Today is the anniversary of George Harrison's death nine years ago in 2001, and we thought a commemorative music lesson was in order. And instead of the usual Beatles fare, we thought we'd show you something a little less known, but just as good— "Handle with Care" by the Traveling Wilburys. Many still aren't familiar with the Traveling Wilburys, despite the superstar musicians involved, but that doesn't change the fact that these guys were awesome!

For anyone who lives in a space that may frown upon making holes in the walls, or for anyone who may not want to take on such a task, there's a simple alternative to hanging curtains or drapes. And the answer is brilliantly simple.

Know where the Dojo in the Courtyard is on Club Penguin? Then did you know you can walk on top of it? It's a cool little glitch that you can without getting banned from Club Penguin or anything like that. It's just a simple Club Penguin glitch.

In this how-to video, you will learn how to indicate if tree damage has occurred due to a natural gas leak. In this example, a Mexican Elder tree has been damaged by the gas leak. You can tell by the brown leaves. The plastic around the soil has trapped the gas in the soil, cutting off the oxygen from the tree. The Indian Hawthorne in this example has also been damaged. There is some foliage burn on the leaves. The bush will have to be trimmed back in order to save it. There are several plant...

Edna shows us the basics of making buttercream frosting for professional, decorative cakes starting with the right ingredients. She uses a basic buttercream recipe, but makes sure that she does not over-mix the ingredients. She also explains how she used to use Crisco, but when the company changed its recipe to zero trans fat, she decided to started using real butter, which makes the frosting a lot less yellow. Additionally, use of Crisco, makes the frosting drier and much more crumbly. If yo...

Want a smokey eye look but only have a single type of eye shadow? This home beauty video tutorial will teach you how to create a classy, imperceptibly gradiated eye look using that single shade of eye shadow.

Damsels in Distress: Everybody likes rescuing a helpless woman, or multiple helpless women. You'll find Antonio and company in the Dorsoduro district to the south. Talk to him and your conversation is interrupted by a murder—that's right, murder! After the cut scene, you need to kill the murderer, who's marked on your map and doesn't move. Make your way toward the murderer and you'll be stopped as he threatens to kill another courtesan. Lock onto him and equip your pistol. Charge the shot ful...

Pull off this easy prank, and – without causing any permanent damage – watch your coworker squirm with frustration.

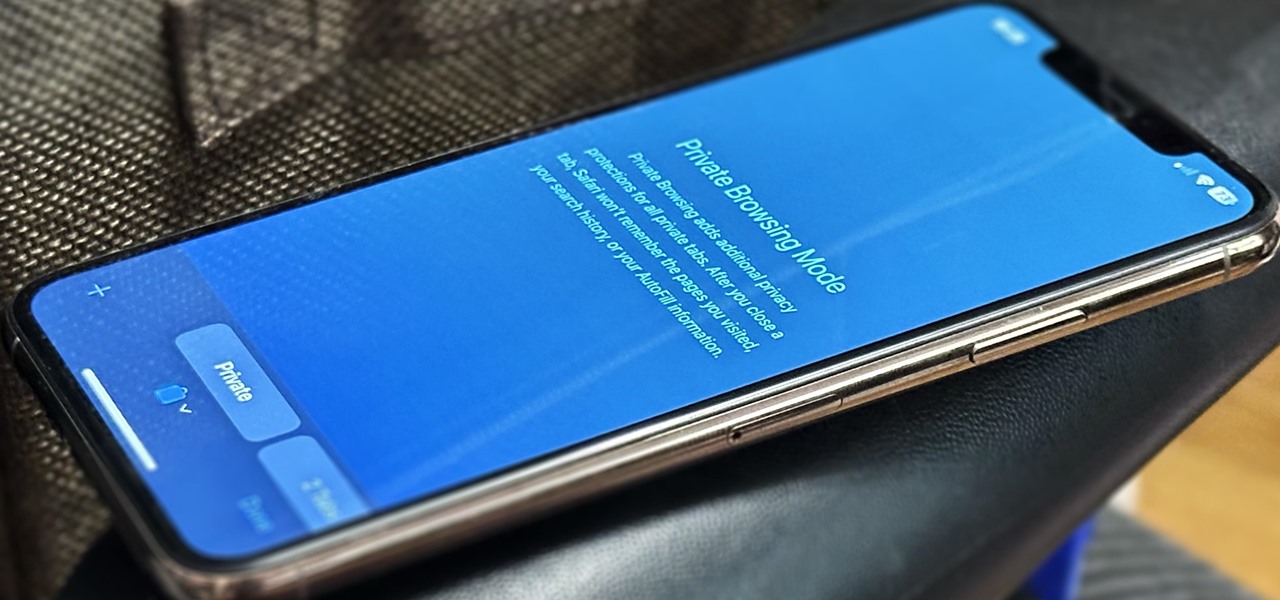
Private Browsing mode finally lives up to its name in Apple's huge Safari 17 update for iPhone, iPad, and Mac. So whether you search for things you don't want anybody to know about or want to ensure websites and trackers aren't eavesdropping on your activity, you'll want to update your devices pronto.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

It's easy to lose the TikTok video you were watching when you accidentally refresh your For You feed, but it's not gone forever. TikTok has a new feature for your iPhone, iPad, or Android device that can show you all your watched videos over the last seven days. There are also other, more hidden ways to see your watch history — one that goes well beyond a week.

Away from the hype around Facebook's smartglasses, the high-end fascination with the Microsoft HoloLens, and the unending rumors about Apple's AR wearable is the small but powerful darling of the enterprise AR world—Vuzix.

Facebook Reality Labs chief Andrew "Boz" Bosworth does a lot of hinting and teasing of what's coming next at Oculus, often with only a vague timeline on the horizon.

Snapchat parent company Snap has opened up its war chest to acquire yet another company that will play a role in its augmented reality ecosystem.

If you were to summarize the path Snap has taken towards augmented reality smartglasses with a meme template, how it started would be the first-generation Spectacles camera glasses and how it's going would be the next-generation Spectacles with AR capabilities.

The big day for Snap that resulted in the debut of brand new augmented reality Spectacles smartglasses is turning into a big week.

The surging activity in augmented reality in both the business and consumer sectors is being matched with a wealth of updates and partnerships from Snap Inc.

In the great smartglasses race, component makers, such as those that supply the crucial waveguide displays that make visualization of virtual content possible, have a vested interest in pushing the industry forward in order to ship units.

As Apple prepares to potentially introduce its (mostly) secretive AR headset for possible introduction later this year and launch next year, the company has made a strategic investment to ensure its supply chain can support it.

If it's always been your dream to work for a large company as an app developer, there's never been a better time to consider the field than right now — especially with companies like Apple staffing up in this department. It feels like everywhere you turn, companies are starting to move in this forward-thinking direction.

Throughout the COVID-19 pandemic, Facebook enjoyed a boost in sales of Portal, its smart video cameras with AR effects, as social distancing became the norm.

As augmented reality space continues to move into the mainstream, the competition to offer immersive services is ramping up as well.

Apple released the fourth public beta for iPhone today, Monday, Mar. 15. The update (build number 18E5178a) comes three hours after the fourth 14.5 developer beta, and includes references in its code to a new "City Charts" playlist feature in Apple Music.

Apple released the fourth developer beta for iPhone today, Monday, Mar. 15. The update (build number 18E5178a) comes 13 days after Apple seeded developers the third 14.5 beta, and 12 days after public testers received their third 14.5 update.

As businesses flocked to Zoom, Microsoft Teams, Google Meet, and other video conferencing platforms to bridge the gap, we wondered aloud -- why aren't more companies leaning even more heavily on augmented reality?

Ever since China's Nreal unveiled its Light smartglasses at CES two years ago, an army of look-alikes have emerged from the Asian nation.

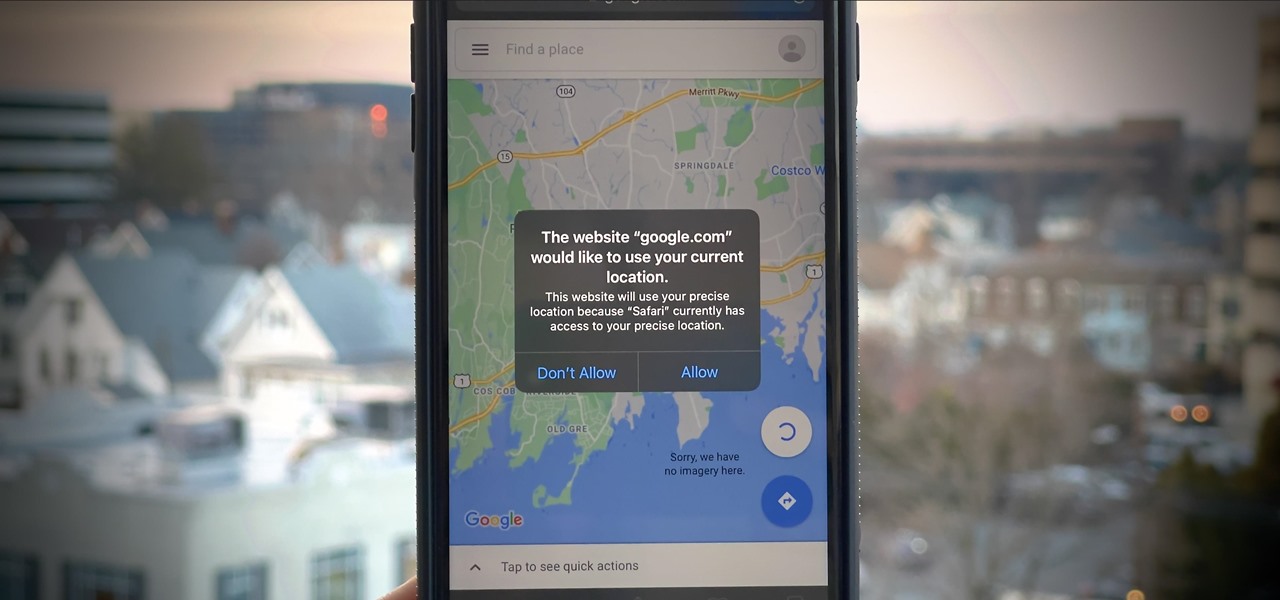
If you surf the web on your iPhone, you no doubt run into this problem all the time: a website wants your location. It can happen when performing a location-based task, such as using a store locator, or whenever a web app just wants to deliver better ads or local recommendations. If you're tired of allowing or denying permission each time, there's an easy way to stop the annoying security pop-ups.

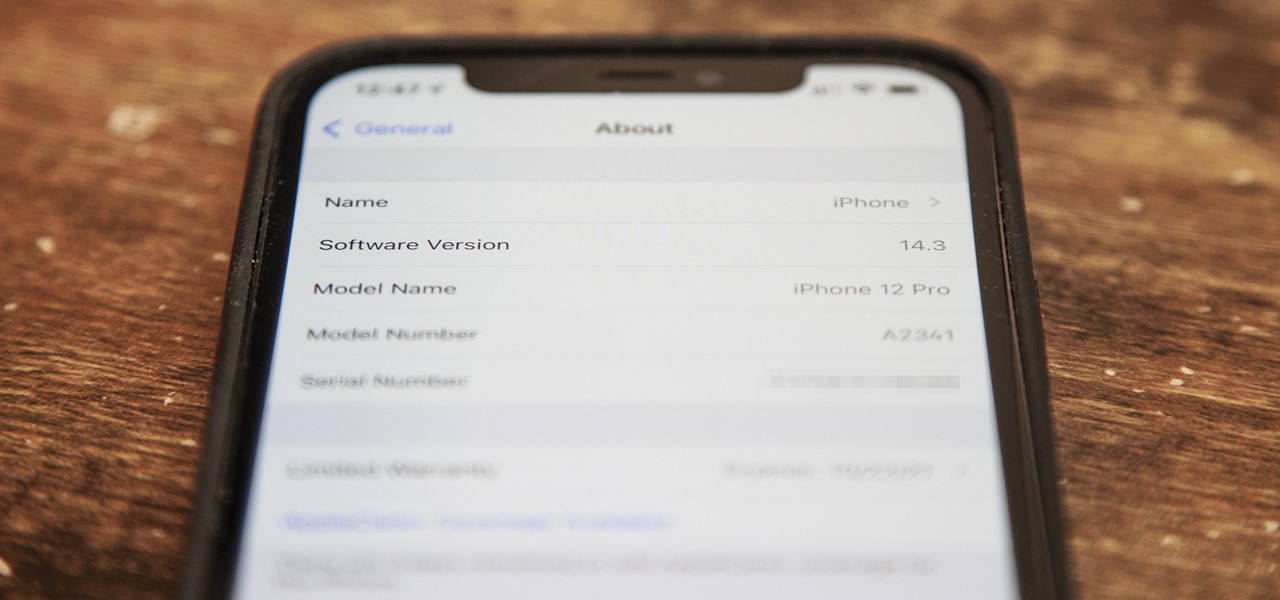
Just as expected, Apple pushed out iOS 14.3 to the masses on Monday, Dec. 14, which coincided with the pumped-up release of Fitness+, Apple's subscription workout service for Apple Watch users. It also came one day before the new AirPods Max hit buyers, and the iPhone needs iOS 14.3 to use all of its features.

For the longest time, we were simply stuck with Safari on the iPhone. Sure, you could install a third-party browser, but Safari was always the default, so tapping on links would always open Apple's app. Times have changed, however, and now you can set third-party browsers like Chrome, Firefox, and Edge as your iPhone's default choice.

Since Motorola engineer Bill Smith invented Six Sigma in 1986, corporations around the world have employed it to eliminate costs and process cycle time while increasing profits and customer satisfaction. These techniques and tools for process improvement were invaluable to famed CEO Jack Welch, who used them to redefine General Electric's business strategy in 1995.

Invented by Motorola engineer Bill Smith in 1986, Six Sigma's methodology defines a series of steps with specific value targets. These targets can be used, for example, to eliminate costs and process cycle time while increasing profits and customer satisfaction.

Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools make saving other people's photos and videos easy, and there are always screenshots.

In 2018, Niantic unveiled its in-development augmented reality cloud platform for smartphones, the Niantic Real World Platform. A demo showed Pikachu and Eevee cavorting in a courtyard, darting in front of and behind potted plants and people's legs as they walked through the scene. This would be the future of Pokémon GO.

On March 13, President Trump announced during a briefing in the Rose Garden that Google was building a COVID-19 screening website to help Americans understand if they might have the new coronavirus. If likely infected, the site would also include the location of a local drive-through testing site to visit. So how can you access the screening website?

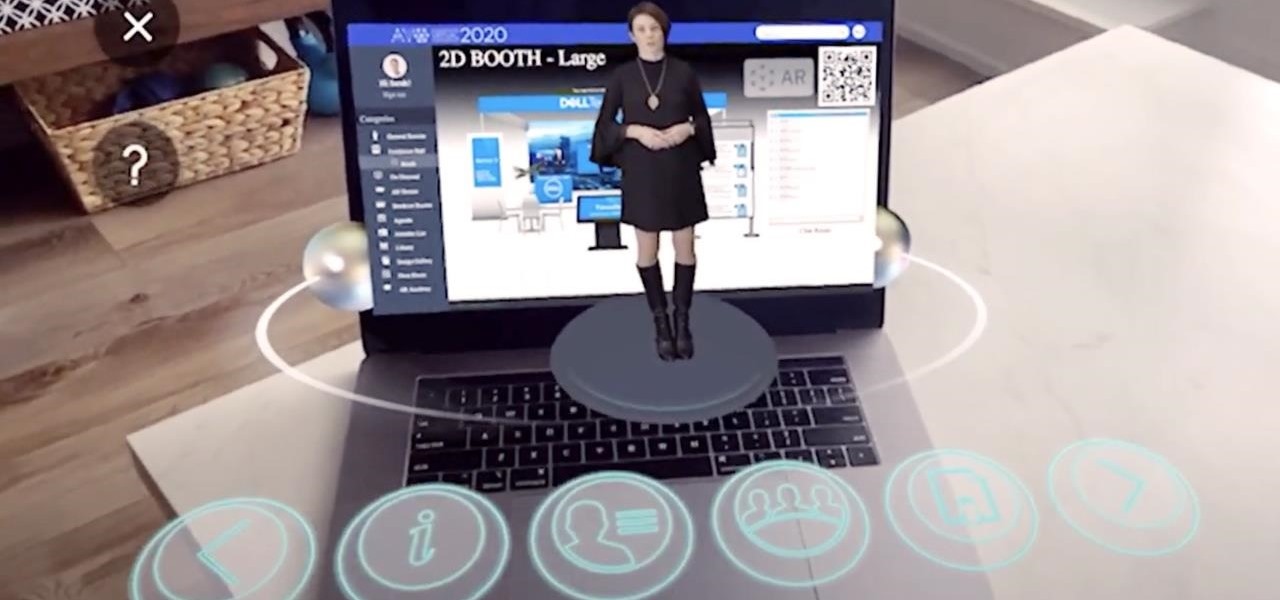
For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

Despite some of the biggest players in tech still lagging in terms of offering smartglasses options, there are nevertheless a number of smartglasses makers, including North and Vuzix, with consumer-grade smartglasses on the market right now.

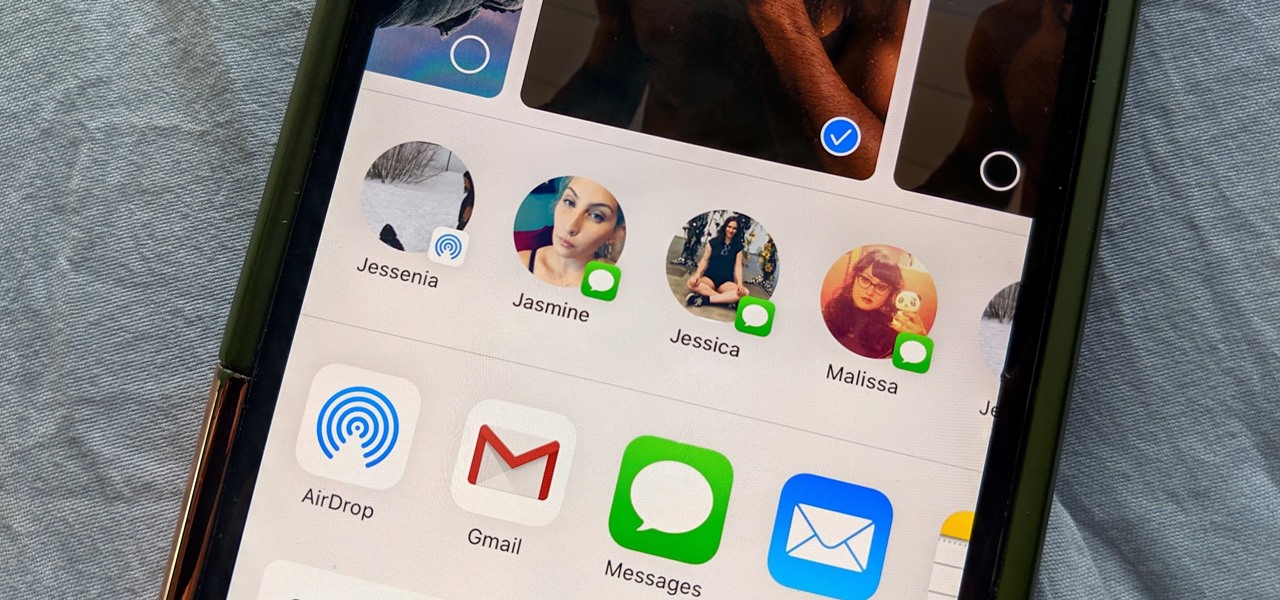
The share system on your iPhone serves as a hub for actions and share extensions, streamlining the process of saving files, sharing photos and videos, and other important tasks. On iOS 13 the Share Sheet has received a considerable upgrade, including the ability to more easily share content with your favorite contacts.

Whenever the name Magic Leap comes up, the talk inevitably seems to turn to the company's big-name backers and "unicorn-level" amounts of cash poured into the venture. And if it's not that, observers tend to focus on the company's market strategy and overall prospects.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Now that Microsoft has squarely focused on the enterprise market with the HoloLens 2, it appears Lenovo is content to play follow-the-leader with its new augmented reality headset.