Magic Leap's recent L.E.A.P. conference was free to all who registered in time, but if you weren't able to make the trip to Hollywood, the company just released video of some of the sessions that took place over the course of two days.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Augmented reality is expected to eventually change everything, and the prevailing view is that those changes will be for the better. The converse view, however, is that the technology will further erode privacy.
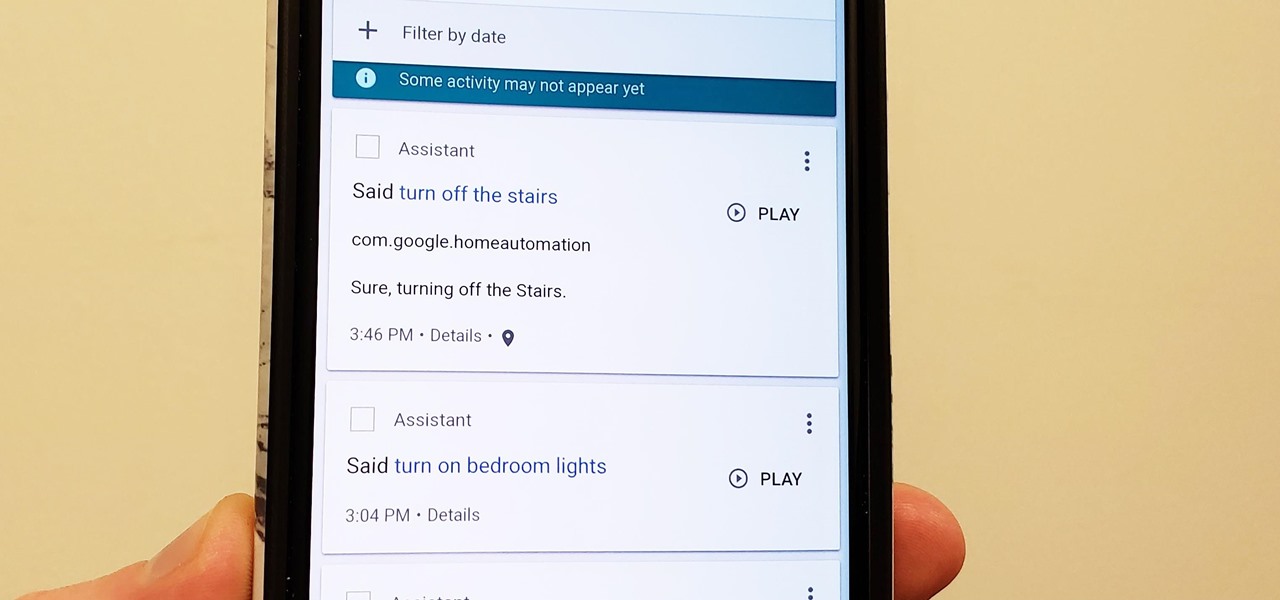
Privacy is a hot topic. In the wake of Facebook's data scandal, many want to safeguard their personal info. On the other hand, we all gain a certain amount of convenience by using services administered by huge companies like Google, Facebook, and Twitter. Google Assistant collects plenty of data, but you can easily check what is stored and delete items at will.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

Google, Facebook, and Huawei have made an investment in nurturing the future of augmented and virtual reality through $6 million in contributions to the opening of a new center at the University of Washington.

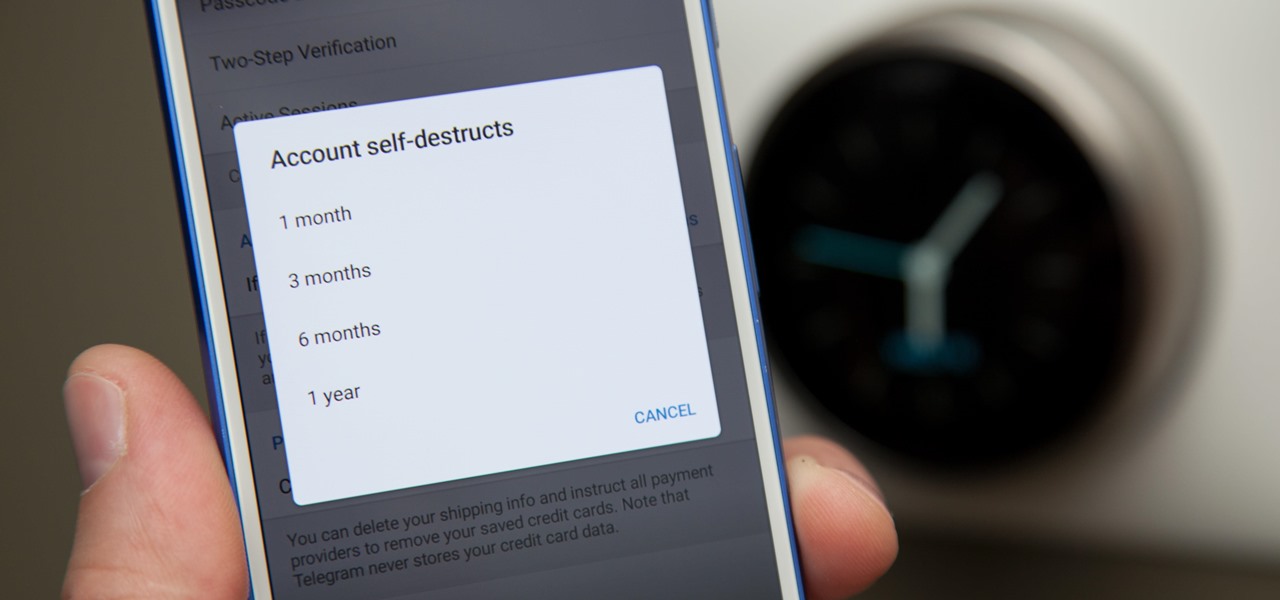
You can send self-destructing messages in Secret Chats, but that's not the only thing that can destroy itself in Telegram after a specified amount of time. Your whole account can disappear after a certain amount of inactivity, so it's important to adjust these settings to give you more time or to kill your account even quicker.

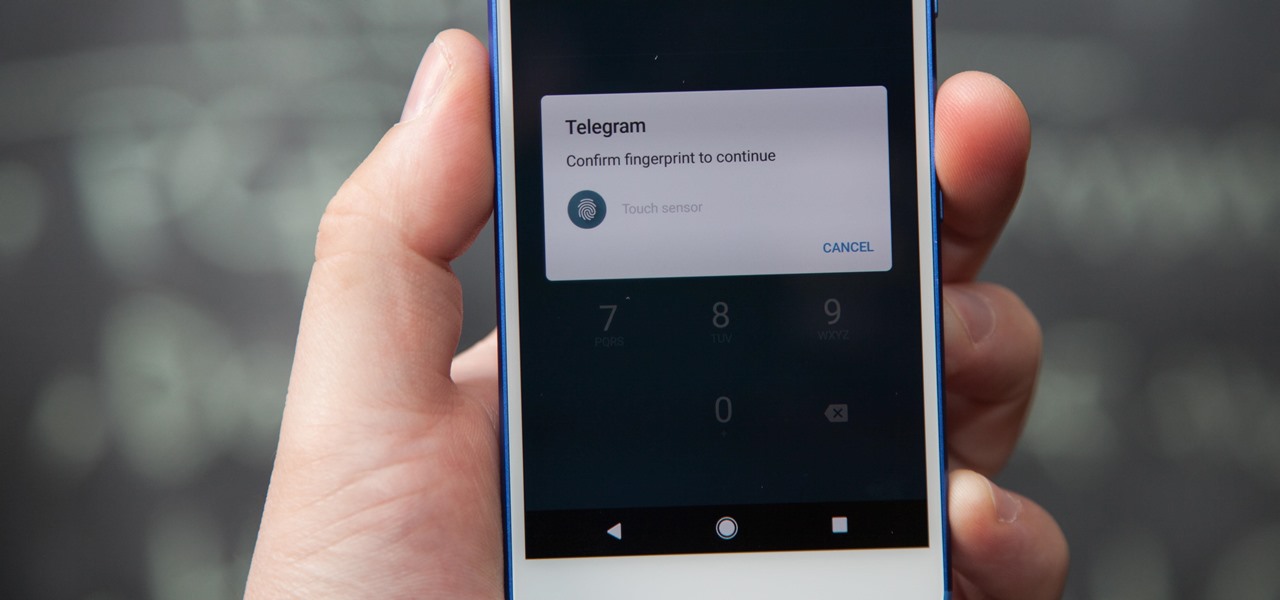
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.

Mobile augmented reality developer Blippar has updated its mobile app for iOS and Android with an augmented reality face profiles feature based on the company's real-time facial recognition engine.

Tesla has confirmed the EV carmaker has begun to upload videos from models equipped with its latest flavor of Autopilot, as Tesla seeks to "fleet source" data to help improve its cars' machine learning capabilities.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

Google seems to be growing tired of the way links appear in its Search results page, because they're currently experimenting with a color change (that's already causing lots of controversy).

Recently, Google unleashed the Chromecast development kit, which lets developers add Chromecast streaming functionality to their own apps. However, there aren't many apps with Chromecast capabilities yet, and big companies and devs are still working on polishing their final products.

You know that feeling when your cell phone gets stolen and you figure it is pretty much lost forever. You could've used one of the millions of device managers and trackers, but ya didn't. And the Good Samaritan is not coming to your rescue.

If you've been using Google's hidden App Ops to lock down and prevent some of your Android applications from exposing your privacy, then think twice before updating to the new Android 4.4.2 software.

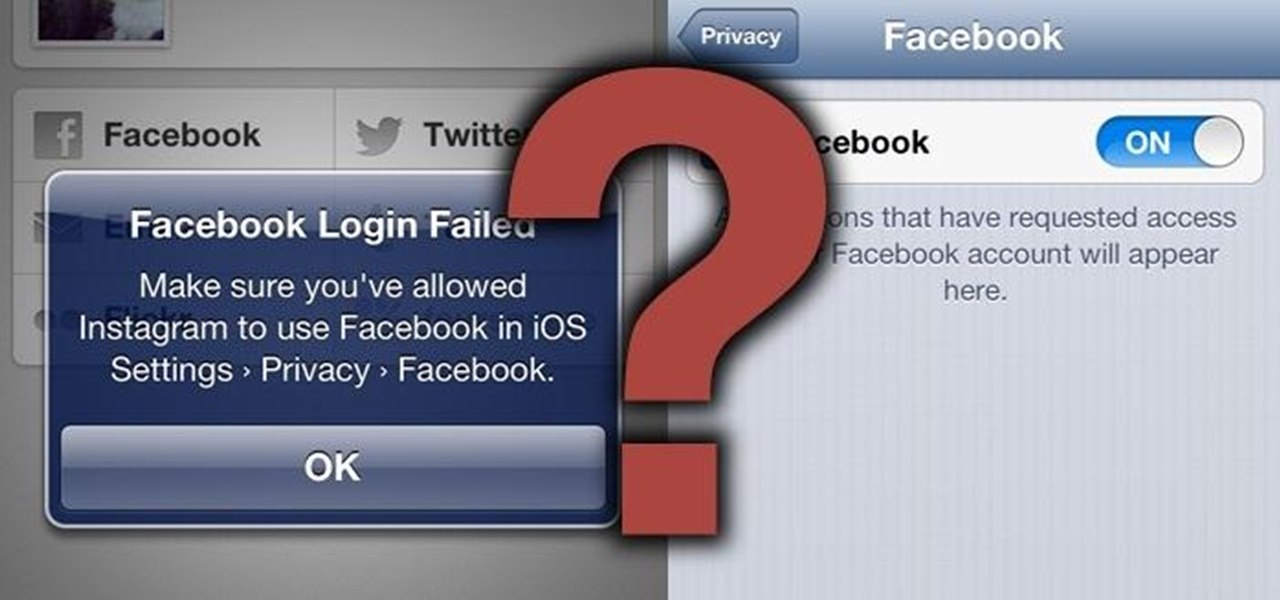
I recently ran into a problem connecting my Instagram app on my iPhone 5 to Facebook, and neither Instagram's or Facebook's help pages were as helpful as they claim to be.

Tim and Kevin meet up/hang out & talk their talk. They discuss buying domain names, choosing business names, starting companies, and selling books by their color. These two entrepreneurs have lots to teach us about selling ideas and making profitable businesses.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

Smartphones and dark mode go hand in hand. Screens can be bright, causing eye strain and battery drain, and dark mode can take the edge off both. It's perfect for nighttime browsing, but also for general use, especially on OLED displays with inky blacks. Dark mode, aka night mode, is particularly great for tweeting, and Twitter makes it easy to switch.

New updates are always exciting, even more so when Google's behind the wheel. Yes, Android 10 "Q" is here, at least in beta form, ready for software testers to dive in and explore all the new changes. Among those changes, however, lie some issues. We won't sugarcoat it — there are some annoying things baked into Android 10.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.

When you leave your iPhone on a table or anywhere within somebody else's eyeshot, a private message may pop up on your lock screen that could be read by anyone who sees it. But there's a way to keep others from reading your possibly sensitive text messages and emails without giving up the convenience of lock screen notifications entirely.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.

It seems that every major social media platform is adding a "Go live" feature to their apps lately. Twitter, in particular, has been at the forefront of the live broadcasting craze for quite some time now.

When you post something online, it pretty much stays there. So it's no surprise that Snapchat, the self-destructive photo-sharing app, became such a huge hit, boasting an estimated 50 million users. Its ephemeral nature has proven popular, especially with teenagers—who are now well aware of the burden that permanence on the internet has.

Need help with Satellite Uplinks in Battlefield: Bad Company 2 on the Xbox 360? Jack and Geoff from Achievement Hunter give you this two-part video guide on finding all 24 M-Com Stations. In the first video, see the locations of the first 12 M-COM Stations that you must explode for great glory! Part two of this tutorial reveals the last 12 locations, along with the location of the Holy Grail. They also finally break that barrier and hug each other. And they also pick up the Complete Blackout ...

Check out this guide to Battlefield Bad Company 2, the mission entitled Zero Dark Thirty. Find the M-Com Stations and destroy them, but stay alert for all enemies. Watch this video walkthrough to learn how to complete the Zero Dark Thirty mission in Bad Company 2 on the PS3.

Things are really heating up now with that the Russians are putting on the pressure in Battlefield Bad Company 2. This time your helicopter gets hit by an RPG and you need to put it down and make your way through the clearing in the jungle. Destroy all the M-Com Stations, and nobody can die. Watch this video walkthrough to learn how to complete the No One Gets Left Behind mission in Bad Company 2 on the PS3.

The first thing you need to do in this mission on Battlefield Bad Company 2 is to hop out of the copter and get in the sand buggy and head to your marked location. You'll need to locate and head to each station on the map: Bravo Base Station, Charlie Base Station, and Alpha Base Station. After that, complete the Triangulation Point. Watch this video walkthrough to learn how to complete the Sangre Del Toro mission in Bad Company 2 on the PS3.

In Obstetrics and Gynecology (OB/GYN), doctors deal specifically with the female reproductive organs, which means a lot of visual inspection of the vaginal area. Whether you're a doctor, surgeon, nurse, or nursing assistant, knowing how to properly drape a patient is detrimental to the patient feeling protected and secure with the hospital staff, along with having some privacy. This video will cover different types of draping techniques.

Is your smartphone eavesdropping on you? It's a question that will never go away because it's easy to envision hackers or malicious apps taking over your device to spy on conversations, snap photos, or even record video. But fewer people will be asking it, thanks to Android 12, which has a new privacy feature that visually warns you of possible invasive surveillance.

Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

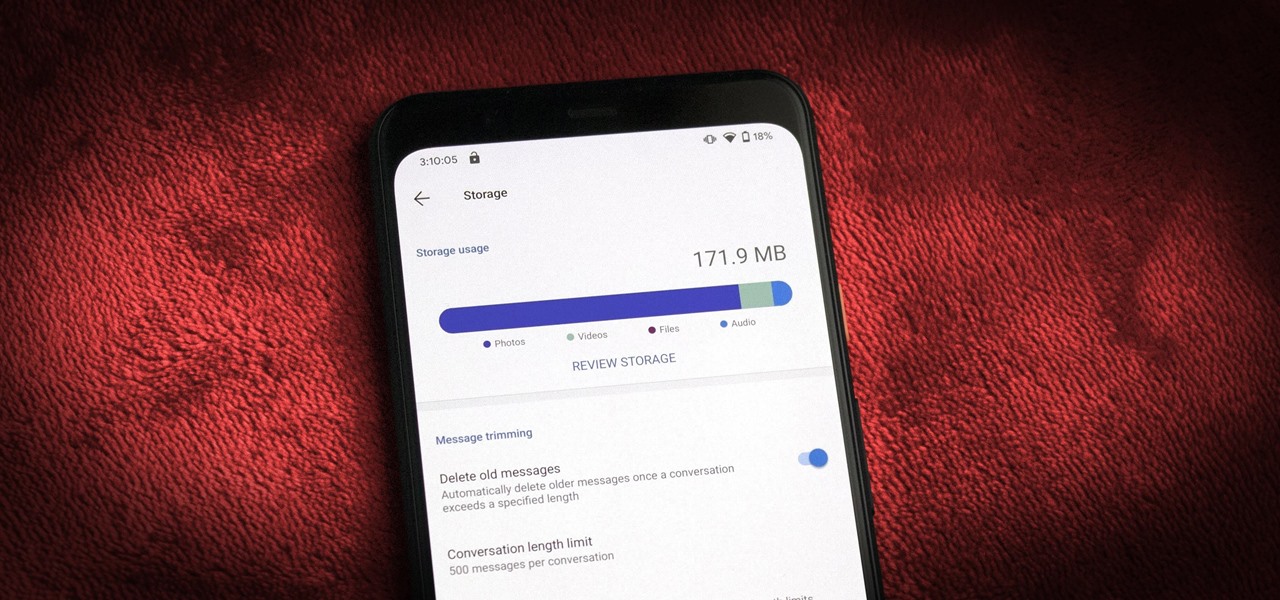
Thanks to backups, Signal conversations can span over multiple years and multiple phones. These archives can get rather large as you share photos, videos, and other files with friends. But between the other apps and large files on your phone, you might not be able to afford to keep all those messages.

Every iPhone since the 5S has come equipped with a microchip called a motion coprocessor, which collects data from integrated accelerometers, gyroscopes and compasses, and can then transfer that information to fitness apps that track physical activity. Essentially, the chip knows whether you're running, walking, sleeping, or driving — but what if you don't want it to?