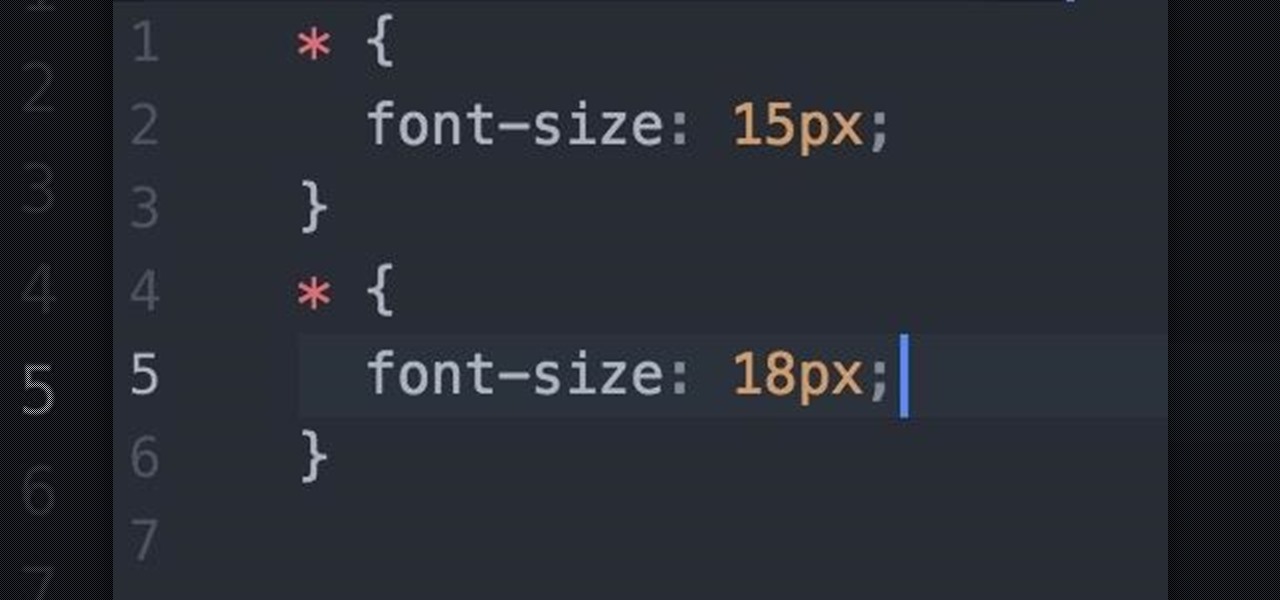
Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure.

Things aren't looking good for Uber after its driverless experiment in Pittsburgh soured relations with local authorities. Surprised? Me neither.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Augmented reality software developer Edgybees has launched Drone Prix. The new mobile app immerses DJI drones and their pilots in more than 30 augmented reality obstacle courses.

John Legere seems to operate under the philosophy of, "If you're going to be late to the party, throw a better one." On Tuesday, Legere announced T-Mobile's intention to build the nation's first true 5G network, following AT&T's rollout of its "5G Evolution" network. A network which many said was, to put it in polite words, nonsense.

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.

It's always nice getting paid to do something you love. That's why Nintendo is offering all Nintendo Switch owners a chance to find vulnerabilities before another hacker beats them to it first. Depending on the vulnerability you find, Nintendo is willing to shell out rewards starting at $100, all the way to $20,000, to the first bug reporter who uncovers it.

As someone who grew up adamantly complaining every time my parents dared to turn on talk radio in the car, I can admit it's a bit weird that I have a love affair with podcasts. I can't help it! Even though podcasts are essentially the modern-day customizable talk radio, I choose to defend my all-out obsession with pointing out how popular they are (I mean, SNL even picked up on the trend).

Pinterest, a worldwide catalog of ideas shared by over 175 million users every month, is dominated by Android users, who are now the app's fastest growing group. Pinterest has since taken notice, and has started to incorporate handy home screen shortcuts for users with Android 7.1 or higher.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

Lightform might just be the thing to have at your next party. The San Francisco-based company just created the first computer ever able to connect to a projector and instantly scan 3D scenes to mix reality with projected light.

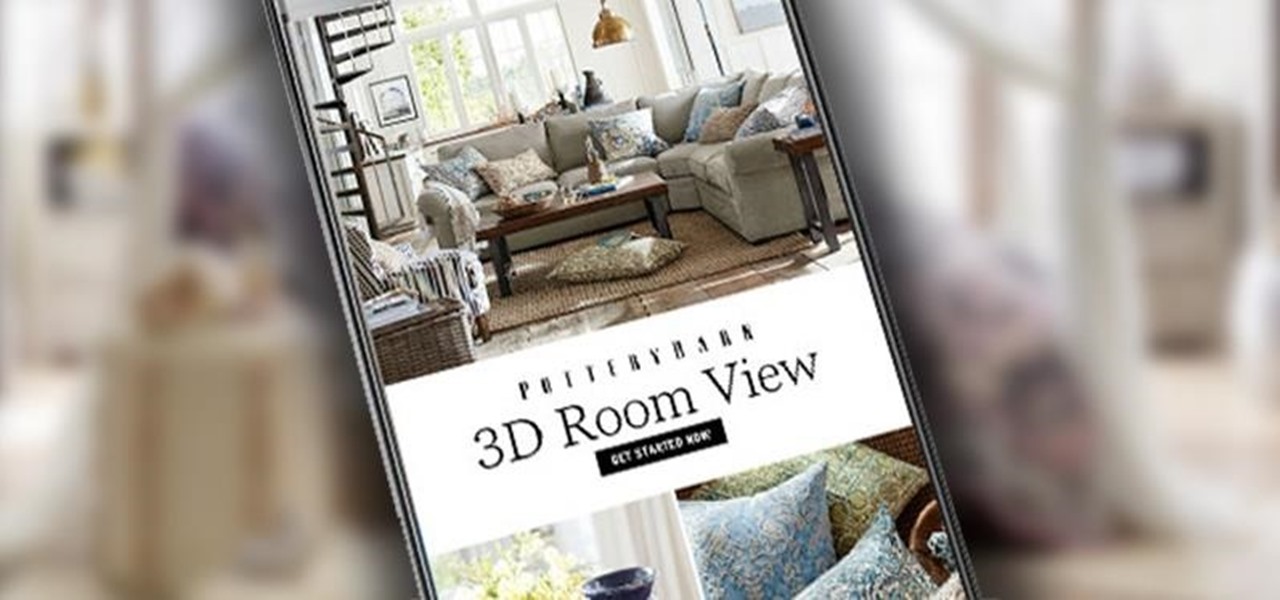
Pottery Barn has teamed up with Google to create 3D Room View, a new mobile app to allow all wannabe interior designers (like me) to pick out the perfect couch, table, or whatever, and then overlay it onto a spot in his or her house.

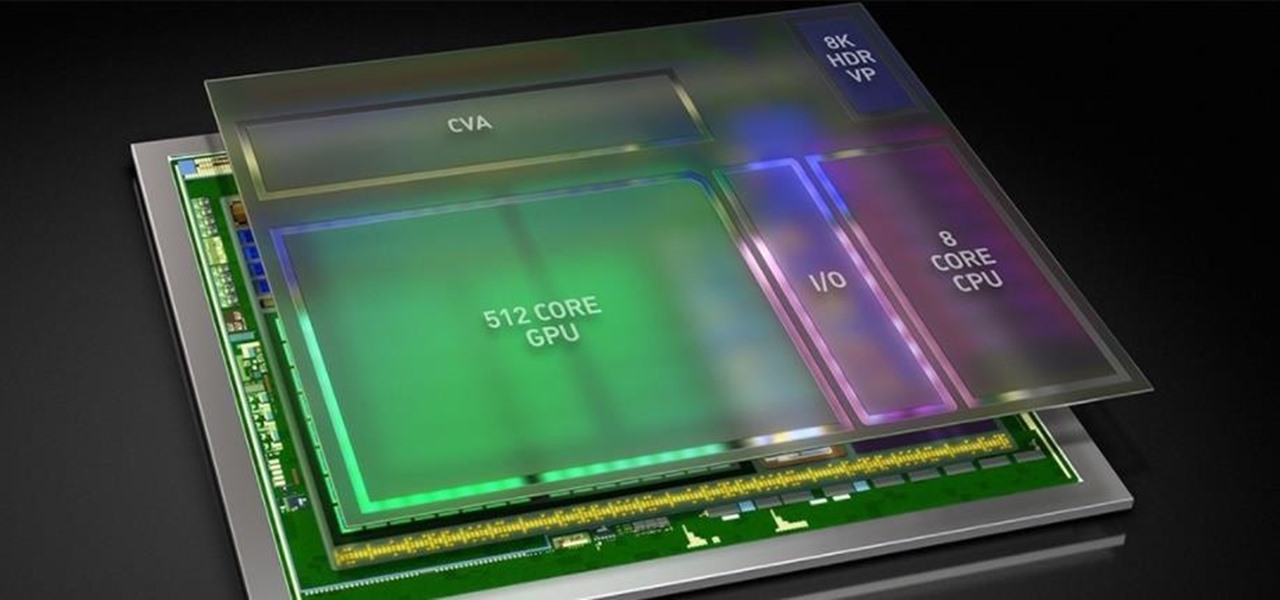
As Intel steps up their investment in driverless technology with a $15 billion acquisition of Mobileye, so have automotive supplier Bosch and NVIDIA teamed up to manufacturer driverless car systems with the much-awaited Xavier chip.

Throughout the summer and fall of 2016, in the sudden whirlwind that was Pokémon GO, it was hard to go anywhere in public without seeing someone attempting to catch Pokémon. Now, thanks to an upcoming platform called Motive.io, from the Vancouver company of the same name, location-driven application development will soon be accessible to everyone.

Cyanogen, Inc., the for-profit company that spun off from its CyanogenMod roots several years ago, has announced that they're shutting down all of their services. The company's impending demise shouldn't directly impact many Android users, but the announcement does have one major repercussion: The servers that used to host the popular CyanogenMod custom ROM have now been shut down.

When the "Just another day in the office at Magic Leap" video was released last year, it was called a mind-blowing, stunning, and breathtaking take on mixed reality gaming. It was a great presentation of what the technology could be, but not for a second did I think it was anything other than a concept video, and I'm not the only one who thought that. This was a goal to reach for mixed reality, not the reality.

As a commercial and potentially consumer product, one might assume it very unlikely to see the Microsoft HoloLens in the military marketplace. And that assumption would be completely wrong. One company from the Ukraine is currently working on using the mixed reality head-mounted computer for 360-degree vision inside armored tanks. If a tank crew could see the entire battlefield there are in, they would likely have a better chance of accomplishing their mission and avoiding damage. Tanks are l...

Uh oh. With millions of devices already sold, Apple's latest blunder is bound to upset the owners of some of their brand new iPhone 7 Plus phones.

The reviews for the Google Pixel phone have hit the web. There's a lot of praise, but not all are so positive. We've collected some of the best takes on the new devices from the top tech sites around.

The future for the Meta 2 augmented reality headset will have to wait. While shipments were supposedly on their way out back in June, Meta revealed today that they need a bit more time to provide the best possible experience—and that's really for the best.

A human rights activist from the United Arab Emirates recently stumbled upon three gaping security loopholes in iOS that work by enticing you to tap a link sent to your iPhone. Ahmed Mansoor received a text message from an unknown number roughly two weeks ago, but instead of following the link it included, he sent the message over to a security researcher at Citizen Lab.

If you spend weekend mornings sadly turning your omelet attempts into scrambled eggs rather than enjoying a perfectly flipped omelet, reach for a resealable plastic bag. Using a ziplock bag to make an omelet is not only foolproof, it's the perfect solution to cooking for a crowd, where you can make everyone's customized omelets at the same time. How cool is that?!

If you're tired of Google tracking you, but love how Chrome works, CyanogenMod has you covered. Their browser is called Gello, which is based off Chromium, Chrome's open-source counterpart. It's basically a souped-up version of Chrome—without all of the intrusive Google stuff. So if you're uncomfortable with Google displaying personalized ads based on your browsing history, or using your location to bring the "Physical Web" to your phone, you won't have to worry about any of that with Gello.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

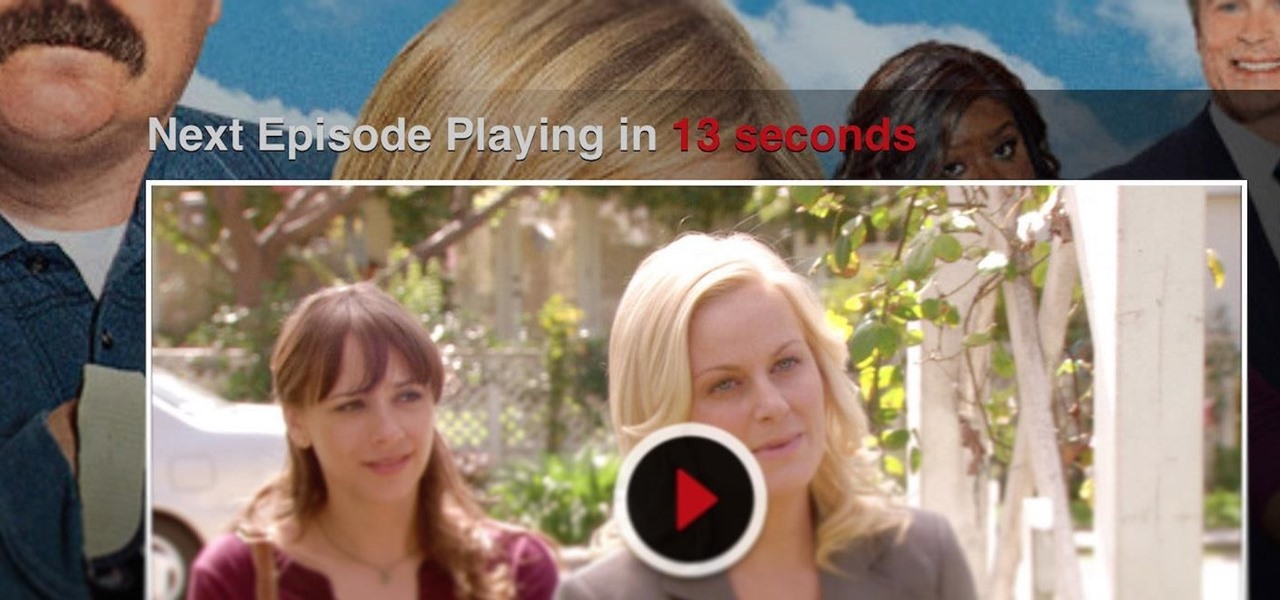
Cord cutters are changing everything about TV—the more of us that sever ties with cable, the more changes we start to see. In fact, viewing habits have already changed so drastically that waiting a week to see the next episode in a series is no longer acceptable, as binge watching has completely eclipsed this old-fashioned format.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

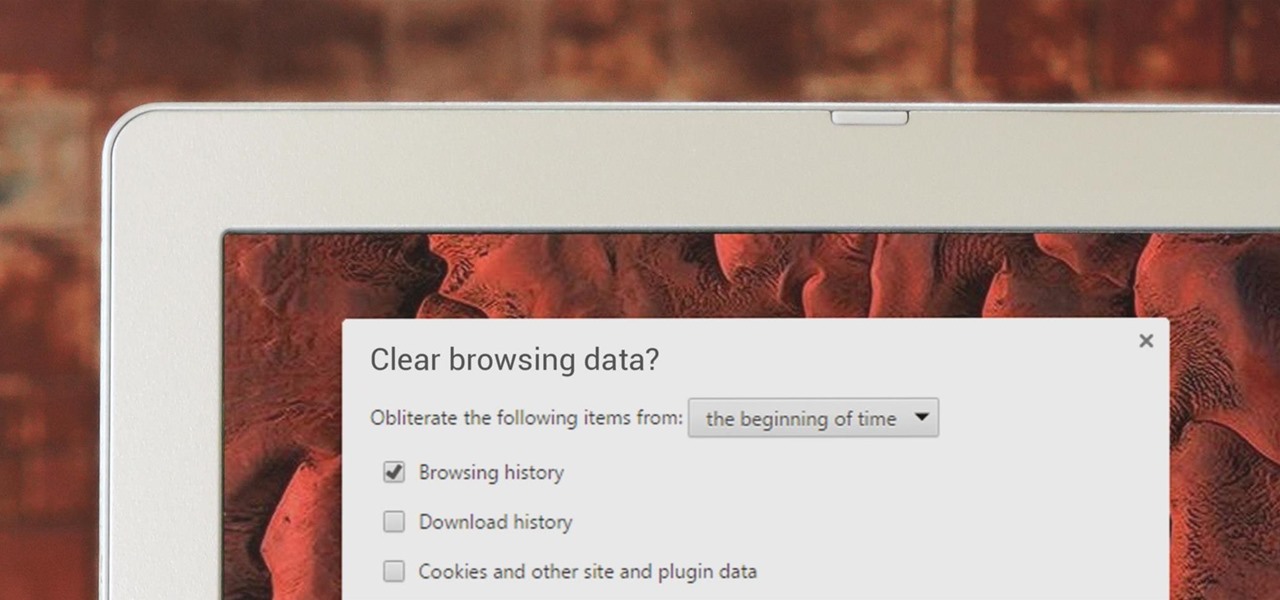
If you've been visiting websites of ill repute, or if you've been Christmas shopping and don't want to spoil the surprise, it would be a disastrous situation if anyone were to come across your browsing history. Visited sites, cookies, and cache can paint a very clear picture of your recent internet activity, and depending on the situation, you may only have a few seconds to delete your history before someone else barges in.

Welcome fellow Null-Byters! I would suggest you watch reading my last tutorial before we begin. In our last adventure, we began making a simple, ugly website. If we want it to make it look good, we should add some styling. But first, we need to understand the basics.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

I'm lucky enough to have internet access on my laptop practically everywhere I go because of my mobile hotspot plan. All I have to do is enable the personal hotspot feature from my iPhone and I can surf the web on any Wi-Fi enabled device. But of course, there's a catch.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

On an Android device, you can download almost any file type into a neat and tidy "Downloads" folder, and those files can then be accessed with an appropriate app, shared via email, or transferred over to your computer. On an iPhone, there is no such folder, and saving files from Safari is almost impossible unless you're jailbroken.