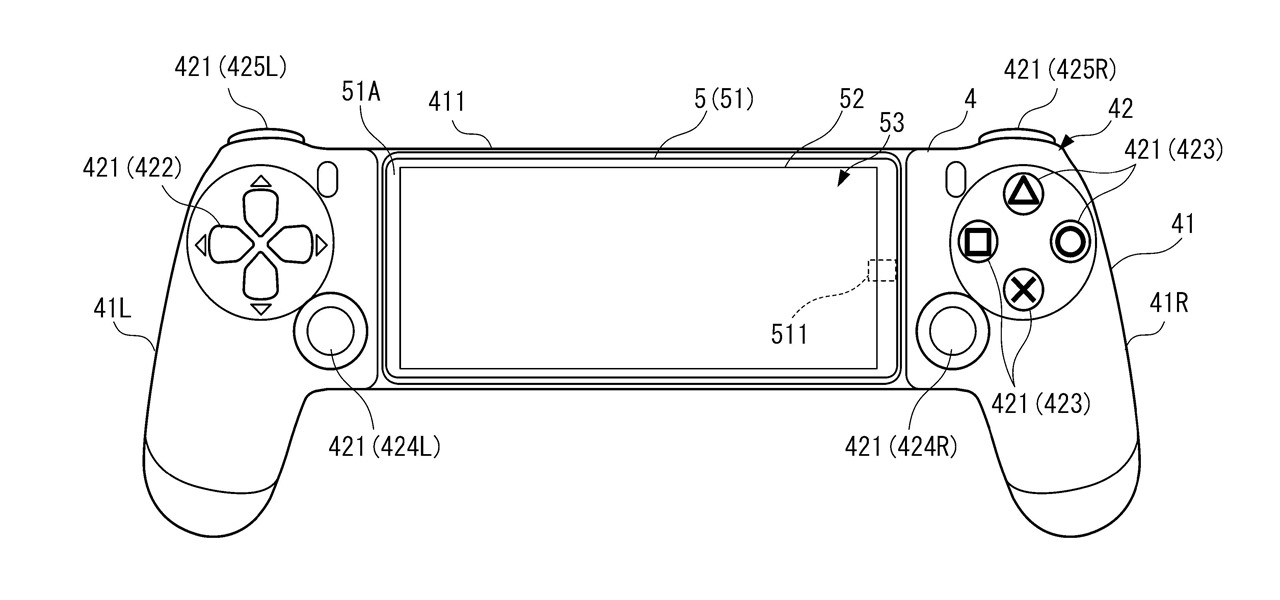
A new Sony patent shows the company doubling down on mobile gaming, and it could mean more advanced controller features for your iPhone or Android phone, similar to those in PlayStation's DualSense and DualShock controllers.

On Monday, the social media giant Facebook suffered a massive outage that, as of this writing, is still in effect.

Even with unlimited resources and a serious case of wanderlust, it's unlikely that you or I will be able to see all of the most famous structures in the world in person.

The Chinese short-form social media giant known as TikTok is getting into an increasingly crowded and competitive space: augmented reality effects tools.